The Spyware Used in Intimate Partner Violence
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
The Impact of Parental Involvement, Parental Support and Family Education on Pupil Achievements and Adjustment: a Literature Review
RESEARCH The Impact of Parental Involvement, Parental Support and Family Education on Pupil Achievements and Adjustment: A Literature Review Professor Charles Desforges with Alberto Abouchaar Research Report RR433 Research Report No 433 THE IMPACT OF PARENTAL INVOLVEMENT, PARENTAL SUPPORT AND FAMILY EDUCATION ON PUPIL ACHIEVEMENT AND ADJUSTMENT: A LITERATURE REVIEW Professor Charles Desforges with Alberto Abouchaar The views expressed in this report are the authors' and do not necessarily reflect those of the Department for Education and Skills. © Queen’s Printer 2003 ISBN 1 84185 999 0 June 2003 1 Acknowledgements This report was compiled in a very short time thanks to the invaluable help given generously by a number of workers in the field. Outstanding amongst these were Mike Gasper, John Bastiani, Jane Barlow, Sheila Wolfendale and Mary Crowley. I am most grateful for their collegial participation. Most important of all to a review are those who work in the engine room. The search, identification, collection and collation of material and the production aspects of the report are critical. Special thanks are due here to Anne Dinan in the University of Exeter Library, Finally, this work would not have been possible without the limitless support of Zoë Longridge-Berry whom I cannot thank enough. 2 Contents Chapter 1 Introduction 1 Chapter 2 Researching parental involvement: 6 some conceptual and methodological issues Chapter 3 The impact of parental involvement 17 on achievement and adjustment Chapter 4 How does parental involvement work? -

Dealing with Digital Distractions Full Disclosure Lets Crush the Critic
By Adam Schwebach, Ph.D. Dealing with Digital Distractions Copyright 2018 Adam J. Schwebach,Ph.D. Full Disclosure ❖ I am NOT a perfect parent ❖ I am a Pediatric Neuropsychologist ❖ When it comes to raising children, I have the same fears, worries and concerns you do Copyright 2018 Adam J. Schwebach, Ph.D. Lets Crush the Critic ❖ Technology is NOT bad ❖ The human species has always been “advancing” ❖ Like all technological advances, there comes unforeseen consequences and challenges ❖ One must be aware of the potential dangers and pitfalls and discover ways to address those issues Copyright 2018 Adam J. Schwebach, Ph.D. Technological Advances that Have Changed Mankind Forever ❖ Electricity ❖ Plastic ❖ Automobile ❖ Airplanes ❖ Microchip ❖ TV ❖ Internet ❖ Mobile Technology (i.e., cell phones) Copyright 2018 Adam J. Schwebach, Ph.D. Lets Talk About Mobile Technology Copyright 2018 Adm J. Schwebach, Ph.D. History of Cell Phones Copyright 2018 Adam J. Schwebach, Ph.D. 1G Phones Copyright 2018 Adam J. Schwebach, Ph.D. 1973 First Cell phone Call by Dr. Cooper Copyright 2018 Adam J. Schwebach, Ph.D. 2G Phones Copyright 2018 Adam J. Schwebach, Ph.D. 2G Phones ❖ In the 1990’s technology advances from “analog” to “digital” ❖ Instead of just being able to make phone calls, digital technology allows people to transmit “data” ❖ In 1993, the first mobile to mobile text message is sent in in Finland Copyright 2018 Adam J. Schwebach, Ph.D. 3G Phones ❖ Increase in band width and mobile storage allows for quicker speeds, live streaming and the ability to “download” data onto a mobile device Copyright 2018 Adam J. -

Mcafee Potentially Unwanted Programs (PUP) Policy March, 2018
POLICY McAfee Potentially Unwanted Programs (PUP) Policy March, 2018 McAfee recognizes that legitimate technologies such as commercial, shareware, freeware, or open source products may provide a value or benefit to a user. However, if these technologies also pose a risk to the user or their system, then users should consent to the behaviors exhibited by the software, understand the risks, and have adequate control over the technology. McAfee refers to technologies with these characteristics as “potentially unwanted program(s),” or “PUP(s).” The McAfee® PUP detection policy is based on the process includes assessing the risks to privacy, security, premise that users should understand what is being performance, and stability associated with the following: installed on their systems and be notified when a ■ Distribution: how users obtain the software including technology poses a risk to their system or privacy. advertisements, interstitials, landing-pages, linking, PUP detection and removal is intended to provide and bundling notification to our users when a software program or technology lacks sufficient notification or control over ■ Installation: whether the user can make an informed the software or fails to adequately gain user consent to decision about the software installation or add- the risks posed by the technology. McAfee Labs is the ons and can adequately back out of any undesired McAfee team responsible for researching and analyzing installations technologies for PUP characteristics. ■ Run-Time Behaviors: the behaviors exhibited by the technology including advertisements, deception, and McAfee Labs evaluates technologies to assess any impacts to privacy and security risks exhibited by the technology against the degree of user notification and control over the technology. -

