Turkish National Cyber-Firewall to Mitigate Countrywide Cyber-Attacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

China, Encryption Policy, and International Influence 3
A HOOVER INSTITUTION ESSAY China, Encryption Policy, and International Influence ADAM SEGAL Series Paper No. 1610 Hanging over the stand-off between the FBI and Apple over access to an encrypted iPhone used by one of the San Bernardino attackers was the question: What would China do?1 If Apple created unique software that allowed Washington access to the phone, would that open the door for Beijing to make similar demands on the company and all other foreign technology firms operating in China? As Senator Ron Wyden of Oregon argued, “This move by the FBI could snowball around the world. Why in the world would our government want to give repressive regimes in Russia and China a blueprint for forcing American companies to create a backdoor?”2 There was, at least at the rhetorical level, interaction between Chinese and US policymakers on the question of encryption. An early draft of China’s counterterrorism Law and Technology, Security, National law, for example, included provisions requiring the installation of backdoors and the reporting of encryption keys. President Barack Obama criticized these provisions in a March 2015 interview with Reuters, claiming they “would essentially force all foreign companies, including US companies, to turn over to the Chinese government mechanisms where they could snoop and keep track of all the users of those services.” He added, “We’ve made very clear to them [the Chinese government] that this is something they’re going to have to change if they expect to do business with the United States.”3 A few days -

Final Study Report on CEF Automated Translation Value Proposition in the Context of the European LT Market/Ecosystem
Final study report on CEF Automated Translation value proposition in the context of the European LT market/ecosystem FINAL REPORT A study prepared for the European Commission DG Communications Networks, Content & Technology by: Digital Single Market CEF AT value proposition in the context of the European LT market/ecosystem Final Study Report This study was carried out for the European Commission by Luc MEERTENS 2 Khalid CHOUKRI Stefania AGUZZI Andrejs VASILJEVS Internal identification Contract number: 2017/S 108-216374 SMART number: 2016/0103 DISCLAIMER By the European Commission, Directorate-General of Communications Networks, Content & Technology. The information and views set out in this publication are those of the author(s) and do not necessarily reflect the official opinion of the Commission. The Commission does not guarantee the accuracy of the data included in this study. Neither the Commission nor any person acting on the Commission’s behalf may be held responsible for the use which may be made of the information contained therein. ISBN 978-92-76-00783-8 doi: 10.2759/142151 © European Union, 2019. All rights reserved. Certain parts are licensed under conditions to the EU. Reproduction is authorised provided the source is acknowledged. 2 CEF AT value proposition in the context of the European LT market/ecosystem Final Study Report CONTENTS Table of figures ................................................................................................................................................ 7 List of tables .................................................................................................................................................. -

Download on Our Platform and We Have Obtained Licenses from Many Content Providers
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 Form 20-F (Mark One) ¨ REGISTRATION STATEMENT PURSUANT TO SECTION 12(b) OR 12(g) OF THE SECURITIES EXCHANGE ACT OF 1934 or x ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2013. or ¨ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to or ¨ SHELL COMPANY REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 Date of event requiring this shell company report Commission file number: 000-51469 Baidu, Inc. (Exact name of Registrant as specified in its charter) N/A (Translation of Registrant’s name into English) Cayman Islands (Jurisdiction of incorporation or organization) Baidu Campus No. 10 Shangdi 10th Street Haidian District, Beijing 100085 The People’s Republic of China (Address of principal executive offices) Jennifer Xinzhe Li, Chief Financial Officer Telephone: +(86 10) 5992-8888 Email: [email protected] Facsimile: +(86 10) 5992-0000 Baidu Campus No. 10 Shangdi 10th Street, Haidian District, Beijing 100085 The People’s Republic of China (Name, Telephone, Email and/or Facsimile number and Address of Company Contact Person) Securities registered or to be registered pursuant to Section 12(b) of the Act: Title of Each Class Name of Each Exchange on Which Registered American depositary shares (ten American depositary shares representing one Class A ordinary share, The NASDAQ Stock Market LLC par value US$0.00005 per share) (The NASDAQ Global Select Market) Class A ordinary shares, par value US$0.00005 per share* The NASDAQ Stock Market LLC (The NASDAQ Global Select Market) * Not for trading, but only in connection with the listing on The NASDAQ Global Select Market of American depositary shares. -

