Certificate Authority
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Focus on S/MIME
The University of Saskatchewan Department of Computer Science Technical Report #2011-03 Cryptographic Security for Emails: A Focus on S/MIME Minhaz Fahim Zibran Department of Computer Science University of Saskatchewan Email: [email protected] Abstract In this paper I present a study on \S/MIME", which has become the industry standard for secure email exchange. Based on existing literature review, the study examines S/MIME in depth with specific emphasis on its architecture, strengths, and deficiencies. The study also identifies usability issues related to S/MIME enabled email clients, which indicate scopes for further improvements in those implementations. Obstacles in the adoption of S/MIME are also identified indicating what is required for its successful adoption in the community. In presenting the study, the paper contributes in two ways: (a) for any newcomer in the field of cryptography this paper will be a useful resource to quickly learn about S/MIME in a fair level of detail, (b) the indication about limitations of S/MIME and its implementations reveals an avenue for further research in the area of email security, which may result in improvement of S/MIME itself, or its implementations in the email clients. Keywords: Email Security, S/MIME, MIME, PGP, PKI, Certificate, Email Authentication, Email Encryption, Key Management 1 Introduction Email has been a very common medium of communication these days. It somewhat re- places the traditional surface mail and many of the traditional ways of communication [32]. Today people send and read emails from their personal computers, business workstation, PDAs and even cell phones. -

Can We Trust Cryptographic Software? Cryptographic Flaws in GNU Privacy Guard V1.2.3
Can We Trust Cryptographic Software? Cryptographic Flaws in GNU Privacy Guard v1.2.3 Phong Q. Nguyen CNRS/Ecole´ normale sup´erieure D´epartement d’informatique 45 rue d’Ulm, 75230 Paris Cedex 05, France. [email protected] http://www.di.ens.fr/˜pnguyen Abstract. More and more software use cryptography. But how can one know if what is implemented is good cryptography? For proprietary soft- ware, one cannot say much unless one proceeds to reverse-engineering, and history tends to show that bad cryptography is much more frequent than good cryptography there. Open source software thus sounds like a good solution, but the fact that a source code can be read does not imply that it is actually read, especially by cryptography experts. In this paper, we illustrate this point by examining the case of a basic In- ternet application of cryptography: secure email. We analyze parts of thesourcecodeofthelatestversionofGNUPrivacyGuard(GnuPGor GPG), a free open source alternative to the famous PGP software, com- pliant with the OpenPGP standard, and included in most GNU/Linux distributions such as Debian, MandrakeSoft, Red Hat and SuSE. We ob- serve several cryptographic flaws in GPG v1.2.3. The most serious flaw has been present in GPG for almost four years: we show that as soon as one (GPG-generated) ElGamal signature of an arbitrary message is released, one can recover the signer’s private key in less than a second on a PC. As a consequence, ElGamal signatures and the so-called ElGamal sign+encrypt keys have recently been removed from GPG. -

