Vulnerability Summary for the Week of April 11, 2016
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Entation to Be Used by Developers and Webmasters
Programming with SPIP DOCUMENTATION TO BE USED BY DEVELOPERS AND WEBMASTERS SPIP’s version 2.1.0+ / August 2010 SPIP’s version 2.1.0+ / August 2010 SPIP is both a publication system and a development platform. After a quick tour of SPIP’s features, we will describe how it works and explain how to develop with it using helpful examples wherever possible. This documentation targets webmasters with knowledge of PHP, SQL, HTML, CSS and JavaScript. Contents Preface..................................................................................... 7 Notes about this documentation............................................... 9 Introduction ............................................................................ 11 The templates ........................................................................ 15 Contents of the directories ..................................................... 87 Extending SPIP .................................................................... 101 Functionalities ...................................................................... 197 Forms ................................................................................... 229 SQL access.......................................................................... 253 Creating your own plugins.................................................... 303 Examples ............................................................................. 315 Glossary ............................................................................... 321 Index ................................................................................... -

Values and Configuration of Users in the Design of Software Source Code
International Journal of Communication 11(2017), 1112–1132 1932–8036/20170005 Values and Configuration of Users in the Design of Software Source Code STÉPHANE COUTURE1 Glendon College, York University, Canada Based on an empirical study of two free and open source software projects, this article focuses on how choices of design within software source code are articulated with values and may favor certain categories of actors over others. After introducing the aim and approach of the study and presenting the studied projects, the article analyzes two controversies that show the articulation of values, configuration of users, and source code design. In conclusion, I argue for the importance for communication and media studies to study the use of source code and how its design may reflect values or may facilitate or constrain the agencies of certain categories of people. Keywords: software source code, free and open source software, digital technologies, configuration of users, values, science and technology studies When I am a graphic designer, my interface is Photoshop, with its buttons, its windows, etc. When I am developer, my interface is code. It is through code that I interact with what I am building, a program. (Interview sf03, July 2009) This quote from an interview I conducted in the course of this study grasps a fundamental argument I want to bring forward in this article: that software source code should be analyzed as an interface with which actors interact to build or modify software. Although metaphors of code are regularly mobilized in communication studies, few studies seem to have been done to closely and empirically investigate what source code exactly is and how its design may reflect values or may facilitate or restrain the capacity of some people to participate in the making of digital technologies. -

Country Profile Taking of Evidence by Video-Link Under the Hague Convention of 18 March 1970 on the Taking of Evidence Abroad in Civil Or Commercial Matters
COUNTRY PROFILE TAKING OF EVIDENCE BY VIDEO-LINK UNDER THE HAGUE CONVENTION OF 18 MARCH 1970 ON THE TAKING OF EVIDENCE ABROAD IN CIVIL OR COMMERCIAL MATTERS STATE NAME: Bolivarian Republic of Venezuela PROFILE UPDATED ON (DATE): May 2017 PART I: STATE 1. Contact details The contact details provided in this section will be published on the Hague Conference website CHAPTER I (LETTERS OF REQUEST) As with any other Letter of Request under Chapter I of the Evidence Convention, the requesting authority should contact the Central Authority(ies)of the requested State when seeking to obtain evidence by means of a Letter of Request, whether using video-link or not. a) Are the contact details of the Central Yes. Authority(ies) designated by YOUR STATE up- No. Please provide the contact details to-date on the Evidence Section of the Hague on a separate Word or PDF document Conference website? for uploading on the Evidence Section of the Hague Conference website. b) Would YOUR STATE be in favour of specifying a Yes. person or department within the Central If YOUR STATE has already done so, Authority(ies) who would assist in please specify the contact details: processing Letters of Request where the use Special Issues Area / Office of of video-links has expressly been requested Consular Relations / Ministry for (e.g.,to arrange the video-link or provide Foreign Relations technical assistance)? No. Please explain why: Comments: c) What arrangements are there for ensuring The office has on-call staff, in charge of the that there is a contact person with whom the information technology area, who is requesting authority can liaise and who is dedicated to the operation of video-link. -