Applications: S
Applications: S This chapter contains the following sections: • Sabah, on page 9 • Safari, on page 10 • SAFT, on page 11 • Sage, on page 12 • Sahibinden, on page 13 • Saks Fifth Avenue, on page 14 • Salesforce.com, on page 15 • Salesforce.com Live Agent, on page 16 • Sam's Club, on page 17 • Sametime, on page 18 • SAMR, on page 19 • Samsung, on page 20 • Samsung Push Notification, on page 21 • SANity, on page 22 • Sanook.com, on page 23 • SAP, on page 24 • SAP HostControl, on page 25 • SASCDN, on page 26 • SATNET, on page 27 • SATNET and Backroom EXPAK, on page 28 • SATNET Monitoring, on page 29 • SaveFrom, on page 30 • Sberbank of Russia, on page 31 • SBS, on page 32 • SCC Security, on page 33 • SCCM, on page 34 • SCCM Remote Control, on page 35 • SCCP, on page 36 • Schedule Transfer Protocol, on page 37 • schuelerVZ, on page 38 • Schwab, on page 39 • ScienceDirect, on page 40 Applications: S 1 Applications: S • SCO Desktop Administration Server, on page 41 • Sco I2 Dialog Daemon, on page 42 • SCO System Administration Server, on page 43 • SCO Web Server Manager 3, on page 44 • SCO WebServer Manager, on page 45 • scohelp, on page 46 • Scopia, on page 47 • Scopia Audio, on page 48 • Scopia Video, on page 49 • Scorecard Research, on page 50 • Scottrade, on page 51 • SCPS, on page 52 • Scribd, on page 53 • Scribd Upload, on page 54 • Scribol, on page 55 • SCSI-ST, on page 56 • SCTP, on page 57 • scx-proxy, on page 58 • SDNS-KMP, on page 59 • SDRP, on page 60 • Seamonkey, on page 61 • Search-Result.com, on page 62 • Searchnu, on page 63 • -

User Browsing Graph: Structure, Evolution and Application1
User Browsing Graph: Structure, Evolution and Application1 Yiqun Liu, Min Zhang, Shaoping Ma, Liyun Ru State Key Lab of Intelligent Technology and Systems Tsinghua National Laboratory for Information Science and Technology Department of Computer Science and Technology Tsinghua University, Beijing, 100084, China P.R. [email protected] ABSTRACT don’t work very well in this new situation. This paper focuses on ‘user browsing graph’ which is constructed Recently, the wisdom of the crowd is paid much attention in with users’ click-through behavior modeled with Web access logs. Web search researches, e.g. [7], [8] and [9]. In their work, users’ User browsing graph has recently been adopted to improve Web browsing behavior is usually considered as implicit feedback search performance and the initial study shows it is more reliable information for page relevance and importance. For example, Liu than hyperlink graph for inferring page importance. However, et. al. constructed ‘user browsing graph’ with search log data [10]. structure and evolution of the user browsing graph haven’t been They proposed a page importance estimation algorithm called fully studied and many questions remain to be answered. In this BrowseRank which performs on the user browsing graph. It is paper, we look into the structure of the user browsing graph and believed that the link structure in user browsing graph is more its evolution over time. We try to give a quantitative analysis on reliable than hyperlink graph because users actually follow links the difference in graph structure between hyperlink graph and in the browsing graph. user browsing graph, and then find out why link analysis Liu’s initial study shows that the BrowseRank algorithm works algorithms perform better on the browsing graph. -

Thème : Le Web Les Moteurs De Recherche Moteur De Recherche
Thème : Le Web Les moteurs de recherche Capacités attendues : - Comprendre le fonctionnement des moteurs de recherche - Mener une analyse critique des résultats d’un moteur de recherche - Comprendre les enjeux de la publication d’informations Moteur de recherche : application informatique permettant de rechercher une ressource (page Web, image, vidéo, fichier…) à partir d’une requête sous forme de mots-clés. 1. Le fonctionnement des moteurs de recherche * Au brouillon, essayez de schématiser le fonctionnement d’un moteur de recherche. Vocabulaire à retenir : - crawlers : robot d’indexation qui explore automatiquement le Web en suivant les liens entre les différentes pages pour collecter les ressources. - indexation : les mots-clés sont listés, classés et enregistrés sur des serveurs qui stockent les données. - pertinence : répond au besoin au moment où il est exprimé. Le Web est un immense graphe : chaque page est un noeud relié à d’autres nœuds par des liens hypertextes. On pourrait le schématiser de façon très simplifiée, comme ci-contre. Mme Suaudeau SNT 2019-2020 * A partir du nœud E, parcourez le graphe précédant en listant les pages consultées et les pages à visiter à chaque étape : Action Pages visitées Pages à visiter On visite E, lié à A et H E A H On visite A , lié à B E A H B On visite H , lié à J E A H B J On visite B , lié à A et C E A H B J C (A déjà visité) On visite J , lié à F E A H B J C F On visite C , lié à A E A H B J C C F (A déjà visité) On visite F , lié à C D G H E A H B J C F D G (C et H déjà visités) On visite D , lié à / E A H B J C F D G On visite G , lié à / E A H B J C F D G * Que se passe-t-il si l’on commence l’exploration par le nœud A ? La visite est terminée en 3 étapes mais on a « raté » une grande partie du graphe. -

