VM/370-A Study of Multiplicity and Usefulness
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Operating System Handbook Or, Fake Your Way Through Minis and Mainframes
The Operating System Handbook or, Fake Your Way Through Minis and Mainframes by Bob DuCharme MVS Table of Contents Chapter 22 MVS: An Introduction.................................................................................... 22.1 Batch Jobs..................................................................................................................1 22.2 Interacting with MVS................................................................................................3 22.2.1 TSO.........................................................................................................................3 22.2.2 ISPF........................................................................................................................3 22.2.3 CICS........................................................................................................................4 22.2.4 Other MVS Components.........................................................................................4 22.3 History........................................................................................................................5 Chapter 23 Getting Started with MVS............................................................................... 23.1 Starting Up.................................................................................................................6 23.1.1 VTAM.....................................................................................................................6 23.1.2 Logging On.............................................................................................................6 -

IBM VM Recovery Manager DR for Power Systems Version 1.5: Deployment Guide Overview for IBM VM Recovery Manager DR for Power Systems
IBM VM Recovery Manager DR for Power Systems Version 1.5 Deployment Guide IBM Note Before using this information and the product it supports, read the information in “Notices” on page 195. This edition applies to IBM® VM Recovery Manager DR for Power Systems Version 1.5 and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 2020, 2021. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents About this document............................................................................................vii Highlighting.................................................................................................................................................vii Case-sensitivity in VM Recovery Manager DR............................................................................................vii ISO 9000....................................................................................................................................................viii Overview...............................................................................................................1 Concepts...............................................................................................................5 KSYS............................................................................................................................................................. 5 HMC............................................................................................................................................................. -
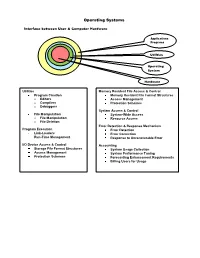
Operating Systems
Operating Systems Interface between User & Computer Hardware Applications Programs Utilities Operating System Hardware Utilities Memory Resident File Access & Control Program Creation Memory Resident File Format Structures o Editors Access Management o Compilers Protection Schemes o Debuggers System Access & Control File Manipulation System-Wide Access o File Manipulation Resource Access o File Deletion Error Detection & Response Mechanism Program Execution Error Detection Link-Loaders Error Correction Run-Time Management Response to Unrecoverable Error I/O Device Access & Control Accounting Storage File Format Structures System Usage Collection Access Management System Performance Tuning Protection Schemes Forecasting Enhancement Requirements Billing Users for Usage Resource Manager O/S KernelKernel I/O Controller Printers, Keyboards, I/O Controller Monitors, Portions of Cameras, the O/S Etc. currently in use Computer Main System Memory Portions of Various I/O Application Devices Programs Currently in use Operating System Data Application Programs I/O Controller Storage Processor Processor Data Processor Processor Operation Allocation of Main Memory is made jointly by both the O/S and Memory Management Hardware O/S controls access to I/O devices by Application Programs O/S controls access to and use of files O/S controls access to and use of the processors, i.e., how much time can be allocated to the execution of a particular Application Program Classification of Operating Systems Interactive O/S Keyboard & Monitor Access to O/S Immediate, -

PKZIP MVS User's Guide
PKZIP for MVS MVS/ESA, OS/390, & z/OS User’s Guide PKMU-V5R5000 PKWARE, Inc. PKWARE, Inc. 9009 Springboro Pike Miamisburg, Ohio 45342 Sales: 937-847-2374 Support: 937-847-2687 Fax: 937-847-2375 Web Site: http://www.pkzip.com Sales - E-Mail: [email protected] Support - http://www.pkzip.com/support 5.5 Edition (2003) PKZIP for MVS™, PKZIP for OS/400™, PKZIP for VSE™, PKZIP for UNIX™, and PKZIP for Windows™ are just a few of the many members in the PKZIP® family. PKWARE, Inc. would like to thank all the individuals and companies -- including our customers, resellers, distributors, and technology partners -- who have helped make PKZIP® the industry standard for Trusted ZIP solutions. PKZIP® enables our customers to efficiently and securely transmit and store information across systems of all sizes, ranging from desktops to mainframes. This edition applies to the following PKWARE of Ohio, Inc. licensed program: PKZIP for MVS™ (Version 5, Release 5, 2003) PKZIP(R) is a registered trademark of PKWARE(R) Inc. Other product names mentioned in this manual may be a trademark or registered trademarks of their respective companies and are hereby acknowledged. Any reference to licensed programs or other material, belonging to any company, is not intended to state or imply that such programs or material are available or may be used. The copyright in this work is owned by PKWARE of Ohio, Inc., and the document is issued in confidence for the purpose only for which it is supplied. It must not be reproduced in whole or in part or used for tendering purposes except under an agreement or with the consent in writing of PKWARE of Ohio, Inc., and then only on condition that this notice is included in any such reproduction. -

