D4.1 Report Platform Requirement
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Learn Python the Hard Way
ptg11539604 LEARN PYTHON THE HARD WAY Third Edition ptg11539604 Zed Shaw’s Hard Way Series Visit informit.com/hardway for a complete list of available publications. ed Shaw’s Hard Way Series emphasizes instruction and making things as ptg11539604 Zthe best way to get started in many computer science topics. Each book in the series is designed around short, understandable exercises that take you through a course of instruction that creates working software. All exercises are thoroughly tested to verify they work with real students, thus increasing your chance of success. The accompanying video walks you through the code in each exercise. Zed adds a bit of humor and inside jokes to make you laugh while you’re learning. Make sure to connect with us! informit.com/socialconnect LEARN PYTHON THE HARD WAY A Very Simple Introduction to the Terrifyingly Beautiful World of Computers and Code Third Edition ptg11539604 Zed A. Shaw Upper Saddle River, NJ • Boston • Indianapolis • San Francisco New York • Toronto • Montreal • London • Munich • Paris • Madrid Capetown • Sydney • Tokyo • Singapore • Mexico City Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. The author and publisher have taken care in the preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. -

Dreamplug User Guide GTI-2010.12.10
Quick Start Guide – DreamPlug page 1 / 11 DreamPlug User Guide GTI-2010.12.10 Thank you for purchasing our DreamPlug – The Power to Innovate! This is running at 2.4GHz yet using less than 10W power consumption. This little palm-sized powerhouse can handle all your biggest tasks while still saving about 96% on energy costs when compared to the average 175 Watt desktop computer. You can customize your Plug to work in almost any industry - Cloud ComputingˈHome / Industrial Automation, Security/Surveillance, Medical Monitoring and Data Capture , High End Audio SystemsˈNetwork Storage and monitoring , VoIP and IPPBXˈSmart Grid /Mesh . You can never have enough storage, not to mention fast access to all that data. That's why we have provided Wi-Fi, Bluetooth, Gigabit Ethernet, USB 2.0 and eSATA connection options to the Server line of products. as the AUDIO INTERFACE, the dreamplug can play the music or others data from this port to the external speaker or others devices.in a word, Go ahead give us what you got, we can take it. Package contents DreamPlug Content List Remark 1 DreamPlug 1 unit 2 Detachable AC-DC Power Supply Unit 1 pc 3 Detachable DC-DC Power Cable 1 pc 4 Detachable AC Slider 1 pc 5 Detachable AC Power Cord Adaptor 1 pc 6 AC power Cord 1 pc 7 Protective Slide Cover for DreamPlug 1 pc 8 Protective Slide Cover for Power Supply Unit 1 pc 9 Ethernet Cable 1 pc 10 Warranty Card 1 pc 11 Quick Reference Guide 1 pc 12 External JTAG Debug Module No Optional item. -
Comprehensiveco.Com Retail Price List Effective 6/15/2018 Pricing Is for Authorized Comprehensive Dealers Only
Toll Free: 800-526-0242 Fax: 201-814-0510 www.comprehensiveco.com Retail Price List Effective 6/15/2018 Pricing is for authorized Comprehensive dealers only. All prices are subject to change without notice. We are not responsible for typographical errors. All terms and conditions apply. Product Type Status Model Number Description UPC MSRP RCA Audio Cables 2PP-2PP-10ST Standard Series 2 gold RCA Plugs Each End Stereo Audio Cable 10ft 808447000016 $8.99 RCA Audio Cables 2PP-2PP-15ST Standard Series 2 gold RCA Plugs Each End Stereo Audio Cable 15ft 808447011760 $10.99 RCA Audio Cables 2PP-2PP-25ST Standard Series 2 gold RCA Plugs Each End Stereo Audio Cable 25ft 808447000047 $11.99 RCA Audio Cables 2PP-2PP-3ST Standard Series 2 gold RCA Plugs Each End Stereo Audio Cable 3ft 808447011913 $3.69 RCA Audio Cables 2PP-2PP-50ST Standard Series 2 gold RCA Plugs Each End Stereo Audio Cable 50ft 808447011777 $22.99 RCA Audio Cables 2PP-2PP-6ST Standard Series 2 gold RCA Plugs Each End Stereo Audio Cable 6ft 808447000092 $6.59 AV Cables 3RCA-3RCA-10ST Standard Series General Purpose 3 RCA Video/Audio Cable 10ft 808447011784 $12.99 AV Cables 3RCA-3RCA-15ST Standard Series General Purpose 3 RCA Video/Audio Cable 15ft 808447049268 $15.99 AV Cables 3RCA-3RCA-25ST Standard Series General Purpose 3 RCA Video/Audio Cable 25ft 808447011791 $19.99 AV Cables 3RCA-3RCA-35ST Standard Series General Purpose 3 RCA Video/Audio Cable 35ft 808447049275 $29.99 AV Cables 3RCA-3RCA-3ST Standard Series General Purpose 3 RCA Video/Audio Cable 3ft 808447011807 $9.99 AV -

