Token Attempt: the Misrepresentation of Website Privacy Policies Through the Misuse of P3P Compact Policy Tokens
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Simplify Your Digital Life ______LYCOS Appoints Ramesh Reddy As ED (Finance) and Group CFO
Simplify your Digital Life _________________________________________________________________________ LYCOS Appoints Ramesh Reddy as ED (Finance) and Group CFO Responsible for the Group’s Financial Management and Strategy Hyderabad, India, May 09, 2016: LYCOS (NSE: LYCOS I BSE: 532368), the global Internet brand is pleased to announce the appointment of Y Ramesh Reddy as the Group Chief Financial Officer and Executive Director (Finance) for the entire LYCOS group. Ramesh brings more than 25 years of experience to LYCOS, including an extensive background working with public companies, corporate finance, operations management, financial planning and analysis, mergers and acquisitions, and investor relations. Ramesh Reddy was the Group CFO of Cambridge Energy Resources (CER), a company focused on providing ‘Green Energy management as a service to Telecom Towers, Group CFO of Cambridge Technology Enterprise (BSE: 532801 | NSE: CTE), and Prior to joining CTE, he was with Virinchi (BSE: 532372), where he played a key role as the Head of the Product Development and Chief Functional Architect. Ramesh has a B. Tech in Chemical Engineering from IIT, Chennai and MBA in Finance & Marketing from XLRI, Jamshedpur. Ramesh will report to the Chairman and CEO, Suresh Reddy and will oversee corporate finance, financial strategy, investor relations and reporting for LYCOS. He will work closely with regional and global financial teams to raise the bar further on strengthening the financial foundation and fiscal discipline of the company. “Ramesh has witnessed the trajectory of the company as a director on the board for the last eight years. We are thrilled to see him take up an executive role with LYCOS. His acute business acumen and solid experience in finance will be a big plus to the company.” said, Suresh Reddy, Chairman and CEO of LYCOS. -

Simplify Your Digital Life LYCOS Announces the Launch of Brightcom
Simplify your Digital Life _________________________________________________________________________ LYCOS Announces the Launch of Brightcom Gali Arnon to be the CEO of Brightcom Hyderabad, India and Herziliya, Israel, April 20, 2016: LYCOS (NSE: LYCOS I BSE: 532368), the global Internet brand, today announced that the company is working on a meaningful and widespread reorganization of the group. These changes are designed to simplify the way LYCOS interacts with customers, partners, investors and world at large. This move will facilitate the organization in becom- ing more nimble and responsive. In line with the above plan, the company made the first major announcement today. BRIGHTCOM powered by LYCOS Brightcom brings together the legacy of ‘Ybrant Digital’ alongside the ‘Brightcom’ Media initiative. This combines data-driven technology together with the company’s strong bonds with advertisers and publishers, all in one consolidated platform. The motto of the brand is ‘Leading through technology, winning through people’. The global expert team, be it in APAC, Israel, Europe, USA or Latin America, offers know-how and perspective, which are shaped into a strategy and a plan of action eventually executed to meet the clients’ goals. The current operations will remain intact. If anything, they will only get better. There are new prod- ucts, exclusive media-assets and new offices, waiting to be unveiled soon. Gali Arnon will take on the role of CEO of Brightcom. She is a natural choice to take up this role due to her initiative in bringing together the core idea and the entire business plan for Brightcom. She will transition out of her current role as the General Manager of the Advertising Division of LYCOS, Ybrant Digital. -

