Decoupling State from Control in Software-Defined Networking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Jeannie: Granting Java Native Interface Developers Their Wishes
Jeannie: Granting Java Native Interface Developers Their Wishes Martin Hirzel Robert Grimm IBM Watson Research Center New York University [email protected] [email protected] Abstract higher-level languages and vice versa. For example, a Java Higher-level languages interface with lower-level languages project can reuse a high-performance C library for binary such as C to access platform functionality, reuse legacy li- decision diagrams (BDDs) through the Java Native Inter- braries, or improve performance. This raises the issue of face [38] (JNI), which is the standard FFI for Java. how to best integrate different languages while also recon- FFI designs aim for productivity, safety, portability, and ciling productivity, safety, portability, and efficiency. This efficiency. Unfortunately, these goals are often at odds. For paper presents Jeannie, a new language design for integrat- instance, Sun’s original FFI for Java, the Native Method In- ing Java with C. In Jeannie, both Java and C code are nested terface [52, 53] (NMI), directly exposed Java objects as C within each other in the same file and compile down to JNI, structs and thus provided simple and fast access to object the Java platform’s standard foreign function interface. By fields. However, this is unsafe, since C code can violate Java combining the two languages’ syntax and semantics, Jean- types, notably by storing an object of incompatible type in a nie eliminates verbose boiler-plate code, enables static error field. Furthermore, it constrains garbage collectors and just- detection across the language boundary, and simplifies dy- in-time compilers, since changes to the data representation namic resource management. -

Spam Experts Incoming Email Filter Eine Leistungsstarke Lösung Zum Schutz Von Netzwerken Vor Eingehenden Spams Und Malware, Dank Der Webhosts Zeit Und Geld Sparen
DATENBLATT Spam Experts Incoming Email Filter Eine leistungsstarke Lösung zum Schutz von Netzwerken vor eingehenden Spams und Malware, dank der Webhosts Zeit und Geld sparen. Eingehende Spam, Ransomware und Phishing-Versuche können für jeden Internetdienstanbieter ein Risiko darstellen. SolarWinds® Spam Experts hilft Webhosts und ISPs/ Telekommunikationsanbietern dabei, den E-Mail-Schutz zu verbessern. Das Lösungsangebot umfasst erschwingliche Filterung eingehender E-Mails. Diese Lösungen basieren auf der intelligenten Protection & Filtering Engine, die permanent aktualisiert wird, um neue Bedrohungen zu erkennen. Die Lösung kann in einer redundanten Cloud-Umgebung oder lokal bereitgestellt werden. FUNKTIONSWEISE Eingangsfilterung Der SolarWinds Spam Experts-Eingangsfilter ist eine Gatewaylösung. Die Aktivierung erfolgt über eine einfache DNS-Anpassung. Sobald die MX-Einträge geändert wurden, Internet Filterung Protokol- gehen alle eingehenden E-Mails zunächst an unser System, lierung wo sie gefiltert und anschließend an die unveränderten Ziel- Mailserver Ihrer Kunden übermittelt werden. Zentralisierte Verwaltung Die Lösung bietet erstklassige Abwehr, die vor Ihrer E-Mail- Infrastruktur ausgeführt wird, und trennt mittels erweiterter rchiierung uarantne Filterungsalgorithmen und Methoden zur Erkennung von Spam-Mustern rechtmäßige von unrechtmäßigen E-Mails. Mit Spam Experts lokal oder gehostete loud einer Genauigkeitsrate von fast 100 % bietet sie vollständigen Schutz für den Posteingang. Potenziell schädliche Mitteilungen werden in eine -