AC and Pwr Supply
AC and other line topics ------------------------------------------------------------------------------------------------------------ Date: Sun, 9 Nov 1997 08:02:09 +0500 From: "Chuck Rippel" <crippel@...> Subject: [R-390] Re: Help please GFI problem > Subject: Help please GFI problem > Chuck, you may have once posted suggestions to me or to the reflector > regarding the apparently naturally-ocurring leakage at the line filter > which then trips my GFI in my modern home. I wired in a nice 3-wire > grounded cord and plug to my 390A, and tripped the GFI in the bathroom > adjacent to the shack, taking out the power to the radio. Now, I just am > using a 2-pin adapter at the end of my 3-pin plug, so I've effectively > undone the update I installed. The 390 will not work in a GFI outlet. Wasn't made to pass UL in 1954. > Is there a simple fix to the radio? I'm getting all kinds of > theories from local (well-meaning) ham-friends, but would really > appreciate hearing from you on this. As always, thanks for all your > help. Would like the venerable old radio to be happy in the modern home, > with me the operator safe from annoying "tingles" or worse. I'd put on a 3 wire cord. I do on all the ones I restore. There is actually a military mod for it. It's kinda tricky to make sure you get the polarity right in the input filter tho. The black wire should attach to the terminal on the input network that is TO YOUR >RIGHT< as you face the REAR of the radio. -

Designing the Internet of Things
Designing the Internet of Things Adrian McEwen, Hakim Cassimally This edition first published 2014 © 2014 John Wiley and Sons, Ltd. Registered office John Wiley & Sons Ltd, The Atrium, Southern Gate, Chichester, West Sussex, PO19 8SQ, United Kingdom For details of our global editorial offices, for customer services and for information about how to apply for permission to reuse the copyright material in this book please see our website at www.wiley.com. The right of the author to be identified as the author of this work has been asserted in accordance with the Copyright, Designs and Patents Act 1988. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, except as permitted by the UK Copyright, Designs and Patents Act 1988, without the prior permission of the publisher. Wiley also publishes its books in a variety of electronic formats. Some content that appears in print may not be available in electronic books. Designations used by companies to distinguish their products are often claimed as trademarks. All brand names and product names used in this book are trade names, service marks, trademarks or registered trademarks of their respective owners. The publisher is not associated with any product or vendor mentioned in this book. This publication is designed to provide accurate and authoritative information in regard to the subject matter covered. It is sold on the under- standing that the publisher is not engaged in rendering professional services. If professional advice or other expert assistance is required, the services of a competent professional should be sought. -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Version 6.10.4.1/OCT.12.2018 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Copyright © 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks or registered trademarks of Symantec Corp. or its affiliates in the U.S. and other coun- tries. Other names may be trademarks of their respective owners. This document is provided for informational purposes only and is not intended as advertising. All warranties relating to the information in this document, either express or implied, are disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. Symantec Corporation 350 Ellis Street Mountain View, CA 94043 www.symantec.com Policy Guide/Page 4 Symantec Web Security Service Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology as well as the WebPulse™ cloud com- munity of over 75 million users. -

