R:BASE 7.6 Command Index
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows NT® 4 for Dummies® File:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM
Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM Table of Contents Windows NT® 4 For Dummies® Introduction About This Book How to Use This Book And What about You? How This Book Is Organized Part I: Introducing Windows NT (Bare-Bones Stuff) Part II: Making Windows NT Do Something Part III: Using Windows NT Applications Part IV: Been There, Done That: Quick References for Moving to Windows NT Part V: Getting Help Part VI: The Part of Tens Icons Used in This Book Where to Go from Here Part I: Intro to Windows NT (Bare Bones Stuff) Chapter 1: What Is Windows NT? What Is This "Windows" Stuff, Anyway? What Does Windows NT 4 Do? Why Should I Bother Using Windows NT? Will I Like Windows NT 4 Better than Windows NT 3.51? What's the Difference between Windows NT Workstation and Windows NT Server? Bracing Yourself for Windows NT 4 Chapter 2: Boring Information, Bothersome Computer Parts The Computer Microprocessor Floppy Disks, Compact Discs (CDs), and Disk Drives Floppy disk flipping What disk drives does Windows NT like? What does "write-protected" mean? Driving with compact discs The Mouse and That Double-Click Stuff Cards and Monitors Keyboards Groups of keys More key principles Print Screen: the one fun, weird code key Modems Printers Networks Sound Cards (Disgusting Bioactive Noises) Parts Required by Windows NT Chapter 3: Windows NT Stuff Everybody Thinks You Already Know Backing Up Your Work Clicking 1 of 9 07/14/99 08:29:14 Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM -

Copyrighted Material
2986IDX.qxd 9/6/01 12:12 AM Page 425 Index Note to the reader: Throughout this index boldfaced page numbers indicate pri- mary discussions of a topic. Italicized page numbers indicate illustrations. A for Local Users and Groups, 171 in Shared Folders, 333 abstracts, from Indexing Service, 140 Active Directory, 7–8 Accessibility, 2–6 for adding programs, 12 Internet Explorer options, 157 ActiveX controls, security settings for, 158 Magnifier, 176–177 Add Counters dialog, 257, 257–258 Narrator, 195–196 Add Excluded Files dialog On-Screen Keyboard, 234, 234–235 (Backup), 35 Options window, 2, 2–3 Add Hardware Wizard, 8–10, 350–351 Utility Manager, 385–386, 386 Add or Remove Programs, 10–13 Accessibility Options dialog, Keyboard address bar tab, 3, 3–4 in Explorer, 101–102, 102 Accessories, 6 in Internet Explorer, 149 Calculator, 37–38 Address Book, 13–25 Command Prompt, 46, 46–47 contact template, 20 Communications, 47 creating contacts, 16–17 Entertainment program group, 92 folders, 22–23 Program Compatibility Wizard, 288, 288–289 groups, 20–22 System Tools, 366. See also Backup identities for, 24–25 Character Map, 40 menus, 15–16 Disk Cleanup, 69–71, 71 retrieving e-mail addresses from, 241 Disk Defragmenter, 71–75 searching for people in, 325–326 File and Settings Transfer toolbar, 14, 15 Wizard, 112 window, 14 Scheduled Tasks, 316, 316–322 Address toolbar, 367 System Information, 361–363COPYRIGHTEDAdministrative Tools, MATERIAL 25–26. See also System Restore, 364, 364–365 Microsoft Management Console (MMC) snap-ins Windows Explorer, 97, 97–106 Active Directory, 7–8 Windows Movie Maker, 406–414, 407 for adding programs, 12 Action menu COM+ (Component Services), 45 for Device Manager, 59–63 Data Sources (ODBC), 51–55 425 2986IDX.qxd 9/6/01 12:12 AM Page 426 ADMINISTRATOR ACCOUNT Event Viewer, 93, 93–96, 94 attrib command, 291 Local Security Policy, 168, 168–170, AU files, 396 168–170 audio. -

Technical Information, You Will Find Several Different Types of Symbols Are Used to Identify Different Sections of Text