Installation of Apache Openmeetings 4.0.3 on Debian 9 This Tutorial Is
Installation of Apache OpenMeetings 4.0.3 on Debian 9 This tutorial is made based on a fresh installations of debian-9.1.0-amd64-DVD-1.iso It is tested with positive result. We will use the Apache's binary version OpenMeetings 4.0.3 stable, that is to say will suppress his compilation. It is done step by step. 19-4-2018 Starting... 1) First, we update and upgrade the OS: sudo apt-get update sudo apt-get upgrade 2) ------ Installation of OpenJava 1.8 ------ OpenMeetings 4.0.3 need Java 1.8 to work. So, we install OpenJava 1.8: sudo apt install openjdk-8-jdk openjdk-8-jdk-headless ...and his plugin for web: sudo apt install icedtea-8-plugin Pag 1 Now, please, select OpenJava, if you have more than one java versions installed: sudo update-alternatives --config java To see the active java version: java -version 3) ------ Installation of LibreOffice ------ LibreOffice is need it to convert to pdf the uploaded office files. The ubuntu desktop iso have already LibreOffice installed. We do it also for server iso: sudo apt-get install libreoffice 4) ------ Installation ImageMagick and Sox ------ ImageMagic, will work the image files, png, jpg, gif, etc. Will install it and some more libraries and paquets: sudo apt-get install -y imagemagick libjpeg62 zlib1g-dev unzip make build-essential wget nmap Sox, work the sound. We´ll compile, because this version is newer than is in the repos: cd /opt wget http://sourceforge.net/projects/sox/files/sox/14.4.2/sox-14.4.2.tar.gz tar xzvf sox-14.4.2.tar.gz cd /opt/sox-14.4.2 ./configure make && make install Pag 2 5) ------ Installation of Adobe flash player ------ OpenMeetings even need Adobe Flash Player for cam. -

A Survey on Content Management System, Software's and Tools
ISSN (Online) 2393-8021 IARJSET ISSN (Print) 2394-1588 International Advanced Research Journal in Science, Engineering and Technology ISO 3297:2007 Certified Vol. 4, Issue 11, November 2017 A Survey on Content Management System, Software's and Tools Madhura K Assistant Professor, Computer Science Department, Presidency University, Bangalore1 Abstract: This paper contains a survey of content management system, content management process, architecture and working. Also contains different types of tools and software. Content Management (CM) is the process for collection, delivery, retrieval, governance and overall management of information in any format. The term is typically used in reference to administration of the digital content lifecycle, from creation to permanent storage or deletion. The content involved may be images, video, audio and multimedia as well as text. A Content Management System (CMS) is a computer application that supports the creation and modification of digital content. It is typically used to support multiple users working in a collaborative environment. A Content Management System (CMS) is a tool for creating and managing digital content such as documents, text, web pages, videos and images.A content management system (CMS) is a software application or set of related programs that are used to create and manage digital content. CMSes are typically used for Enterprise Content Management (ECM) and Web Content Management (WCM). An ECM facilitates collaboration in the workplace by integrating document management, digital asset management and records retention functionalities, and providing end users with role-based access to the organization's digital assets. A WCM facilitates collaborative authoring for websites. ECM software often includes a WCM publishing functionality, but ECM webpages typically remain behind the organization's firewall. -
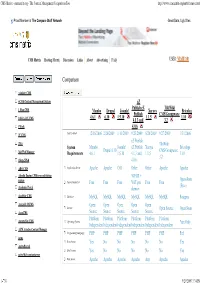
CMS Matrix - Cmsmatrix.Org - the Content Management Comparison Tool
CMS Matrix - cmsmatrix.org - The Content Management Comparison Tool http://www.cmsmatrix.org/matrix/cms-matrix Proud Member of The Compare Stuff Network Great Data, Ugly Sites CMS Matrix Hosting Matrix Discussion Links About Advertising FAQ USER: VISITOR Compare Search Return to Matrix Comparison <sitekit> CMS +CMS Content Management System eZ Publish eZ TikiWiki 1 Man CMS Mambo Drupal Joomla! Xaraya Bricolage Publish CMS/Groupware 4.6.1 6.10 1.5.10 1.1.5 1.10 1024 AJAX CMS 4.1.3 and 3.2 1Work 4.0.6 2F CMS Last Updated 12/16/2006 2/26/2009 1/11/2009 9/23/2009 8/20/2009 9/27/2009 1/31/2006 eZ Publish 2flex TikiWiki System Mambo Joomla! eZ Publish Xaraya Bricolage Drupal 6.10 CMS/Groupware 360 Web Manager Requirements 4.6.1 1.5.10 4.1.3 and 1.1.5 1.10 3.2 4Steps2Web 4.0.6 ABO.CMS Application Server Apache Apache CGI Other Other Apache Apache Absolut Engine CMS/news publishing 30EUR + system Open-Source Approximate Cost Free Free Free VAT per Free Free (Free) Academic Portal domain AccelSite CMS Database MySQL MySQL MySQL MySQL MySQL MySQL Postgres Accessify WCMS Open Open Open Open Open License Open Source Open Source AccuCMS Source Source Source Source Source Platform Platform Platform Platform Platform Platform Accura Site CMS Operating System *nix Only Independent Independent Independent Independent Independent Independent ACM Ariadne Content Manager Programming Language PHP PHP PHP PHP PHP PHP Perl acms Root Access Yes No No No No No Yes ActivePortail Shell Access Yes No No No No No Yes activeWeb contentserver Web Server Apache Apache -