Biographies of Participants American University Law Review
American University Law Review Volume 50 | Issue 2 Article 6 2000 Biographies of Participants American University Law Review Follow this and additional works at: http://digitalcommons.wcl.american.edu/aulr Part of the Law Commons Recommended Citation American University Law Review. "Biographies of Participants." American University Law Review 50, no.2 (2000): 451-472. This Conference & Symposia is brought to you for free and open access by the Washington College of Law Journals & Law Reviews at Digital Commons @ American University Washington College of Law. It has been accepted for inclusion in American University Law Review by an authorized administrator of Digital Commons @ American University Washington College of Law. For more information, please contact [email protected]. Biographies of Participants This conference & symposia is available in American University Law Review: http://digitalcommons.wcl.american.edu/aulr/vol50/ iss2/6 BIOGRAPHIES oF PARTICIPANTS JONATHAN BAND received a B.A., magna cum laude, Phi Beta Kappa, in 1982 from Harvard College, and a J.D. from Yale Law School in 1985. Mr. Band's areas of practice include intellectual property, administrative litigation, and Internet regulation. His work in the intellectual property field has focused on appellate litigation in softwvare copyright cases such as Gates Rubber Co. v. Bando Chemical, Inc. and advocacy concerning intellectual property policy issues. His administrative litigation experience includes representing the City and County of San Francisco in noise matters before the Federal Aviation Administration and the State of Alaska in a matter relating to the Exxon Valdez oil spill before the Federal Energy Regulatory Commission. Mr. Band has advised clients on Internet issues including online banking, privacy, spare, gambling and indecency. -
Marketing Digital Media Worldwide
Marketing Digital Media Worldwide Ybrant buys Lycos for $36 Million Lycos Inc., the leading brand of search based internet properties and services. Daum Communications will focus on Korean domestic business after this sale. Hyderabad, India, August 16, 2010: Ybrant Digital, the end-to-end provider of digital marketing solutions, today announced the signing of the stock purchase agreement to acquire Lycos Inc., the leading brand of search based internet properties and services from Daum Communications. Ybrant’s well known brands include Oridian, AdDynamix, dream ad, Max Interactive and VoloMP. Lycos consistently averages 12 - 15 million monthly unique visitors in the U.S., and is a top 25 Internet destination worldwide, reaching nearly 60 million unique visitors globally. The Lycos Network of sites and services includes Lycos.com, Tripod, Angelfire, Gamesville, and HotBot. Together, these sites and service help bring people together to interact, to find new friends, and to express themselves in positive, powerful ways. Daum reorganized the business of Lycos in 2009 and has turned Lycos profitable. As a result of the sale of Lycos, Daum will be able to devote its energy and corporate resources in order to find new potential growth business and future-oriented pipeline such as mobile, LBS, SNS and Search. “Brand Lycos needs no introduction, we are excited to bring in the Lycos properties into our fold.” said Suresh Reddy, Chairman and CEO, Ybrant Digital. “The quality of content and tools offered by Lycos has always attracted the best of the consumers across the world. Our goal is to combine the benefits of Ybrant’s global network with what Lycos has to offer in creating a compelling global destination for our advertising clients worldwide. -

Cie and Terra Lycos Celebrate Marketing and Strategic Alliance
CIE AND TERRA LYCOS CELEBRATE MARKETING AND STRATEGIC ALLIANCE § This alliance will be focused in the development of joint marketing strategies, including webcasting of various live entertainment events. Mexico City, November 30, 2000 – Corporacion Interamericana de Entretenimiento S.A. de C.V. (“CIE” or “the Company”) (BMV: CIE B), the leading live entertainment company in Latin America, today announced that it has established an alliance with Terra Lycos Mexico, a subsidiary of Terra Lycos (MC: TRR; Nasdaq: TRLY), the leading Internet company in the Spanish and Portuguese-speaking markets, to provide access to a great diversity of CIE’s contents and advertising platforms, through the development of various marketing strategies, including webcasting of live events, aimed at promoting Terra Lycos’ portal in Mexico. Arturo Galván, the country manager of Terra Lycos in Mexico, commented: “With this alliance Terra Lycos and CIE will develop joint marketing, diffusion and coverage of games, shows and spectacles which will be staged in the best venues and auditoriums of the country, as well as access to webcasting of a diverse and renowned artists and performances, nationally and internationally. With this alliance, more than three million Mexican users that integrate the Internet community of Terra Lycos, will enjoy a great diversity of events and entertainment by accessing Terra Lycos’ portal (www.terra.com.mx). With this agreement, “Terra Lycos and CIE will do the entertainment more yours than ever.” Rodrigo González Calvillo, Chief Operating Officer of CIE, mentioned: “The alliance we have reached with Terra Lycos, the leading Internet company in the Spanish and Portuguese-speaking markets, will allow CIE in the next years to develop one of the most complete marketing programs in Mexico, through an important range of services and products that we have in the country, including this great new media, the Internet. -

