System Programming - the Human and the Machine Michael Kline Miami University, [email protected]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Rocket Model 204 System Manager's Guide
Rocket Model 204 System Manager’s Guide Version 7 Release 4.0 May 2012 204-0704-SM-01 Notices Edition Publication date: May 2012 Book number: 204-0704-SM-01 Product version: Rocket Model 204 System Manager’s Guide Version 7 Release 4.0 Copyright © Computer Corporation of America 1989-2012. All Rights Reserved. Computer Corporation of America is a wholly-owned subsidiary of Rocket Software, Inc. Trademarks Rocket is a registered trademark of Rocket Software, Inc. For a list of Rocket registered trademarks go to: www.rocketsoftware.com/about/legal. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names of their respective owners. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license. Note This product may contain encryption technology. Many countries prohibit or restrict the use, import, or export of encryption technologies, and current use, import, and export regulation should be followed when exporting this product. Contact information Web Site: www.rocketsoftware.com Rocket Software, Inc. Headquarters 77 4th Avenue, Suite 100 Waltham, MA 02451–1468 USA Tel: +1.617.614.4321 Fax: +1.617.630.7100 ii Contacting Technical Support If you have current support and maintenance agreements with Rocket Software and CCA, contact Rocket Software Technical support by email or by telephone: Email: [email protected] Telephone : North America +1.800.755.4222 United Kingdom/Europe +44 (0) 20 8867 6153 Alternatively, you can access the Rocket Customer Portal and report a problem, download an update, or read answers to FAQs. -

VM for MVS Systems Programmers Part 2 Martha Mcconaghy, Marist College Mark Post, EDS Monday, August 14, 2006 Session 9128 Follow up Presentations
VM For MVS Systems Programmers Part 2 Martha McConaghy, Marist College Mark Post, EDS Monday, August 14, 2006 Session 9128 Follow Up Presentations • Other presentations this week which cover related subjects in more detail: • 9107 – 9109 Introduction to VM Hands-on Lab Tue 8am-noon • 9125 Virtual Networking with z/VM Guest LANS and Virtual Switch Tue 8am • 9115 VM Performance Introduction Tue 1:20pm • 9119 z/VM Installation - What are you afraid of? Tue 3pm • 9117 Introduction to VMSES/E for z/VM Wed 9:30am • 9118 Maintaining z/VM with VMSES/E lab Wed 11am • 9133 Configuring, Customizing and Modifying your VM System without an IPL Wed 3pm • 9123 TRACK for z/VM – What’s Happening in your Virtual Machine Thur 9:30am • 9116 z/VM Simplified Network Configuration Thur 3pm • 9136 Automated Linux Guest Monitoring on z/VM using PROP 35 Agenda • Part 1: • Introduction to and comparison of basic concepts • What is a hypervisor and what about all the “virtual” stuff? • Caring for a VM system (maintenance, system datasets, etc.) • System configuration concepts • Part 2: • Applications and guests • CMS vs. TSO • File Editors • Misc good stuff We will answer questions as time allows….. 36 Application Support • CP level of z/VM cannot execute applications. It’s only job is to emulate hardware and manage resources. • Does not provide file editing or writing capabilities. It can read CMS files for use with system configuration. • Cannot compile, assemble or execute programs. • CMS started out as an operating system during the early days of mainframes. • Became popular as a “guest” on CP to provide user/application functions. -

Using IPCS with MVS/ESA Version 5
SYSTEM BY TOM BRYANT STRATEGIES MVS/XA/ESA Problem Solving: Part I — Using IPCS With MVS/ESA Version 5 PCS for MVS/ESA Version 5 has come a long way since I first used it in 1983 at the prompting of an exuberant IBM customer engineer. IPCS IPCS for MVS/ESA continues to move toward a fully panel-driven environment, although in Version 5 offers many Isome situations, I find using IPCS commands easier. capabilities, including the ability to scan for unformatted storage dumps. This article Future articles will examine the environ- easily in batch mode as well as in an ISPF mental record editing and printing program foreground session. I also wanted a CLIST examines the many (EREP), one-page MVS/XA/ESA abend that was well-documented with easy-to-use facilities of IPCS, analysis, advanced SVCDUMP analysis, parameters. Finally, I wanted a CLIST that slip traps and GTF tracing, and standalone does not hang onto dump directory and IPCS and includes some dump analysis. print dataset allocations when completed, as of the author’s favorite IPCS stands for Interactive Problem the IBM BLSCDDIR CLIST does. Control System, although most people IPCS commands. (myself included) use it just for looking at IPCS CLISTS FOR MVS/ESA unformatted storage dumps. IPCS will process VERSION 4.3 AND ABOVE SVCDUMPs which are dumps usually pro- The #IPCSTJB CLIST is the mainline duced with the abend (SVC 13) issued by your CLIST that you execute to establish an IPCS program or the system. Other unformatted session (see Figure 1). If you are invoking dumps that IPCS will produce include an #IPCSTJB for the first time, the NEW CLIST application unformatted dump allocated keyword parameter indicates that you will through the SYSMDUMP DD statement and dynamically create a VSAM dump directory the standalone dump produced by the stand- using the value of the VOL CLIST keyword alone dump program. -