Silverstripe
silverstripe #silverstripe 1 1: 2 2 2 Examples 2 2 CMS / 2 2: DataExtensions 4 Examples 4 DataObject 4 DataObject 4 DataExtension 4 3: LeftAndMain 6 6 Examples 6 1. 6 6 6 6 2. HelloWorldLeftAndMain.php 6 7 7 7 3. (HelloWorldLeftAndMain_Content.ss) 8 . 8 8 4: ModelAdmin 9 Examples 9 9 UI DataObject 9 DataObject . 9 DataObject 9 searchable_fields ModelAdmin . 10 GridField 10 ModelAdmin 11 5: ORM 12 Examples 12 DataObject 12 6: 13 13 ? 13 13 Examples 13 13 13 YAML 13 13 7: 15 15 Examples 15 SilverStripe Grid 15 GridField 15 15 15 CMS 16 16 8: 17 17 Examples 17 17 AJAX 17 17 19 20 : 20 9: 22 22 Examples 22 MyClass.php 22 23 You can share this PDF with anyone you feel could benefit from it, downloaded the latest version from: silverstripe It is an unofficial and free silverstripe ebook created for educational purposes. All the content is extracted from Stack Overflow Documentation, which is written by many hardworking individuals at Stack Overflow. It is neither affiliated with Stack Overflow nor official silverstripe. The content is released under Creative Commons BY-SA, and the list of contributors to each chapter are provided in the credits section at the end of this book. Images may be copyright of their respective owners unless otherwise specified. All trademarks and registered trademarks are the property of their respective company owners. Use the content presented in this book at your own risk; it is not guaranteed to be correct nor accurate, please send your feedback and corrections to [email protected] https://riptutorial.com/ko/home 1 1: Silverstripe PHP . -

Installation of Apache Openmeetings 4.0.0 on Debian 9 This Tutorial Is
Installation of Apache OpenMeetings 4.0.0 on Debian 9 This tutorial is made based on a fresh installations of debian-9.1.0-amd64-DVD-1.iso It is tested with positive result. We will use the Apache's binary version OpenMeetings 4.0.0 stable, that is to say will suppress his compilation. It is done step by step. 5-11-207 Starting... 1) First, we update and upgrade the OS: sudo apt-get update sudo apt-get upgrade 2) ------ Installation of OpenJava 1.8 ------ OpenMeetings 4.0.0 need Java 1.8 to work. So, we install OpenJava 1.8: sudo apt install openjdk-8-jdk openjdk-8-jdk-headless ...and his plugin for web: sudo apt install icedtea-8-plugin Pag 1 Now, please, select OpenJava, if you have more than one java versions installed: sudo update-alternatives --config java To see the active java version: java -version 3) ------ Installation of LibreOffice ------ LibreOffice is need it to convert to pdf the uploaded office files. The ubuntu desktop iso have already LibreOffice installed. We do it also for server iso: sudo apt-get install libreoffice 4) ------ Installation ImageMagick and Sox ------ ImageMagic, will work the image files, png, jpg, gif, etc. Will install it and some more libraries and paquets: sudo apt-get install -y imagemagick libjpeg62 zlib1g-dev unzip make build-essential wget nmap Sox, work the sound. We´ll compile, because this version is newer than is in the repos: cd /opt wget http://sourceforge.net/projects/sox/files/sox/14.4.2/sox-14.4.2.tar.gz tar xzvf sox-14.4.2.tar.gz cd /opt/sox-14.4.2 ./configure make && make install Pag 2 5) ------ Installation of Adobe flash player ------ OpenMeetings even need Adobe Flash Player for cam. -

