8Th Gen Intel® Core™ Processor Family I/O Datasheet, Vol. 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
How to Hack a Turned-Off Computer Or Running Unsigned
HOW TO HACK A TURNED-OFF COMPUTER, OR RUNNING UNSIGNED CODE IN INTEL ME Contents Contents ................................................................................................................................ 2 1. Introduction ...................................................................................................................... 3 1.1. Intel Management Engine 11 overview ............................................................................. 4 1.2. Published vulnerabilities in Intel ME .................................................................................. 5 1.2.1. Ring-3 rootkits.......................................................................................................... 5 1.2.2. Zero-Touch Provisioning ........................................................................................... 5 1.2.3. Silent Bob is Silent .................................................................................................... 5 2. Potential attack vectors ...................................................................................................... 6 2.1. HECI ............................................................................................................................... 6 2.2. Network (vPro only)......................................................................................................... 6 2.3. Hardware attack on SPI interface ..................................................................................... 6 2.4. Internal file system ......................................................................................................... -

Microcode Revision Guidance August 31, 2019 MCU Recommendations
microcode revision guidance August 31, 2019 MCU Recommendations Section 1 – Planned microcode updates • Provides details on Intel microcode updates currently planned or available and corresponding to Intel-SA-00233 published June 18, 2019. • Changes from prior revision(s) will be highlighted in yellow. Section 2 – No planned microcode updates • Products for which Intel does not plan to release microcode updates. This includes products previously identified as such. LEGEND: Production Status: • Planned – Intel is planning on releasing a MCU at a future date. • Beta – Intel has released this production signed MCU under NDA for all customers to validate. • Production – Intel has completed all validation and is authorizing customers to use this MCU in a production environment. -

Intel X86 Considered Harmful
Intel x86 considered harmful Joanna Rutkowska October 2015 Intel x86 considered harmful Version: 1.0 1 Contents 1 Introduction5 Trusted, Trustworthy, Secure?......................6 2 The BIOS and boot security8 BIOS as the root of trust. For everything................8 Bad SMM vs. Tails...........................9 How can the BIOS become malicious?.................9 Write-Protecting the flash chip..................... 10 Measuring the firmware: TPM and Static Root of Trust........ 11 A forgotten element: an immutable CRTM............... 12 Intel Boot Guard............................. 13 Problems maintaining long chains of trust............... 14 UEFI Secure Boot?........................... 15 Intel TXT to the rescue!......................... 15 The broken promise of Intel TXT.................... 16 Rescuing TXT: SMM sandboxing with STM.............. 18 The broken promise of an STM?.................... 19 Intel SGX: a next generation TXT?................... 20 Summary of x86 boot (in)security.................... 21 2 Intel x86 considered harmful Contents 3 The peripherals 23 Networking devices & subsystem as attack vectors........... 23 Networking devices as leaking apparatus................ 24 Sandboxing the networking devices................... 24 Keeping networking devices outside of the TCB............ 25 Preventing networking from leaking out data.............. 25 The USB as an attack vector...................... 26 The graphics subsystem......................... 29 The disk controller and storage subsystem............... 30 The audio -

