On Computer Security by the CERN Computer Security Team ( (Edition of 2019)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IJIMAI20163 6.Pdf
INTERNATIONAL JOURNAL OF INTERACTIVE MULTIMEDIA AND ARTIFICIAL INTELLIGENCE ISSN: 1989-1660–VOL. III, NUMBER 6 IMAI RESEARCH GROUP COUNCIL Executive Director - Dr. Jesús Soto Carrión, Pontifical University of Salamanca, Spain Research Director - Dr. Rubén González Crespo, Universidad Internacional de La Rioja - UNIR, Spain Financial Director - Dr. Oscar Sanjuán Martínez, ElasticBox, USA Office of Publications Director - Lic. Ainhoa Puente, Universidad Internacional de La Rioja - UNIR, Spain Director, Latin-America regional board - Dr. Carlos Enrique Montenegro Marín, Francisco José de Caldas District University, Colombia EDITORIAL TEAM Editor-in-Chief Dr. Rubén González Crespo, Universidad Internacional de La Rioja – UNIR, Spain Associate Editors Dr. Jordán Pascual Espada, ElasticBox, USA Dr. Juan Pavón Mestras, Complutense University of Madrid, Spain Dr. Alvaro Rocha, University of Coimbra, Portugal Dr. Jörg Thomaschewski, Hochschule Emden/Leer, Emden, Germany Dr. Carlos Enrique Montenegro Marín, Francisco José de Caldas District University, Colombia Dr. Vijay Bhaskar Semwal, Indian Institute of Technology, Allahabad, India Editorial Board Members Dr. Rory McGreal, Athabasca University, Canada Dr. Abelardo Pardo, University of Sidney, Australia Dr. Hernán Sasastegui Chigne, UPAO, Perú Dr. Lei Shu, Osaka University, Japan Dr. León Welicki, Microsoft, USA Dr. Enrique Herrera, University of Granada, Spain Dr. Francisco Chiclana, De Montfort University, United Kingdom Dr. Luis Joyanes Aguilar, Pontifical University of Salamanca, Spain Dr. Ioannis Konstantinos Argyros, Cameron University, USA Dr. Juan Manuel Cueva Lovelle, University of Oviedo, Spain Dr. Pekka Siirtola, University of Oulu, Finland Dr. Francisco Mochón Morcillo, National Distance Education University, Spain Dr. Manuel Pérez Cota, University of Vigo, Spain Dr. Walter Colombo, Hochschule Emden/Leer, Emden, Germany Dr. Javier Bajo Pérez, Polytechnic University of Madrid, Spain Dr. -
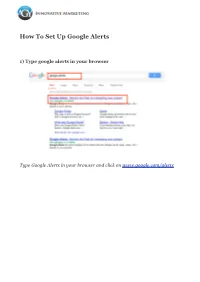
How to Set up Google Alerts
How To Set Up Google Alerts 1) Type google alerts in your browser Type Google Alerts in your browser and click on www.google.com/alerts 2) Set up your alerts In Search Query put in the topics you want google to source out for you. It might be of interest to have your name, your company domain, competitors domains, keywords you'd like to source information about or whatever you'd like to research. Enter the email address you want the alerts to go to. 3) Verify your alert Login into your email address that the alert is going to and verify it by clicking on the link. 4) Set up folders/labels so alerts skip your inbox (we will use Gmail for this example) 1) Tick the alerts that have come to your inbox. 2) Click on More, in the drop down menu choose 'Filter messages like these' 5) Create filter 1) Just click on 'create filter with this search' 6) Applying label/folder for alert to skip inbox. (Gmail calls folders labels, you can set them up under 'settings', 'labels'. 1) Tick skip the inbox (helps keep your inbox free) 2) Tick apply label 3) Choose what label (Here we have called it Alerts) 4) Tick to apply other alerts if found any 5) Create filter This is one easy way for information you are interested in to come to you. By setting up Alert Folders or Labels as Gmail calls them, they won't clog up your inbox, keeping it clear and leaving you to your choosing when you want to check your alerts for any useful information. -