Z/VM Version 7 Release 2
z/VM Version 7 Release 2 OpenExtensions User's Guide IBM SC24-6299-01 Note: Before you use this information and the product it supports, read the information in “Notices” on page 201. This edition applies to Version 7.2 of IBM z/VM (product number 5741-A09) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2020-09-08 © Copyright International Business Machines Corporation 1993, 2020. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................. xi Tables................................................................................................................ xiii About this Document........................................................................................... xv Intended Audience..................................................................................................................................... xv Conventions Used in This Document......................................................................................................... xv Escape Character Notation................................................................................................................... xv Case-Sensitivity.....................................................................................................................................xv Typography............................................................................................................................................xv -

Network Program Products General Information and Planning For
---- -------- - --- Network Program Products GC30-3463-0 -------_.---- - - --- General Information and Planning for NetView Release 2 MVS, VM and VSE ----- - --- Network Program Products GC30·3463·0 --_--------- - - ---.-. General Information and Planning for NetView Release 2 MVS, VM and VSE First Edition (June 1987) This book applies to the following IBM licensed program: NetView Release 2 for MVS/370 (program number 5665-361). MVS/XA (program number 5665-362). VM (program number 5664-204). and VSE (program number 5666-343). The licensed program described in this manual. and all licensed material avaiiable for it. are provided by IBM under terms of the Agreement for IBM Licensed Programs. Changes are made periodically to the information herein; before you use this publication in connection with the operation of IBM systems. consult the latest IBM Systeml370, 30xx, and 4300 Processors Bibliography, GC20-0001. for the editions that are applicable and current. Any reference to an IBM licensed program in this document is not intended to state or imply that only IBM's program may be used. Any functionally equivalent program may be used instead. It is possible that this material may contain reference to. or information about. IBM products (machines and programs). programming. or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such products. programs. or services in your country. Publications are not stocked at the address given below. If you want more IBM publications. ask your IBM representative or write to the IBM branch office serving your locality. A form for your comments is provided at the back of this publication. -

CA XCOM Data Transport for UNIX and Linux Overview Guide
CA XCOM™ Data Transport® for UNIX and Linux Overview Guide r11.5 Second Edition This documentation and any related computer software help programs (hereinafter referred to as the “Documentation”) is for the end user’s informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and protected by the copyright laws of the United States and international treaties. Notwithstanding the foregoing, licensed users may print a reasonable number of copies of the documentation for their own internal use, and may make one copy of the related software as reasonably required for back-up and disaster recovery purposes, provided that all CA copyright notices and legends are affixed to each reproduced copy. Only authorized employees, consultants, or agents of the user who are bound by the provisions of the license for the product are permitted to have access to such copies. The right to print copies of the documentation and to make a copy of the related software is limited to the period during which the applicable license for the Product remains in full force and effect. Should the license terminate for any reason, it shall be the user’s responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. EXCEPT AS OTHERWISE STATED IN THE APPLICABLE LICENSE AGREEMENT, TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NONINFRINGEMENT. -

Z/OS Basic Skills Information Center: Mainframe Concepts
z/OS Basic Skills Information Center Mainframe concepts z/OS Basic Skills Information Center Mainframe concepts Note Before using this information and the product it supports, read the information in “Notices” on page 45. This edition applies to z/OS (product number 5694-A01). We appreciate your comments about this publication. Comment on specific errors or omissions, accuracy, organization, subject matter, or completeness of this book. The comments you send should pertain to only the information in this manual or product and the way in which the information is presented. For technical questions and information about products and prices, contact your IBM branch office, your IBM business partner, or your authorized remarketer. When you send comments to IBM, you grant IBM a nonexclusive right to use or distribute your comments in any way it believes appropriate without incurring any obligation to you. IBM or any other organizations will only use the personal information that you supply to contact you about the issues that you state on this form. Send your comments through this Web site: http://publib.boulder.ibm.com/infocenter/zoslnctr/v1r7/ index.jsp?topic=/com.ibm.zcontact.doc/webqs.html © Copyright International Business Machines Corporation 2005, 2008. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Introduction to the mainframe . .v Mainframe operating system: z/TPF . .22 Chapter 1. The value of the mainframe Chapter 2. Mainframe hardware today . .1 concepts . .23 The S/360: A turning point in mainframe history . .1 Mainframe hardware: Terminology . .23 Mainframe architecture: Secure, compatible, and still Mainframe hardware: Evolving design . -