2016 Kaby Lake Platforms Silicon Initialization Code Release Notes Intel Restricted Secret 5
2016 Kaby Lake Platforms Silicon Initialization Code Release Notes April 2020 Release Version 3.8.0 Intel Restricted Secret By using this document, in addition to any agreements you have with Intel, you accept the terms set forth below. You may not use or facilitate the use of this document in connection with any infringement or other legal analysis concerning Intel products described herein. You agree to grant Intel a non-exclusive, royalty-free license to any patent claim thereafter drafted which includes subject matter disclosed herein. INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE, EXPRESS OR IMPLIED, BY ESTOPPEL OR OTHERWISE, TO ANY INTELLECTUAL PROPERTY RIGHTS IS GRANTED BY THIS DOCUMENT. EXCEPT AS PROVIDED IN INTEL'S TERMS AND CONDITIONS OF SALE FOR SUCH PRODUCTS, INTEL ASSUMES NO LIABILITY WHATSOEVER AND INTEL DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY, RELATING TO SALE AND/OR USE OF INTEL PRODUCTS INCLUDING LIABILITY OR WARRANTIES RELATING TO FITNESS FOR A PARTICULAR PURPOSE, MERCHANTABILITY, OR INFRINGEMENT OF ANY PATENT, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT. A "Mission Critical Application" is any application in which failure of the Intel Product could result, directly or indirectly, in personal injury or death. SHOULD YOU PURCHASE OR USE INTEL'S PRODUCTS FOR ANY SUCH MISSION CRITICAL APPLICATION, YOU SHALL INDEMNIFY AND HOLD INTEL AND ITS SUBSIDIARIES, SUBCONTRACTORS AND AFFILIATES, AND THE DIRECTORS, OFFICERS, AND EMPLOYEES OF EACH, HARMLESS AGAINST ALL CLAIMS COSTS, DAMAGES, AND EXPENSES AND REASONABLE ATTORNEYS' FEES ARISING OUT OF, DIRECTLY OR INDIRECTLY, ANY CLAIM OF PRODUCT LIABILITY, PERSONAL INJURY, OR DEATH ARISING IN ANY WAY OUT OF SUCH MISSION CRITICAL APPLICATION, WHETHER OR NOT INTEL OR ITS SUBCONTRACTOR WAS NEGLIGENT IN THE DESIGN, MANUFACTURE, OR WARNING OF THE INTEL PRODUCT OR ANY OF ITS PARTS. -

Intense PC3 Kaby Lake 7Th Generation Intel Core Mini PC Product Specification V.1.3
Intense PC3 Kaby Lake th 7 Generation Intel Core Mini PC Product Specification v.1.3 Thanks to improved GPU (Intel HD 620 Graphics) and latest generation of Intel CPU (Kaby Lake), Intense PC3 can render demanding graphics and record-decode videos faster than ever while consuming less power. Intense PC3 supports 3x 4K display and is greatly recommended for CCTV, signage, virtualisation, 24/7 applications and real-time monitoring. This miniature fanless PC also provides faster storage and improved booting time thanks to new M.2 slot for SATA 3.0 or NVMe drives. Highly customisable thanks to face modules supporting built-in fibre optics, Ethernet bypass, power-over-Ethernet… IPC3 is recommended for advanced networking. Key Features Ideal For • High processing performance • CCTV, video surveillance • Fast Clock Speed (up to 3.5GHz with i7) • Real-time monitoring • Dual display mode supported • 24/7 applications • 3x 4K displays • Virtualization • Generous Memory (up to 32GB DDR4) • Windows IoT • Fast boosting time (M.2 SATA or NVMe) • Advanced networking • Low power consumption • Signage • Ruggedized die-cast aluminium shell • Video recording/decoding • Customisable Face Module • Rendering graphics Product Specifications Model IPC3 i5 Barebone IPC3 i7 Barebone Name IPC3REV2-i5 IPC3REV2-i7 Current HW Revision 2.0 Long Term Availability 2020 - (then product will be available with similar or better CPU) Processor Intel 7th Gen Core i5-7200U Processor Intel 7th Gen Core i7-7500U Processor Type (Kaby Lake) (Kaby Lake) Cores 64-bit dual core Clock speed 2.5GHz (turbo boost up to 3.1GHz) 2.7GHz (turbo boost up to 3.5GHz) Cache 3MB SmartCache 4MB SmartCache TDP 15W Chipset Intel Mobile PCH (MCP package) Memory Supported Up to 32GB (2x 16GB) DDR4 2133 SO-DIMM (non-ECC) Barebone as default. -

