Impact of User Data Privacy Management Controls on Mobile Device Investigations Panagiotis Andriotis, Theo Tryfonas
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Protecting Location Privacy Fromuntrusted Wireless Service
Protecting Location Privacy from Untrusted Wireless Service Providers Keen Sung Brian Levine Mariya Zheleva University of Massachusetts Amherst University of Massachusetts Amherst University at Albany, SUNY [email protected] [email protected] [email protected] ABSTRACT 1 INTRODUCTION Access to mobile wireless networks has become critical for day- When mobile users connect to the Internet, they authenticate to a to-day life. However, it also inherently requires that a user’s geo- cell tower, allowing service providers such as Verizon and AT&T graphic location is continuously tracked by the service provider. to store a log of the time, radio tower, and user identity [69]. As It is challenging to maintain location privacy, especially from the providers have advanced towards the current fifth generation of provider itself. To do so, a user can switch through a series of iden- cellular networks, the density of towers has grown, allowing these tifiers, and even go offline between each one, though it sacrifices logs to capture users’ location with increasing precision. Many users utility. This strategy can make it difficult for an adversary to per- are persistently connected, apprising providers of their location all form location profiling and trajectory linking attacks that match day. Connecting to a large private Wi-Fi network provides similar observed behavior to a known user. information to its administrators. And some ISPs offer cable, cellular, In this paper, we model and quantify the trade-off between utility and Wi-Fi hotspots as a unified package. and location privacy. We quantify the privacy available to a com- While fixed user identifiers are useful in supporting backend munity of users that are provided wireless service by an untrusted services such as postpaid billing, wireless providers’ misuse of provider. -

SGP Technologies Et INNOV8 Annoncent Le Lancement En Avant-Première Mondiale Du Smartphone BLACKPHONE Dans Les Boutiques LICK
PRESS RELEASE SGP Technologies et INNOV8 annoncent le lancement en avant-première mondiale du smartphone BLACKPHONE dans les boutiques LICK Paris (France) / Geneva (Suisse), 5 Juin 2014. Blackphone, le premier smartphone qui permet la sécurité de la vie privée des utilisateurs, sera lancé en avant-première cet été en France chez LICK, 1er réseau de boutiques 2.0 dédié aux objets connectés. SGP Technologies (Joint-Venture entre Silent Circle et Geeksphone) créateur du BLACKPHONE a choisi le groupe INNOV8, pour dévoiler le premier smartphone qui respecte la vie privée, à l’occasion de l’ouverture de LICK (Groupe INNOV8), le premier réseau de boutiques 2.0 dédié aux objets connectés, le 5 juin au Concept Store des 4 Temps à la Défense. Dès cet été, LICK sera le premier réseau de magasins autorisé à distribuer cette innovation technologique. La distribution sera ensuite ouverte à d’autres canaux en France via Extenso Telecom (Leader de la distribution de smartphones, accessoires et objets connectés en France) afin de proposer au plus grand nombre cette innovation technologique en phase avec les attentes des clients soucieux du respect de leur vie privée et de leur sécurité. "La France est connue pour être très ouverte à l’innovation. Nous sommes heureux de travailler avec le groupe INNOV8 pour lancer le Blackphone sur ce marché important en Europe et d'offrir aux utilisateurs de smartphones une solution inégalée pour la protection de leur vie privée et de leur sécurité», a déclaré Tony Bryant, VP Sales de SGP Technologies. « Nous sommes convaincus que la technologie devient un véritable style de vie. -