Opettajan Arvio Opinnäytetyöstä
Harrison Oriahi CONTENT MANAGEMENT SYSTEMS (CMS) CONTENT MANAGEMENT SYSTEMS (CMS) Harrison Oriahi Bachelor’s thesis Autumn 2014 Degree Programme in Information Technology Oulu University of Applied Sciences ABSTRACT Oulu University of Applied Sciences Degree in Information Technology, Internet Services Author(s): Harrison Oriahi Title of Bachelor’s thesis: Content Management Systems Supervisor(s): Veijo Väisänen Term and year of completion: Autumn 2014 Number of pages: 48 + 3 appendices ABSTRACT: This thesis describes the three most common and widely used content management systems (CMS) used to power several millions of business websites on the internet. Since there are many other content managements systems online, this report provides some helpful guides on each of these three most used systems and the web design projects that each of them maybe most suitable. There are plenty of options when it comes to selecting a content management system for a development project and this thesis focuses on making a detailed comparison between the three most commonly used ones. This comparison will help provide a clear understanding of why a content management system maybe preferred to the other when considering any web design project. To help detect the content management system (CMS) or development platform that an already existing website is built on, some helpful website analyzing tools are also discussed in this report. By reading this report, a reader with no previous experience with content management systems will be able to have a general view on what they are, what the commonly used ones are and what to consider when making a choice of content management system to use. -

3Rd Eye Vision Credentials Summer 2016 Intro
3rd Eye Vision Credentials Summer 2016 Intro Thank you for your interest in 3rd Eye Vision. Contents These are our credentials, they should give you an insight into what we do, what we’re like and how 04 About Us we work. To find out more, give us a call. 05 What We Do 06 Process 08 Who We Are 10 Case Studies 24 Spotlights 28 What Next ? 2 Things you’ll notice: When you start working with us, you’ll see that we’re a bit different to other agencies. Your project will be right first time When you speak, we listen very carefully. Requests are logged so they can’t be missed. We value your time by making sure everything is good to go. Your ideas are heard Okay, so we might be the experts with oodles of technical smarts, but we respect your knowledge of your business and your industry. So we want to hear what you think. Your requirements are met We’re a bunch of reactionaries. That’s right. We react to the changing situation on the ground. And by ground we don’t mean ground at all. If your needs change, we respond. We’re flexible like that. 3 About us Often considered as the London agency by the sea, we are an established digital agency providing strategy, design and development services for our clients. Established in 1998 (yes that We have been interdisciplinary makes us 18 years old!) we since before it became cool, have an agile team of 12. we thrive from our shared We’ve been working on passion for innovative ideas. -

Documentation SPIP
SPIP WEBMESTRES Table des matières Où placer les fichiers de squelettes ? .................................................................................................... 5 Les squelettes par défaut : dist/ ................................................................................................... 5 Votre dossier squelettes/ .............................................................................................................. 5 Utiliser un autre dossier de squelettes ......................................................................................... 6 Priorité des dossiers de squelettes ............................................................................................... 6 Et les fichiers .php3 (ou .php) dans tout ça ? .............................................................................. 7 Principe général .................................................................................................................................... 8 Pour chaque type de page, un squelette ...................................................................................... 8 Lorsque SPIP appelle un squelette, il lui passe un contexte ....................................................... 9 Le principe de fonctionnement du cache, de manière simplifiée .............................................. 10 Le fichier .html .......................................................................................................................... 11 Une interface différente dans le même site .............................................................................. -

Society of American Archivists Council Meeting August 25, 2008 San Francisco, California
Agenda Item II.O. Society of American Archivists Council Meeting August 25, 2008 San Francisco, California Report: Website Working Group (Prepared by Brian Doyle, Chair) WORKING GROUP MEMBERS Brian Doyle, Chair Gregory Colati Christine Di Bella Chatham Ewing Jeanne Kramer-Smyth Mark Matienzo Aprille McKay Christopher Prom Seth Shaw Bruce Ambacher, Council Liaison BACKGROUND For several years, there has been a keen and growing interest among SAA’s members in the deployment of a robust content management system (CMS) featuring state-of-the-art Web 2.0 applications—wikis, blogs, RSS feeds, etc. While these types of programs are often associated with social networking, a comprehensive CMS would also redress a number of important organizational challenges that SAA faces: • How can SAA’s component groups (e.g., boards, committees, task forces, etc.) collaborate more effectively in an online environment? • How can official documents (e.g., minutes, reports, newsletters, etc.) be more easily published to the Web by SAA’s component groups, described and accessed via appropriate metadata, and scheduled for retention? • How can SAA enhance its online publishing capabilities and ensure that the necessary tools are available for authorized subject experts to edit and update such official electronic publications as Richard Pearce-Moses’ Glossary of Archival and Records Management Terminology , DACS Online, and the EAD Help Pages, as well as such important resources as an SAA standards portal or the Technology Best Practices Task Force working document? Report: Website Working Group Page 1 of 17 0808-1-WebWG-IIO SAA’s existing Web technology does not adequately fulfill these needs.