Thinkcentre M58p with Intel AMT White Paper
ThinkCentre M58p with Intel Active Management Technology First Edition (October 2008) Contents About this document . .v Intel ME configuration. .10 Intel AMT setup and configuration . .13 Driver description . .18 Chapter 1. Introduction to Intel vPro and Intel AMT technology . .1 Chapter 6. Web user interface . .19 Acronyms . .1 Access the Web user interface . .19 Provision the Intel AMT system . .19 Chapter 2. Lenovo ThinkCentre Logging onto the client system . .19 computer equipped with Intel AMT Function in Web user interface . .20 technology . .3 Appendix A. Two examples of Intel Chapter 3. ISV solution introduction . .5 AMT setup and configuration: SMB mode and enterprise mode . .23 Chapter 4. Main features of computers Intel AMT setup and configuration steps - SMB built with Intel AMT . .7 mode . .23 Intel AMT setup and configuration steps - Enterprise mode . .23 Chapter 5. Intel AMT setup and configuration based on Lenovo Appendix B. Default configuration ThinkCentre M58p . .9 values for Intel MEBx . .25 Associated Intel AMT setup and configuration in BIOS . .9 Intel MEBx setup and configuration . .10 Appendix C. Notices . .27 Entering MEBx configuration user interface. .10 Trademarks . .28 Changing Intel ME password . .10 iii iv ThinkCentre M58p with Intel AMT White Paper About this document ® This document provides information about the application of the Intel Active ® ® Management Technology (Intel AMT) for Lenovo ThinkCentre M58p desktop computers. It provides a step-by-step approach to successfully use the Intel AMT technology. This document is intended for trained IT professionals, or those responsible for deploying new computers throughout their organizations. The readers should have basic knowledge of network and computer technology, and be familiar with these terms: TCP/IP, DHCP, IDE, DNS, Subnet Mask, Default Gateway, and Domain Name. -

8Th Generation Intel® Core™ Processors Product Brief
PRODUCT BRIEF 8TH GENERATION INTEL® CORE™ PROCESSORS Mobile U-Series: Peak Performance on the Go The new 8th generation Intel® Core™ Processor U-series—for sleek notebooks and 2 in 1s elevates your computing experience with an astounding 40 percent leap in productivity performance over 7th Gen PCs,1 brilliant 4K Ultra HD entertainment, and easier, more convenient ways to interact with your PC. With 10 hour battery life2 and robust I/O support, Intel’s first quad-core U-series processors enable portable, powerhouse thin and light PCs, so you can accomplish more on the go. Extraordinary Performance and Responsiveness With Intel’s latest power-efficient microarchitecture, advanced process technology, and silicon optimizations, the 8th generation Intel Core processor (U-series) is Intel’s fastest 15W processor3 with up to 40 percent greater productivity than 7th Gen processors and 2X more productivity vs. comparable 5-year-old processors.4 • Get fast and responsive web browsing with Intel® Speed Shift Technology. • Intel® Turbo Boost Technology 2.0 lets you work more productively by dynamically controlling power and speed—across cores and graphics— boosting performance precisely when it is needed, while saving energy when it counts. • With up to four cores, 8th generation Intel Core Processor U-series with Intel® Hyper-Threading Technology (Intel® HT Technology) supports up to eight threads, making every day content creation a compelling experience on 2 in 1s and ultra-thin clamshells. • For those on the go, PCs enabled with Microsoft Windows* Modern Standby wake instantly at the push of a button, so you don’t have to wait for your system to start up. -

Class-Action Lawsuit
Case 3:20-cv-00863-SI Document 1 Filed 05/29/20 Page 1 of 279 Steve D. Larson, OSB No. 863540 Email: [email protected] Jennifer S. Wagner, OSB No. 024470 Email: [email protected] STOLL STOLL BERNE LOKTING & SHLACHTER P.C. 209 SW Oak Street, Suite 500 Portland, Oregon 97204 Telephone: (503) 227-1600 Attorneys for Plaintiffs [Additional Counsel Listed on Signature Page.] UNITED STATES DISTRICT COURT DISTRICT OF OREGON PORTLAND DIVISION BLUE PEAK HOSTING, LLC, PAMELA Case No. GREEN, TITI RICAFORT, MARGARITE SIMPSON, and MICHAEL NELSON, on behalf of CLASS ACTION ALLEGATION themselves and all others similarly situated, COMPLAINT Plaintiffs, DEMAND FOR JURY TRIAL v. INTEL CORPORATION, a Delaware corporation, Defendant. CLASS ACTION ALLEGATION COMPLAINT Case 3:20-cv-00863-SI Document 1 Filed 05/29/20 Page 2 of 279 Plaintiffs Blue Peak Hosting, LLC, Pamela Green, Titi Ricafort, Margarite Sampson, and Michael Nelson, individually and on behalf of the members of the Class defined below, allege the following against Defendant Intel Corporation (“Intel” or “the Company”), based upon personal knowledge with respect to themselves and on information and belief derived from, among other things, the investigation of counsel and review of public documents as to all other matters. INTRODUCTION 1. Despite Intel’s intentional concealment of specific design choices that it long knew rendered its central processing units (“CPUs” or “processors”) unsecure, it was only in January 2018 that it was first revealed to the public that Intel’s CPUs have significant security vulnerabilities that gave unauthorized program instructions access to protected data. 2. A CPU is the “brain” in every computer and mobile device and processes all of the essential applications, including the handling of confidential information such as passwords and encryption keys. -