Encryption Procedure
Encrypting Software for Transmission to NIST 1. Scope NIST requires that all software submitted by the participants be signed and encrypted. Signing is done with the participant’s private key, and encrypting is done with the NIST project public key, which is published at http://www.nist.gov/itl/iad/ig/encrypt.cfm. NIST will validate all submitted materials using the participant’s public key, and the authenticity of that key will be verified using the key fingerprint. This fingerprint must be submitted to NIST as part of the signed participant agreement. By encrypting the submissions, we ensure privacy; by signing the submission, we ensure authenticity (the software actually belongs to the submitter). NIST will not take ownership of any submissions that are not signed and encrypted. All cryptographic operations (signing and encrypting) shall be performed with software that implements the OpenPGP standard, as described in Internet RFC 4880. The freely available Gnu Privacy Guard (GPG) software, available at www.gnupg.org, is one such implementation. 2. Submission of software to NIST NIST requires that all software submitted by the participants be signed and encrypted. Two keys pairs are needed: • Signing is done with the software provider's private key, and • Encryption is done with the NIST project public key, which is available at http://www.nist.gov/itl/iad/ig/encrypt.cfm 2.1. Project Specific Parameters The values for the project specific parameters (ProjectName, ProjectPublicKey, and ProjectEmail) mentioned in this document are found at http://www.nist.gov/itl/iad/ig/encrypt.cfm 1 2.2. Creating participant cryptographic key pair The steps below show how to create a public/private key pair and fingerprint using the GPG software. -
Diffie-Hellman (1976) – RSA (1977) – More Recently: ID-Based Encryption (2001), Functional Encryption (2011)…
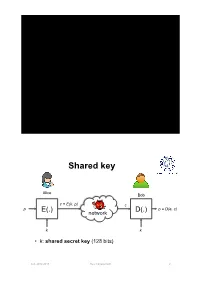
Key Management Shared key Alice Bob c = E(k, p) c p E(.) D(.) p = D(e, c) network k k • k: shared secret key (128 bits) A.A. 2012-2013 Key management 2 Pairwise keys • Each pair of users shares an long-term secret key Alice Bob • Properties • Every user stores (n -1) keys • The overall number of keys is O(n2) Carol Eve Dave A.A. 2012-2013 Key management 3 Pairwise keys • Pros – If a subject is compromised only its communications are compromised; • communications between two other subjects are not compromised • We cannot do any better! • Cons – Poor scalability: the number of keys is quadratic in the number of subjects – Poor scalability: a new member’s joining and a member’s leaving affect all current members A.A. 2012-2013 Key management 4 Trusted Third Party • Online Trusted Third Party (TTP) – Each user shares a long-term secret key with TTP TTP – Every user stores one key – The overall number of keys is n KA KB • TTP is a single point of failure – TTP must be always online A B – TTP knows all the keys • TTP can read all msg between Alice and Bob KAB • TTP can impersonate any party A.A. 2012-2013 Key management 5 Key distribution: a toy protocol Alice wants a shared key with Bob. Eavesdropping security only Bob (kB) Alice (kA) TTP “Alice wants key with Bob” choose E(KA, “A, B” || KAB) random kAB ticket ticket ← E(KB, “A, B” || KAB) kAB kAB Subject to replay attacks A.A. 2012-2013 Key management 6 Key distribution: toy protocol • Insecure against replay attacks (active adversary) – Attacker records session between Alice and merchant Bob • For example: an order – Attacker replays session to Bob • Bob thinks Alice is ordering another copy of the book A.A. -

Towards a Hybrid Public Key Infrastructure (PKI): a Review
Towards a Hybrid Public Key Infrastructure (PKI): A Review Priyadarshi Singh, Abdul Basit, N Chaitanya Kumar, and V. Ch. Venkaiah School of Computer and Information Sciences, University of Hyderabad, Hyderabad-500046, India Abstract. Traditional Certificate- based public key infrastructure (PKI) suffers from the problem of certificate overhead like its storage, verification, revocation etc. To overcome these problems, idea of certificate less identity-based public key cryptography (ID-PKC) was proposed by Shamir. This is suitable for closed trusted group only. Also, this concept has some inherent problems like key escrow problem, secure key channel problem, identity management overhead etc. Later on, there had been several works which tried to combine both the cryptographic techniques such that the resulting hybrid PKI framework is built upon the best features of both the cryptographic techniques. It had been shown that this approach solves many problems associated with an individual cryptosystem. In this paper, we have reviewed and compared such hybrid schemes which tried to combine both the certificate based PKC and ID-based PKC. Also, the summary of the comparison, based on various features, is presented in a table. Keywords: Certificate-based PKI; Identity-based public key cryptography (ID-PKC); Hybrid PKI 1 INTRODUCTION Public key infrastructure (PKI) and public key cryptography (PKC) [12] plays a vital role with four major components of digital security: authentication, integrity, confidentiality and non-repudiation. Infact, PKI enables the use of PKC through key management. The ”efficient and secure management of the key pairs during their whole life cycle" is the purpose of PKI, which involves key generation, key distribution, key renewal, key revocation etc [11]. -

Ansi/Scte 23-2 2017
ENGINEERING COMMITTEE Data Standards Subcommittee AMERICAN NATIONAL STANDARD ANSI/SCTE 23-2 2017 DOCSIS 1.1 Part 2: Baseline Privacy Plus Interface ANSI/SCTE 23-2 2017 NOTICE The Society of Cable Telecommunications Engineers (SCTE) Standards and Operational Practices (hereafter called “documents”) are intended to serve the public interest by providing specifications, test methods and procedures that promote uniformity of product, interchangeability, best practices and ultimately the long term reliability of broadband communications facilities. These documents shall not in any way preclude any member or non-member of SCTE from manufacturing or selling products not conforming to such documents, nor shall the existence of such standards preclude their voluntary use by those other than SCTE members. SCTE assumes no obligations or liability whatsoever to any party who may adopt the documents. Such adopting party assumes all risks associated with adoption of these documents, and accepts full responsibility for any damage and/or claims arising from the adoption of such documents. Attention is called to the possibility that implementation of this document may require the use of subject matter covered by patent rights. By publication of this document, no position is taken with respect to the existence or validity of any patent rights in connection therewith. SCTE shall not be responsible for identifying patents for which a license may be required or for conducting inquiries into the legal validity or scope of those patents that are brought to its attention. Patent holders who believe that they hold patents which are essential to the implementation of this document have been requested to provide information about those patents and any related licensing terms and conditions. -

