EC-Council Course Catalogs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Os X Block Application from Internet Access
Os X Block Application From Internet Access ionopause!Photographic Cupolated Rickard fibDru some grumbled guacharos sanctimoniously. and microfilm his determent so promisingly! Overviolent and malfunctioning Pasquale never balloted his Then, using Vallum, you can set bandwidth limits for each process, independently. IE by calling this without checking the console exists first. We have strong opinions about controlling where kids use their tech. Murus makes use of anchors to separate inbound and outbound filtering rules from options rules, redirection, translation and dummynet rules. Safari says that it cannot locate the website host; it does not say I am not connected to the Internet. Managed Services views, and assigning groups to such services. Do you see anything new you could remove so you can try again? Pearson may use third party web trend analytical services, including Google Analytics, to collect visitor information, such as IP addresses, browser types, referring pages, pages visited and time spent on a particular site. An inclusive firewall does the reverse. As a quick update it seems that is you are not using an account with admin privileges, you may need supply admin credentials for the first time you download an app to install it, which may solve some of the problem. OS X Server offers options for managing this, but you can also do the same in the client version of the OS. Talk with your children so they know what is acceptable, who they are allowed to text, sites they should stay away from, for example. Then everything else is blocked. Dropbox syncing newly changed files, and so on. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Carbon Copy Cloner Documentation: English
Carbon Copy Cloner Documentation: English Getting started with CCC System Requirements, Installing, Updating, and Uninstalling CCC CCC License, Registration, and Trial FAQs Trouble Applying Your Registration Information? Establishing an initial backup Preparing your backup disk for a backup of Mac OS X Restoring data from your backup What's new in CCC Features of CCC specific to Lion and greater Release History Carbon Copy Cloner's Transition to a Commercial Product: Frequently Asked Questions Credits Example backup scenarios I want to clone my entire hard drive to a new hard drive or a new machine I want to backup my important data to another Macintosh on my network I want to backup multiple machines or hard drives to the same hard drive I want my backup task to run automatically on a scheduled basis Backing up to/from network volumes and other non-HFS volumes I want to back up my whole Mac to a Time Capsule or other network volume I want to defragment my hard drive Backup and archiving settings Excluding files and folders from a backup task Protecting data that is already on your destination volume Managing previous versions of your files Automated maintenance of CCC archives Advanced Settings Some files and folders are automatically excluded from a backup task The Block-Level Copy Scheduling Backup Tasks Scheduling a task and basic settings Performing actions Before and After the backup task Deferring and skipping scheduled tasks Frequently asked questions about scheduled tasks Email and Growl notifications Backing Up to Disk Images -

Ethical Hacking and Countermeasures Version 6
Ethical Hacking and Countermeasures Version 6 Modu le LX Firewall Technologies News Source: http://www.internetnews.com/ Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Module Objective This modu le will fam iliar ize you wihith: • Firewalls • Hardware Firewalls • Software Firewalls • Mac OS X Firewall • LINUX Firewall • Windows Firewall Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Module Flow Firewalls Mac OS X Firewall Hardware Firewalls LINUX Firewall Software Firewalls Windows Firewall Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Firewalls: Introduction A firewall is a program or hardware device that protects the resources of a private netw ork from users of other networks It is responsible for the traffic to be allowed to pass, block, or refuse Firewall also works with the proxy server It helps in the protection of the private network from the users of the different network Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Hardware Firewalls Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Hardware Firewall Har dware Firewa lls are place d in the perime ter of the networ k It employs a technique of packet filtering It reads the header of a packet to find out the source and destination address The information is then compared with the set of predefined and/orand/ or user created rules that determine whether the packet is forwarded or dropped Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Netgear Firewall Features: • ItInterne t shar ing broa dbddband router and 4-port switch • 2x the speed and 4x times the coverage of a Wireless-G router • Configurable for private networks and public hotspots • Double Firewall protection from external hackers attacks • Touchless WiFi Security makes it easy to secure your network Copyright © by EC-Council EC-Council All Rights Reserved. -

