File Power Folder and Move Files to It Instead of Using Rm Or Rmdir
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

GNU CPIO GNU Cpio 2.5 June 2002
GNU CPIO GNU cpio 2.5 June 2002 by Robert Carleton Copyright c 1995, 2001, 2002 Free Software Foundation, Inc. This is the first edition of the GNU cpio documentation, and is consistent with GNU cpio 2.5. Published by the Free Software Foundation 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this manual under the con- ditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this manual into another lan- guage, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Chapter 2: Tutorial 1 1 Introduction GNU cpio copies files into or out of a cpio or tar archive, The archive can be another file on the disk, a magnetic tape, or a pipe. GNU cpio supports the following archive formats: binary, old ASCII, new ASCII, crc, HPUX binary, HPUX old ASCII, old tar, and POSIX.1 tar. The tar format is provided for compatability with the tar program. By default, cpio creates binary format archives, for compatibility with older cpio programs. When extracting from archives, cpio automatically recognizes which kind of archive it is reading and can read archives created on machines with a different byte-order. -

Real Time Operating Systems Rootfs Creation: Summing Up
Real Time Operating Systems RootFS Creation: Summing Up Luca Abeni Real Time Operating Systems – p. System Boot System boot → the CPU starts executing from a well-known address ROM address: BIOS → read the first sector on the boot device, and executes it Bootloader (GRUB, LILO, U-Boot, . .) In general, load a kernel and an “intial ram disk” The initial fs image isn’t always needed (example: netboot) Kernel: from arm-test-*.tar.gz Initial filesystem? Loaded in RAM without the kernel help Generally contains the boot scripts and binaries Real Time Operating Systems – p. Initial Filesystem Old (2.4) kernels: Init Ram Disk (initrd); New (2.6) kernels: Init Ram Filesystem (initramfs) Generally used for modularized disk and FS drivers Example: if IDE drivers and Ext2 FS are modules (not inside the kernel), how can the kernel load them from disk? Solution: boot drivers can be on initrd / initramfs The bootloader loads it from disk with the kernel The kernel creates a “fake” fs based on it Modules are loaded from it Embedded systems can use initial FS for all the binaries Qemu does not need a bootloader to load kernel and initial FS (-kernel and -initrd) Real Time Operating Systems – p. Init Ram Filesystem Used in 2.6 kernels It is only a RAM FS: no real filesystem metadata on a storage medium All the files that must populate the FS are stored in a cpio package (similar to tar or zip file) The bootloader loads the cpio file in ram At boot time, the kernel “uncompresses” it, creating the RAM FS, and populating it with the files contained in the archive The cpio archive can be created by using the cpio -o -H newc command (see man cpio) Full command line: find . -

Working with Compressed Archives
Working with compressed archives Archiving a collection of files or folders means creating a single file that groups together those files and directories. Archiving does not manipulate the size of files. They are added to the archive as they are. Compressing a file means shrinking the size of the file. There are software for archiving only, other for compressing only and (as you would expect) other that have the ability to archive and compress. This document will show you how to use a windows application called 7-zip (seven zip) to work with compressed archives. 7-zip integrates in the context menu that pops-up up whenever you right-click your mouse on a selection1. In this how-to we will look in the application interface and how we manipulate archives, their compression and contents. 1. Click the 'start' button and type '7-zip' 2. When the search brings up '7-zip File Manager' (as the best match) press 'Enter' 3. The application will startup and you will be presented with the 7-zip manager interface 4. The program integrates both archiving, de/compression and file-management operations. a. The main area of the window provides a list of the files of the active directory. When not viewing the contents of an archive, the application acts like a file browser window. You can open folders to see their contents by just double-clicking on them b. Above the main area you have an address-like bar showing the name of the active directory (currently c:\ADG.Becom). You can use the 'back' icon on the far left to navigate back from where you are and go one directory up. -

Z/VM Version 7 Release 2
z/VM Version 7 Release 2 OpenExtensions User's Guide IBM SC24-6299-01 Note: Before you use this information and the product it supports, read the information in “Notices” on page 201. This edition applies to Version 7.2 of IBM z/VM (product number 5741-A09) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2020-09-08 © Copyright International Business Machines Corporation 1993, 2020. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................. xi Tables................................................................................................................ xiii About this Document........................................................................................... xv Intended Audience..................................................................................................................................... xv Conventions Used in This Document......................................................................................................... xv Escape Character Notation................................................................................................................... xv Case-Sensitivity.....................................................................................................................................xv Typography............................................................................................................................................xv -