Washington Systems Center Technical Bulletin: "SNA Networking Products Overview and SNA Release/Function Guide" (GG22-9256-00)
Washington Technical Systems Bulletin Center A. H. Shrader GG22-9386-00 December 1984 Washington Systems Center Gaithersburg, Maryland Technical Bulletin SNA NETWORKING PRODUCT OVERVIEW Hank Shrader GG22-9386-00 December 1984 The information contained in this document has not been submitted to any formal IBM test and is distributed on an "as is" basis WITHOUT ANY WARRANTY EITHER EXPRESSED OR IMPLIED. The use of this information or the implementation of any of these techniques is a customer responsibility and depends on the customer's ability to evaluate and integrate them into the customer's operational environment. While each item may have been reviewed by IBM for accuracy in a specific situation, there is no guarantee that the same or similar results will be obtained elsewhere. Customers attempting to adapt these techniques to their own environments do so at their own risk. In this document, any references made to an IBM program product are not intended to state or imply that only IBM's program product may be used; \ any functionally equivalent program may be used instead. It is possible that this material may contain reference to, or information about, IBM products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such IBM products, programming, or services in your country. Publications are not stocked at the address given below; requests for IBM publications should be made to your IBM representative or to the IBM office serving your locality. A form for reader's comments is provided at the back of this publication. -

Z/OS Basics Preface
Contents Preface . iii How this course is organized . iii How each topic is organized . iv Part 1. Introduction to z/OS and the mainframe environment Chapter 1. Introduction to the new mainframe . 3 1.1 The new mainframe. 4 1.2 The S/360: A turning point in mainframe history . 4 1.3 An evolving architecture . 5 1.4 Mainframes in our midst . 6 1.5 What is a mainframe? . 7 1.6 Who uses mainframe computers?. 10 1.7 Factors contributing to mainframe use . 11 1.8 Typical mainframe workloads . 14 1.9 Roles in the mainframe world . 21 1.10 z/OS and other mainframe operating systems . 27 1.11 Summary . 29 Chapter 2. z/OS overview. 31 2.1 What is an operating system? . 32 2.2 Overview of z/OS facilities. 32 2.3 What is z/OS? . 34 2.4 Virtual storage and other mainframe concepts . 39 2.5 What is workload management? . 57 2.6 I/O and data management. 60 2.7 Supervising the execution of work in the system . 60 2.8 Defining characteristics of z/OS . 68 2.9 Licensed programs for z/OS . 69 2.10 Middleware for z/OS . 70 2.11 A brief comparison of z/OS and UNIX. 71 2.12 Summary . 73 Chapter 3. TSO/E, ISPF, and UNIX: Interactive facilities of z/OS . 75 3.1 How do we interact with z/OS? . 76 3.2 TSO overview . 76 3.3 ISPF overview . 80 3.4 z/OS UNIX interactive interfaces. 99 3.5 Summary . -
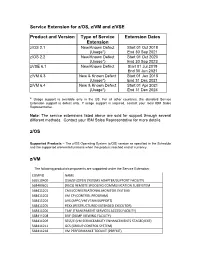
Service Extension for Z/OS, Z/VM and Z/VSE
Service Extension for z/OS, z/VM and z/VSE Product and Version Type of Service Extension Dates Extension z/OS 2.1 New/Known Defect Start 01 Oct 2018 (Usage*) End 30 Sep 2021 z/OS 2.2 New/Known Defect Start 01 Oct 2020 (Usage*) End 30 Sep 2023 zVSE 6.1 New/Known Defect Start 01 Jul 2019 End 30 Jun 2021 z/VM 6.3 New & Known Defect Start 01 Jan 2018 (Usage*) End 31 Dec 2021 z/VM 6.4 New & Known Defect Start 01 Apr 2021 (Usage*) End 31 Dec 2024 * Usage support is available only in the US. For all other countries, the standard Service Extension support is defect only. If usage support is required, contact your local IBM Sales Representative. Note: The service extensions listed above are sold for support through several different methods. Contact your IBM Sales Representative for more details. z/OS Supported Products – The z/OS Operating System (z/OS) version as specified in the Schedule and the supported elements/functions when the product reached end of currency. z/VM The following products/components are supported under the Service Extension: COMPID NAME 565510400 OSA/SF (OPEN SYSTEMS ADAPTER/SUPPORT FACILITY) 568409601 (RSCS) REMOTE SPOOLING COMMUNICATION SUBSYSTEM 568411201 CMS (CONVERSATIONAL MONITOR SYSTEM) 568411202 VM CP (CONTROL PROGRAM) 568411204 AVS (APPC/VM VTAM SUPPORT) 568411205 REXX (RESTRUCTURED EXTENDED EXECUTOR) 568411206 TSAF (TRANSPARENT SERVICES ACCESS FACILITY) 568411208 DVF (DUMP VIEWING FACILITY) 568411209 SESS/E (VM SERVICEABILITY ENHANCEMENTS STAGED/EXT) 568411211 GCS (GROUP CONTROL SYSTEM) 568411218 VM PERFORMANCE -