Technical FAST/TOOLS R10.01 Information System Hardening Windows 7/8, Windows Server 2008/2012 TI 50A01A10-02EN (Rev. 1.0) Yokogawa Electric Corporation TI 50A01A10-02EN 2-9-32, Nakacho, Musashino-shi, Tokyo, 180-8750 Japan ©Copyright June 2015 (YK) Tel.: 81-422-52-2006 Fax.: 81-422-52-2540 1st Edition June 30, 2015 (YK) Blank Page i Introduction n Purpose In order to protect systems from network related security vulnerabilities, it is important to harden the operating system on which the application is running. This document describes the hardening procedure to be followed for FAST/TOOLS R10.01 systems running Microsoft operating systems. n Validity This document is primarily intended for internal Yokogawa use when engineering projects that use FAST/TOOLS on Microsoft operating systems. n Definitions, Abbreviations and Acronyms AV : Antivirus software DMZ : DeMilitarized Zone GSC : Global SCADA Center SCADA : Supervisory Control And Data Acquisition n References [1] McAfee VirusScan Enterprise version 8.8, YHQ recommended antivirus software. [2] IT Security Guide for System Products (Common Information) TI30A15B30-01E. All Rights Reserved Copyright © 2015, Yokogawa Electric Corporation TI 50A01A10-02EN June 30, 2015-00 ii n Symbol Marks Throughout this Technical Information, you will find several different types of symbols are used to identify different sections of text. This section describes these icons. CAUTION Identifies instructionsthat must be observed in order to avoid physical injury and electric shock or death to the operator. IMPORTANT Identifies importantinformation required to understand operations or functions. TIP Identifies additionalinformation. SEE ALSO Identifies asource to be referred to. n Trademark • FAST/TOOLS is registered trademark of Yokogawa Electric Corporation. -

DPS7000/XTA User's Guide Security on the DIANE System
A Security of the DIANE System ASCALE 7000 DPS7000/XT NOV Security REFERENCE 47 A2 02EL 01 DPS7000/XTA NOVASCALE 7000 Security of the DIANE System Security September 2004 BULL CEDOC 357 AVENUE PATTON B.P.20845 49008 ANGERS CEDEX 01 FRANCE REFERENCE 47 A2 02EL 01 The following copyright notice protects this book under Copyright laws which prohibit such actions as, but not limited to, copying, distributing, modifying, and making derivative works. Copyright Bull SAS 2004 Printed in France Suggestions and criticisms concerning the form, content, and presentation of this book are invited. A form is provided at the end of this book for this purpose. To order additional copies of this book or other Bull Technical Publications, you are invited to use the Ordering Form also provided at the end of this book. Trademarks and Acknowledgements We acknowledge the right of proprietors of trademarks mentioned in this book. Intel® and Itanium® are registered trademarks of Intel Corporation. Windows® and Microsoft® software are registered trademarks of Microsoft Corporation. UNIX® is a registered trademark in the United States of America and other countries licensed exclusively through the Open Group. Linux® is a registered trademark of Linus Torvalds. The information in this document is subject to change without notice. Bull will not be liable for errors contained herein, or for incidental or consequential damages in connection with the use of this material. Preface Preface Purpose This document targets customers requiring information about security issues on the Diane system (DPS7000/XTA). Several aspects of security are dealt with: NTFS permissions, essential services for the smooth running of the system and its maintenance, user groups and accounts, the NetBios share, the use of an antivirus software and the Windows updates. -

Windows XP Power-Users Troll the Web, Documentation, and Friends for Useful Tips and Tricks--A Keyboard Shortcut Here, an Undocu
< Day Day Up > • Table of Contents • Index • Reviews • Reader Reviews • Errata • Academic • How to Cure the SP2 Upgrade Blues • Power Hound Tips for Online Protection Windows XP Power Hound By Preston Gralla Publisher: O'Reilly Pub Date: September 2004 ISBN: 0-596-00619-5 Pages: 400 Windows XP power-users troll the web, documentation, and friends for useful tips and tricks--a keyboard shortcut here, an undocumented double-click there to eliminate annoyances, save time, and take control of their Windows XP. There's an easier way. This insightful and amusing book is packed with hundreds of power tips, cool tricks, and workarounds in one organized, easy-to-use resource--for everything from the desktop