How the Rise of Big Data and Predictive Analytics Are Changing the Attorney's Duty of Competence Peter Segrist
NORTH CAROLINA JOURNAL OF LAW & TECHNOLOGY Volume 16 | Issue 3 Article 6 3-1-2015 How the Rise of Big Data and Predictive Analytics Are Changing the Attorney's Duty of Competence Peter Segrist Follow this and additional works at: http://scholarship.law.unc.edu/ncjolt Part of the Law Commons Recommended Citation Peter Segrist, How the Rise of Big Data and Predictive Analytics Are Changing the Attorney's Duty of Competence, 16 N.C. J.L. & Tech. 527 (2015). Available at: http://scholarship.law.unc.edu/ncjolt/vol16/iss3/6 This Article is brought to you for free and open access by Carolina Law Scholarship Repository. It has been accepted for inclusion in North Carolina Journal of Law & Technology by an authorized administrator of Carolina Law Scholarship Repository. For more information, please contact [email protected]. NORTH CAROLINA JOURNAL OF LAW & TECHNOLOGY VOLUME 16, ISSUE 3: MARCH 2015 HOW THE RISE OF BIG DATA AND PREDICTIVE ANALYTICS ARE CHANGING THE ATTORNEY’S DUTY OF COMPETENCE Peter Segrist* If the legal profession had been able to foresee in the late 1990s and early 2000s, prior to the meteoric rise and ensuing cultural ubiquity of social media, that every tagged spring break photo, 2:00 a.m. status update, and furious wall post would one day be vulnerable to potential exposure in the cold, unforgiving light of civil and criminal litigation, attorneys would have been well-advised to discuss the ramifications of such actions, statements, and disclosures with their clients. Today, a similar phenomenon is looming in the form of the collection, aggregation, analysis and sale of personal data, and it will be the prudent attorney who competently advises his clients to stay ahead of the curve. -

Tii Internet Intelligence Newsletter
TODDINGTON INTERNATIONAL INC. TII INTERNET INTELLIGENCE NEWSLETTER MARCH 2014 EDITION IN THIS EDITION FEATURED ARTICLES: WELCOME TO THE MARCH EDITION OF THE TII ONLINE • Tor Project Updates RESEARCH AND INTELLIGENCE NEWSLETTER • Smart Phone Spying for the Masses • Secure Communications: Silent We’d like to thank all of those who attended last month’s 3-day Circle and Geeksphone Release Internet Intelligence workshops in Vancouver and Toronto. With a “Blackphone” full compliment of delegates from Canada, the US, the Caribbean, • Deanonymizing Documents and Europe and the Middle East, the workshops represented a great Identifying Authorship Through learning and networking opportunity, as well as a chance to see two Stylometry of Canada’s most beautiful cities. • Changing Our World: The Internet of With updated curriculums, our next Canadian-based 3-day Things Advanced Internet Intelligence Training conferences will be in Vancouver at the Pan Pacific Hotel September 22 - 24, 2014 and UPCOMING EVENTS: Toronto at the Royal York Hotel October 6 - 8, 2014. • OSIRA Inaugural Conference - We will also be conducting a 2-day Advanced Online OSINT London: May 7th - 8th workshop in Hong Kong April 2nd to 3rd, 2014, and presenting our bi-annual 3-day Internet Intelligence Training conference at RESOURCES FOR INVESTIGATORS & INTELLIGENCE the University of Cambridge in conjunction with our friends at the PROFESSIONALS: International Chamber of Commerce, Commercial Crime Services, April 7th to 9th, 2014. • eLearning “Using the Internet as an Investigative Research Tool” Congratulations to our students who have completed our e-Learning • Useful Sites & Resources for courses in the last two months: Paul Smith, Annette Scheer, Laureen Investigators Molulu-Knight - Custom House, Frank Sirianni - Ontario Lottery and Gaming Corporation, Chris Pyer - UK, Steve Ganyu - RBC, Michelle • Also of Interest Cameron - RCMP and Alexandra Phillips - Australian Defence. -

RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER
NOW SUPPORTING 19,203 DEVICE PROFILES +1,528 APP VERSIONS UFED TOUCH, UFED 4PC, RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER COMMON/KNOWN HIGHLIGHTS System Images IMAGE FILTER ◼ Temporary root (ADB) solution for selected Android Focus on the relevant media files and devices running OS 4.3-5.1.1 – this capability enables file get to the evidence you need fast system and physical extraction methods and decoding from devices running OS 4.3-5.1.1 32-bit with ADB enabled. In addition, this capability enables extraction of apps data for logical extraction. This version EXTRACT DATA FROM BLOCKED APPS adds this capability for 110 devices and many more will First in the Industry – Access blocked application data with file be added in coming releases. system extraction ◼ Enhanced physical extraction while bypassing lock of 27 Samsung Android devices with APQ8084 chipset (Snapdragon 805), including Samsung Galaxy Note 4, Note Edge, and Note 4 Duos. This chipset was previously supported with UFED, but due to operating system EXCLUSIVE: UNIFY MULTIPLE EXTRACTIONS changes, this capability was temporarily unavailable. In the world of devices, operating system changes Merge multiple extractions in single unified report for more frequently, and thus, influence our support abilities. efficient investigations As our ongoing effort to continue to provide our customers with technological breakthroughs, Cellebrite Logical 10K items developed a new method to overcome this barrier. Physical 20K items 22K items ◼ File system and logical extraction and decoding support for iPhone SE Samsung Galaxy S7 and LG G5 devices. File System 15K items ◼ Physical extraction and decoding support for a new family of TomTom devices (including Go 1000 Point Trading, 4CQ01 Go 2505 Mm, 4CT50, 4CR52 Go Live 1015 and 4CS03 Go 2405). -