LECTURE NOTE 5: the MEMORY MANAGEMENT REAL MODE Allows the Microprocessor to Address Only the First 1Mbyte of Memory Even If Its Pentium II Microprocessor
LECTURE NOTE 5: THE MEMORY MANAGEMENT REAL MODE Allows the microprocessor to address only the first 1Mbyte of memory even if its Pentium II microprocessor. The first 1Mbyte of memory is called either the real mode or conventional memory system. The DOS operating system requires the microprocessor to operate in this mode. It allows application software. Segment and Offset Through the combination of these two, a memory location is accessed in the real mode. All real mode memory address must consist of a segment address plus an offset address. Segment Address Defines the beginning address of any 64k-byte memory segment. Offset Address Sometimes called displacement or relative. Selects any location within the 64k-byte memory segment. It is the distance above the start of the segment. Note: Each segment register is internally appended with a 0H on its right end. The segment address can begin only at a 16-byte boundary, which is called paragraph. Once the beginning address in known, an ending address is known, by adding FFFFH. The code segment register defines the start of the code segment and the instruction pointer to locate the next instruction within the code segment. This combination (CS:IP or CS:EIP) locates the next instruction executed by the microprocessor. Stack data are referenced through the stack segment at the memory location addressed by either the stack pointer (SP/ESP) or the base pointer (BP/EBP). These combinations are referred to as SS:SP (SS:ESP) or SS:BP (SS:EBP). Addressing Modes 1. Register Addressing Mode transfer a copy of a byte or word from the source register or memory location to the destination register or memory location. -

Facility/370: Introduction
File No. S370-20 Order No. GC20-1800=9 IDl\n \/:u+ •• ".1 I\n"n"': ..... ft IDIVI V IIlUQI .Via"'lllIlv Facility/370: Systems Introduction Release 6 PLC 4 This publication introduces VM/370, and is intended for anyone who is interested in VM/370. However, the reader should have a basic understanding of I BM data processing. VM/370 (Virtual Machine Facility/370) is a system control program (SCP) that tailors the resources and capabilities of a single System/370 computer to provide concurrent users their one unique (virtual) machine. VM/370 consists of a Control Program (CP), which manages the real computer, a Conversational Monitor System (CMS), which is a general-purpose conversational time-sharing system that executes in a virtual machine, a Remote Spooling Communications Subsystem (RSCS), which spools files to and from geographically remote locations, and a Interactive Problem Control System (I PCS), which provides problem analysis and management faci I ities. The first section of the publication is an introduction; it describes what VM/370 can do. The second, third, fourth, and fifth sections describe the Control Program, Conversational Monitor System, Remote Spooling Communications Subsystem, and Interactive Problem Control System respectively. The appendixes include information about VM/370 publication-to-audience relationship and VM/370-related publications for CMS users. , This publication is a prerequisite for the VM/370 system library. --...- --- ---.-- ------- ------ --..- --------- -~-y- Page of GC20-1800-9 As Updated Aug 1, 1979 by TNL GN25-0U89 ~b Edition (Karch 1919) This edition (GC20-1800-~ together with Technical Newsletter GN25-0489. dated August 1, 1919, applies to Release 6 PLC 4 (Program Level Change) of IBM Virtual Machine Facility/310 and to all subsequent releases until otherwise indicated in new editions or Technical Newsletters. -