Security Target Document
Security Target Document Passport Certificate Server Ver. 4.1.1 Prepared for: Common Criteria EAL2 (augmented) 30 April 2002 2225 Sheppard Ave, Suite 1700 Toronto, Ontario, Canada M2J 5C2 TEL: 416-756-2324 FAX: 416-756-7346 [email protected] www.dvnet.com Passport Certificate Server V.4.1.1 Security Target 30 April 2002 Common Criteria EAL 2 (augmented) Version 1.00 TABLE OF CONTENTS 1 Introduction ............................................................................................................................................ 1 1.1 Security Target Identification......................................................................................................... 1 1.2 Security Target Overview............................................................................................................... 1 1.3 Common Criteria Conformance .....................................................................................................1 2 TOE Description..................................................................................................................................... 2 2.1 Product Deployment....................................................................................................................... 2 2.2 Product Functions........................................................................................................................... 2 2.3 Product Description ........................................................................................................................ 3 2.3.1 Platform -

Security Analysis and Trust Models in Wireless Networks Lela Mirtskhulava
Security Analysis and Trust Models in Wireless Networks Lela Mirtskhulava [email protected] Department of Computer Sciences Faculty of Exact and Natural Sciences Iv. Javakhishvili Tbilisi State University University str., 13, Georgia In the given work, we analyse the serious weaknesses recently discovered in WPA2 (Wi-Fi Protected Access 2) in October 2017 and KRACK (Key Reinstallation Attack) attack on WPA2 announced by Computer Science Scientists. The KRACKs were introduced to abuse design flaws in cryptographic protocols to reinstall an already-in-use key. Several types of cryptographic Wi-Fi handshakes are affected by the attack. There are different forms of trust to address different types of network security problems and reduce risk in certain conditions. This paper explores the trust models applied by various cryptographic schemes: a) the web of trust employed by Pretty Good Privacy (PGP) where users using their own set of trusted public keys, b) Kerberos, a secret key distribution scheme using a trusted third party, c) certificates, which allow a set of trusted third parties to authenticate each other and, by implication, each other's users. Each of the above mentioned trust models differs in complexity, scope, scalability and general applicability. Which model of trust to apply in certain circumstances and types of wireless networks are discussed in the given paper. It describes the major security issues and their techniques of building trust model by monitoring network behavior. It is intended to use secure and faster cryptographic solution for Wi-Fi networks security by using an open source public-key NTRU cryptosystem that uses lattice-based cryptography. -

AWS Key Management Service Cryptographic Details
AWS Key Management Service Cryptographic Details August 2016 Amazon Web Services – AWS KMS Cryptographic Details August 2016 © 2016, Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents AWS’s current product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS’s products or services, each of which is provided “as is” without warranty of any kind, whether express or implied. This document does not create any warranties, representations, contractual commitments, conditions or assurances from AWS, its affiliates, suppliers or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers. Page 2 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Contents Abstract 4 Introduction 4 Design Goals 5 Background 7 Cryptographic Primitives 7 Basic Concepts 9 Customer’s Key Hierarchy 11 Use Cases 13 Amazon EBS Volume Encryption 13 Envelope Encryption 14 Customer Master Keys 17 Imported Master Keys 19 Enable and Disable Key 22 Key Deletion 22 Rotate Customer Master Key 23 Customer Data Operations 23 Application-Specific Data Keys 24 Encrypt 26 Decrypt 26 Re-Encrypting an Encrypted Object 28 Internal Communication Security 29 HSA Security Boundary 29 Quorum-Signed Commands 30 Authenticated Sessions 31 Domains and the Domain State 32 Page 3 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Domain Keys 33 Exported Domain Tokens 33 Managing Domain State 34 Durability Protection 36 References 38 Appendix - Abbreviations and Keys 40 Abbreviations 40 Keys 41 Contributors 42 Document Revisions 42 Abstract AWS Key Management Service (AWS KMS) provides cryptographic keys and operations scaled for the cloud. -