Why “Mobile” Security Is the Hardest Security
Tufts University School of Engineering COMP 111 - Security Why “Mobile” Security is the Hardest Security By Kevin Dorosh Abstract Tech-savvy people understand that Android is less safe than iPhone, but most don’t understand how glaring cell phone security is across the board. Android’s particularly lackluster performance is exemplified in the MAC address randomization techniques employed to prevent others from being able to stalk your location through your mobile device. MAC address randomization was introduced by Apple in June of 2014 and by Google in 2015, although (glaringly) only 6% of Android devices today currently have this tech [3]. Sadly, in devices with the tech enabled, the Karma attack can still be exploited. Even worse, both iOS and Android are susceptible to RTS (request to send frame) attacks. Other power users have even seen success setting up desktop GSM towers as intermediaries between mobile devices and real cell phone towers to gather similar information [5]. This paper attempts to explain simple techniques to glean information from other mobile phones that can be used for nefarious purposes from stalking to identity fraud, but also by government agencies to monitor evildoers without their knowledge. As this paper should make clear, mobile security is far more difficult than “stationary security”, for lack of a better term. Even worse, some of these flaws are problems exist with the Wi-Fi protocol itself, but we will still offer solutions to mitigate risks and fix the protocols. As we do more on our phones every day, it becomes imperative that we understand and address these risks. -

Zapdroid: Managing Infrequently Used Applications on Smartphones Indrajeet Singh Srikanth V
ZapDroid: Managing Infrequently Used Applications on Smartphones Indrajeet Singh Srikanth V. Krishnamurthy Harsha V. Madhyastha UC Riverside UC Riverside University of Michigan [email protected] [email protected] [email protected] Iulian Neamtiu UC Riverside [email protected] ABSTRACT More generally, users may only interact with some down- User surveys have shown that a typical user has over loaded apps infrequently (i.e., not use them for prolonged a hundred apps on her smartphone [1], but stops using periods). These apps continue to operate in the back- many of them. We conduct a user study to identify such ground and have significant negative effects (e.g., leak unused apps, which we call zombies, and show via exper- private information or significantly tax resources such iments that zombie apps consume significant resources as the battery). Unfortunately, users are often unaware on a user's smartphone and access her private informa- of such app activities. We call such seldom-used apps, tion. We then design and build ZapDroid, which enables which indulge in undesired activities, \zombie apps." users to detect and silo zombie apps in an effective way In this paper, we seek to build a framework, ZapDroid, to to prevent their undesired activities. If and when the identify and subsequently quarantine such zombie apps user wishes to resume using such an app, ZapDroid re- to stop their undesired activities. Since a user can change stores the app quickly and effectively. Our evaluations her mind about whether or not to use an app, a zombie show that: (i) ZapDroid saves twice the energy from un- app must be restored quickly if the user chooses.1 wanted zombie app behaviors as compared to apps from the Play Store that kill background unwanted processes, The classification of an app as a zombie app is inher- and (ii) it effectively prevents zombie apps from using ently subjective. -