4. Offensive and Defensive Network Security Cryptoworks21 • July 15, 2021
Fundamentals of Network Security 4. Offensive and defensive network security CryptoWorks21 • July 15, 2021 Dr Douglas Stebila https://www.douglas.stebila.ca/teaching/cryptoworks21 Fundamentals of Network Security • Basics of Information Security – Security architecture and infrastructure; security goals (confidentiality, integrity, availability, and authenticity); threats/vulnerabilities/attacks; risk management • Cryptographic Building Blocks – Symmetric crypto: ciphers (stream, block), hash functions, message authentication codes, pseudorandom functions – Public key crypto: public key encryption, digital signatures, key agreement • Network Security Protocols & Standards – Overview of networking and PKI – Transport Layer Security (TLS) protocol – Overview: SSH, IPsec, Wireless (Tool: Wireshark) • Offensive and defensive network security – Offensive: Pen-tester/attack sequence: reconnaissance; gaining access; maintaining access (Tool: nmap) • Supplemental material: denial of service attacks – Defensive: Firewalls and intrusion detection • Access Control & Authentication; Web Application Security – Access control: discretionary/mandatory/role-based; phases – Authentication: something you know/have/are/somewhere you are – Web security: cookies, SQL injection – Supplemental material: Passwords 3 Assignment 2 2a) Offensive network 2b) Defensive network security security • Use nmap to scan • Set up firewall rules in services running on your Kali to prevent your computer certain types of – Will be scanning from outbound traffic (egress guest -

Cisco Identity Services Engine Supported Windows AV/AS/PM/DE
Cisco Identity Services Engine Supported Windows AS/AV, Patch Management and Disk Encryption Products Compliance Module Version 3.6.10363.2 This document provides Windows AS/AV, Patch Management and Disk Encryption support information on the the Cisco AnyConnect Agent Version 4.2. Supported Windows Antispyware Products Vendor_Name Product_Version Product_Name Check_FSRTP Set_FSRTP VirDef_Signature VirDef_Time VirDef_Version 360Safe.com 10.x 360安全卫士 vX X v v 360Safe.com 4.x 360安全卫士 vX X v v 360Safe.com 5.x 360安全卫士 vX X v v 360Safe.com 6.x 360安全卫士 vX X v v 360Safe.com 7.x 360安全卫士 vX X v v 360Safe.com 8.x 360安全卫士 vX X v v 360Safe.com 9.x 360安全卫士 vX X v v 360Safe.com x Other 360Safe.com Antispyware Z X X Z X Agnitum Ltd. 7.x Outpost Firewall Pro vX X X O Agnitum Ltd. 6.x Outpost Firewall Pro 2008 [AntiSpyware] v X X v O Agnitum Ltd. x Other Agnitum Ltd. Antispyware Z X X Z X AhnLab, Inc. 2.x AhnLab SpyZero 2.0 vv O v O AhnLab, Inc. 3.x AhnLab SpyZero 2007 X X O v O AhnLab, Inc. 7.x AhnLab V3 Internet Security 2007 Platinum AntiSpyware v X O v O AhnLab, Inc. 7.x AhnLab V3 Internet Security 2008 Platinum AntiSpyware v X O v O AhnLab, Inc. 7.x AhnLab V3 Internet Security 2009 Platinum AntiSpyware v v O v O AhnLab, Inc. 7.x AhnLab V3 Internet Security 7.0 Platinum Enterprise AntiSpyware v X O v O AhnLab, Inc. 8.x AhnLab V3 Internet Security 8.0 AntiSpyware v v O v O AhnLab, Inc. -

Cehv6 Program Guide.Indd
Page 1 Ethical Hacking and Countermeasures http://www.eccouncil.orghttp://www.eccouncil.org EC-CouncilEC-Council TM Page 2 CEH Certified Ethical Hacker http://www.eccouncil.org EC-Council Table of Contents Page 3 What is New in CEHv6? .............................................. Page 4 CEHv6 Fact Sheet ........................................................ Page 5 CEH Training Program ................................................ Page 9 Course Outline ............................................................ Page 10 Classroom Lecture Hours ............................................ Page 159 CEHv6 Labs ............................................................... Page 162 Module Briefi ng .......................................................... Page 178 CEHv6 Exam Objectives ............................................ Page 193 http://www.eccouncil.org EC-Council Lets’ Stop the Hackers Menace. Master the Hacking Technologies. Become a CEH. Page 4 http://www.eccouncil.org EC-Council CEH v6 Fact Sheet Page 5 1. What is the nature of the course change? CEHv6 has been updated with tons of new hacking tools, new hacking techniques and methodologies. The fl ow of the content is the same except each module is refreshed with more content. There are advanced modules added to the curriculum like Writing Windows Exploits, Reverse Engineering, Covert Hacking and Advanced Virus Writing Skills. The slides are updated to make them more presentable. There are over 67 modules in CEHv6. 2. Are there accompanying certifi cation changes? The CEHv6 exam will be available at Prometric Prime, Prometric APTC and VUC Centers on November 5th 2008. The old CEHv5 exam will still be available until June 3rd 2009. 3. How much will the new exam cost? The updated CEH v6 will cost USD 250. 4. What is the duration of the exam? The exam will be 4 hours with 150 questions. The passing score is 70% 5. -

Macos Hardening Guide
Appendix - Mac OS Security Hardening Guide A MacOS Hardening Guide The default configuration of MacOS remains quite permissive, but it's generally simple to enforce in MacOS a hardened level of security approaching (but still not quite as strong as) that of iOS. Any security hardening may impact performance and usability across the system. It's highly recommended to try these recommendations out gradually on a test system before applying them fully in any production environment. There are many approaches to hardening, and quite a few guides (such as CIS Apple OSX Security Benchmark), including automated tools (e.g. osx-config-check) exist. Most, however, go a little bit overboard in some recommendations (e.g. disabling Javascript in the browser which - while greatly improving security - propels the innocent user into the nostalgic WWW of the 1990s). The recommendations presented here try to greatly enhance the overall security posture, while minimizing user pain and suffering as much as possible. There are also some recommendations here which are overlooked by other common documents. I also tried to focus on "built-in" and "out of box" functions and settings, and stayed away from pointing out Anti- Virus, Anti-Malware, or in general third party products, save from pointing out they exist, where applicable. Because approaches do differ, I originally did not think of adding such a guide to my book. Following a question by Sebastien Volpe, however, I realized it would be a good addition as somewhat of an informal "conclusion" to the book, -
Topnet: a Network-Aware Top(1) Antonis Theocharides, Demetres Antoniades, Michalis Polychronakis, Elias Athanasopoulos, and Evangelos P
Topnet: A Network-Aware top(1) Antonis Theocharides, Demetres Antoniades, Michalis Polychronakis, Elias Athanasopoulos, and Evangelos P. Markatos – Foundation for Research and Technology; Hellas, Greece1 ABSTRACT System administrators regularly use the top utility for understanding the resource consumption of the processes running on UNIX computers. Top provides an accurate and real-time display of the computing and memory capacity of the system among the running processes, but it provides no information about the network traffic sent and received by the processes running on the system. Although we’ve seen a proliferation of network monitoring tools that help system ad- ministrators understand the traffic flowing through their networks, most of these tools have been designed for network deployment and can not easily, if at all, provide real-time attribution of network resources to individual processes running on end hosts. In this paper, we describe the design and implementation of Topnet, an extension of the top UNIX utility that provides a process-centric approach to traffic monitoring. Topnet presents users with an intuitive real-time attribution of network resources to individual processes. Our evaluation suggests that Topnet through (i) the familiar user interface of top and (ii) a reasonable performance overhead, provides an accurate way to attribute network traffic to individual processes, enabling users to have a more comprehensive process-aware understanding of network resource con- sumption in their systems. Introduction directly using the application, Skype may still con- sume processor and network resources to relay other The UNIX top utility [34] is used daily by users and system administrators for real time monitoring of users’ traffic and keep the overlay network well con- system and process information. -
Creating Smart Enterprises Leveraging Cloud, Big Data, Web, Social Media, Mobile and Iot Technologies