Internet Security Threat Report Volume 24 | February 2019
ISTRInternet Security Threat Report Volume 24 | February 2019 THE DOCUMENT IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENT. THE INFORMATION CONTAINED IN THIS DOCUMENT IS SUBJECT TO CHANGE WITHOUT NOTICE. INFORMATION OBTAINED FROM THIRD PARTY SOURCES IS BELIEVED TO BE RELIABLE, BUT IS IN NO WAY GUARANTEED. SECURITY PRODUCTS, TECHNICAL SERVICES, AND ANY OTHER TECHNICAL DATA REFERENCED IN THIS DOCUMENT (“CONTROLLED ITEMS”) ARE SUBJECT TO U.S. EXPORT CONTROL AND SANCTIONS LAWS, REGULATIONS AND REQUIREMENTS, AND MAY BE SUBJECT TO EXPORT OR IMPORT REGULATIONS IN OTHER COUNTRIES. YOU AGREE TO COMPLY STRICTLY WITH THESE LAWS, REGULATIONS AND REQUIREMENTS, AND ACKNOWLEDGE THAT YOU HAVE THE RESPONSIBILITY TO OBTAIN ANY LICENSES, PERMITS OR OTHER APPROVALS THAT MAY BE REQUIRED IN ORDER FOR YOU TO EXPORT, RE-EXPORT, TRANSFER IN COUNTRY OR IMPORT SUCH CONTROLLED ITEMS. TABLE OF CONTENTS 1 2 3 BIG NUMBERS YEAR-IN-REVIEW FACTS AND FIGURES METHODOLOGY Formjacking Messaging Cryptojacking Malware Ransomware Mobile Living off the land Web attacks and supply chain attacks Targeted attacks Targeted attacks IoT Cloud Underground economy IoT Election interference MALICIOUS -

Protect Yourself and Your Personal Information*
CYBER SAFETY Protect yourself and your personal information * Cybercrime is a growing and serious threat, making it essential that fraud prevention is part of our daily activities. Put these safeguards in place as soon as possible—if you haven’t already. Email Public Wi-Fi/hotspots Key Use separate email accounts: one each Minimize the use of unsecured, public networks CYBER SAFETY for work, personal use, user IDs, alerts Turn oF auto connect to non-preferred networks 10 notifications, other interests Tips Turn oF file sharing Choose a reputable email provider that oFers spam filtering and multi-factor authentication When public Wi-Fi cannot be avoided, use a 1 Create separate email accounts virtual private network (VPN) to help secure your for work, personal use, alert Use secure messaging tools when replying session to verified requests for financial or personal notifications and other interests information Disable ad hoc networking, which allows direct computer-to-computer transmissions Encrypt important files before emailing them 2 Be cautious of clicking on links or Never use public Wi-Fi to enter personal attachments sent to you in emails Do not open emails from unknown senders credentials on a website; hackers can capture Passwords your keystrokes 3 Use secure messaging tools when Create complex passwords that are at least 10 Home networks transmitting sensitive information characters; use a mix of numbers, upper- and Create one network for you, another for guests via email or text message lowercase letters and special characters and children -

Security Now! #664 - 05-22-18 Spectreng Revealed
Security Now! #664 - 05-22-18 SpectreNG Revealed This week on Security Now! This week we examine the recent flaws discovered in the secure Signal messaging app for desktops, the rise in DNS router hijacking, another seriously flawed consumer router family, Microsoft Spectre patches for Win10's April 2018 feature update, the threat of voice assistant spoofing attacks, the evolving security of HTTP, still more new trouble with GPON routers, Facebook's Android app mistake, BMW's 14 security flaws and some fun miscellany. Then we examine the news of the next-generation of Spectre processor speculation flaws and what they mean for us. Our Picture of the Week Security News Update your Signal Desktop Apps for Windows & Linux A few weeks ago, Argentinian security researchers discovered a severe vulnerability in the Signal messaging app for Windows and Linux desktops that allows remote attackers to execute malicious code on recipient systems simply by sending a message—without requiring any user interaction. The vulnerability was accidentally discovered while researchers–amond them Juliano Rizzo–were chatting on Signal messenger and one of them shared a link of a vulnerable site with an XSS payload in its URL. However, the XSS payload unexpectedly got executed on the Signal desktop app!! (Juliano Rizzo was on the beach when the BEAST and CRIME attacks occurred to him.) After analyzing the scope of this issue by testing multiple XSS payloads, they found that the vulnerability resides in the function responsible for handling shared links, allowing attackers to inject user-defined HTML/JavaScript code via iFrame, image, video and audio tags. -

Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research
applied sciences Systematic Review Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research Majda Wazzan 1,*, Daniyal Algazzawi 2 , Omaima Bamasaq 1, Aiiad Albeshri 1 and Li Cheng 3 1 Computer Science Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah 21589, Saudi Arabia; [email protected] (O.B.); [email protected] (A.A.) 2 Information Systems Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah 21589, Saudi Arabia; [email protected] 3 Xinjiang Technical Institute of Physics & Chemistry Chinese Academy of Sciences, Urumqi 830011, China; [email protected] * Correspondence: [email protected] Abstract: Internet of Things (IoT) is promising technology that brings tremendous benefits if used optimally. At the same time, it has resulted in an increase in cybersecurity risks due to the lack of security for IoT devices. IoT botnets, for instance, have become a critical threat; however, systematic and comprehensive studies analyzing the importance of botnet detection methods are limited in the IoT environment. Thus, this study aimed to identify, assess and provide a thoroughly review of experimental works on the research relevant to the detection of IoT botnets. To accomplish this goal, a systematic literature review (SLR), an effective method, was applied for gathering and critically reviewing research papers. This work employed three research questions on the detection methods used to detect IoT botnets, the botnet phases and the different malicious activity scenarios. The authors analyzed the nominated research and the key methods related to them. The detection Citation: Wazzan, M.; Algazzawi, D.; methods have been classified based on the techniques used, and the authors investigated the botnet Bamasaq, O.; Albeshri, A.; Cheng, L. -

Master List of Games This Is a List of Every Game on a Fully Loaded SKG Retro Box, and Which System(S) They Appear On
Master List of Games This is a list of every game on a fully loaded SKG Retro Box, and which system(s) they appear on. Keep in mind that the same game on different systems may be vastly different in graphics and game play. In rare cases, such as Aladdin for the Sega Genesis and Super Nintendo, it may be a completely different game. System Abbreviations: • GB = Game Boy • GBC = Game Boy Color • GBA = Game Boy Advance • GG = Sega Game Gear • N64 = Nintendo 64 • NES = Nintendo Entertainment System • SMS = Sega Master System • SNES = Super Nintendo • TG16 = TurboGrafx16 1. '88 Games ( Arcade) 2. 007: Everything or Nothing (GBA) 3. 007: NightFire (GBA) 4. 007: The World Is Not Enough (N64, GBC) 5. 10 Pin Bowling (GBC) 6. 10-Yard Fight (NES) 7. 102 Dalmatians - Puppies to the Rescue (GBC) 8. 1080° Snowboarding (N64) 9. 1941: Counter Attack ( Arcade, TG16) 10. 1942 (NES, Arcade, GBC) 11. 1943: Kai (TG16) 12. 1943: The Battle of Midway (NES, Arcade) 13. 1944: The Loop Master ( Arcade) 14. 1999: Hore, Mitakotoka! Seikimatsu (NES) 15. 19XX: The War Against Destiny ( Arcade) 16. 2 on 2 Open Ice Challenge ( Arcade) 17. 2010: The Graphic Action Game (Colecovision) 18. 2020 Super Baseball ( Arcade, SNES) 19. 21-Emon (TG16) 20. 3 Choume no Tama: Tama and Friends: 3 Choume Obake Panic!! (GB) 21. 3 Count Bout ( Arcade) 22. 3 Ninjas Kick Back (SNES, Genesis, Sega CD) 23. 3-D Tic-Tac-Toe (Atari 2600) 24. 3-D Ultra Pinball: Thrillride (GBC) 25. 3-D WorldRunner (NES) 26. 3D Asteroids (Atari 7800) 27. -

