Threats and Risks to Mobile Phone in Japan
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Customising Handset Settings
UG.A1000.book Page 1 Wednesday, September 15, 2004 2:35 PM Welcome Welcome to the world of Motorola digital wireless communications! We are pleased that you have chosen the Motorola A1000 multimedia handset. Camera (Point 2 Point) Two-way video conferencing Earpiece Game Key B Status Light Speakerphone Key Game A Key Navigation Key Push center Touchscreen button left, right, up, or down to move through Send Key items. Press Press to make center button to and answer select voice or video highlighted item. calls. When not in a call, press to End Key display call Press and Triangle Key history. release to end calls and to display phone dial pad. Welcome - 1 UG.A1000.book Page 2 Wednesday, September 15, 2004 2:35 PM www.motorola.com MOTOROLA and the Stylised M Logo are registered in the US Patent & Trademark Office. All other product or service names are the property of their respective owners. The Bluetooth trademarks are owned by their proprietor and used by Motorola, Inc. under licence. © Motorola, Inc. 2004. Software Copyright Notice The Motorola products described in this manual may include copyrighted Motorola and third party software stored in semiconductor memories or other media. Laws in the United States and other countries preserve for Motorola and third party software providers certain exclusive rights for copyrighted software, such as the exclusive rights to distribute or reproduce the copyrighted software. Accordingly, any copyrighted software contained in the Motorola products may not be modified, reverse-engineered, distributed, or reproduced in any manner to the extent allowed by law. -

Symbian in the Enterprise
Symbian in the Enterprise Symbian OS is the world-leading open operating system that powers the most popular and advanced smartphones from the world’s leading handset manufacturers. Symbian OS is the industry's standard choice for smartphones that not only feature calendars, contacts, messaging, push email and web browsing, but can also extend easily to any enterprise information system. Maximize productivity from one converged device Email and messaging – all Symbian OS phones have email Staying connected with colleagues, customers and partners support out of the box. Emails can be composed, read and throughout the day is fundamental to business. Symbian managed offline as well as online. The phone can support OS smartphones for mobile professionals are, first and several email accounts and, depending on available memory, foremost, uncompromised great phones, robust and can store around 1000 emails. Email attachments can be capable, with excellent battery life, size and usability. In viewed using downloadable viewers. Some Symbian OS addition to regular voice, messaging and email, the open phones are supplied with these viewers already installed. nature of Symbian OS phones enables a range of advanced solutions, such as voice conferencing and push-to-talk. Push email – business users can access their full corporate Lotus Notes/Microsoft Exchange email and additionally have it ‘pushed’ to their phone using downloadable applications Extend the phone to any back-end infrastructure from companies such as Intellisync, Smartner, Visto, Symbian’s approach to enterprise connectivity is to ensure Extended Systems, JP Mobile and others. These solutions that Symbian OS phones can be extended to any existing have end-to-end security. -

Mobile Connection Explorer for Windows Introduction and Features
Mobile Connection Explorer 15 May 2013 for Windows Version 21 Introduction and Features Public version Gemfor s.r.o. Tyršovo nám. 600 252 63 Roztoky Czech Republic Gemfor s.r.o. Tyršovo nám. 600 252 63 Roztoky Czech Republic e-mail: [email protected] Contents Contents ...................................................................................................................... 2 History ......................................................................................................................... 3 1. Scope ..................................................................................................................... 3 2. Abbreviations ......................................................................................................... 4 3. Solution .................................................................................................................. 5 4. Specification ........................................................................................................... 5 5. Product description ................................................................................................. 9 5.1 Supported operating systems ....................................................................... 9 5.2 Hardware device connections ....................................................................... 9 5.3 Network connection types ............................................................................. 9 5.4 Customizable graphical skin ...................................................................... -

Radioactive: Enabling Large-Scale Asynchronous Audio Discussions on Mobile Devices
RadioActive: Enabling large-scale asynchronous audio discussions on mobile devices Aaron Zinman B.S. Cognitive Science University of California, San Diego June 2004 MASSACHUSETTS INSTrWUE OF TECHNOLOGY SEPB 1 2006 Submitted to the Program in Media Arts and Sciences, LIBRARIES School of Architecture and Planning, in partial partial fulfillment of the requirements for the degree of Master of Science in Media Arts and Sciences at the Massachusetts Institute of Technology August 2006 ARCHIVES © 2006 Massachusetts Institute of Technology Author Aaron Zinman Program in Media Arts and Sciences AV-gist 11, 2006 Certified by Judith S. Donath Associate Professor ofl edia Arts and Sciences Thesis Supervisor Acceptd by Andrew Lippman Chair, Department Committee on Graduate Students Program in Media Arts and Sciences RadioActive: Enabling large-scale asynchronous audio discussions on mobile devices Aaron Zinman Submitted to the Program in Media Arts and Sciences, School of Architecture and Planning, in partial fulfillment of the requirements for the degree of Master of Science in Media Arts and Sciences at the Massachusetts Institute of Technology August 2006 Abstract Current mobile technology works well to connect individuals together at any time or place. However, general focus on one-to-one conversations has overlooked the poten- tial of always-on group and community links. I hypothesize that asynchronous persist- ent audio is a superior medium to support scalable always-on group communication for mobile devices. To evaluate this claim, one must first have an adequate interaction de- sign before its possible to investigate the qualities and usage patterns over the long- term. This design does not exist for mobile devices. -

That the Ultimate
THAT THEUS009755874B2ULTIMATE (12 ) United States Patent ( 10 ) Patent No. : US 9 , 755 ,874 B2 Feher (45 ) Date of Patent: " Sep . 5 , 2017 ( 54 ) DIGITAL MOBILE COMMUNICATION ( 56 ) References Cited ( 71 ) Applicant: Kamilo Feher , El Macero , CA (US ) U . S . PATENT DOCUMENTS 3 ,702 , 476 A 11/ 1972 Nathanson ( 72 ) Inventor: Kamilo Feher, El Macero , CA (US ) 3 ,944 ,926 A 3 / 1976 Feher ( * ) Notice : Subject to any disclaimer , the term of this ( Continued ) patent is extended or adjusted under 35 U . S . C . 154 ( b ) by 0 days . FOREIGN PATENT DOCUMENTS This patent is subject to a terminal dis AU 2005335219 1 / 2010 claimer. CN 0512333 1 /2008 ( Continued ) ( 21 ) Appl. No .: 15 / 268, 614 OTHER PUBLICATIONS Sep . 18 , 2016 ( 22 ) Filed : U . S . Appl. No . 09 / 370 , 360 , filed Aug . 9 , 1999 , US pat Publication (65 ) Prior Publication Data Number not known U . S . Appl. No . 09 /370 ,360 Feher, K . (SPECT ) . US 2017 /0041169 A1 Feb . 9 , 2017 (Continued ) Primary Examiner — Ted Wang Related U . S . Application Data Continuation of application No . 14 / 963 , 251, filed on (57 ) ABSTRACT (63 ) Digital mobile communications devices and methods for Dec . 9 , 2015 , now Pat . No . 9 ,450 ,716 , which is a processing , modulation and demodulation , transmission and (Continued ) reception of spread spectrum signals , Orthogonal Frequency Division Multiplexed (OFDM ) signals and conversion of (51 ) Int. CI. spread spectrum signals into OFDM signals . Received H04L 27 / 26 ( 2006 .01 ) spread spectrum signals from 3G cellular systems are con G06F 19 /00 ( 2011 .01 ) verted into OFDM signals and transmitted in a Wi- Fi (Continued ) network . -

The Frame Work for Kinetic Text Messages on Mobile Phones Sooyun Im Iowa State University
Iowa State University Capstones, Theses and Retrospective Theses and Dissertations Dissertations 2007 The frame work for kinetic text messages on mobile phones Sooyun Im Iowa State University Follow this and additional works at: https://lib.dr.iastate.edu/rtd Part of the Art and Design Commons Recommended Citation Im, Sooyun, "The frame work for kinetic text messages on mobile phones" (2007). Retrospective Theses and Dissertations. 15090. https://lib.dr.iastate.edu/rtd/15090 This Thesis is brought to you for free and open access by the Iowa State University Capstones, Theses and Dissertations at Iowa State University Digital Repository. It has been accepted for inclusion in Retrospective Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. The frame work for kinetic text messages on mobile phones by Sooyun Im A thesis submitted to the graduate faculty in partial fulfillment of the requirements for the degree of MASTER OF FINE ARTS Major: Graphic Design Program of Study Committee: Sunghyun Kang, Major Professor Paul Bruski Shana Smith Iowa State University Ames, Iowa 2007 Copyright © Sooyun Im, 2007. All rights reserved. UMI Number: 1446126 UMI Microform 1446126 Copyright 2007 by ProQuest Information and Learning Company. All rights reserved. This microform edition is protected against unauthorized copying under Title 17, United States Code. ProQuest Information and Learning Company 300 North Zeeb Road P.O. Box 1346 Ann Arbor, MI 48106-1346 ii TABLE OF CONTENTS ABSTRACT iv CHAPTER 1. INTRODUCTION 1 CHAPTER 2. LITERATURE REVIEW 4 A. Mobile communication technology 4 1. -
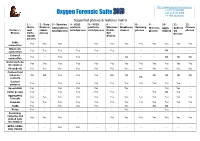
Oxygen Forensic Suite
http://www.oxygen-forensic.com +1 877 9 OXYGEN Oxygen Forensic Suite +44 20 8133 8450 +7 495 222 9278 Supported phones & features matrix 1 – 2 - Sony 3 – Symbian 4 - UIQ2 5 – UIQ3 6 - 7 - 8- 9- 10- 11- 12- Nokia Ericsson S60 platform platform platform Windows Blackberry Samsung Motorola Apple Android Chinese Feature \ and classic smartphones smartphones smartphones Mobile devices phones phones devices OS phones Phones Vertu phones 5/6 devices classic devices phones Cable Yes Yes Yes - Yes Yes Yes Yes Yes Yes Yes Yes connection Bluetooth Yes Yes Yes Yes Yes Yes - - - NA - - connection Infrared Yes - Yes Yes - - NA - - NA NA NA connection General phone Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes information Phonebook Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Custom field labels for NA NA Yes Yes Yes NA NA NA NA NA NA contacts NA Contact Yes - Yes Yes Yes Yes Yes Yes Yes Yes Yes - pictures Speed dials Yes - Yes Yes Yes - Yes - - Yes Yes - Caller groups Yes - Yes Yes Yes Yes - - Yes NA Yes - Aggregated Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Contacts Calendar Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Tasks Yes - Yes Yes Yes - Yes - NA NA - - Notes Yes - - - - - Yes - - Yes - - Incoming, outgoing and Yes Yes Yes - - Yes Yes Yes Yes Yes Yes Yes missed calls information GPRS, EDGE, - - Yes Yes - - - - - - - CSD, HSCSD - and Wi-Fi traffic and sessions log Sent and received SMS, - Sent SMS - Yes Yes Yes(2) - - - - - - MMS, E-mail messages log Deleted - messages - - Yes(1) - Yes(1) - - - Yes(8) - - information Flash SMS -

A Study of Application Programming Interfaces for Mobile Operating Systems by Ashok Chakravarthy Mandala