to Office programs to the registry. < Day Day Up > < Day Day Up > • Table of Contents • Index • Reviews • Reader Reviews • Errata • Academic • How to Cure the SP2 Upgrade Blues • Power Hound Tips for Online Protection Windows XP Power Hound By Preston Gralla Publisher: O'Reilly Pub Date: September 2004 ISBN: 0-596-00619-5 Pages: 400 Copyright The Missing Credits About the Author About the Creative Team Acknowledgments The Missing Manual Series Introduction How This Book Works Some Experience Required About These Arrows About MissingManuals.com Chapter 1. Getting Started Section 1.1. Startup and Shutdown Section 1.2. Controlling Your Monitor and Sounds Section 1.3. Individual Windows Tricks Section 1.4. User Accounts and Logons Chapter 2. The Desktop and Interface Section 2.1. Desktop Makeover Section 2.2. The Start Menu Section 2.3. The Taskbar Section 2.4. The Control Panel Section 2.5. -

Ba Asics S of C Com Mpute Er
Bachelor of Commerce (DDE) Semester – II Paper Code – BM2006-II BASICS OF COMPUTER - II DIRECTORATE OF DISTANCE EDUCATION MAHARSHI DAYANAND UNIVERSITY, ROHTAK (A State University established under Haryana Act No. XXV of 1975) NAAC 'A+’ Grade Accredited University Material Production Content Writer: Copyright © 2020, Maharshi Dayanand University, ROHTAK All Rights Reserved. No part of this publication may be reproduced or stored in a retrieval system or transmitted in any form or by any means; electronic, mechanical, photocopying, recording or otherwise, without the written permission of the copyright holder. Maharshi Dayanand University ROHTAK – 124 001 ISBN : Price : Publisher: Maharshi Dayanand University Press Publication Year : 2021 B.Com-I (Second Semester) Basics of Computer-II PAPER CODE: BM2006-II Theory Paper Max Marks: 80 Time: 3 Hrs Internal marks: 20 Note: - The Examiner shall set nine questions in all covering the whole syllabus. Question No.1 will be compulsory covering all the units and shall carry 8 small questions of 2 marks each. The rest of the eight questions will be set from all the four units. The examiner will set two questions from each unit out of which the candidate shall attempt four questions selecting one question from each unit. All the questions shall carry 16 marks each. Unit-I Types of software; Application and system software, multi programme, operating- system and its functions, Time sharing, multiprocessing. Unit-II Computer Applications: Computer application in Education, Commerce & Marketing and Management. Unit-III Introduction to windows: Types of windows, Windows as an operating system, Windows explorer, using clipboard, using paint brush, control panel installing a printer. -
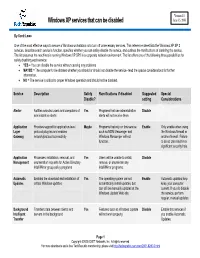
Windows XP Services That Can Be Disabled June 15, 2005
Version 1.0 Windows XP services that can be disabled June 15, 2005 By Scott Lowe One of the most effective ways to secure a Windows workstation is to turn off unnecessary services. This reference sheet lists the Windows XP SP 2 services, describes each service's function, specifies whether you can safely disable the service, and outlines the ramifications of disabling the service. The list assumes the machines is running Windows XP SP2 in a corporate network environment. The list offers one of the following three possibilities for safely disabling each service: • YES = You can disable the service without causing any problems. • MAYBE = The computer's role dictates whether you should or should not disable the service--read the special considerations for further information. • NO = The service is critical to proper Windows operation and should not be disabled. Service Description Safely Ramifications if disabled Suggested Special Disable? setting Considerations Alerter Notifies selected users and computers of Yes Programs that use administrative Disable administrative alerts alerts will not receive them. Application Provides support for application-level Maybe Programs that rely on this service, Enable Only enable when using Layer protocol plug-ins and enables such as MSN Messenger and the Windows firewall or Gateway network/protocol connectivity Windows Messenger will not another firewall. Failure function. to do so can result in a significant security hole. Application Processes installation, removal, and Yes Users will be unable to install, Disable Management enumeration requests for Active Directory remove, or enumerate any IntelliMirror group policy programs IntelliMirror programs. Automatic Enables the download and installation of Yes The operating system cannot Enable Automatic updates help Updates critical Windows updates automatically install updates, but keep your computer can still be manually updated at the current. -