Intel Management Engine Deep Dive
Intel Management Engine Deep Dive Peter Bosch About me Peter Bosch ● CS / Astronomy student at Leiden University ● Email : [email protected] ● Twitter: @peterbjornx ● GitHub: peterbjornx ● https://pbx.sh/ About me Previous work: ● CVE-2019-11098: Intel Boot Guard bypass through TOCTOU attack on the SPI bus (Co-discovered by @qrs) Outline 1. Introduction to the Management Engine Operating System 2. The Management Engine as part of the boot process 3. Possibilities for opening up development and security research on the ME Additional materials will be uploaded to https://pbx.sh/ in the days following the talk. About the ME About ME ● Full-featured embedded system within the PCH ○ 80486-derived core ○ 1.5MB SRAM ○ 128K mask ROM ○ Hardware cryptographic engine ○ Multiple sets of fuses. ○ Bus bridges to PCH global fabric ○ Access to host DRAM ○ Access to Ethernet, WLAN ● Responsible for ○ System bringup ○ Manageability ■ KVM ○ Security / DRM ■ Boot Guard ■ fTPM ■ Secure enclave About ME ● Only runs Intel signed firmware ● Sophisticated , custom OS ○ Stored mostly in SPI flash ○ Microkernel ○ Higher level code largely from MINIX ○ Custom filesystems ○ Custom binary format ● Configurable ○ Factory programmed fuses ○ Field programmable fuses ○ SPI Flash ● Extensible ○ Native modules ○ JVM (DAL) Scope of this talk Intel ME version 11 , specifically looking at version 11.0.0.1205 Platforms: ● Sunrise Point (Core 6th, 7th generation SoC, Intel 100, 200 series chipset) ● Lewisburg ( Intel C62x chipsets ) Disclaimer ● I am in no way affiliated with Intel Corporation. ● All information presented here was obtained from public documentation or by reverse engineering firmware extracted from hardware found “in the wild”. ● Because this presentation covers a very broad and scarcely documented subject I can not guarantee accuracy of the contents. -

AMT Implementation on a UTC RETAIL 3170 POS
VICTOR , NY – CLEVELAND , OH – SCOTTSDALE , AZ AMT Implementation on a UTC RETAIL 3170 POS Controlling POS systems using Intel AMT Features UTC RETAIL 1 November 19, 2012 11823029A VICTOR , NY – CLEVELAND , OH – SCOTTSDALE , AZ Scope The document was written for use by UTC RETAIL 3170 POS customers to enable the AMT feature in the 3170 hardware. It includes step-by-step instructions to configure a 3170 system allowing AMT to be examined and exercised. Background AMT is a feature of the Intel® vPro™ Technology. From the Intel website: “Intel® vPro™ technology is a set of security and manageability capabilities built into the 3rd generation Intel Core vPro processor family, the Intel Xeon processor E3-1200 product family, Intel® chipsets, and network adapters.” Also, vPro: “Uses Intel® Active Management Technology (Intel® AMT) to facilitate remote management of platform applications, even when the platform is turned off, as long as the platform is connected to a power line and network.” A discussion of vPro is beyond the scope and purpose of this document. Full vPro implementation requires a CPU upgrade from the CPU included in a base 3170 and an IT staff that has the resources to dedicate itself to implementation and use. Every 3170 has the Standard AMT . The security features enabled by AMT require a certain level of Intel CPU, an Intel AMT enabled chipset and an Intel network interface IC. These components all exist in the 3170. To use the Standard AMT , the 3170 must have its power cord plugged into an active power plug, must be connected to an active network and its AMT system must be configured. -