Backing up Data
Backing up data On LINUX and UNIX Logical backup • Why? Job security • For user data. • Remember endian order, character set issues. • Full backup + incremental = backup set No differential (see find command). • Backup without a restore test is just a tape • mt or rmt used for generic tape management. See mt, rmt manpage. See /dev/rmt0 • See text for CD/DVD procedures • Use commercial products for business. Why? Tape catalog management. Backup Commands • cp (duh) • ftp (eh) • rcp (no, no, no) • scp • rsync • tar • cpio • pax (see cpio, tar) • dump/restore – the standard The usual suspects • cp –rp source destination • ftp hostname user name cd source or destination lcd destination/source put/get filename quit • scp source user@destination:/pathtofile scp user@source:/pathtofile /destination • rcp source user@destination:/pathtofile rcp user@ source:/pathtofile /destination uses .rhosts see manpage on hosts.equiv rsync • Support from rsync.samba.org • rsync copies files either to or from a remote host, or locally on the current host but does not support copying files between two remote hosts. • rsync can reduce the amount of data sent over the network by sending only the differences between the source files and the existing files in the destination. • There are two different ways for rsync to contact a remote system: using a remote- shell program as the transport (such as ssh or rsh) or contacting an rsync daemon directly via TCP. See the manpage on rsyncd.conf. • rsync –avh /source /destination • rsync -avze ssh /home/user/directory/ user@remotehost:home/user/directory/ • Other Options -a, --archive archive mode; equals -r, --recursive recurse into directories -u, --update skip files that are newer on the receiver Tape ARchive • Most portable backup utility between systems. -

Proceedings of the 17 Large Installation Systems Administration
USENIX Association Proceedings of the 17th Large Installation Systems Administration Conference San Diego, CA, USA October 26–31, 2003 THE ADVANCED COMPUTING SYSTEMS ASSOCIATION © 2003 by The USENIX Association All Rights Reserved For more information about the USENIX Association: Phone: 1 510 528 8649 FAX: 1 510 548 5738 Email: [email protected] WWW: http://www.usenix.org Rights to individual papers remain with the author or the author's employer. Permission is granted for noncommercial reproduction of the work for educational or research purposes. This copyright notice must be included in the reproduced paper. USENIX acknowledges all trademarks herein. Further Torture: More Testing of Backup and Archive Programs Elizabeth D. Zwicky ABSTRACT Every system administrator depends on some set of programs for making secondary copies of data, as backups for disaster recovery or as archives for long term storage. These programs, like all other programs, have bugs. The important thing for system administrators to know is where those bugs are. Some years ago I did testing on backup and archive programs, and found that failures were extremely common and that the documented limitations of programs did not match their actual limitations. Curious to see how the situation had changed, I put together a new set of tests, and found that programs had improved significantly, but that undocumented failures were still common. In the previous tests, almost every program crashed outright at some point, and dump significantly out-performed all other contenders. In addition, many programs other than the backup and archive programs failed catastrophically (most notably fsck on many platforms, and the kernel on one platform). -

12.1 Introduction 12.2 Tar Command
12.1 Introduction Linux distributions provide several different sets of commands for compressing and archiving files and directories. This chapter will describe their advantages and disadvantages as well as their usefulness in making backup copies of files and directories efficiently. More sophisticated types of copying, using the dd and cpio commands, will also be covered. These commands, while more complex, offer powerful features. 12.2 tar Command An archive is a single file, which consists of many files, though not necessarily compressed. The tar command is typically used to make archives within Linux. These tar archive files, sometimes called tarballs, were originally used to backup data onto magnetic tape. Tar is derived from the words "tape archive". While the primary purpose of the tar command is to merge multiple files into a single file, it is capable of many different operations and there are numerous options. The functionality of the tar command can be broken down into three basic functions: creating, viewing and extracting archives. The tar command accepts all three styles of options (x, -x, --extract) as parameters. Do not be surprised to see it used with options that have no hyphens (BSD style), a single hyphen (UNIX style) or two hyphens (GNU style). The tar command originally did not support compression, but a newer version that was developed by the GNU project supports both gzip and bzip2compression. Both of these compression schemes will be presented later in this chapter. To use gzip compression with the tar command, use the -z option. To use bzip2 compression, use the -j option. -