![[MS-DCLB]: Desktop Clipboard Protocol](https://docslib.b-cdn.net/cover/4686/ms-dclb-desktop-clipboard-protocol-6004686.webp)
[MS-DCLB]: Desktop Clipboard Protocol
[MS-DCLB]: Desktop Clipboard Protocol Intellectual Property Rights Notice for Open Specifications Documentation . Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages, standards as well as overviews of the interaction among each of these technologies. Copyrights. This documentation is covered by Microsoft copyrights. Regardless of any other terms that are contained in the terms of use for the Microsoft website that hosts this documentation, you may make copies of it in order to develop implementations of the technologies described in the Open Specifications and may distribute portions of it in your implementations using these technologies or your documentation as necessary to properly document the implementation. You may also distribute in your implementation, with or without modification, any schema, IDL’s, or code samples that are included in the documentation. This permission also applies to any documents that are referenced in the Open Specifications. No Trade Secrets. Microsoft does not claim any trade secret rights in this documentation. Patents. Microsoft has patents that may cover your implementations of the technologies described in the Open Specifications. Neither this notice nor Microsoft's delivery of the documentation grants any licenses under those or any other Microsoft patents. However, a given Open Specification may be covered by Microsoft Open Specification Promise or the Community Promise. If you would prefer a written license, or if the technologies described in the Open Specifications are not covered by the Open Specifications Promise or Community Promise, as applicable, patent licenses are available by contacting [email protected]. Trademarks. The names of companies and products contained in this documentation may be covered by trademarks or similar intellectual property rights. -

Windows XP Pocket Reference 1
I l@ve RuBoard • Table of Contents • Reviews • Reader Reviews • Errata Windows XP Pocket Reference By David A. Karp Publisher : O'Reilly Pub Date : December 2002 ISBN : 0-596-00425-7 Pages : 188 Windows XP Pocket Reference is a handy book for power users and system administrators who need a solid reference with quick answers, but not a lot of explanation. This book is a powerful tool that quickly covers XP's applications and tools, tasks and settings, and commands. I l@ve RuBoard 1 / 182 I l@ve RuBoard • Table of Contents • Reviews • Reader Reviews • Errata Windows XP Pocket Reference By David A. Karp Publisher : O'Reilly Pub Date : December 2002 ISBN : 0-596-00425-7 Pages : 188 Copyright Chapter 1. Introduction Section 1.1. Conventions Used in This Book Section 1.2. A Crash Course in the Basics of Windows XP Chapter 2. Shortcuts Section 2.1. Working with Files Section 2.2. Helpful Explorer Keystrokes Section 2.3. Keyboard Accelerators Listed by Function Section 2.4. Keyboard Accelerators Listed by Key Chapter 3. Components Accessibility Options Accessibility Wizard Activate Windows Active Connections Utility Add Hardware Wizard Add or Remove Programs Address Book At Attrib Backup Boot Configuration Manager Calculator Character Map Chkdsk Clipbook Viewer Command Prompt Control Panel Create Shared Folder Date and Time Device Manager Disk Cleanup Disk Defragmenter DiskPart Display Properties DriverQuery FAT to NTFS Conversion Utility Fax Console Fax Cover Page Editor File Compare (comp) File Compare (fc) File and Settings Transfer Wizard -