Untraceable Links: Technology Tricks Used by Crooks to Cover Their Tracks
UNTRACEABLE LINKS: TECHNOLOGY TRICKS USED BY CROOKS TO COVER THEIR TRACKS New mobile apps, underground networks, and crypto-phones are appearing daily. More sophisticated technologies such as mesh networks allow mobile devices to use public Wi-Fi to communicate from one device to another without ever using the cellular network or the Internet. Anonymous and encrypted email services are under development to evade government surveillance. Learn how these new technology capabilities are making anonymous communication easier for fraudsters and helping them cover their tracks. You will learn how to: Define mesh networks. Explain the way underground networks can provide untraceable email. Identify encrypted email services and how they work. WALT MANNING, CFE President Investigations MD Green Cove Springs, FL Walt Manning is the president of Investigations MD, a consulting firm that conducts research related to future crimes while also helping investigators market and develop their businesses. He has 35 years of experience in the fields of criminal justice, investigations, digital forensics, and e-discovery. He retired with the rank of lieutenant after a 20-year career with the Dallas Police Department. Manning is a contributing author to the Fraud Examiners Manual, which is the official training manual of the ACFE, and has articles published in Fraud Magazine, Police Computer Review, The Police Chief, and Information Systems Security, which is a prestigious journal in the computer security field. “Association of Certified Fraud Examiners,” “Certified Fraud Examiner,” “CFE,” “ACFE,” and the ACFE Logo are trademarks owned by the Association of Certified Fraud Examiners, Inc. The contents of this paper may not be transmitted, re-published, modified, reproduced, distributed, copied, or sold without the prior consent of the author. -
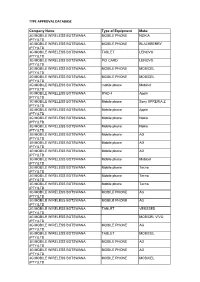
Type Approval Database 2017031231.Pdf
TYPE APPROVAL DATABASE Company Name Type of Equipment Make 3G MOBILE WIRELESS BOTSWANA MOBILE PHONE NOKIA (PTY)LTD 3G MOBILE WIRELESS BOTSWANA MOBILE PHONE BLACKBERRY (PTY)LTD 3G MOBILE WIRELESS BOTSWANA TABLET LENOVO (PTY)LTD 3G MOBILE WIRELESS BOTSWANA PCI CARD LENOVO (PTY)LTD 3G MOBILE WIRELESS BOTSWANA MOBILE PHONE MOBICEL (PTY)LTD 3G MOBILE WIRELESS BOTSWANA MOBILE PHONE MOBICEL (PTY)LTD 3G MOBILE WIRELESS BOTSWANA mobile phone Mobicel (PTY)LTD 3G MOBILE WIRELESS BOTSWANA IPAD 4 Apple (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone Sony XPRERIA Z (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone Apple (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone Nokia (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone Nokia (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone AG (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone AG (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone AG (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone Mobicel (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone Tecno (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone Tecno (PTY)LTD 3G MOBILE WIRELESS BOTSWANA Mobile phone Tecno (PTY)LTD 3G MOBILE WIRELESS BOTSWANA MOBILE PHONE AG (PTY)LTD 3G MOBILE WIRELESS BOTSWANA MOBILE PHONE AG (PTY)LTD 3G MOBILE WIRELESS BOTSWANA TABLET VERSSED (PTY)LTD 3G MOBILE WIRELESS BOTSWANA MOBICEL VIVO (PTY)LTD 3G MOBILE WIRELESS BOTSWANA MOBILE PHONE AG (PTY)LTD 3G MOBILE WIRELESS BOTSWANA TABLET MOBICEL (PTY)LTD 3G MOBILE WIRELESS BOTSWANA MOBILE PHONE AG (PTY)LTD 3G MOBILE WIRELESS BOTSWANA MOBILE PHONE AG (PTY)LTD 3G MOBILE WIRELESS BOTSWANA -

Ecodesign Preparatory Study on Mobile Phones, Smartphones and Tablets
Ecodesign preparatory study on mobile phones, smartphones and tablets Draft Task 4 Report Technologies Written by Fraunhofer IZM, Fraunhofer ISI, VITO October – 2020 Authors: Karsten Schischke (Fraunhofer IZM) Christian Clemm (Fraunhofer IZM) Anton Berwald (Fraunhofer IZM) Marina Proske (Fraunhofer IZM) Gergana Dimitrova (Fraunhofer IZM) Julia Reinhold (Fraunhofer IZM) Carolin Prewitz (Fraunhofer IZM) Christoph Neef (Fraunhofer ISI) Contributors: Antoine Durand (Quality control, Fraunhofer ISI) Clemens Rohde (Quality control, Fraunhofer ISI) Simon Hirzel (Quality control, Fraunhofer ISI) Mihaela Thuring (Quality control, contract management, VITO) Study website: https://www.ecosmartphones.info EUROPEAN COMMISSION Directorate-General for Internal Market, Industry, Entrepreneurship and SMEs Directorate C — Sustainable Industry and Mobility DDG1.C.1 — Circular Economy and Construction Contact: Davide Polverini E-mail: [email protected] European Commission B-1049 Brussels 2 Ecodesign preparatory study on mobile phones, smartphones and tablets Draft Task 4 Report Technologies 4 EUROPEAN COMMISSION Europe Direct is a service to help you find answers to your questions about the European Union. Freephone number (*): 00 800 6 7 8 9 10 11 (*) The information given is free, as are most calls (though some operators, phone boxes or hotels may charge you). LEGAL NOTICE This document has been prepared for the European Commission however it reflects the views only of the authors, and the Commission cannot be held responsible for any use which may be made of the information contained therein. More information on the European Union is available on the Internet (http://www.europa.eu). Luxembourg: Publications Office of the European Union, 2020 ISBN number doi:number © European Union, 2020 Reproduction is authorised provided the source is acknowledged. -