Of What We Want the Cross-Platform Report June 2014
MORE OF WHAT WE WANT THE CROSS-PLATFORM REPORT JUNE 2014 Copyright © 2014 The Nielsen Company THE CROSS-PLATFORM SERIES | Q1 2014 weLCOME Today’s viewers are making device and platform choices that have a profound impact on the meaning of television and video. This May we witnessed a great transformation during a traditionally television- centric time of the year. Referred to as the Upfront, TV networks showcase their fall shows and highlight what American consumers’ love: content. The Upfront draws the interest of advertisers and media networks as they engage in an elaborate negotiation and collaboration around the buying and selling of advertising inventory for the coming season. This year was different. Early conversations around time-shifting and digital became very real. Upfront talks around shifting some deals from Live+3 days to Live+7 days, digital rights, DOUNIA TURRILL and programmatic buying, have those of us in the media and advertising industry SVP INSIGHTS, NIELSEN on the edge of our seats. Just as cable networks entered the Upfront fanfare a few years back, digital publishers, who have for the past couple of years showcased themselves in the Newfronts, came out strong. Capturing the attention of Millennials in growing numbers, these agile powerhouses challenge the media landscape. And, at the risk of being repetitive, the American consumer has never before engaged with more content across media type, media devices and content type. THE VIDeo VIEWING CURVE coNTINUES to GROW AS DELIVERY AND EXploratioN OF coNTENT coNTINUES to EXpaND. Understanding, defining and measuring this curve matters to our clients. Time- shifting allows us to watch more content, video on demand allows us to watch more content, and digital delivery allows us to watch more content. -

The Social TV Viewer
The Social TV Viewer An explorative study of the viewing behavior associated with synchronous social TV DON MICHAEL GRABEN Master of Science Thesis Stockholm, Sweden 2013 The Social TV Viewer An explorative study of the viewing behavior associated with synchronous social TV DON MICHAEL GRABEN DM228X, Master’s Thesis in Media Technology (30 ECTS credits) Degree Progr. in Media Technology 270 credits Royal Institute of Technology year 2013 Supervisor at CSC was Pernilla Josefsson Examiner was Stefan Hrastinski TRITA-CSC-E 2013:003 ISRN-KTH/CSC/E--13/003--SE ISSN-1653-5715 Royal Institute of Technology School of Computer Science and Communication KTH CSC SE-100 44 Stockholm, Sweden URL: www.kth.se/csc The Social TV Viewer An Explorative Study of the Viewing Behavior Associated with Synchronous Social TV Abstract This thesis is a qualitative study conducted for Ericsson ConsumerLab which explores the phenomenon of Social TV consumption from the perspective of its adopters. Through a series of in-depth interviews it explores the phenomenon, investigating both how and why TV consumers are using social media to talk about TV content while watching it. The findings of this thesis include numerous insights about the viewing behavior associated with synchronous Social TV, covering several different aspects: Driving forces, the context in which Social TV viewing takes place, the features of the content being consumed, with whom and how Social TV viewers are interacting with each other, identified barriers and needs, as well as perceived effects on the TV viewing experience. It becomes evident that TV viewers consider the act of watching TV as a highly social activity, seeking to share it with other like-minded individuals, using social media to recreate the experience of watching together as a co-located group. -

Exploring Social Media Scenarios for the Television
Exploring Social Media Scenarios for the Television Noor F. Ali-Hasan Microsoft 1065 La Avenida Street Mountain View, CA 94043 [email protected] Abstract social media currently fits in participants‟ lives, gauge their The use of social technologies is becoming ubiquitous in the interest in potential social TV features, and understand lives of average computer users. However, social media has their concerns for such features. This paper discusses yet to infiltrate users‟ television experiences. This paper related research in combining TV and social technologies, presents the findings of an exploratory study examining presents the study‟s research methods, introduces the social scenarios for TV. Eleven participants took part in the participants and their defining characteristics, and three-part study that included in-home field visits, a diary summarizes the study‟s findings in terms of the study of participants‟ daily usage of TV and social media, participants‟ current TV and social media usage and their and participatory design sessions. During the participatory interest in social scenarios for the TV. design sessions, participants evaluated and discussed several paper wireframes of potential social TV applications. Overall, participants responded to most social TV concepts with excitement and enthusiasm, but were leery of scenarios Related Work that they felt violated their privacy. In recent years, a great deal of research has been conducted around the use of blogs and online social networks. Studies exploring social television applications have been Introduction fewer in number, likely due to the limited availability of Whether in the form of blogs or online social networks, such applications in consumers‟ homes. -