JNI – C++ Integration Made Easy
JNI – C++ integration made easy Evgeniy Gabrilovich Lev Finkelstein [email protected] [email protected] Abstract The Java Native Interface (JNI) [1] provides interoperation between Java code running on a Java Virtual Machine and code written in other programming languages (e.g., C++ or assembly). The JNI is useful when existing libraries need to be integrated into Java code, or when portions of the code are implemented in other languages for improved performance. The Java Native Interface is extremely flexible, allowing Java methods to invoke native methods and vice versa, as well as allowing native functions to manipulate Java objects. However, this flexibility comes at the expense of extra effort for the native language programmer, who has to explicitly specify how to connect to various Java objects (and later to disconnect from them, to avoid resource leak). We suggest a template-based framework that relieves the C++ programmer from most of this burden. In particular, the proposed technique provides automatic selection of the right functions to access Java objects based on their types, automatic release of previously acquired resources when they are no longer necessary, and overall simpler interface through grouping of auxiliary functions. Introduction The Java Native Interface1 is a powerful framework for seamless integration between Java and other programming languages (called “native languages” in the JNI terminology). A common case of using the JNI is when a system architect wants to benefit from both worlds, implementing communication protocols in Java and computationally expensive algorithmic parts in C++ (the latter are usually compiled into a dynamic library, which is then invoked from the Java code). -

Achieving Redundancy with Hosting Controller
Perspective In the perilous world of hosting one of the most sought-after features is failover capability. Most hosting providers desire a redundant setup in order to keep their content highly available (H.A) and minimize the chances of downtime in case of a disaster. Why is Redundancy Important? Hosting businesses usually require their data-centric internet applications to be served by more than one servers in a highly available cluster. Redundancy ensures that the data of a provider is always safe and readily available. Maximizing uptime is one of the prime goals of ISPs, ITSPs, Telcos, HSPs, MSPs and other Cloud providers. Redundancy can and does help. Hosting Controller Pushing Boundaries to accomplish end-to-end Redundancy Let’s explore the failover capabilities inherent in Hosting Controller Panel Exchange High Web DNS Replication Redundancy Availability Redundancy HC HC HC proposes the setup of an IIS Web manages the DNS redundancy in HC holds the ability of offering high Farm for achieving web a proficient manner. DNS zones availability and site resilience for redundancy. There are various can be replicated from the Exchange through its ways to design the infrastructure Primary DNS to the Secondary or holds the provision for control Primary/Secondary arrangement. of a Web Farm however HC Tertiary DNS for that matter. The panel redundancy through its This connotes the staging of recommends a Homogeneous replication is handled through simple multi portal server Exchange servers in a Web Farm with Shared Hosting Controller’s own capability. Primary/Secondary arrangement Configuration. interface. HC Master Control Portal Servers A successful installation of HC ends up creating an admin site in IIS called HostingController. -

