Festi Botnet Analysis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trojan Vs Rat Vs Rootkit Mayuri More1, Rajeshwari Gundla2, Siddharth Nanda3 1U.G
IJRECE VOL. 7 ISSUE 2 (APRIL- JUNE 2019) ISSN: 2393-9028 (PRINT) | ISSN: 2348-2281 (ONLINE) Trojan Vs Rat Vs Rootkit Mayuri More1, Rajeshwari Gundla2, Siddharth Nanda3 1U.G. Student, 2 Senior Faculty, 3Senior Faculty SOE, ADYPU, Lohegaon, Pune, Maharashtra, India1 IT, iNurture, Bengaluru, India2,3 Abstract - Malicious Software is Malware is a dangerous of RATs completely and prevent confidential data being software which harms computer systems. With the increase leaked. So Dan Jiang and Kazumasa Omote researchers in technology in today’s days, malwares are also increasing. have proposed an approach to detect RAT in the early stage This paper is based on Malware. We have discussed [10]. TROJAN, RAT, ROOTKIT in detail. Further, we have discussed the adverse effects of malware on the system as III. CLASSIFICATION well as society. Then we have listed some trusted tools to Rootkit vs Trojan vs Rat detect and remove malware. Rootkit - A rootkit is a malicious software that permits a legitimate user to have confidential access to a system and Keywords - Malware, Trojan, RAT, Rootkit, System, privileged areas of its software. A rootkit possibly contains Computer, Anti-malware a large number of malicious means for example banking credential stealers, keyloggers, antivirus disablers, password I. INTRODUCTION stealers and bots for DDoS attacks. This software stays Nowadays, this world is full of technology, but with the hidden in the computer and allocates the remote access of advantages of technology comes its disadvantages like the computer to the attacker[2]. hacking, corrupting the systems, stealing of data etc. These Types of Rootkit: malpractices are possible because of malware and viruses 1. -

Adware-Searchsuite
McAfee Labs Threat Advisory Adware-SearchSuite June 22, 2018 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains behavioral information, characteristics and symptoms that may be used to mitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs. To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware and Threat Reports” at the following URL: https://www.mcafee.com/enterprise/en-us/sns/preferences/sns-form.html Summary Detailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation Vectors Mitigation Characteristics and Symptoms Restart Mechanism McAfee Foundstone Services The Threat Intelligence Library contains the date that the above signatures were most recently updated. Please review the above mentioned Threat Library for the most up to date coverage information. Infection and Propagation Vectors Adware-SearchSuite is a "potentially unwanted program" (PUP). PUPs are any piece of software that a reasonably security- or privacy-minded computer user may want to be informed of and, in some cases, remove. PUPs are often made by a legitimate corporate entity for some beneficial purpose, but they alter the security state of the computer on which they are installed, or the privacy posture of the user of the system, such that most users will want to be aware of them. Mitigation Mitigating the threat at multiple levels like file, registry and URL could be achieved at various layers of McAfee products. Browse the product guidelines available here (click Knowledge Center, and select Product Documentation from the Support Content list) to mitigate the threats based on the behavior described in the Characteristics and symptoms section. -

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Crimeware on the Net
Crimeware on the Net The “Behind the scenes” of the new web economy Iftach Ian Amit Director, Security Research – Finjan BlackHat Europe, Amsterdam 2008 Who Am I ? (iamit) • Iftach Ian Amit – In Hebrew it makes more sense… • Director Security Research @ Finjan • Various security consulting/integration gigs in the past – R&D – IT • A helping hand when needed… (IAF) 2 BlackHat Europe – Amsterdam 2008 Today’s Agenda • Terminology • Past vs. