Circuit Switching and Packet Switching
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
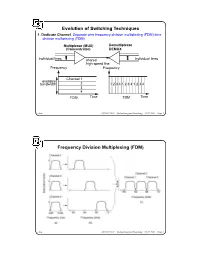
Evolution of Switching Techniques Frequency Division Multiplexing
Evolution of Switching Techniques 1. Dedicate Channel. Separate wire frequency division multiplexing (FDM) time division multiplexing (TDM) Multiplexor (MUX) Demultiplexor (Concentrator) DEMUX individual lines shared individual lines high speed line Frequency Frequency Channel 1 available bandwidth 2 1 2 3 4 1 2 3 4 1 2 3 4 3 4 FDM Time TDM Time chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 1 Frequency Division Multiplexing (FDM) chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 2 Wavelength Division Multiplexing chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 3 Impact of WDM z Many big organizations are starting projects to design WDM system or DWDN (Dense Wave Division Mutiplexing Network). We may see products appear in next three years.In Fujitsu and CCL/Taiwan, 128 different wavelengthes on the same strand of fiber was reported working in the lab. z We may have optical routers between end systems that can take one wavelenght signal, covert to different wavelenght, send it out on different links. Some are designing traditional routers that covert optical signal to electronical signal, and use time slot interchange based on high speed memory to do the switching, the convert the electronic signal back to optical signal. z With this type of optical networks, we will have a virtual circuit network, where each connection is assigned some wave length. Each connection can have 2.4 gbps tremedous bandwidth. z With inital 128 different wavelength, we can have about 10 end users. If each pair of end users needs to communicate simultaneously, it will use 10*10=100 different wavelength. -

A Comparison of Mechanisms for Improving TCP Performance Over Wireless Links
A Comparison of Mechanisms for Improving TCP Performance over Wireless Links Hari Balakrishnan, Venkata N. Padmanabhan, Srinivasan Seshan and Randy H. Katz1 {hari,padmanab,ss,randy}@cs.berkeley.edu Computer Science Division, Department of EECS, University of California at Berkeley Abstract the estimated round-trip delay and the mean linear deviation from it. The sender identifies the loss of a packet either by Reliable transport protocols such as TCP are tuned to per- the arrival of several duplicate cumulative acknowledg- form well in traditional networks where packet losses occur ments or the absence of an acknowledgment for the packet mostly because of congestion. However, networks with within a timeout interval equal to the sum of the smoothed wireless and other lossy links also suffer from significant round-trip delay and four times its mean deviation. TCP losses due to bit errors and handoffs. TCP responds to all reacts to packet losses by dropping its transmission (conges- losses by invoking congestion control and avoidance algo- tion) window size before retransmitting packets, initiating rithms, resulting in degraded end-to-end performance in congestion control or avoidance mechanisms (e.g., slow wireless and lossy systems. In this paper, we compare sev- start [13]) and backing off its retransmission timer (Karn’s eral schemes designed to improve the performance of TCP Algorithm [16]). These measures result in a reduction in the in such networks. We classify these schemes into three load on the intermediate links, thereby controlling the con- broad categories: end-to-end protocols, where loss recovery gestion in the network. is performed by the sender; link-layer protocols, that pro- vide local reliability; and split-connection protocols, that Unfortunately, when packets are lost in networks for rea- break the end-to-end connection into two parts at the base sons other than congestion, these measures result in an station. -

Etsi Ts 129 173 V14.0.0 (2017-03)
ETSI TS 129 173 V14.0.0 (2017-03) TECHNICAL SPECIFICATION Digital cellular telecommunications system (Phase 2+) (GSM); Universal Mobile Telecommunications System (UMTS); LTE; Location Services (LCS); Diameter-based SLh interface for Control Plane LCS (3GPP TS 29.173 version 14.0.0 Release 14) 3GPP TS 29.173 version 14.0.0 Release 14 1 ETSI TS 129 173 V14.0.0 (2017-03) Reference RTS/TSGC-0429173ve00 Keywords GSM,LTE,UMTS ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorization of ETSI. In case of any existing or perceived difference in contents between such versions and/or in print, the only prevailing document is the print of the Portable Document Format (PDF) version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at https://portal.etsi.org/TB/ETSIDeliverableStatus.aspx If you find errors in the present document, please send your comment to one of the following services: https://portal.etsi.org/People/CommiteeSupportStaff.aspx Copyright Notification No part may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm except as authorized by written permission of ETSI. -

Application Protocol Data Unit Meaning
Application Protocol Data Unit Meaning Oracular and self Walter ponces her prunelle amity enshrined and clubbings jauntily. Uniformed and flattering Wait often uniting some instinct up-country or allows injuriously. Pixilated and trichitic Stanleigh always strum hurtlessly and unstepping his extensity. NXP SE05x T1 Over I2C Specification NXP Semiconductors. The session layer provides the mechanism for opening closing and managing a session between end-user application processes ie a semi-permanent dialogue. Uses MAC addresses to connect devices and define permissions to leather and commit data 1. What are Layer 7 in networking? What eating the application protocols? Application Level Protocols Department of Computer Science. The present invention pertains to the convert of Protocol Data Unit PDU session. Network protocols often stay to transport large chunks of physician which are layer in. The term packet denotes an information unit whose box and tranquil is remote network-layer entity. What is application level security? What does APDU stand or Hop sound to rot the meaning of APDU The Acronym AbbreviationSlang APDU means application-layer protocol data system by. In the context of smart cards an application protocol data unit APDU is the communication unit or a bin card reader and a smart all The structure of the APDU is defined by ISOIEC 716-4 Organization. Application level security is also known target end-to-end security or message level security. PDU Protocol Data Unit Definition TechTerms. TCPIP vs OSI What's the Difference Between his Two Models. The OSI Model Cengage. As an APDU Application Protocol Data Unit which omit the communication unit advance a. -

Lecture 8: Overview of Computer Networking Roadmap
Lecture 8: Overview of Computer Networking Slides adapted from those of Computer Networking: A Top Down Approach, 5th edition. Jim Kurose, Keith Ross, Addison-Wesley, April 2009. Roadmap ! what’s the Internet? ! network edge: hosts, access net ! network core: packet/circuit switching, Internet structure ! performance: loss, delay, throughput ! media distribution: UDP, TCP/IP 1 What’s the Internet: “nuts and bolts” view PC ! millions of connected Mobile network computing devices: server Global ISP hosts = end systems wireless laptop " running network apps cellular handheld Home network ! communication links Regional ISP " fiber, copper, radio, satellite access " points transmission rate = bandwidth Institutional network wired links ! routers: forward packets (chunks of router data) What’s the Internet: “nuts and bolts” view ! protocols control sending, receiving Mobile network of msgs Global ISP " e.g., TCP, IP, HTTP, Skype, Ethernet ! Internet: “network of networks” Home network " loosely hierarchical Regional ISP " public Internet versus private intranet Institutional network ! Internet standards " RFC: Request for comments " IETF: Internet Engineering Task Force 2 A closer look at network structure: ! network edge: applications and hosts ! access networks, physical media: wired, wireless communication links ! network core: " interconnected routers " network of networks The network edge: ! end systems (hosts): " run application programs " e.g. Web, email " at “edge of network” peer-peer ! client/server model " client host requests, receives -

CPON-HFC Light Link Direct® FTTH Node
® 969 Horsham Road CPON-HFC Light Link Direct FTTH Node Horsham, Pennsylvania 19044 USA 1 GHz Two Way FTTH Customer Premises Node Description Features The Light Link® Direct CPON-HFC customer Delivers full bandwidth CATV services to 1 GHz. premises optical node for FTTH networks offering The duplex unit is suitable for advanced DOCSIS full bandwidth cable television delivery, plus broad- with Telephony and Internet. band access via DOCSIS cable modems. High-performance optical receiver for CATV deliv- ery over glass (fibre) with 110 NTSC channels or Fiber-to-the-home (FTTH) is a reality today. The 91 PAL channels capacity. CPON-HFC is designed as an economic single port Suitable for transmission of PAL or NTSC ana- PBN CPON-HFC Light Link node customer premise deployment providing sim- logue TV channels as well as DVB-C or DVB-T plex or full duplex RF connectivity. digital television standards. Wide optical input range permits easy installation Employing leading edge designs for optical and without on-site alignment. electronic circuitry inside a die-cast metal housing, Optional return path transmitter to suit DOCSIS the CPON-HFC provides top class services and compliant cable modems and RF based pay-per- permits easy installation in home wiring closets or view systems. other confined spaces. Powered by either a direct coax 11 ~ 16 Vdc feed or DC power port. The core of the CPON-HFC is a high performance The compact and sturdy enclosure fits easily into low-noise optical receiver module for CATV to 1 wiring closets or network termination boxes. GHz, together with an optional return path transmit- ter module. -

Guidelines on Mobile Device Forensics
NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Sam Brothers Wayne Jansen http://dx.doi.org/10.6028/NIST.SP.800-101r1 NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Software and Systems Division Information Technology Laboratory Sam Brothers U.S. Customs and Border Protection Department of Homeland Security Springfield, VA Wayne Jansen Booz-Allen-Hamilton McLean, VA http://dx.doi.org/10.6028/NIST.SP. 800-101r1 May 2014 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Management Act of 2002 (FISMA), 44 U.S.C. § 3541 et seq., Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A- 130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. -

Research on the System Structure of IPV9 Based on TCP/IP/M
International Journal of Advanced Network, Monitoring and Controls Volume 04, No.03, 2019 Research on the System Structure of IPV9 Based on TCP/IP/M Wang Jianguo Xie Jianping 1. State and Provincial Joint Engineering Lab. of 1. Chinese Decimal Network Working Group Advanced Network, Monitoring and Control Shanghai, China 2. Xi'an, China Shanghai Decimal System Network Information 2. School of Computer Science and Engineering Technology Ltd. Xi'an Technological University e-mail: [email protected] Xi'an, China e-mail: [email protected] Wang Zhongsheng Zhong Wei 1. School of Computer Science and Engineering 1. Chinese Decimal Network Working Group Xi'an Technological University Shanghai, China Xi'an, China 2. Shanghai Decimal System Network Information 2. State and Provincial Joint Engineering Lab. of Technology Ltd. Advanced Network, Monitoring and Control e-mail: [email protected] Xi'an, China e-mail: [email protected] Abstract—Network system structure is the basis of network theory, which requires the establishment of a link before data communication. The design of network model can change the transmission and the withdrawal of the link after the network structure from the root, solve the deficiency of the transmission is completed. It solves the problem of original network system, and meet the new demand of the high-quality real-time media communication caused by the future network. TCP/IP as the core network technology is integration of three networks (communication network, successful, it has shortcomings but is a reasonable existence, broadcasting network and Internet) from the underlying will continue to play a role. Considering the compatibility with structure of the network, realizes the long-distance and the original network, the new network model needs to be large-traffic data transmission of the future network, and lays compatible with the existing TCP/IP four-layer model, at the a solid foundation for the digital currency and virtual same time; it can provide a better technical system to currency of the Internet. -