Handbook of Research on Web 2.0, 3.0, and X.0: Technologies, Business, and Social Applications
Handbook of Research on Web 2.0, 3.0, and X.0: Technologies, Business, and Social Applications San Murugesan Multimedia University, Malaysia & University of Western Sydney, Australia Volume I INFORMATION SCIENCE REFERENCE Hershey • New York Director of Editorial Content: Kristin Klinger Senior Managing Editor: Jamie Snavely Assistant Managing Editor: Michael Brehm Publishing Assistant: Sean Woznicki Typesetter: Carole Coulson, Ricardo Mendoza, Kurt Smith Cover Design: Lisa Tosheff Printed at: Yurchak Printing Inc. Published in the United States of America by Information Science Reference (an imprint of IGI Global) 701 E. Chocolate Avenue Hershey PA 17033 Tel: 717-533-8845 Fax: 717-533-8661 E-mail: [email protected] Web site: http://www.igi-global.com/reference Copyright © 2010 by IGI Global. All rights reserved. No part of this publication may be reproduced, stored or distributed in any form or by any means, electronic or mechanical, including photocopying, without written permission from the publisher. Product or company names used in this set are for identification purposes only. Inclusion of the names of the products or companies does not indicate a claim of ownership by IGI Global of the trademark or registered trademark. Library of Congress Cataloging-in-Publication Data Handbook of research on Web 2.0, 3.0, and X.0 : technologies, business, and social applications / San Murugesan, editor. p. cm. Includes bibliographical references and index. Summary: "This book provides a comprehensive reference source on next generation Web technologies and their applications"--Provided by publisher. ISBN 978-1-60566-384-5 (hardcover) -- ISBN 978-1-60566-385-2 (ebook) 1. Web 2.0. -
Brightcom Group Ltd
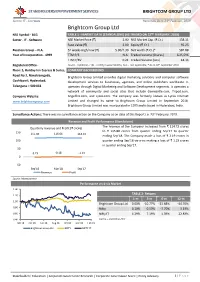
STAKEHOLDERS EMPOWERMENT SERVICES BRIGHTCOM GROUP LTD SECTOR: IT - SOFTWARE REPORTING DATE: 23RD FEBRUARY, 2019 Brightcom Group Ltd NSE Symbol - BCG TABLE 1 - MARKET DATA (STANDALONE) (AS TRADED ON 22ND FEBRUARY, 2019) Sector - IT - Software NSE Market Price (`) 2.90 NSE Market Cap. (₹ Cr.) 138.11 Face Value (`) 2.00 Equity (` Cr.) 95.25 Business Group – N.A. 52 weeks High/Low (₹) 5.90/2.30 Net worth (₹ Cr.)* 582.88 Year of Incorporation - 1999 TTM P/E N.A. Traded Volume (Shares) 6,25,596 TTM P/BV 0.24 Traded Volume (lacs) 18.14 Registered Office - Source - Capitaline, TTM - Trailing Twelve Months, N.A. - Not Applicable, * As on 30th September 2018 Floor: 5, Holiday Inn Express & Suites, COMPANY BACKGROUND Road No 2, Nanakramguda, Brightcom Group Limited provides digital marketing solutions and computer software Gachibowli, Hyderabad, development services to businesses, agencies, and online publishers worldwide. It Telangana – 500 032 operates through Digital Marketing and Software Development segments. It operates a network of community and social sites that include Gamesville.com, Tripod.com, Company Website: Angelfire.com, and Lycos.com. The company was formerly known as Lycos Internet www.brightcomgroup.com Limited and changed its name to Brightcom Group Limited in September 2018. Brightcom Group Limited was incorporated in 1999 and is based in Hyderabad, India. rd Surveillance Actions: There was no surveillance action on the Company as on date of this Report i.e. 23 February, 2019. Revenue and Profit Performance (Standalone) The revenue of the Company increased from ₹ 114.72 crores Quarterly revenue and Profit (₹ CRORE) 150 to ₹ 115.88 crores from quarter ending Sep’17 to quarter 115.88 116.64 114.72 ending Sep’18. -