T U M a Digital Wallet Implementation for Anonymous Cash
Technische Universität München Department of Informatics Bachelor’s Thesis in Information Systems A Digital Wallet Implementation for Anonymous Cash Oliver R. Broome Technische Universität München Department of Informatics Bachelor’s Thesis in Information Systems A Digital Wallet Implementation for Anonymous Cash Implementierung eines digitalen Wallets for anonyme Währungen Author Oliver R. Broome Supervisor Prof. Dr.-Ing. Georg Carle Advisor Sree Harsha Totakura, M. Sc. Date October 15, 2015 Informatik VIII Chair for Network Architectures and Services I conrm that this thesis is my own work and I have documented all sources and material used. Garching b. München, October 15, 2015 Signature Abstract GNU Taler is a novel approach to digital payments with which payments are performed with cryptographically generated representations of actual currencies. The main goal of GNU Taler is to allow taxable anonymous payments to non-anonymous merchants. This thesis documents the implementation of the Android version of the GNU Taler wallet, which allows users to create new Taler-based funds and perform payments with them. Zusammenfassung GNU Taler ist ein neuartiger Ansatz für digitales Bezahlen, bei dem Zahlungen mit kryptographischen Repräsentationen von echten Währungen getätigt werden. Das Hauptziel von GNU Taler ist es, versteuerbare, anonyme Zahlungen an nicht-anonyme Händler zu ermöglichen. Diese Arbeit dokumentiert die Implementation der Android-Version des Taler-Portemonnaies, der es Benutzern erlaubt, neues Taler-Guthaben zu erzeugen und mit ihnen Zahlungen zu tätigen. I Contents 1 Introduction 1 1.1 GNU Taler . .2 1.2 Goals of the thesis . .2 1.3 Outline . .3 2 Implementation prerequisites 5 2.1 Native libraries . .5 2.1.1 Libgcrypt . -
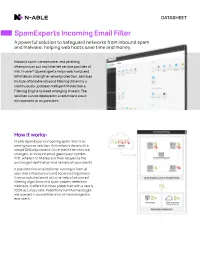
Spamexperts Incoming Email Filter a Powerful Solution to Safeguard Networks from Inbound Spam and Malware, Helping Web Hosts Save Time and Money
DATASHEET SpamExperts Incoming Email Filter A powerful solution to safeguard networks from inbound spam and malware, helping web hosts save time and money. Inbound spam, ransomware, and phishing attempts can put any internet service provider at risk. N-able™ SpamExperts helps web hosts and ISPs/telcos strengthen email protection. Services include affordable inbound filtering driven by a continuously updated Intelligent Protection & Filtering Engine to meet emerging threats. The solution can be deployed in a redundant cloud environment or on premises. How it works: N-able SpamExperts incoming spam filter is an email gateway solution. Activation is done with a simple DNS adjustment. Once the MX records are changed, all inbound email goes to our system first, where it is filtered and then relayed to the unchanged destination mail servers of your clients. It provides first-level defense running in front of your mail infrastructure and separates legitimate from unsolicited email with the help of advanced filtering algorithms and spam pattern detection methods. It offers full inbox protection with a nearly 100% accuracy rate. Potentially harmful messages are queued in quarantine and can be managed by end users. Helps save resources and money • Protects networks against the latest email-based threats. • Saves network resources with an efficient first-level incoming filter defense. • Helps save money with competitive and affordable licenses. Offers dual deployment options and integrates with a broad range of tools • Cloud or on-premises deployment. • Free add-ons to integrate with the most popular control panels and other email collaboration tools. • Multiple branding options available. Global statistics Gives customers and users visibility and control over their email flows • Empowers users to manage their email flows and gain real-time visibility into threats. -

Nacldroid: Native Code Isolation for Android Applications
NaClDroid: Native Code Isolation for Android Applications Elias Athanasopoulos1, Vasileios P. Kemerlis2, Georgios Portokalidis3, and Angelos D. Keromytis4 1 Vrije Universiteit Amsterdam, The Netherlands [email protected] 2 Brown University, Providence, RI, USA [email protected] 3 Stevens Institute of Technology, Hoboken, NJ, USA [email protected] 4 Columbia University, New York, NY, USA [email protected] Abstract. Android apps frequently incorporate third-party libraries that contain native code; this not only facilitates rapid application develop- ment and distribution, but also provides new ways to generate revenue. As a matter of fact, one in two apps in Google Play are linked with a library providing ad network services. However, linking applications with third-party code can have severe security implications: malicious libraries written in native code can exfiltrate sensitive information from a running app, or completely modify the execution runtime, since all native code is mapped inside the same address space with the execution environment, namely the Dalvik/ART VM. We propose NaClDroid, a framework that addresses these problems, while still allowing apps to include third-party code. NaClDroid prevents malicious native-code libraries from hijacking Android applications using Software Fault Isolation. More specifically, we place all native code in a Native Client sandbox that prevents uncon- strained reads, or writes, inside the process address space. NaClDroid has little overhead; for native code running inside the NaCl sandbox the slowdown is less than 10% on average. Keywords: SFI, NaCl, Android 1 Introduction Android is undoubtedly the most rapidly growing platform for mobile devices, with estimates predicting one billion Android-based smartphones shipping in 2017 [12]. -