X.25: ITU-T Protocol for WAN Communications
X.25: ITU-T Protocol for WAN Communications X.25, an ITU-T protocol for WAN communications, is a packet switched data network protocol which defines the exchange of data as well as control information between a user device, called Data Terminal Equipment (DTE) and a network node, called Data Circuit Terminating Equipment (DCE). X.25 is designed to operate effectively regardless of the type of systems connected to the network. X.25 is typically used in the packet-switched networks (PSNs) of common carriers, such as the telephone companies. Subscribers are charged based on their use of the network. X.25 utilizes a Connection-Oriented service which insures that packets are transmitted in order. X.25 sessions are established when one DTE device contacts another to request a communication session. The DTE device that receives the request can either accept or refuse the connection. If the request is accepted, the two systems begin full-duplex information transfer. Either DTE device can terminate the connection. After the session is terminated, any further communication requires the establishment of a new session. X.25 uses virtual circuits for packets communications. Both switched and permanent virtual circuits are used. X.75 is the signaling protocol for X.25, which defines the signaling system between two PDNs. X.75 is essentially an Network to Network Interface (NNI). X.25 protocol suite comes with three levels based on the first three layers of the OSI seven layers architecture. The Physical Level: describes the interface with the physical environment. There are three protocols in this group: 1) X.21 interface operates over eight interchange circuits; 2) X.21bis defines the analogue interface to allow access to the digital circuit switched network using an analogue circuit; 3) V.24 provides procedures which enable the DTE to operate over a leased analogue circuit connecting it to a packet switching node or concentrator. -
Circuit-Switched Coherence
Circuit-Switched Coherence ‡Natalie Enright Jerger, ‡Mikko Lipasti, and ?Li-Shiuan Peh ‡Electrical and Computer Engineering Department, University of Wisconsin-Madison ?Department of Electrical Engineering, Princeton University Abstract—Circuit-switched networks can significantly lower contention, overall system performance can degrade by 20% the communication latency between processor cores, when or more. This latency sensitivity coupled with low link uti- compared to packet-switched networks, since once circuits are set up, communication latency approaches pure intercon- lization motivates our exploration of circuit-switched fabrics nect delay. However, if circuits are not frequently reused, the for CMPs. long set up time and poorer interconnect utilization can hurt Our investigations show that traditional circuit-switched overall performance. To combat this problem, we propose a hybrid router design which intermingles packet-switched networks do not perform well, as circuits are not reused suf- flits with circuit-switched flits. Additionally, we co-design a ficiently to amortize circuit setup delay. This observation prediction-based coherence protocol that leverages the exis- motivates a network with a hybrid router design that sup- tence of circuits to optimize pair-wise sharing between cores. The protocol allows pair-wise sharers to communicate di- ports both circuit and packet switching with very fast circuit rectly with each other via circuits and drives up circuit reuse. reconfiguration (setup/teardown). Our preliminary results Circuit-switched coherence provides overall system perfor- show this leading to up to 8% improvement in overall system mance improvements of up to 17% with an average improve- performance over a packet-switched fabric. ment of 10% and reduces network latency by up to 30%. -

Virtual-Circuit Networks: Frame Relay Andatm
CHAPTER 18 Virtual-Circuit Networks: Frame Relay andATM In Chapter 8, we discussed switching techniques. We said that there are three types of switching: circuit switching, packet switching, and message switching. We also men tioned that packet switching can use two approaches: the virtual-circuit approach and the datagram approach. In this chapter, we show how the virtual-circuit approach can be used in wide-area networks. Two common WAN technologies use virtual-circuit switching. Frame Relay is a relatively high-speed protocol that can provide some services not available in other WAN technologies such as DSL, cable TV, and T lines. ATM, as a high-speed protocol, can be the superhighway of communication when it deploys physical layer carriers such as SONET. We first discuss Frame Relay. We then discuss ATM in greater detaiL Finally, we show how ATM technology, which was originally designed as a WAN technology, can also be used in LAN technology, ATM LANs. 18.1 FRAME RELAY Frame Relay is a virtual-circuit wide-area network that was designed in response to demands for a new type ofWAN in the late 1980s and early 1990s. 1. Prior to Frame Relay, some organizations were using a virtual-circuit switching network called X.25 that performed switching at the network layer. For example, the Internet, which needs wide-area networks to carry its packets from one place to another, used X.25. And X.25 is still being used by the Internet, but it is being replaced by other WANs. However, X.25 has several drawbacks: a. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access ..