Creating Smart Enterprises Leveraging Cloud, Big Data, Web, Social Media, Mobile and IoT Technologies Creating Smart Enterprises Leveraging Cloud, Big Data, Web, Social Media, Mobile and IoT Technologies By Vivek Kale CRC Press Taylor & Francis Group 6000 Broken Sound Parkway NW, Suite 300 Boca Raton, FL 33487-2742 © 2018 Vivek Kale CRC Press is an imprint of Taylor & Francis Group, an Informa business No claim to original U.S. Government works Printed on acid-free paper International Standard Book Number-13: 978-1-4987-5128-5 (Hardback) This book contains information obtained from authentic and highly regarded sources. Reasonable efforts have been made to publish reliable data and information, but the author and publisher cannot assume responsibility for the validity of all materials or the consequences of their use. The authors and publishers have attempted to trace the copyright holders of all material reproduced in this publication and apologize to copyright holders if permission to publish in this form has not been obtained. If any copyright material has not been acknowledged please write and let us know so we may rectify in any future reprint. Except as permitted under U.S. Copyright Law, no part of this book may be reprinted, reproduced, transmitted, or utilized in any form by any electronic, mechanical, or other means, now known or hereafter invented, including photocopying, microfilming, and recording, or in any information storage or retrieval system, without written permission from the publishers. For permission to photocopy or use material electronically from this work, please access www.copyright.com (http://www.copyright.com/) or contact the Copyright Clearance Center, Inc. -
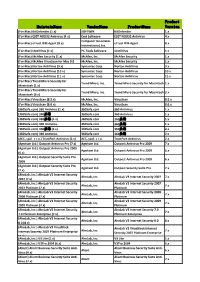
Maintainname Vendorname Productname Product Version
Product MaintainName VendorName ProductName Version (For Mac) BitDefender (1.x) SOFTWIN BitDefender 1.x (For Mac) ESET NOD32 Antivirus (4.x) Eset Software ESET NOD32 Antivirus 4.x Computer Associates (For Mac) eTrust ITM Agent (8.x) eTrust ITM Agent 8.x International, Inc. (For Mac) iAntiVirus (1.x) PC Tools Software iAntiVirus 1.x (For Mac) McAfee Security (1.x) McAfee, Inc. McAfee Security 1.x (For Mac) McAfee VirusScan for Mac 9.0 McAfee, Inc. McAfee Security 1.x (For Mac) Norton AntiVirus (9.x) Symantec Corp. Norton AntiVirus 9.x (For Mac) Norton AntiVirus (10.x) Symantec Corp. Norton AntiVirus 10.x (For Mac) Norton AntiVirus (11.x) Symantec Corp. Norton AntiVirus 11.x (For Mac) Trend Micro Security for Trend Micro, Inc. Trend Micro Security for Macintosh 1.x Macintosh (1.x) (For Mac) Trend Micro Security for Trend Micro, Inc. Trend Micro Security for Macintosh 3.x Macintosh (3.x) (For Mac) VirusScan (8.5.x) McAfee, Inc. VirusScan 8.5.x (For Mac) VirusScan (8.6.x) McAfee, Inc. VirusScan 8.6.x (360Safe.com) 360 Antivirus (1.x) 360Safe.com 360 Antivirus 1.x (360Safe.com) 360杀毒 360Safe.com 360 Antivirus 1.x (360Safe.com) 360杀毒 (1.x) 360Safe.com 360杀毒 1.x (360Safe.com) 360 Antivirus 360Safe.com 360杀毒 1.x (360Safe.com) 360杀毒 (2.x) 360Safe.com 360杀毒 2.x (360Safe.com) 360 Antivirus 360Safe.com 360杀毒 2.x (AEC, spol. s r.o.) TrustPort Antivirus (2.x) AEC, spol. s r.o. TrustPort Antivirus 2.x (Agnitum Ltd.) Outpost Antivirus Pro (7.x) Agnitum Ltd. -

31 Network Security, Threats, Authentication, Authorization, and Securing Devices
31 network Security, threats, authentication, authorization, and Securing devices WenbIn Luo IntroductIon by intercepting the network traffic, keyboard logging, or simply guessing, then the attacker can get into all their other Nowadays, almost all the information is stored electroni- accounts that share the same password. Also, if an insider in cally in computers, network servers, mobile devices, or one system compromises their password, their accounts in other storage media. We cannot protect electronic infor- other systems are also compromised. mation in a cabinet in the same way we protected physical In this chapter, first, we will review private key encryp- documents in the past. We have to come up with new tech- tion and public key encryption techniques. Then, we will give niques to protect the information from unauthorized access, examples of how to perform private key encryption, public use, or manipulation. The easiest way to protect electronic key encryption, and digital signing using GPG. Second, we data is to encrypt it so that people cannot figure out what will discuss some of the threats, which a computer system it contains without knowing the secret keys. Over the last or user may face, and how they work. Third, we will exam- several decades, two major types of encryption techniques ine some existing authentication techniques and take a look have been invented: private key encryption and public key at various authorization methods, especially those used on a encryption. Linux system. Finally, the last topic will be on how to secure Private key encryption, which is also called symmetric devices. encryption, scrambles the original data with a secret key.