Developing and Benchmarking Native Linux Applications on Android
Developing and Benchmarking Native Linux Applications on Android Leonid Batyuk, Aubrey-Derrick Schmidt, Hans-Gunther Schmidt, Ahmet Camtepe, and Sahin Albayrak Technische Universit¨at Berlin, 10587 Berlin, Germany {aubrey.schmidt,leonid.batyuk,hans-gunther.schmidt,ahmet.camtepe, sahin.albayrak}@dai-labor.de http://www.dai-labor.de Abstract. Smartphones get increasingly popular where more and more smartphone platforms emerge. Special attention was gained by the open source platform Android which was presented by the Open Handset Al- liance (OHA) hosting members like Google, Motorola, and HTC. An- droid uses a Linux kernel and a stripped-down userland with a custom Java VM set on top. The resulting system joins the advantages of both environments, while third-parties are intended to develop only Java ap- plications at the moment. In this work, we present the benefit of using native applications in Android. Android includes a fully functional Linux, and using it for heavy computational tasks when developing applications can bring in substantional performance increase. We present how to develop native applications and software components, as well as how to let Linux appli- cations and components communicate with Java programs. Additionally, we present performance measurements of native and Java applications executing identical tasks. The results show that native C applications can be up to 30 times as fast as an identical algorithm running in Dalvik VM. Java applications can become a speed-up of up to 10 times if utilizing JNI. Keywords: software, performance, smartphones, android, C, Java. 1 Introduction With the growing customer interest in smartphones the number of available platforms increases steadily. -

Servers Prior to Use
TECANA AMERICAN UNIVERSITY BACHELOR OF SCIENCE – Information System Engineering Trabajo Especial de Grado Internet Service Provider – Hosting Automation Software Presentado por: Bhamidipati Venkata Gopala Anirudha Sharma Como requisito para optar al titulo: Bachelor of Science in Information System Engineering Por Academic Dirección: Dr. Jesús Reinaldo Rivas Zabaleta, Ph.D. Por Academic Staff: Dr. Raúl Roldán, Ph.D. Caracas, 15 de Agosto de 2005 1 TECANA AMERICAN UNIVERSITY BACHELOR OF SCIENCE – Information System Engineering Trabajo Especial de Grado Internet Service Provider – Hosting Automation Software Presentado por: Bhamidipati Venkata Gopala Anirudha Sharma Como requisito para optar al titulo: Bachelor of Science in Information System Engineering Por Academic Dirección: Dr. Jesús Reinaldo Rivas Zabaleta, Ph.D. Por Academic Staff: Dr. Raúl Roldán, Ph.D. Caracas, 15 de Agosto de 2005 “Por la presente juro y doy fe que soy el único autor del presente trabajo especial de grado y que su contenido es consecuencia de mi trabajo, experiencia e investigación académica” _______________________________________________ Autor: Bhamidipati Venkata Gopala Anirudha Sharma Fecha:14-Aug-2005 Ciudad: Caracas, Venezuela. 2 About the Industry Technical Reviewer: Ing. Oswaldo José Inojosa Moya: Ex – CTO, Dayco Telecom C.A. He is one of the founder members of the original team who lead the formation of the 1st Data Center in Venezuela, and was instrumental in the formation of high availability services in the country. He came to lead a multi-disciplinary task force of operations at Daycohost, from a large transnational ATM Solution Provider called Newbridge which later was absorbed Alcatel. He has graduated from the prestigious Simon Bolivar University in Caracas, Venezuela as “Electronics Engineer “and later on specialized in “Business Finance” from the same university. -