Download for Z/OS
Print Services Facility for z/OS Version 4, Release 6.0 Download for z/OS IBM S550-0429-05 Note Before using this information and the product it supports, read the information in “Notices” on page 83. This edition applies to the IBM® Print Services Facility™ Version 4 Release 6 Modification 0 for z/OS®, Program Number 5655-M32, and to all subsequent releases and modifications until otherwise indicated in new editions. This edition replaces S550-0429-04. © Copyright International Business Machines Corporation 1995, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents List of Figures...................................................................................................... vii List of Tables........................................................................................................ ix About this publication...........................................................................................xi Who should read this publication............................................................................................................... xi How this publication is organized............................................................................................................... xi Understanding the syntax notation used in this publication......................................................................xi Related information....................................................................................................................................xii -

The Pentium Processor
Chapter 7 The Pentium Processor 7–1 The main purpose of registers is to provide a scratch pad so that the processor can keep data on a temporary basis. For example, the processor may keep the procedure return address, stack pointer, instruction pointer, and so on. Registers are also used to keep the data handy so that it can avoid costly memory accesses. Keeping frequently accessed data in registers is a common compiler optimization technique. 7–2 Pentium supports the following three address spaces: 1. Linear address space 2. Physical address space 3. I/O address space (from discussion in Section 1.7) 7–3 In segmented memory organization, memory is partitioned into segments, where each segment is a small part of the memory. In the real mode, each segment of memory is a linear contiguous sequence of up to 64 KB. In the protected mode, it can be up to 4 GB. Pentium supports segmentation largely to provide backward compatibility to 8086. Note that 8086 is a 16-bit processor with 20 address lines. This mismatch between the processor’s 16-bit registers and 20-bit addresses is solved by using the segmented memory architecture. This segmented architecture has been carried over to Pentium. However, in the protected mode, it is possible to consider the entire memory as a single segment; thus, segmentation is completely turned off. 7–4 In the real mode, a segment is limited to 64 KB due to the fact that 16 bits are used to indicate the offset value into a segment. This magic number 16 is due to the 16-bit registers used 8086 processor. -

Scalability of VM Provisioning Systems
Scalability of VM Provisioning Systems Mike Jones, Bill Arcand, Bill Bergeron, David Bestor, Chansup Byun, Lauren Milechin, Vijay Gadepally, Matt Hubbell, Jeremy Kepner, Pete Michaleas, Julie Mullen, Andy Prout, Tony Rosa, Siddharth Samsi, Charles Yee, Albert Reuther Lincoln Laboratory Supercomputing Center MIT Lincoln Laboratory Lexington, MA, USA Abstract—Virtual machines and virtualized hardware have developed a technique based on binary code substitution been around for over half a century. The commoditization of the (binary translation) that enabled the execution of privileged x86 platform and its rapidly growing hardware capabilities have (OS) instructions from virtual machines on x86 systems [16]. led to recent exponential growth in the use of virtualization both Another notable effort was the Xen project, which in 2003 used in the enterprise and high performance computing (HPC). The a jump table for choosing bare metal execution or virtual startup time of a virtualized environment is a key performance machine execution of privileged (OS) instructions [17]. Such metric for high performance computing in which the runtime of projects prompted Intel and AMD to add the VT-x [19] and any individual task is typically much shorter than the lifetime of AMD-V [18] virtualization extensions to the x86 and x86-64 a virtualized service in an enterprise context. In this paper, a instruction sets in 2006, further pushing the performance and methodology for accurately measuring the startup performance adoption of virtual machines. on an HPC system is described. The startup performance overhead of three of the most mature, widely deployed cloud Virtual machines have seen use in a variety of applications, management frameworks (OpenStack, OpenNebula, and but with the move to highly capable multicore CPUs, gigabit Eucalyptus) is measured to determine their suitability for Ethernet network cards, and VM-aware x86/x86-64 operating workloads typically seen in an HPC environment. -