Platform Leadership through System Interfaces: A Study of Application Programming Interfaces for Mobile Operating Systems by Ashok Chakravarthy Mandala Bachelor of Engineering, Computer Science Birla Institute of Technology and Science, Pilani, India Submitted to the System Design and Management Program in Partial Fulfillment of the Requirements for the Degree of Master of Science in Engineering and Management at the Massachusetts Institute of Technology February 2007 © 2007 Ashok Mandala All rights reserved The author hereby grants to MIT permission to reproduce and to distribute publicly paper and electronic copies of this thesis document in whole or in part. Signature of Auiithnr - Ashok Mandala System Design and Management Program February 2007 Certified by Michael A. Cusumano Thesis Supervisor Sloan School of Management Certified by Patrick Hale MASSACHUSETTS INSTITUT OF TEO-NOLOGY Director System Design and Management Program MAY 0 6 2008 ARCHGES LIBRARIES Platform Leadership through System Interfaces: A Study of Application Programming Interfaces for Mobile Operating Systems By Ashok C. Mandala Submitted to the System Design and Management Program on January 19, 2007 in Partial Fulfillment of the Requirements for the Degree of Master of Science in Engineering and Management ABSTRACT The Smart Mobile device industry is witnessing rapid growth with the increased convergence of voice-centric mobile phones and data-centric personal digital assistant systems. Improving capabilities in device hardware have allowed development of complex user interfaces, multimedia and communication capabilities on these devices. Modem Mobile Operating Systems manage this complexity in the mobile device by administering hardware resources and providing a platform for development of new consumer and enterprise applications. -
How to Develop Applications and Make Money on Symbian Smart Phones Half-Day Introductory Workshop
How to develop applications and make money on Symbian smart phones Half-day introductory Workshop 2:00 p.m. – 6:00 p.m., 25th September, 2005 XinHua Book City (新華書城), 1 Leighton Road, Causeway Bay, Hong Kong In the first half of 2005 more than 14.5 million Symbian OS phones are shipped. This 191% increase on the equivalent period in 2004 shows the rapid growth in the global market for phones based on advanced operating systems and that Symbian has maintained and continues to extend its leadership of this global market. Symbian OS worldwide installed base reaches more than 39 million phones*. More and more users are paying for mobile applications and services. More and more companies are seeking mobile enterprise solutions. Smart phones are replacing PDAs for both commercial and individual sides. The need for high-quality, innovative and customized mobile software is intense. How do you capture this exploding trend and make money with it? This half-day workshop will show you the path and tips to rapidly start developing applications for Symbian smart phones. And how you can make money with your Symbian applications. Who should attend? - If you want to learn how to start to develop Symbian applications. - If you want to know the business model of mobile, especially Symbian applications - If you are considering which mobile enterprise solution to offer - Anyone interested in know what Symbian is all about. What will you learn? - How to start developing Symbian applications - Where to get help in developing Symbian applications - What must be needed to make commercial Symbian applications - What are the marketing and distribution channels for your Symbian applications Prerequisite - Basic C++ programming skills and understandings Program Rundown Time Topic 2:00p.m. -

Flexible User Interface - FLUSI
School of Mathematics and Systems Engineering Reports from MSI - Rapporter från MSI Flexible User Interface - FLUSI Jan Conrad Jan MSI Report 06010 2006 Växjö University ISSN 1650-2647 SE-351 95 VÄXJÖ ISRN VXU/MSI/DA/E/--06010/--SE Flexible User Interface FLUSI Jan Conrad Abstract The cellular phone network has been increasing rapidly during the last years. For many people the mobile phone has become an every day gadget with a wide performance and functional range. The usage of technologies like GPRS, HSCSD, EDGE and UMTS as well as the bandwidth of networks and consequently the connectivity of the phones has also increased persistently. Coming along with that, three technologies, which are ubiquitous or pervasive computing, mobile and wireless networks and location-based technologies, are making rapid progress. The aim of this thesis is to offer an architecture for a location-based user interface in the intersection of the three technologies mentioned