Nethomura Deployment Platform and Networking Middleware Is Still Evolving
Networking Middleware and Online-Deployment Mechanisms for Java-based Games Chris Carter1, Dr Abdennour El Rhalibi1, Prof. Madjid Merabti1, Dr Marc Price2 (1) School of Computing & Mathematical Sciences, Liverpool John Moores University, Byrom Street, Liverpool, L3 3AF, UK [email protected]; [email protected]; [email protected] (2) BBC Research and Development. Kingswood Warren, Tadworth, Surrey, KT20 6NP, UK [email protected] Abstract. Currently, web-based online gaming applications are predominately utilising Adobe Flash or Java Applets as their core technologies. These games are often casual, two- dimensional games and do not utilise the specialist graphics hardware which has proliferated across modern PCs and Consoles. Multi-user online game play in these titles is often either non-existent or extremely limited. Computer games applications which grace the current generation of consoles and personal computers are designed to utilise the increasingly impressive hardware power at their disposal. However, these are commonly distributed using a physical medium or deployed through custom, proprietary networking mechanisms and rely upon platform-specific networking APIs to facilitate multi-user online game play. In order to unify the concepts of these disparate styles of gaming, this paper presents two interconnected systems which are implemented using Java Web Start and JXTA P2P technologies, providing a platform-independent framework capable of deploying hardware accelerated cross-platform, cross-browser online-enabled Java games, as part of the Homura Project. Keywords: Web Technologies, Distributed Systems, Java, Homura, NetHomura, Java Monkey Engine, jME, Java Web Start, Deployment, JXTA, Peer to Peer Networking, P2P Games. -

Advanced 3D Visualization for Simulation Using Game Technology
Proceedings of the 2011 Winter Simulation Conference S. Jain, R. R. Creasey, J. Himmelspach, K. P. White, and M. Fu, eds. ADVANCED 3D VISUALIZATION FOR SIMULATION USING GAME TECHNOLOGY Jonatan L. Bijl Csaba A. Boer TBA B.V. Karrepad 2a 2623 AP Delft, Netherlands ABSTRACT 3D visualization is becoming increasingly popular for discrete event simulation. However, the 3D visu- alization of many of the commercial off the shelf simulation packages is not up to date with the quickly developing area of computer graphics. In this paper we present an advanced 3D visualization tool, which uses game technology. The tool is especially fit for discrete event simulation, it is easily configurable, and it can be kept up to date with modern computer graphics techniques. The tool has been used in several container terminal simulation projects. From a survey under simulation experts and our experience with the visualization tool, we concluded that realism is important for some of the purposes of visualization, and the use of game technology can help to achieve this goal. 1 INTRODUCTION Simulation is the process of designing a model of a concrete system and conducting experiments with this model in order to understand the behavior of the concrete system and/or evaluate various strategies for the operation of the system (Shannon 1975). Although the simulation experiment can produce a large amount of data, the visualization of a simulated system provides a more complete understanding of its behavior. In the visualization, key elements of the system are represented on the screen by icons that dynamically change position, color and shape as the simulation evolves through time (Law and Kelton 2000). -