CHAPTER 6: Governance and Order in a Networked World
6 GOVERNANCE AND ORDER IN A NETWORKED WORLD Niall Ferguson “ s the world slouching toward a grave systemic crisis?” asked the his- Itorian Philip Zelikow at the annual gathering of the Aspen Strategy Group earlier this summer, the kind of “deep system- wide crisis . when people all over the world no longer think the old order work[s].” Among the reasons he gave for anticipating such a crisis was “the digital revolution and the rise of a networked world.” To grasp the scale and nature of this coming crisis, we must begin by recognizing how drasti- cally the balance of power has shift ed in our time from hierarchically ordered empires and superpowers (the euphemism for empire developed to suit American and Soviet sensibilities) to distributed networks. To be sure, the formal “org. chart” of global power is still dominated by the vertically structured super- polities that gradually evolved out of the republics and monarchies of early modern Europe, the colonies they established in the New World, and the older empires of Asia. Th ough not the most populous nation in the world, the United States is certainly the world’s most powerful state, despite—or perhaps because of—the peculiarities of its political system. Its nearest rival, the People’s Republic of China, is usually seen as a profoundly diff erent kind of state, for while the United States has two major parties, the People’s Republic has one, and only one. Th e US government is founded on the separation 159 119106-Shultz_BeyondDisruption.indd9106-Shultz_BeyondDisruption.indd 159159 33/23/18/23/18 77:12:12 PMPM 160 Niall Ferguson of powers, not least the independence of its judiciary; the PRC subordi- nates all other institutions, including the courts, to the dictates of the Communist Party. -

Sogou Announces Fourth Quarter and Full Year 2020 Results BEIJING, China, February 4, 2021 – Sogou Inc. (NYSE: SOGO) ("So
Sogou Announces Fourth Quarter and Full Year 2020 Results BEIJING, China, February 4, 2021 – Sogou Inc. (NYSE: SOGO) ("Sogou" or the “Company"), an innovator in search and a leader in China's internet industry, today announced its unaudited financial results for the fourth quarter and full year, ended December 31, 2020. Fourth Quarter 2020 Financial Results Total revenues1 were $189.5 million, a 37% decrease year-over-year. The decrease was primarily driven by uncertainties with respect to Sogou’s business policies among certain advertisers as a result of the previously-announced proposal by Tencent Holdings Limited (“Tencent”) to take Sogou private, as well as reduced traffic acquisition activity. • Search and search-related revenues were $166.7 million, a 39% decrease year- over-year. Auction-based pay-for-click services decreased year-over-year, accounting for 84.0% of search and search-related revenues, compared to 88.2% in the corresponding period in 2019. • Other revenues were $22.8 million, a 14% decrease year-over-year. The decrease was primarily due to decreased revenues from non-core businesses. Cost of revenues was $151.2 million, a 10% decrease year-over-year. Traffic acquisition cost, a primary driver of cost of revenues, was $115.5 million, a 10% decrease year-over-year, representing 60.9% of total revenues, compared to 42.8% in the corresponding period in 2019. The decrease in traffic acquisition costs was driven by decreased traffic acquisition from third parties. Gross profit and non-GAAP2 gross profit were both $38.3 million, a 71% decrease year- over-year for both. -