Chapter 10 Introduction to Batch Files
Instructor’s Manual Chapter 10 Lecture Notes Introduction to Batch Files Chapter 10 Introduction to Batch Files LEARNING OBJECTIVES 1. Compare and contrast batch and interactive processing. 2. Explain how batch files work. 3. Explain the purpose and function of the REM, ECHO, and PAUSE commands. 4. Explain how to stop or interrupt the batch file process. 5. Explain the function and use of replaceable parameters in batch files. 6. Explain the function of pipes, filters, and redirection in batch files. STUDENT OUTCOMES 1. Use Edit to write batch files. 2. Use COPY CON to write batch files. 3. Write and execute a simple batch file. 4. Write a batch file to load an application program. 5. Use the REM, PAUSE, and ECHO commands in batch files. 6. Terminate a batch file while it is executing. 7. Write batch files using replaceable parameters. 8. Write a batch file using pipes, filters, and redirection. CHAPTER SUMMARY 1. Batch processing means running a series of instructions without interruption. 2. Interactive processing allows the user to interface directly with the computer and update records immediately. 3. Batch files allow a user to put together a string of commands and execute them with one command. 4. Batch files must have the .BAT or .CMD file extension. 5. Windows looks first internally for a command, then for a .COM files extension, then for a .EXE file extension, and finally for a .BAT or .CMD file extension. 6. Edit is a full-screen text editor used to write batch files. 7. A word processor, if it has a means to save files in ASCII, can be used to write batch files. -

Uni Hamburg – Mainframe Summit 2010 Z/OS – the Mainframe Operating System
Uni Hamburg – Mainframe Summit 2010 z/OS – The Mainframe Operating System Appendix 2 – JES and Batchprocessing Redelf Janßen IBM Technical Sales Mainframe Systems [email protected] © Copyright IBM Corporation 2010 Course materials may not be reproduced in whole or in part without the prior written permission of IBM. 4.0.1 Introduction to the new mainframe Chapter 7: Batch processing and the Job Entry Subsystem (JES) © Copyright IBM Corp., 2010. All rights reserved. Introduction to the new mainframe Chapter 7 objectives Be able to: • Give an overview of batch processing and how work is initiated and managed in the system. • Explain how the job entry subsystem (JES) governs the flow of work through a z/OS system. © Copyright IBM Corp., 2010. All rights reserved. 3 Introduction to the new mainframe Key terms in this chapter • batch processing • procedure • execution • purge • initiator • queue • job • spool • job entry subsystem (JES) • symbolic reference • output • workload manager (WLM) © Copyright IBM Corp., 2010. All rights reserved. 4 Introduction to the new mainframe What is batch processing? Much of the work running on z/OS consists of programs called batch jobs. Batch processing is used for programs that can be executed: • With minimal human interaction • At a scheduled time or on an as-needed basis. After a batch job is submitted to the system for execution, there is normally no further human interaction with the job until it is complete. © Copyright IBM Corp., 2010. All rights reserved. 5 Introduction to the new mainframe What is JES? In the z/OS operating system, JES manages the input and output job queues and data. -

Airline Control System Version 2: General Information Manual Figures
Airline Control System Version 2 IBM General Information Manual Release 4.1 GH19-6738-13 Airline Control System Version 2 IBM General Information Manual Release 4.1 GH19-6738-13 Note Before using this information and the product it supports, be sure to read the general information under “Notices” on page ix. This edition applies to Release 4, Modification Level 1, of Airline Control System Version 2, Program Number 5695-068, and to all subsequent releases and modifications until otherwise indicated in new editions. Order publications through your IBM representative or the IBM branch office serving your locality. Publications are not stocked at the address given below. A form for readers’ comments appears at the back of this publication. If the form has been removed, address your comments to: ALCS Development 2455 South Road P923 Poughkeepsie NY 12601-5400 USA When you send information to IBM, you grant IBM a nonexclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright IBM Corporation 2003, 2019. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures .................................... v Tables .................................... vii Notices .................................... ix Trademarks ................................... ix About this book ................................ xi Who should read this book .............................. xi Related publications ...............................