Keyword Rank Create Your Own Proxy Server 1 Alter a Pdf 1 How Do I Find
Keyword Rank create your own proxy server 1 alter a pdf 1 how do i find out the name of a song 1 how to get around blocked youtube videos 1 what version of windows 7 should i buy 1 setting up proxy 1 finding similar songs 1 app store returns 1 youtube music finder 1 google earth picture date 1 wireless mouse freezes 1 use second router as access point 1 set up a proxy 1 second router as access point 1 how to find newspaper articles from the past 1 google voice india number 1 connect two wireless routers together 1 setup a proxy 1 youtube blocked in your country 1 youtube blocked in country 1 youtube playlist on ipad 1 best pdf organizer 1 set up proxy 1 types of computer cords 1 set up second router 1 translate japanese pdf to english 1 computer plugs and connectors 1 how to find news articles from the past 1 compose html email in gmail 1 computer cable names 1 connecting two wireless routers together 1 how to look someone up by email 1 jpeg versus png 1 gmail mailmerge 1 find someone via email 1 remove nyt cookies 1 ipad youtube playlist 1 how to install proxy server 1 how to make a wireless router 1 how to search someone by email 1 edit current website 1 transfer from blogger to wordpress 1 best free dictation software 1 see passwords 1 100 most useful websites 1 how to find high resolution images 1 can you ping an email address 1 pdf file organizer 1 101 websites 1 how can i find out the name of a song 1 websites when your bored 1 how to find a newspaper article from the past 1 return apps 1 how to get old newspaper articles 1 track -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Revision: NOV.07.2020 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Policy Guide/Page 4 Symantec WSS Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology, including the WebPulse™ cloud community. With extensive web application controls and detailed reporting features, IT administrators can use the Web Security Service to create and enforce granular policies that are applied to all covered users, including fixed locations and roaming users. If the WSS is the body, then the policy engine is the brain. While the WSS by default provides malware protection (blocks four categories: Phishing, Proxy Avoidance, Spyware Effects/Privacy Concerns, and Spyware/Malware Sources), the additional policy rules and options you create dictate exactly what content your employees can and cannot access—from global allows/denials to individual users at specific times from specific locations. -
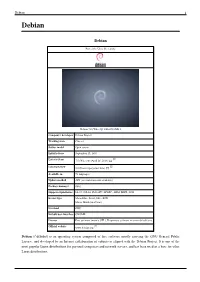
Debian 1 Debian
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life. -

Realidad Aumentada Como Estrategia Didáctica En Curso De Ciencias Naturales De Estudiantes De Quinto Grado De Primaria De La Institución Educativa Campo Valdés
REALIDAD AUMENTADA COMO ESTRATEGIA DIDÁCTICA EN CURSO DE CIENCIAS NATURALES DE ESTUDIANTES DE QUINTO GRADO DE PRIMARIA DE LA INSTITUCIÓN EDUCATIVA CAMPO VALDÉS OSCAR MAURICIO BUENAVENTURA BARON UNIVERSIDAD DE MEDELLIN ESPECIALIZACION EN INGENIERIA DE SOFTWARE COHORTE VI MEDELLIN 2014 REALIDAD AUMENTADA COMO ESTRATEGIA DIDÁCTICA EN CURSO DE CIENCIAS NATURALES DE ESTUDIANTES DE QUINTO GRADO DE PRIMARIA DE LA INSTITUCIÓN EDUCATIVA CAMPO VALDÉS OSCAR MAURICIO BUENAVENTURA BARON Requisito para optar al grado de Especialista en Ingeniería de Software Asesor EDWIN MAURICIO HINCAPIÉ MONTOYA UNIVERSIDAD DE MEDELLIN ESPECIALIZACION EN INGENIERIA DE SOFTWARE COHORTE VI MEDELLIN 2014 Nota de aceptación: ___________________________________ ___________________________________ ___________________________________ ___________________________________ ___________________________________ ___________________________________ ___________________________________ Firma presidente de jurado ___________________________________ Firma del jurado ___________________________________ Firma del jurado 3 Con todo mi cariño y mi amor para las personas que hicieron todo en la vida para que yo pudiera lograr mis sueños, por motivarme y darme la mano cuando sentía que el camino se terminaba, a ustedes por siempre mi corazón y mi gratitud. Mamá, Papá, Tía y Tocayo 4 TABLA DE CONTENIDO RESUMEN ...........................................................................................................................................9 INTRODUCCION .............................................................................................................................