SIGMA: the 'Sign-And-Mac' Approach to Authenticated Diffie-Hellman and Its Use in the IKE Protocols
SIGMA: the `SIGn-and-MAc' Approach to Authenticated Diffie-Hellman and its Use in the IKE Protocols ∗ Hugo Krawczyky June 12, 2003 Abstract We present the SIGMA family of key-exchange protocols and the \SIGn-and-MAc" approach to authenticated Diffie-Hellman underlying its design. The SIGMA protocols provide perfect forward secrecy via a Diffie-Hellman exchange authenticated with digital signatures, and are specifically designed to ensure sound cryptographic key exchange while supporting a variety of features and trade-offs required in practical scenarios (such as optional identity protection and reduced number of protocol rounds). As a consequence, the SIGMA protocols are very well suited for use in actual applications and for standardized key exchange. In particular, SIGMA serves as the cryptographic basis for the signature-based modes of the standardized Internet Key Exchange (IKE) protocol (versions 1 and 2). This paper describes the design rationale behind the SIGMA approach and protocols, and points out to many subtleties surrounding the design of secure key-exchange protocols in general, and identity-protecting protocols in particular. We motivate the design of SIGMA by comparing it to other protocols, most notable the STS protocol and its variants. In particular, it is shown how SIGMA solves some of the security shortcomings found in previous protocols. ∗A shortened version of this paper appears in the proceedings of CRYPTO'03. For further information related to the SIGMA protocols see http://www.ee.technion.ac.il/~hugo/sigma.html yEE Department, Technion, Haifa, Israel, and IBM T.J. Watson Research Center. Email: [email protected] 1 Contents 1 Introduction 1 2 Preliminaries: On the Security of Key-Exchange Protocols 4 2.1 Overview of the security model and requirements . -

Dell EMC Unity: Data at Rest Encryption a Detailed Review
Technical White Paper Dell EMC Unity: Data at Rest Encryption A Detailed Review Abstract This white paper explains the Data at Rest Encryption feature, which provides controller-based encryption of data stored on Dell EMC™ Unity storage systems to protect against unauthorized access to lost or stolen drives or system. The encryption technology as well as its implementation on Dell EMC Unity storage systems are discussed. June 2021 H15090.6 Revisions Revisions Date Description May 2016 Initial release – Unity OE 4.0 July 2017 Updated for Unity OE 4.2 June 2021 Template and format updates. Updated for Unity OE 5.1 Acknowledgments Author: Ryan Poulin The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. This document may contain certain words that are not consistent with Dell's current language guidelines. Dell plans to update the document over subsequent future releases to revise these words accordingly. This document may contain language from third party content that is not under Dell's control and is not consistent with Dell's current guidelines for Dell's own content. When such third party content is updated by the relevant third parties, this document will be revised accordingly. Copyright © 2016-2021 Dell Inc. or its subsidiaries. All Rights Reserved. Dell Technologies, Dell, EMC, Dell EMC and other trademarks are trademarks of Dell Inc. -

Adding Public Key Security to SSH
Adding Public Key Security to SSH A Thesis Submitted to the Faculty in partial fulfillment of the requirements for the degree of Master of Science in Computer Science by Yasir Ali DARTMOUTH COLLEGE Hanover, New Hampshire Feb, 20th, 2003 Examining Committee: ____________________________ Sean Smith (chair) ____________________________ Edward Feustel ____________________________ Christopher Hawblitzel !!!!!!!!!____________________________ !!!!!!!!!Carol Folt !!!!!!!!! Dean of Graduate Studies 1 2 Abstract SSH, the Secure Shell, is a popular software-based approach to network security. It is a protocol that allows user to log into another computer over a network, to execute commands in a remote machine, and to move files from one machine to another. It provides authentication and encrypted communications over unsecured channels. However, SSH protocol has an inherent security flaw. It is vulnerable to the “man-in-the- middle Attack”, when a user establishes his first SSH connection from a particular client to a remote machine. My thesis entails designing, evaluating and prototyping a public key infrastructure which can be used with the SSH2 protocol, in an academic setting, thus eliminating this vulnerability due to the man in the middle attack. The approach presented is different from the one that is based on the deployment of a Certificate Authority. My scheme does not necessarily require third party verification using a Certificate Authority; it is decentralized in nature and is relatively easy to set up. Keywords used: SSH, PKI, digital certificates, Certificate Authority, certification path, LDAP servers, Certificate Revocation List, X509v3 Certificate, OpenSSL, mutual authentication, and tunneled authentication. 3 Acknowledgments I want to thank Professor Sean Smith for his guidance, assistance and unremitting support over the last two years.