Technical Brief P2P Iot Botnets Clean AC Font
Uncleanable and Unkillable: The Evolution of IoT Botnets Through P2P Networking Technical Brief By Stephen Hilt, Robert McArdle, Fernando Merces, Mayra Rosario, and David Sancho Introduction Peer-to-peer (P2P) networking is a way for computers to connect to one another without the need for a central server. It was originally invented for file sharing, with BitTorrent being the most famous P2P implementation. Decentralized file-sharing systems built on P2P networking have stood the test of time. Even though they have been used to share illegal pirated content for over 20 years, authorities have not been able to put a stop to these systems. Of course, malicious actors have used it for malware for quite a long time as well. Being able to create and manage botnets without the need for a central server is a powerful capability, mostly because law enforcement and security companies typically take down criminal servers. And since a P2P botnet does not need a central command-and-control (C&C) server, it is much more difficult to take down. From the point of view of defenders, this is the scariest problem presented by P2P botnets: If they cannot be taken down centrally, the only option available would be to disinfect each of the bot clients separately. Since computers communicate only with their own peers, the good guys would need to clean all the members one by one for a botnet to disappear. Originally, P2P botnets were implemented in Windows, but developers of internet-of-things (IoT) botnets do have a tendency to start incorporating this feature into their creations. -
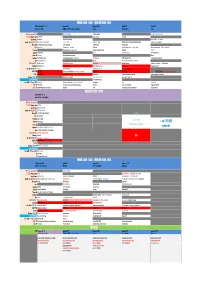
Programme Edition
JOURNEE 13h00 - 18h00 WEEK END 14h00 - 19h00 JOURJOURJOUR Vendredi 18/12 - 19h00 Samedi 19/12 Dimanche 20/12 Lundi 21/12 Mardi 22/12 ThèmeThèmeThème Science Fiction Zelda & le J-RPG (Jeu de rôle Japonais) ArcadeArcadeArcade Strange Games AnimeAnimeAnime NES / Twin Famicom / MSXMSXMSX The Legend of Zelda Rainbow Islands Teenage Mutant Hero Turtles SC 3000 / Master System Psychic World Streets of Rage Rampage Super Nintendo Syndicate Zelda Link to the Past Turtles in Time + Sailor Moon Megadrive / Mega CD / 32X32X32X Alien Soldier + Robo Aleste Lunar 2 + Soleil Dynamite Headdy EarthWorm Jim + Rocket Knight Adventures Dragon Ball Z + Quackshot Nintendo 64 Star Wars Shadows of the Empire Furai no Shiren 2 Ridge Racer 64 Buck Bumble SaturnSaturnSaturn Deep Fear Shining Force III scénario 2 Sky Target Parodius Deluxe Pack + Virtual Hydlide Magic Knight Rayearth + DBZ Shinbutouden Playstation Final Fantasy VIII + Saga Frontier 2 Elemental Gearbolt + Gun Blade Arts Tobal n°1 Dreamcast Ghost Blade Spawn Twinkle Star Sprites Alice's Mom Rescue Gamecube F Zero GX Zelda Four Swords 4 joueurs Bleach Playstation 2 Earth Defense Force Code Age Commanders / Stella Deus Puyo Pop Fever Earth Defense Force Cowboy Bebop + Berserk XboxXboxXbox Panzer Dragoon Orta Out Run 2 Dead or Alive Xtreme Beach Volleyball Wii / Wii UWii U / Wii JPWii JP Fragile Dreams Xenoblade Chronicles X Devils Third Samba De Amigo Tatsunoko vs Capcom + The Skycrawlers Playstation 3 Guilty Gear Xrd Demon's Souls J Stars Victory versus + Catherine Kingdom Hearts 2.5 Xbox 360 / XBOX -

007: the World Is Not Enough 1080 Teneighty Snowboarding a Bug's
007: The World Is Not Enough 1080 TenEighty Snowboarding A Bug's Life Aerofighter Assault AeroGauge Aidyn Chronicles : The First Mage All Star Tennis 99 All-Star Baseball 2000 All-Star Baseball 2001 All-Star Baseball 99 Armorines - Project S.W.A.R.M. Army Men : Air Combat Army Men : Sarge's Heroes Army Men : Sarge's Heroes 2 Asteroids Hyper 64 Automobili Lamborghini Banjo-Kazooie Banjo-Tooie Bassmasters 2000 Batman Beyond : Return of the Joker BattleTanx BattleTanx - Global Assault Battlezone : Rise of the Black Dogs Beetle Adventure Racing! Big Mountain 2000 Bio F.R.E.A.K.S. Blast Corps Blues Brothers 2000 Body Harvest Bomberman 64 Bomberman 64 : The Second Attack! Bomberman Hero Bottom of the 9th Brunswick Circuit Pro Bowling Buck Bumble Bust-A-Move '99 Bust-A-Move 2: Arcade Edition California Speed Carmageddon 64 Castlevania Castlevania : Legacy of Darkness Chameleon Twist Chameleon Twist 2 Charlie Blast's Territory Chopper Attack Clay Fighter : Sculptor's Cut Clay Fighter 63 1-3 Command & Conquer Conker's Bad Fur Day Cruis'n Exotica Cruis'n USA Cruis'n World CyberTiger Daikatana Dark Rift Deadly Arts Destruction Derby 64 Diddy Kong Racing Donald Duck : Goin' Qu@ckers*! Donkey Kong 64 Doom 64 Dr. Mario 64 Dual Heroes Duck Dodgers Starring Daffy Duck Duke Nukem : Zero Hour Duke Nukem 64 Earthworm Jim 3D ECW Hardcore Revolution Elmo's Letter Adventure Elmo's Number Journey Excitebike 64 Extreme-G Extreme-G 2 F-1 World Grand Prix F-Zero X F1 Pole Position 64 FIFA 99 FIFA Soccer 64 FIFA: Road to World Cup 98 Fighter Destiny 2 Fighters -