MBS Compression Plugin.Pdf
MBS Compression Plugin Documentation Christian Schmitz September 6, 2021 2 0.1 Introduction This is the PDF version of the documentation for the Xojo Plug-in from Monkeybread Software Germany. Plugin part: MBS Compression Plugin 0.2 Content • 1 List of all topics 3 • 2 List of all classes 29 • 3 List of all modules 31 • 4 List of all global methods 33 • 5 All items in this plugin 35 • 8 List of Questions in the FAQ 225 • 9 The FAQ 235 Chapter 1 List of Topics • 5 Archive 35 – 5.1.1 class ArchiveEntryMBS 35 ∗ 5.1.7 Clear 36 ∗ 5.1.8 ClearACL 36 ∗ 5.1.9 ClearXAttr 36 ∗ 5.1.10 Clone as ArchiveEntryMBS 36 ∗ 5.1.11 Constructor 37 ∗ 5.1.12 Constructor(Archive as ArchiverMBS) 37 ∗ 5.1.13 Destructor 37 ∗ 5.1.14 GetFFlags(byref FlagsSet as UInt64, byref FlagsClear as UInt64) 37 ∗ 5.1.15 SetFFlags(FlagsSet as UInt64, FlagsClear as UInt64) 37 ∗ 5.1.16 SetLink(link as string) 37 ∗ 5.1.17 UnsetATime 38 ∗ 5.1.18 UnsetBTime 38 ∗ 5.1.19 UnsetCTime 38 ∗ 5.1.20 UnsetGName 38 ∗ 5.1.21 UnsetHardLink 38 ∗ 5.1.22 UnsetMTime 38 ∗ 5.1.23 UnsetPathName 39 ∗ 5.1.24 UnsetSize 39 ∗ 5.1.25 UnsetSymLink 39 ∗ 5.1.26 UnsetUName 39 ∗ 5.1.28 ADateTime as DateTime 39 ∗ 5.1.29 ATime as Date 40 ∗ 5.1.30 ATimeSet as Boolean 40 ∗ 5.1.31 BDateTime as DateTime 40 ∗ 5.1.32 BTime as Date 40 3 4 CHAPTER 1. LIST OF TOPICS ∗ 5.1.33 BTimeSet as Boolean 40 ∗ 5.1.34 CDateTime as DateTime 41 ∗ 5.1.35 CTime as Date 41 ∗ 5.1.36 CTimeSet as Boolean 41 ∗ 5.1.37 Dev as Integer 41 ∗ 5.1.38 DevMajor as Integer 41 ∗ 5.1.39 DevMinor as Integer 42 ∗ 5.1.40 DevSet as Boolean 42 ∗ 5.1.41 FFlags as -