Is Google the Next Microsoft? Competition, Welfare and Regulation in Online Search
IS GOOGLE THE NEXT MICROSOFT? COMPETITION, WELFARE AND REGULATION IN ONLINE SEARCH RUFUS POLLOCK UNIVERSITY OF CAMBRIDGE Abstract. The rapid growth of online search and its centrality to the ecology of the Internet pose important questions: why is the search engine market so concentrated and will it evolve towards monopoly? What implications does this concentration have for consumers, search engines, and advertisers? Does search require regulation and if so in what form? This paper supplies empirical and theoretical material with which to examine these questions. In particular, we (a) show that the already large levels of concentration are likely to continue (b) identify the consequences, negative and positive, of this outcome (c) discuss the regulatory interventions that policy-makers could use to address these. Keywords: Search Engine, Regulation, Competition, Antitrust, Platform Markets JEL Classification: L40 L10 L50 Emmanuel College and Faculty of Economics, University of Cambridge. Email: [email protected] or [email protected]. I thank the organizers of 2007 IDEI Toulouse Conference on the Economics of the Software and Internet Industries whose search round-table greatly stimulated my thoughts on this topic as well as participants at seminars in Cambridge and at the 2009 RES conference. Particular thanks is also due to the editor and anonymous referee who provided an excellent set of comments that served to greatly improve the paper. Finally, I would like to thank http://searchenginewatch.com and Hitwise who both generously provided me with access to some of their data. This work is licensed under a Creative Commons Attribution Licence (v3.0, all jurisdictions). -
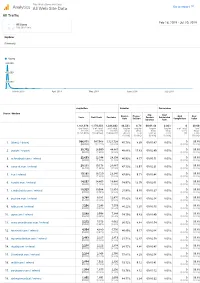
Thiswaifudoesnotexist.Net: Google Analytics: All Traffic 20190218-20190720
This Waifu Does Not Exist Analytics All Web Site Data Go to report All Traffic Feb 18, 2019 - Jul 20, 2019 All Users 100.00% Users Explorer Summary Users 600,000 400,000 200,000 March 2019 April 2019 May 2019 June 2019 July 2019 Acquisition Behavior Conversions Source / Medium Avg. Goal Bounce Pages / Goal Goal Users New Users Sessions Session Conversion Rate Session Completions Value Duration Rate 1,161,978 1,170,333 1,384,602 46.58% 8.74 00:01:48 0.00% 0 $0.00 % of Total: % of Total: % of Total: Avg for Avg for Avg for Avg for % of Total: % of 100.00% 100.07% 100.00% View: View: View: View: 0.00% Total: (1,161,978) (1,169,566) (1,384,602) 46.58% 8.74 00:01:48 0.00% (0) 0.00% (0.00%) (0.00%) (0.00%) (0.00%) ($0.00) 1. (direct) / (none) 966,071 967,968 1,121,738 45.78% 8.39 00:01:47 0.00% 0 $0.00 (82.06%) (82.71%) (81.02%) (0.00%) (0.00%) 2. google / organic 30,702 28,990 44,887 48.86% 15.63 00:02:49 0.00% 0 $0.00 (2.61%) (2.48%) (3.24%) (0.00%) (0.00%) 3. m.facebook.com / referral 22,693 22,544 24,304 46.93% 4.77 00:00:51 0.00% 0 $0.00 (1.93%) (1.93%) (1.76%) (0.00%) (0.00%) 4. away.vk.com / referral 20,111 19,178 26,667 47.13% 13.97 00:02:31 0.00% 0 $0.00 (1.71%) (1.64%) (1.93%) (0.00%) (0.00%) 5. -

List of Search Engines
A blog network is a group of blogs that are connected to each other in a network. A blog network can either be a group of loosely connected blogs, or a group of blogs that are owned by the same company. The purpose of such a network is usually to promote the other blogs in the same network and therefore increase the advertising revenue generated from online advertising on the blogs.[1] List of search engines From Wikipedia, the free encyclopedia For knowing popular web search engines see, see Most popular Internet search engines. This is a list of search engines, including web search engines, selection-based search engines, metasearch engines, desktop search tools, and web portals and vertical market websites that have a search facility for online databases. Contents 1 By content/topic o 1.1 General o 1.2 P2P search engines o 1.3 Metasearch engines o 1.4 Geographically limited scope o 1.5 Semantic o 1.6 Accountancy o 1.7 Business o 1.8 Computers o 1.9 Enterprise o 1.10 Fashion o 1.11 Food/Recipes o 1.12 Genealogy o 1.13 Mobile/Handheld o 1.14 Job o 1.15 Legal o 1.16 Medical o 1.17 News o 1.18 People o 1.19 Real estate / property o 1.20 Television o 1.21 Video Games 2 By information type o 2.1 Forum o 2.2 Blog o 2.3 Multimedia o 2.4 Source code o 2.5 BitTorrent o 2.6 Email o 2.7 Maps o 2.8 Price o 2.9 Question and answer .