Reporting, and General Mentions Seem to Be in Decline
CYBER THREAT ANALYSIS Return to Normalcy: False Flags and the Decline of International Hacktivism By Insikt Group® CTA-2019-0821 CYBER THREAT ANALYSIS Groups with the trappings of hacktivism have recently dumped Russian and Iranian state security organization records online, although neither have proclaimed themselves to be hacktivists. In addition, hacktivism has taken a back seat in news reporting, and general mentions seem to be in decline. Insikt Group utilized the Recorded FutureⓇ Platform and reports of historical hacktivism events to analyze the shifting targets and players in the hacktivism space. The target audience of this research includes security practitioners whose enterprises may be targets for hacktivism. Executive Summary Hacktivism often brings to mind a loose collective of individuals globally that band together to achieve a common goal. However, Insikt Group research demonstrates that this is a misleading assumption; the hacktivist landscape has consistently included actors reacting to regional events, and has also involved states operating under the guise of hacktivism to achieve geopolitical goals. In the last 10 years, the number of large-scale, international hacking operations most commonly associated with hacktivism has risen astronomically, only to fall off just as dramatically after 2015 and 2016. This constitutes a return to normalcy, in which hacktivist groups are usually small sets of regional actors targeting specific organizations to protest regional events, or nation-state groups operating under the guise of hacktivism. Attack vectors used by hacktivist groups have remained largely consistent from 2010 to 2019, and tooling has assisted actors to conduct larger-scale attacks. However, company defenses have also become significantly better in the last decade, which has likely contributed to the decline in successful hacktivist operations. -

How to Stay Safe in Today's World
REFERENCES Internet Safety http://www.aarp.org/money/scams-fraud/info-08-2011/ internet-security.html How to Stay Safe in Identify Theft Federal Trade Commission (FTC) File Complaint: https://www.ftccomplaintassistant.gov/ ID Theft Hotline: 1-877-438-4338 Today’s World Credit Bureaus: Eqiuifax: 1-888-766-0008 Experian: 1-888-397-3742 TransUnion: 1-800-680-7289 Internet Terminology Medical Fraud: Hotline: 1-800-403-0864 Internet Safety Social Security: Hotline: 1-800-269-0271 Identify/Medical Theft http://oig.ssa.gov/report-fraud-waste-or-abuse/fraud-waste- and-abuse Card Skimming http://www.ftc.gov/bcp/edu/microsites/idtheft/ Remote Controls Booklet Sponsored by: Indiana Extension Homemakers Association Education Focus Group 2015-2016 www.ieha.families.com For more information contact your County Extension Office 16 INTERNET TERMINOLOGY NOTES APPS (applications): a shortcut to information categorized by an icon Attachment: a file attached to an e-mail message. Blog: diary or personal journal posted on a web site, updated frequently. Browser: a program with a graphical user interface for displaying HTML files, used to navigate the World Wide Web (a web browser) Click: pressing and releasing a button on a mouse to select or activate the area on the screen where the cursor s pointing to. Cloud: a loosely defined term for any system providing access via processing powers. Cookies: a small piece of code that is downloaded to computers to keep track of user’s activities. Cyberstalking: a crime in which the attacker harasses a victim using electronic communication, such as -e mail, instant messaging or post- ed messages.