Freebsd General Commands Manual BSDCPIO (1)
BSDCPIO (1) FreeBSD General Commands Manual BSDCPIO (1) NAME cpio —copyfiles to and from archives SYNOPSIS cpio { −i}[options][pattern . ..][<archive] cpio { −o}[options] <name-list [>archive] cpio { −p}[options] dest-dir < name-list DESCRIPTION cpio copies files between archivesand directories. This implementation can extract from tar,pax, cpio, zip, jar,ar, and ISO 9660 cdrom images and can create tar,pax, cpio, ar,and shar archives. The first option to cpio is a mode indicator from the following list: −i Input. Read an archive from standard input (unless overriden) and extract the contents to disk or (if the −t option is specified) list the contents to standard output. If one or more file patterns are specified, only files matching one of the patterns will be extracted. −o Output. Read alist of filenames from standard input and produce a newarchive onstandard output (unless overriden) containing the specified items. −p Pass-through. Read alist of filenames from standard input and copythe files to the specified direc- tory. OPTIONS Unless specifically stated otherwise, options are applicable in all operating modes. −0 Read filenames separated by NUL characters instead of newlines. This is necessary if anyofthe filenames being read might contain newlines. −A (o mode only) Append to the specified archive.(Not yet implemented.) −a (o and p modes) Reset access times on files after theyare read. −B (o mode only) Block output to records of 5120 bytes. −C size (o mode only) Block output to records of size bytes. −c (o mode only) Use the old POSIX portable character format. Equivalent to −-format odc. -
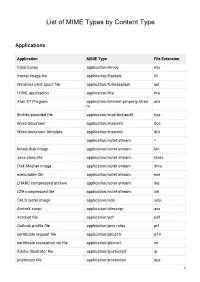
List-Of-Mime-Types-By-Content-Type.Pdf
List of MIME Types by Content Type Applications Application MIME Type File Extension Corel Envoy application/envoy evy fractal image file application/fractals fif Windows print spool file application/futuresplash spl HTML application application/hta hta Atari ST Program application/internet-property-strea acx m BinHex encoded file application/mac-binhex40 hqx Word document application/msword doc Word document template application/msword dot application/octet-stream * binary disk image application/octet-stream bin Java class file application/octet-stream class Disk Masher image application/octet-stream dms executable file application/octet-stream exe LHARC compressed archive application/octet-stream lha LZH compressed file application/octet-stream lzh CALS raster image application/oda oda ActiveX script application/olescript axs Acrobat file application/pdf pdf Outlook profile file application/pics-rules prf certificate request file application/pkcs10 p10 certificate revocation list file application/pkix-crl crl Adobe Illustrator file application/postscript ai postscript file application/postscript eps 1 postscript file application/postscript ps rich text format file application/rtf rtf set payment initiation application/set-payment-initiation setpay set registration initiation application/set-registration-initiatio setreg n Excel Add-in file application/vnd.ms-excel xla Excel chart application/vnd.ms-excel xlc Excel macro application/vnd.ms-excel xlm Excel spreadsheet application/vnd.ms-excel xls Excel template application/vnd.ms-excel -

Z/VM Version 7 Release 2
z/VM Version 7 Release 2 OpenExtensions Commands Reference IBM SC24-6297-01 Note: Before you use this information and the product it supports, read the information in “Notices” on page 547. This edition applies to Version 7.2 of IBM z/VM (product number 5741-A09) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2020-12-02 © Copyright International Business Machines Corporation 1993, 2020. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................. ix Tables.................................................................................................................. xi About This Document..........................................................................................xiii Intended Audience.................................................................................................................................... xiii Conventions Used in This Document........................................................................................................ xiii Escape Character Notation.................................................................................................................. xiii Case-Sensitivity....................................................................................................................................xiii Typography...........................................................................................................................................xiii -

MIME Types MIME Content-Types Supported by Most Web Servers, Identified with File Extensions, Are Listed in the Following Table
MIME Types MIME content-types supported by most web servers, identified with file extensions, are listed in the following table. MIME Tpe Identification File Extension application/acad AutoCAD dwg application/arj compressed archive arj application/astound Astound asd, asn application/clariscad ClarisCAD ccad application/drafting MATRA Prelude drafting drw application/dxf DXF (AutoCAD) dxf application/i-deas SDRC I-DEAS unv application/iges IGES graphics format iges, igs application/java-archive Java archive jar application/mac-binhex40 Macintosh binary BinHex 4.0 hqx application/msaccess Microsoft Access mdb application/msexcel Microsoft Excel xla, xls, xlt, xlw application/mspowerpoint Microsoft PowerPoint pot, pps, ppt application/msproject Microsoft Project mpp application/msword Microsoft Word doc, word, w6w application/mswrite Microsoft Write wri application/octet-stream uninterpreted binary bin application/oda ODA oda application/pdf Adobe Acrobat pdf application/postscript PostScript ai, eps, ps application/pro_eng PTC Pro/ENGINEER part, prt application/rtf Rich Text Format rtf application/set SET (French CAD) set application/sla stereolithography stl application/solids MATRA Prelude Solids sol application/STEP ISO-10303 STEP data st, step, stp application/vda VDA-FS Surface data vda application/x-bcpio binary CPIO bcpio application/x-cpio POSIX CPIO cpio application/x-csh C-shell script csh application/x-director Macromedia Director dcr, dir, dxr application/x-dvi TeX DVI dvi application/x-dwf AutoCAD dwf application/x-gtar GNU