Premium: Brightcom Group: for Hefty Gains!
Premium: Brightcom Group: For Hefty Gains! Dated 17 April 21 and Vol. XXX No.25| (Code: 532368) (FV: Rs.2) (CMP: Rs.8) Incorporated in 1999, the Brightcom Group (BCG), formerly known as Lycos Internet, is an Indian service company engaged in providing digital marketing services and development of computer software and services. It is a lso a global information technology (IT) implementation and outsourcing services provider. It has a presence across India, USA, Australia, Israel, Brazil, Argentina, Uruguay etc. and has 463 employees and consultants working in 22 offices spread across the world. Its software development services are based in India. It has 2 Indian subsidiaries and 14 subsidiaries. Lycos was acquired by Ybrant in 2010 for $36 million and renamed as Lycos Internet Ltd. In 2018, Lycos Internet was renamed to Brightcom Group L td. It was ready with changes required to conform to the European General Data Protection Regulation (GDPR). It increased its service offerings in Artificial Intelligence and Machine Learning. Brightcom Group was featured among Fortune India 500 in 2019. BCG offers digital marketing solutions to businesses, agencies and online publishers around the world. Over the period of next twenty years, BCG became a global player in digital marketing and related platforms by successfully acquiring and integrating 10 acquisitions. It has offices in the US, Argentina, Brazil, Chile, Uruguay, Mexico, UK, France, Germany, Sweden, Ukraine, Serbia, Israel, China, India, and Australia and with representatives or partners in Poland and Italy. BCG provides enterprise solutions and specializes in enterprise resource planning (ERP) solutions, Microsoft and open-source systems development. -

Filed by Vringo, Inc. Pursuant to Rule 425 Under the Securities Act Of
Filed by Vringo, Inc. Pursuant to Rule 425 under the Securities Act of 1933 (the "Securities Act") and deemed filed pursuant to Rule 14a-12 under the Securities Exchange Act of 1934 (the "Exchange Act") Securities Act File Number: 333-180609 Subject Company: Vringo, Inc. Exchange Act File Number: 001-34785 Set forth below is the presentation made by counsel to I/P Engine, Inc., a wholly-owned subsidiary of Innovate/Protect, Inc., at the Markman hearing on June 4, 2012 in connection with the lawsuit captioned I/P Engine, Inc. v. AOL Inc. et al., Civ. Action No. 2:11-cv-512, filed in United States District Court for the Eastern District of Virginia, Norfolk Division on September 15, 2011. MARKMAN HEARING June 4, 2012 1 1 2 Patents - in - Suit 2 1998 – 2002, Lycos buys over two dozen web entities, including: Tripod, Gamesville, WhoWhere, Wired Digital, Quote.com, Angelfire, Matchmaker.com, Raging Bull 1998, Lycos.com - #7 Most visited website 2000, Terra Networks acquires Lycos for over $12 billion Mr. Kosak Director of Engineering/CTO (Lycos) Technical Consultant (I/P Engine) Mr. Lang CTO (Lycos) CTO/CEO (I/P Engine) 3 4 US PATENT 6,314,420 US PATENT 6,775,664 4 Patents - In - Suit Filtering on the basis of: Content Collaborative Feedback Overall relevance to the query 5 6 US PATENT 6,314,420 6 US PATENT 6,775,664 7 8 US PATENT 5,867,799 8 US PATENT 6,314,420 US PATENT 5,867,799 1996 1998 9 10 US PATENT 6,314,420 10 11 SEARCH GRILL GO 11 informons containing “ Grill ” GRILL INFORMONS SEARCH RESULTS 12 RESULTS… 1. -

Zap.Com Announces Initial Members Of
Zap.com Announces Initial Members of November 30, 1999 ROCHESTER, N.Y.--(BUSINESS WIRE)--Nov. 29, 1999--Zap.com Corp. (OTCBB:ZPCM - news) announced today the initial members of ``The Zap 200 Best Internet Sites.'' The Zap 200, is a quick and easy, one stop guide to the Internet's best web sites located at www.zap.com. The Zap 200 is selected by a panel of experts from among thousands of interesting, informative and entertaining Internet sites. Avram Glazer, President of Zap.com Corp. stated, ``The ZAP 200 is the Internet users one-stop source for the finest sites the web. It is different from other source or guide sites in that Zap.com provides the user with a simple, centralized solution for Internet users looking for the very best the web has to offer. The Zap 200 will be updated with new and outstanding web sites on a regular basis. Internet sites interested in being considered for inclusion in the Zap 200 should fill out the feedback form at www.zap.com. The initial members of the Zap 200 (by category) are as follows: SEARCH/POTALS - About.com (www.about.com) - Altavista (www.altavista.com) - Disinfo (www.disinfo.com) - Excite (www.excite.com) - GO Network (www.go.com) - Google (www.google.com) - Hotbot www.hotbot.com) - Looksmart (www.looksmart.com) - Lycos (www.lycos.com) - MSN (www.msn.com) - Netscape Netcenter (www.netscape.com) - Yahoo (www.yahoo.com) NEWS/WEATHER - ABC News (www.abcnews.com) - BBC Online (www.bbc.co.uk/home/today/index.shtml) - CNN Interactive (www.cnn.com) - The Drudge Report (www.drudgereport.com) - MSNBC (www.msnbc.com/news/default.asp) -