Florida Units 1–6
Level 1 Florida Units 1–6 STUDENT BOOK Lesson 1 | Reading Louisa Moats, Ed.D., Author Interesting REVIEWER’SInsects DRAFT Mosquitoes can live in very cold places. So Many Insects! What is the largest group of animals in the world? It’s insects! About 900,000 species of insects have been discovered so far. Scientists think that millions more are yet to be found. Here are a few interesting insects. connect An Insect Helper join together; unite 5 Ladybugs are tiny beetles. They are less than half an inch long. Many ladybugs have redconnect or orange to wing two cases and dark spots. The wing cases wings. They cover the wings when the ladybug is not flying. , some people think ladybugs 10 Out of ignorance hurt crops. However, that is not true. Ladybugs eat other insects. Those insects would destroy plants. This includes the sap-sucking aphids. Ladybugs are cute, and they help gardeners! A ladybug may eat up An Insect Hunter to 60 aphids a day. 15 A praying mantis is a strong, clever insect. Its name comes from the way it holds its front legs. They ignorance are folded. It looks like it is praying. It looks like it lack of knowledge would not hurt a fly. Yet, it is a strong predator. It has sharp spines on its front legs. These spines stick and 20 hold its prey. 4 Unit 1 Level 1 Fl ida Units 1–6 STUDENT BOOK Louisa Moats, Ed.D., Author Lesson 1 | Reading Interesting Insects Mosquitoes can live in very cold places. -

(Malicious Software) Installed on Your Computer Without Your Consent to Monitor Or Control Your Computer Use
Spyware is a type of malware (malicious software) installed on your computer without your consent to monitor or control your computer use. Clues that spyware is on a computer may include a barrage of pop-ups, a browser that takes you to sites you don't want, unexpected toolbars or icons on your computer screen, keys that don't work, random error messages, and sluggish performance when opening programs or saving files. In some cases, there may be no symptoms at all. While the term spyware suggests that software that secretly monitors the user's computing, the functions of spyware extend well beyond simple monitoring. Spyware programs can: Collect information stored on the computer or attached network drives, Collect various types of personal information, such as Internet surfing habits, sites that have been visited Collect user names and passwords stored on your computer as well as those entered from the keyboard. Interfere with user control of the computer Install additional software on the computer Redirect Web browser activity. Change computer settings, resulting in slow connection speeds, different home pages, and/or loss of Internet or functionality of other programs. The best defense against spyware and other unwanted software is not to download it in the first place. Here are a few helpful tips that can protect you from downloading software you don't want: Update your operating system and Web browser software, and set your browser security high enough to detect unauthorized downloads. Use anti-virus and anti-spyware, as well as a firewall software, and update them all regularly. -

Welcome to the Jungle:1 the State Privacy Implications of Spam, Phishing and Spyware
February 2005 Welcome to the Jungle:1 The State Privacy Implications of Spam, Phishing and Spyware Section I: An Overview It’s a Jungle Out There: In an environment in which 53% of all reported fraud complaints to the Federal Trade Commission (FTC) in 2004 were Internet-related, the Internet and email threats of spam, phishing and spyware all are real threats with real consequences.2 They are increasingly used by criminals, instead of just novice teenage hackers3 and can be lucrative alone or in furthering a larger criminal enterprise. Armed with these incentives, spammers, phishers and spyware purveyors are motivated and possess the expertise to avoid the attempts of law enforcement, industry and others to bring these threats in hand. Moreover, while banks, financial institutions, ISPs (Internet Service Providers) and even online auction site users have borne the initial brunt of threats like phishing, other sectors are becoming targets as the first wave of targeted sectors puts in place more effective security measures. This could place government and citizen information at risk of unauthorized disclosure and could lead to serious consequences, such as the release of sensitive homeland security and critical infrastructure information or personal information that could result in identity theft. In addition, spam, phishing and spyware infringe upon citizens’ perceived “right to be left alone” while surfing the Internet and using email. The fact that so many individuals’ privacy has been impacted to varying extents by these threats has compounded their significance. For example, a 2004 phishing attack spoofed4 an email from the FDIC (Federal Deposit Insurance Corporation). -