Promethean Series
PROMETHEAN SERIES Ruggedized Small Form Factor CPU / GPU Systems Rugged and Reliable Performance The Promethean series of rugged, compact, and powerful small form factor systems are designed to provide highly flexible and configurable solutions for applications ranging from industrial/commercial, medical, and military. Based on COM Express (Computer-On-Module) architecture, Promethean combines high-end GPUs with latest generation of x86 processors in a ruggedized small form factor package. Promethean systems can be ordered with a variety of different CPU and GPU engines as required for your application. The system can be configured with various complements of high performance I/O as required. The architecture also supports the ability for customer defined memory type and capacities as required. Compact and Lightweight The rugged aluminum enclosure has been designed to be lightweight but strong. Deep finning provides for maximum cooling capability. Depending on Features and Benefits the requirements, the Promethean system can be mounted from the bottom, or " Provides high performance CPUs either side surface thus allowing greatest flexibility in placement, mounting, and with the latest generation of Intel Processors cable routing. The ruggedness extends beyond the robust physical housing. The Promethean system is designed for operation up to 50,000 feet elevation, and has "Order using a building block approach: an operating temperate range of 0ᵒC to +55ᵒC. If a wider temperature range is Mix and match Intel® CPUs required, a variant of the Promethean can operate at the extreme temperate range with NVIDIA® GPUs of -40ᵒC to +85ᵒC. Promethean systems also meet MIL-STD-810H for shock and "Highly configurable. -
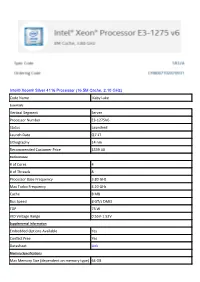
Intel® Xeon® Silver 4116 Processor (16.5M Cache, 2.10 Ghz) Code Name Kaby Lake
Intel® Xeon® Silver 4116 Processor (16.5M Cache, 2.10 GHz) Code Name Kaby Lake Essentials Vertical Segment Server Processor Number E3-1275V6 Status Launched Launch Date Q1'17 Lithography 14 nm Recommended Customer Price $339.00 Performance # of Cores 4 # of Threads 8 Processor Base Frequency 3.80 GHz Max Turbo Frequency 4.20 GHz Cache 8 MB Bus Speed 8 GT/s DMI3 TDP 73 W VID Voltage Range 0.55V-1.52V Supplemental Information Embedded Options Available Yes Conflict Free Yes Datasheet Link Memory Specifications Max Memory Size (dependent on memory type) 64 GB Memory Types DDR4-2400, DDR3L-1866 Max # of Memory Channels 2 Max Memory Bandwidth 37.5 GB/s ECC Memory Supported ‡ Yes Graphics Specifications Processor Graphics ‡ Intel® HD Graphics P630 Graphics Base Frequency 350 MHz Graphics Max Dynamic Frequency 1.15 GHz Graphics Video Max Memory 1.7 GB Graphics Output eDP/DP/HDMI/DVI 4K Support Yes, at 60Hz Max Resolution (HDMI 1.4)‡ 4096x2160@24Hz Max Resolution (DP)‡ 4096x2304@60Hz Max Resolution (eDP - Integrated Flat Panel)‡ 4096x2304@60Hz Max Resolution (VGA)‡ N/A DirectX* Support 12 OpenGL* Support 4.4 Intel® Quick Sync Video Yes Intel® InTru™ 3D Technology Yes Intel® Clear Video HD Technology Yes Intel® Clear Video Technology Yes # of Displays Supported ‡ 3 Device ID 0x591D Expansion Options Scalability 1S Only PCI Express Revision 3.0 PCI Express Configurations ‡ 1x16, 2x8, 1x8+2x4 Max # of PCI Express Lanes 16 Package Specifications Sockets Supported FCLGA1151 Max CPU Configuration 1 Package Size 37.5mm x 37.5mm Low Halogen Options Available