Windows XP.Pdf
ð£ì 1 M«ì£v âvd - å¼ º¡Â¬ó (An Intruduction to Windows XP) 1.1 M«ì£v âvd â¡ð¶ â¡ù? M«ì£v âvd ¹ªó£çðûù â¡ð¶ âõ¼ âOî£è ðò¡ð´¶õîªèù õ®õ¬ñèðì æ Þòè º¬ø¬ñ (Op- erating System) Ý°. M«ì£¬ú ðò¡ð´¶õF à÷ Iè ¾ ºAòñ£ù ÜÂÃô, T»ä (GUI - Graphical User Interface - GOOYEE âù àêKè ð´Aø¶) âùð´ Üî¡ õ¬óè¬ô Þ¬ì ºè Ý°. ñQî ͬ÷J¡ Þìð°F» õôð°F» Þ¼«õÁ Fø¡ªðø¬õ â¡Á è¼îð´Aø¶. Þìðè ͬ÷, ðìè¬÷ ¹K¶ ªè£õF Fø¡ ªðø¶; ð¬ìð£è Cî¬ùèO¡ Hø Hìñ£è M÷°õ¶; àÀíõ£ àîð´ âíèO¡ Þ¼ Hìñ£è Fèõ¶. õôðè ͬ÷«ò£ î¼èº¬ø Cî¬ùèO (Logical Thinking) Cø¶ M÷°Aø¶. T»ä-Þ¡ ÜPºè¶° º¡¹, èEªð£PJ¡ Þòè º¬ø¬ñJ ðEò£Pòõè ªð¼ 𣽠Þìðè ͬ÷¬ò ñ´«ñ ðò¡ð´Fù£è â¡Á õô ðè ͬ÷¬ò õ£÷£ ¬õF¼îù â¡Á ïðð´Aø¶. M «ì£v Þòè º¬ø¬ñ, Þìðè ͬ÷¬ò» õôðè ͬ÷ ¬ò» 弫êó ðò¡ð´F ªè£Aø¶ âù è¼îð´Aø¶. âFó¶ì¡ ªî£ì¹ªè£÷ Þ¬ìºè àî¾Aø¶. à¬ñ J Þ¬ìºè â¡ð¶ Þ¼«õÁ ༪ð£¼èÀ° (Entities) Þ¬ì «òò£ù ªñGè Þ¬í¹ (Virtual Connection) Ý°. â´¶ è£ì£è, ¯M ªî£¬ôM (TV Remote) â¡ð¶ ðòù¬ó» ¯M¬ò » Þ¬í° æ Þ¬ìºè Ý°. ââv-ì£v (MS-DOS) àðì ªð¼ð£ô£ù Þòè º¬ø¬ñè èì¬÷ õK Þ¬ì ºè¬î«ò (Command Line Interface) ðò¡ð´¶A¡øù. -

February 2010
Lorain County Computer Users Group www.LCCUG.com [email protected] Volume 22 Number 2 February 2010 Tuesday February 9, 2010 Inside This Issue Digital Books - President’s Letter Pg 2 What is all the Fuss LCCUG Officers List Pg 2 About? February Programs Pg 3 Minutes Pg 4 Presented by Genealogy Pg 5 Sandee Ruth Windows XP… Pg 6 LCCUG President Windows Vista… Pg 8 Treasurer’s Report Pg 9 Need Help Pg 10 Classes, Workshops & SIGs Pg 10,11 Tuesday Windows 7… Pg 12 February 23, 2010 Reader’s Tips Pg 13 Finding Help In Windows Pg 14 Networking for Dummies Part 1.. Pg 16 Computer Networking for Dummies Part 2… Pg 18 Tweaks Tips, Fun Facts, & Terms Pg 19 Presented by Map Pg 20 Carl Sloan & Lloyd Libengood of Discount Computer Parts Monthly Meetings Held At Gould Auditorium 2 nd Floor, St. Joseph Community Center, Lorain, OH 5:30 PM Doors Open With Outer Lobby Q & A Sessions 6:45 PM Meeting & Presentation Begins A Word From LCCUG Officers For 2010 Our President Sandee Ruth President [email protected] Why I love digital pictures… Lou Koch Vice President [email protected] Try as I might, I have not been able to get comfortable Don Hall using the settings on my digital camera beyond ―auto‖. Secretary Someday I’d like to master that but for now, I am enjoy- [email protected] ing digital photography. Micky Knickman Treasurer [email protected] The wonder of a digital camera is the ability to take LOTS of pictures and not worrying what is it going to Newsletter Pam Rihel cost to develop them. -
Windows XP Pocket Reference by David A
I l@ve RuBoard • Table of Contents • Reviews • Reader Reviews • Errata Windows XP Pocket Reference By David A. Karp Publisher : O'Reilly Pub Date : December 2002 ISBN : 0-596-00425-7 Pages : 188 Windows XP Pocket Reference is a handy book for power users and system administrators who need a solid reference with quick answers, but not a lot of explanation. This book is a powerful tool that quickly covers XP's applications and tools, tasks and settings, and commands. I l@ve RuBoard I l@ve RuBoard • Table of Contents • Reviews • Reader Reviews • Errata Windows XP Pocket Reference By David A. Karp Publisher : O'Reilly Pub Date : December 2002 ISBN : 0-596-00425-7 Pages : 188 Copyright Chapter 1. Introduction Section 1.1. Conventions Used in This Book Section 1.2. A Crash Course in the Basics of Windows XP Chapter 2. Shortcuts Section 2.1. Working with Files Section 2.2. Helpful Explorer Keystrokes Section 2.3. Keyboard Accelerators Listed by Function Section 2.4. Keyboard Accelerators Listed by Key Chapter 3. Components Accessibility Options Accessibility Wizard Activate Windows Active Connections Utility Add Hardware Wizard Add or Remove Programs Address Book At Attrib Backup Boot Configuration Manager Calculator Character Map Chkdsk Clipbook Viewer Command Prompt Control Panel Create Shared Folder Date and Time Device Manager Disk Cleanup Disk Defragmenter DiskPart Display Properties DriverQuery FAT to NTFS Conversion Utility Fax Console Fax Cover Page Editor File Compare (comp) File Compare (fc) File and Settings Transfer Wizard Folder