above. The system should work with a minimum of special hardware requirement. Not to overload the user with information, the user interface should be adaptable, context-aware and location-based. The context-data should remain extendible and adaptable. II Acknowledgements I would like to thank some people who helped and supported us in writing my thesis. First, I am grateful to Jesper Andersson. He has been a continual support. He was always available for me and inspired me with many relevant and useful ideas and critics. Secondly I thank Marcus Edvinsson who introduced me to the XAP-System. Last but not the least I thank Mathias Hedenborg and Maria Karlsson who made this thesis possible. -

Introduction to Symbian OS Characteristics of Symbian V.7.0S Enhancements in Symbian V.9.2 Leaves Vs
IInnttrroodduuccttiioonn ttoo SSyymmbbiiaann OOSS Marco Aiello VITALab --- TUW ien (A) & DIT --- Universita’ di Trento (I) [email protected] Material based on original material from the author, from the http://www.symbian.com website, and from the book Symbian OS Explained by Jo Stichbury, Wiley (2005). SSyymmbbiiaann OOSS Introduction to Symbian OS Characteristics of Symbian v.7.0s Enhancements in Symbian v.9.2 Leaves vs. Exceptions Event-drive multitasking using Active Objects Active Objects scheduler Threads and Processes Sy mbian OS 2 Aiello ©2005 SSyymmbbiiaann OOSS An operating system for mobile devices with limited resources, multitasking needs and soft real time requirements. Based on a modular, layered, micro-kernel approach. Requirements: Resilient power-management Careful use of memory resources Multi-tasking (e.g, phone calls, messages, alarms, games, wap browser, camera, bluetooth app, etc.) Soft Real-Time (e.g., incoming phone call) Robust Symbian OS was designed for mobile devices, from its earliest incarnation as EPOC32 in the Psion Series 5. Symbian OS is a consortium formed in 1998 and owned by Psion, Nokia, Sony Ericsson, Panasonic (Matsushita), and Siemens. The shareholders are licensees of Symbian OS. In addition, because Symbian OS is an open platform, any manufacturer can license it. Sy mbian OS 3 Aiello ©2005 SSyymmbbiiaann OOSS oonn tthhee ffoolllloowwiinngg HHWW Motorola A1000 FOMA F900iC FOMA F880iES Nokia 7710 Nokia 3230 Sony Ericsson P910 BenQ P30 FOMA F901iC FOMA F900iC Lenovo P930 Nokia 7710 -
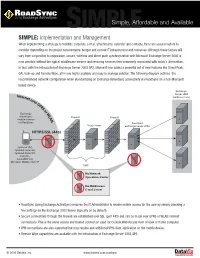
Implementation and Management Simple, Affordable and Available
SIMPLESimple, Affordable and Available SIMPLE: Implementation and Management When implementing a strategy to mobilize corporate e-mail, attachments, calendar and contacts, there are several factors to consider depending on the project requirements, budget and current IT infrastructure and resources. Although these factors will vary from corporation to corporation, secure, wireless and direct push synchronization with Microsoft Exchange Server 2003 is now possible without the typical middleware servers and recurring services fees commonly associated with today's alternatives. In fact, with the introduction of Exchange Server 2003 SP2, Microsoft has added a powerful set of new features like Direct Push, GAL look-up and Remote Wipe, all in one highly scalable and easy to manage solution. The following diagram outlines the recommended network configuration when standardizing on Exchange ActiveSync connectivity via RoadSync on a non-Microsoft based device. Exchange Server 2003 Intern mailbox servers et o ve r G PR S o r Exchange W ActiveSync- L A Firewall Firewall enabled device N via RoadSync Front End Proxy Server Exchange Server 2003 HTTPS/SSL (443) Symbian UIQ, Symbian Series 60, Symbian Series 80, Palm OS, Java MIDP 2.0 Windows Mobile 2003 SE DMZ No Network Operations Center No Middleware E-mail Server • RoadSync (using Exchange ActiveSync) requires the IT Administrator to enable mobile access for the user by simply checking a few settings on the Exchange 2003 Server (typically on by default). • Secure connections through the firewall are established over SSL (port 443) and can be made over GPRS or WLAN internet connections. This is the same secure and trusted connection used for Outlook Web Access from a kiosk or home computer.