The World Wide Web and Social Computing ! Based on Slides Originally Published by Thomas J
15-292 History of Computing The World Wide Web and Social Computing ! Based on slides originally published by Thomas J. Cortina in 2004 for a course at Stony Brook University. Revised in 2013 by Thomas J. Cortina for a computing history course at Carnegie Mellon University. Early Search Applications l Gopher l a distributed document search and retrieval network protocol designed for the Internet. l Released in 1991 by Paul Lindner and Mark McCahill of the University of Minnesota. l WAIS (Wide Area Information Servers) l A distributed text searching system to search index databases on remote computers. l Promoted by Thinking Machines Corporation. Early Search Applications Early Search Applications l Archie l Considered to be the first search engine. l Developed in 1990 at McGill University. l Keeps a database of directories and files in FTP sites on the Internet. l Search based on file name. Use FTP to fetch. l Veronica l Very Easy Rodent-Oriented Net-wide Index to Computerized Archives l Developed in 1992 at the University of Nevada at Reno. l Searches every item in all Gopher menus for specific keywords. Use FTP to fetch. l Jughead l Jonzy's Universal Gopher Hierarchy Excavation And Display! l Developed in 1993 at the University of Utah. l Similar to Veronica but it searches a single server at a time. World Wide Web l In 1989, Tim Berners-Lee, a physicist working at CERN, the European Particle Physics Laboratory, wanted a way for physicists to share information about their research. l His documentation project was the source of the two key inventions that made the World Wide Web possible: l HTML – HyperText Markup Language l URL – Uniform Resource Locator Web Browsers l Mosaic l Developed by a team at the National Center for Supercomputing Applications at the University of Illinois at Urbana-Champaign (NCSA-UIUC), led by Marc Andreesen. -

Simplify Your Digital Life Lycos TV Adds
Simplify your Digital Life ______________________________________________________________________________________ Lycos TV Adds Cool New Content to its Entertainment Channel The “One Question Interviews” by Rick Yaeger Hyderabad, December 04, 2014: Lycos TV announced the addition of new content from Actor/Executive Producer Greg Grunberg, under Entertainment Channel, “The One Question Interviews” by Rick Yaeger. This wildly popular, unconventional interview show is already on the channel www.lycostv.com. Celebrity guests include Chris Gorham, Sendhil Ramamurthy, Reno Wilson, Josh Malina, Tony Goldwyn, Vanna White, Derek Theler, Ken Leung, Neil Jackson and many other personalities from TV, Film, Music, & Sports. The One Question Interviews by Rick Yaeger is a show where celebrity guests are given an opportunity to share their latest work or important cause. The conversation of the show leads up to the moment when a single conversation starter interview question is chosen at random from a deck of cards and discussed. Rick Yaeger is known for his work on The Lab with Leo Laporte (2007), Easy to Assemble (2008) and One Question Interviews (2013). Rick is a resource for people in the entertainment industry who want to master social media and distribute their content online. About Lycos TV LycosTV is the premium destination for all things video on Lycos.com. It is a visually beautiful experience, utilizing our own HD player. All content will be placed into “channels”, like Entertainment, Food, News, etc., that each user will be able to ultimately customize based on his/her interests. Visit: www.lycostv.com About Lycos: Lycos is one of the original and most widely known Internet brands in the world, evolving from one of the first search engines on the web, into a comprehensive digital media destination for consumers across the world.