Ace-Q1-Sep-2016
P1 / MOBILE P2 / NANOSTRUCTURED P3 / SCREENLESS P4 / THE REAL 4G COLLABORATION CARBON COMPOSITES DISPLAY Such breakthroughs could The app synchronized his New techniques to Holographic colour video give networks some 30 times Recyclable contributions with everyone nanostructure carbon fibres display with the resolution as much capacity as LTE- else’s for novel composites of a standard TV. Advanced. Thermoset Plastics Called poly(hexahydrotriazine)s, or PHTs, these can be dissolved in strong acid, A new kind of plastic to cut landfill waste breaking apart the polymer chains into component monomers that can then be NEW HORIZON COLLEGE OF ENGINEERING Plastics are divided into thermoplastics and reassembled into new products. Like thermoset plastics. The former can be heated and traditional unrecyclable thermosets, these shaped many times and are ubiquitous in the new structures are rigid, resistant to heat ADVANCED CONTEMPORARY and tough, with the same potential modern world, comprising everything from applications as their unrecyclable children’s toys to lavatory seats. Because they can forerunners. EMERGING TECHNOLOGY be melted down and reshaped, thermoplastics are Although no recycling is 100 percent generally recyclable. Thermoset plastics, however, efficient, this innovation—if widely can only be heated and shaped once, after which deployed—should speed up the move DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING ACE / Q1 / SEP 2016 molecular changes mean they are “cured,” impossible to recycle. As a result, most thermoset toward a circular economy, with a big reduction in landfill waste from plastics. We retaining their shape and strength even when polymers end up as landfill. Given the ultimate expect recyclable thermoset polymers to subjected to intense heat and pressure. -

UNIVERSITY of CALIFORNIA RIVERSIDE Improving User Privacy
UNIVERSITY OF CALIFORNIA RIVERSIDE Improving User Privacy in Emerging Platforms A Dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science by Indrajeet Singh December 2014 Dissertation Committee: Professor Srikanth Krishnamurthy, Chairperson Professor Harsha Madhyastha Professor Eamonn Keogh Professor Neal Young Professor Iulian Neamtiu Copyright by Indrajeet Singh 2014 The Dissertation of Indrajeet Singh is approved: Committee Chairperson University of California, Riverside To my family and my near and dear ones. Thank you all for the constant support, encouragement, and love throughout my life. iv ABSTRACT OF THE DISSERTATION Improving User Privacy in Emerging Platforms by Indrajeet Singh Doctor of Philosophy, Graduate Program in Computer Science University of California, Riverside, December 2014 Professor Srikanth Krishnamurthy, Chairperson With the advent of personalized services and devices, like online social networks and smartphones, a user’s (otherwise private or sensitive) information is shared with these platforms. While this sharing of information undoubtedly adds value to the user’s experience, it raises some pressing concerns about the user’s privacy, or the lack of it. In this dissertation, we propose three major frameworks designed and implemented specif- ically to protect the users’ privacy on such emerging and highly personalized platforms. The three frameworks are as follows. 1. Twitsper, a wrapper for Twitter that allows user to exchange private messages without hurting Twitter’s commercial interest. 2. Hermes, a decentralized social network with architecture the explicit goal of preserving a user’s privacy and anonymity (including even their sharing patterns) while minimizing the cost each user incurs due to the decentralized model.