Hires Through May 31, 2018
Hire Heroes USA 2018 Confirmed Hires through May 31, 2018 (Last) Service Service Branch Other Hiring Company Name Position Hired For Rank Army CW-4 Agbotic Greenhouse Cluster Manager Air Force E-1 Nexgen Pharma Assistant Army E-1 Paralyzed Veterans of America Service Officer Supervisor Army E-1 Entrepreneur Owner Army E-1 Ohio Media School "Web Content Radio Coordinator Army E-1 Wireless Advocates Sales Representative Navy E-1 Uber-eats Customer Service Air Force E-1 Diamond Springs Water Warehouse Specialist Army E-1 KFC Fry Cook Army E-2 Lockheed Martin Corporation Security Officer Navy E-2 Delta Dental Customer Service Representative Army E-2 GOODYEAR COMMERCIAL TIRE Driver Air Force E-2 BNSF Trainee Conductor Army E-2 Best Western Plus Inn and Suites Maintenance Technician Army E-2 Systems Planning & Analysis, Inc. Program Manager Army E-2 Blue Line Protection Group Armed Security Guard Army E-2 DaVita Dialysis Tech Army E-2 HCI integrated solutions IT Consultant Air Force E-2 Goodwill Industries Case Manager Marines E-2 G&D Integrated Material Handler Air Force E-2 ProScope Flood/Insurance Adjuster Navy E-2 Pop Media Group Post Production Technician Army E-2 PFM Help Desk Analyst Marines E-2 Apex Systems, Inc Desktop Support Army E-2 Cheers Liquor Mart Cashier General Dynamics - Information Marines E-3 Technology Computer Engineer Air Force E-3 HAECO Americas FAA Airframe Certified Technician Navy E-3 Britts Home Furnishings Sales Consultant Department of Homeland Security Marines E-3 (NPPD) Customs Agent Army E-3 Social SEO Marketing -

IT-Zertifikate (Mit Besonderer Berücksichtigung Von IT-Security-Zertifizierungen)
IT-Zertifikate (mit besonderer Berücksichtigung von IT-Security-Zertifizierungen) Orientiert an: http://www.itiki.de/qualifikationen/zertifikate/ und Anbieterhomepages Legende: Grün spezifisch IT-Security, Schwarz ausgesprochener Bezug zu IT-Security, Hellgrau nachrangiger Bezug zu IT-Security Rot kein direkter Bezug zu IT-Security ISACA (http://www.isaca.de/index.php/zert-start) Governance Compliance iT5 Certified Information Systems Auditor (CISA) Certified Information Security Manager (CISM) Certified in the Governance of Enterprise IT (CGEIT) Certified in Risk and Information Systems Control (CRISC) Compliance manager iTCM Governance manager iTGM Cyber-Security Practitioner IT Risk iT5 QARiF quality assurance review (ISC)² (https://www.isc2.org/) System Security Certified Practitioner (SSCP) Certified Authorization Professional (CAP) Certified Secure Software Lifecycle Professional (CSSLP) Certified Cyber Forensics Professional (CCFP) HealthCare Information Security and Privacy Practitioner (HCISPP) Certified Cloud Security Professional (CCSP) CISSP® - Certified Information Systems Security Professional Cisco (http://www.ccna.de/ccda.htm) Cisco Certified Network Associate (CCNA) Cisco Certified Entry Network Technician (CCENT) Cisco Certified Design Associate (CCDA) Cisco Certified Network Professional (CCNP) Cisco Certified Design Professional (CCDP) Cisco Certified Internetwork Professional (CCIP) Cisco Certified Voice Professional (CCVP) Cisco Certified Internetwork Expert (CCIE) Cisco Certified Security