Java Native Interface Application Notes
Java Native Interface Application Notes Da Ke 4/5/2009 ECE 480 Spring 2009, Design Team 3 Department of Electrical and Computer Engineering Michigan State University Abstract Java is one of most widely used programming language today due to its openness, ability to scale up and portability. The language is design to have a simpler object model and fewer low-level facilities like pointer methods in C/C++. Sometime this could impose a limitation on what a program can do. This application note will explore various ways of implementation that will allow Java to interact with some programs that are written in lower level language. Keywords: Java, JVM, JNI, Linux, Windows, Operating System, Native interface, Native code Introduction Most modern high level programming languages today are capable of handling what once consider trivial tasks for developers like memory management. However, this doesn't come without cost. A Java application does not interact with underlying system infrastructure directly instead it first compile source code to bytecode and run on Java virtual machine which itself is an application that run on top of the operating system. The Java virtual machine acts like a mediator between the application and the operating system. Most modern implementations of Java Virtual Machine does include several interfaces and libraries that we can utilize to allow Java applications to perform some system level tasks and even speed up the execution of the program by handing over some more resource-intense operations to programs that are runs natively on the machine. Objective This application note will explain different approaches to implement system level functions using Java Programming Language. -

Calling C Library Routines from Java Using the Java Native Interface
Numerical Algorithms Group Title: Calling C Library Routines from Java Using the Java Native Interface Summary: This paper presents a technique for calling C library routines directly from Java, saving you the trouble of rewriting code in Java and gaining portability via Java Virtual Machines. The NAG C Library from the Numerical Algorithms Group (www.nag.com) is a mathematical and statistical library containing routines for linear algebra, optimization, quadrature, differential equations, regression analysis, and time-series analysis. Although written in C, the library’s functionality can be accessed from other languages. On PCs, DLL versions of the library can be exploited in many ways, including calling from Microsoft Excel, Visual Basic, or Borland Delphi. Consequently, NAG C Library users often ask if they can call it from Java. One way to perform numerical computations is by creating Java classes that implement the required functionality. However, this is often difficult and time consuming. In this article, I present a technique for calling C Library routines directly from Java. Apart from avoiding rewriting numerical code in Java, using existing C code has another advantage. Java is portable -- compiled programs run on any machine with a Java Virtual Machine (VM). To accomplish this, the Java compiler does not compile to a machine- dependent assembler, but to machine-independent Run-Time Error Messages bytecode that is interpreted at run time by the VM. Although the interpreter is efficient, no interpreted If you get a Java error message, such as program runs as fast as programs compiled to assembler “interface library CJavaInterface cannot be code. -

File-Based Sharing for Dynamically Compiled Code on Dalvik Virtual Machine
File-Based Sharing For Dynamically Compiled Code On Dalvik Virtual Machine Yao-Chih Huang, Yu-Sheng Chen, Wuu Yang, Jean Jyh-Jiun Shann Department of Computer Science National Chiao Tung University Hsinchu City 300, Taiwan fychuang, yusheng, wuuyang, [email protected] Abstract—Memory footprint is considered as an impor- Generally speaking, native code that is generated by a tant design issue for embedded systems. Sharing dynamically dynamic compiler would be stored at a memory area called compiled code among virtual machines can reduce memory code cache. In the Android platform, every virtual machine footprint and recompilation overhead. On the other hand, sharing writable native code may cause security problems, would allocate its own code cache. Thus, native code might due to support of native function call such as Java Native be duplicated in several code cache and result in wasting Interface (JNI). We propose a native-code sharing mechanism of memory. On the other hand, same native code may be that ensures the security for Dalvik virtual machine (VM) on compiled repeatedly and result in reduced performance. the Android platform. Dynamically generated code is saved in So, sharing native code in the code cache among virtual a file and is shared with memory mapping when other VMs need the same code. Protection is granted by controlling of file machines can reduce memory footprint. This sharing ap- writing permissions. To improve the security, we implement a proach also avoids repeated compilation of the same code daemon process, named Query Agent, to control all accesses and hence improve performance. to the native code and maintain all the information of traces, There exist two works about code sharing in VM : which are the units of the compilation in the Dalvik VM.