Left to Your Own Devices Understanding Consumption in Today’S Connected World Q4 2018 Contents
VAB - INSIGHTS REPORT 2019 ................. Left To Your Own Devices Understanding Consumption In Today’s Connected World Q4 2018 Contents Summary 3 Media Consumption Overview 4-8 Video Device Segmentation 9-14 4th Quarter Holiday TV Viewing Habits 15-17 Ad-Supported Multiscreen TV Brands 18-23 Cinema Highlight Reel 24-26 Contact Information 27 Appendix I – Major Ethnicities’ Device Usage 28-30 Appendix II – Live vs. Time-Shifted TV Viewing 31-33 2 Summary In our latest quarterly report surveying the video landscape, Left To Your Own Devices, we update the media consumption habits of major demographic segments based on recently released Q4 ’18 data and take a deeper look into TV viewing habits during popular Q4 holidays. Consumers are living in a video world – it accounted for over 50% of the 11+ hours that people spend with media per day in Q4 ‘18 - but it’s important to note that Television reigns as the leader of this world, with “live TV” representing nearly 70% of total video viewing. However, we know that different demographics and people in different life stages may consume media differently than others and these behaviors continue to evolve. In recognition of this, we’ve updated our comprehensive segmentation analysis highlighting the who, what, where, when and how by device, which explores the nuances that exist within the video ecosystem. Although overall time spent with Television (the device) has decreased, as video viewing grows on alternative devices such as connected devices and smartphones, ad-supported multiscreen TV -
75% of Marketers Say SEO Is Content Creation
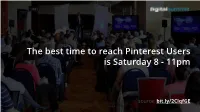
The best time to reach Pinterest Users is Saturday 8 - 11pm source: bit.ly/2CIqfGE Google 'near me' searches doubled in 2017 source: bit.ly/2CUEYOT 71% of marketers believe mobile marketing is core to their business source: bit.ly/2muBZG2 On average, content marketing costs 62% less than traditional marketing (and generates 3x leads) source: bit.ly/2CIqfGE 39% of marketers think their organization's marketing strategy is not effective source: bit.ly/2AG6jzh More than $1B will be spent on Influencer Marketing in 2018 source: bit.ly/2lYBosE 8% of the 200 largest US advertisers have taken media-buying in-house source: bit.ly/2nzPBww 81% reported increased website traffic with as little as 6 hrs/week of social media marketing source: bit.ly/2jpjqwL LinkedIn currently has 3M active job listings source: bit.ly/2lFxxlL Pizza, steak and sushi are the most Instagrammed food source: bit.ly/2hZAI28 200M Instagram users per day visit a business profile source: bit.ly/2owZoWG Spotify has 140M active monthly listeners source: bit.ly/2sHpmce 83% of brands found Facebook Live effective for reaching new audiences source: bit.ly/2irCegl 80% of email users access their email accounts exclusively from their mobile device source: bit.ly/2muBZG2 Highest rank content has an average of 1,200 words source: bit.ly/2kmwUL3 Personalized CTA's lead to 42% more conversions source: bit.ly/2kFqjj0 64% of Pinterest referral traffic comes from mobile & tablet devices source: bit.ly/2muBZG2 80% of users recall a video ad they viewed in the past 30 days source: bit.ly/2kFqjj0 -

Sugary Drinks... Drink Water!
Dear School Leader, Welcome to the 5-2-1-0 Goes to School Toolkit! On behalf of Let’s Move Pittsburgh, we would like to thank you for your interest in starting a 5-2-1-0 program at your school. 5-2-1-0 Goes to School is part of Let’s Move Pittsburgh’s larger effort to lead a 5-2-1-0 initiative in Allegheny County. We are proud to join cities from more than 40 states across the country who have embraced the 5-2-1-0 message as a formula for healthy living. Let’s Move Pittsburgh’s 5-2-1-0 initiative is modeled after 5-2-1-0 Let’s Go!, a nationally recognized program launched in Maine. Let’s Go! focuses on delivering consistent messages of nutritious food choices and active lifestyles to children, families and providers in settings where our children live, learn and grow. For our local initiative, we have adopted or modified Let’s Go!’s materials and generated new resources for you to use in your 5-2-1-0 program. We are thankful for the opportunity to partner with Let’s Go! and work towards our shared vision of raising a healthy generation of kids. Learn more about the original Let’s Go! by visiting www.letsgo.org. The key messages of 5-2-1-0 are 5 servings of fruits and vegetables, 2 hours or less of recreational screen time, at least 1 hour of physical activity and 0 sugary drinks and more water—every day! The 5-2-1-0 Goes to School Toolkit is a step-by-step guide for launching, leading and evaluating your 5-2-1-0 program.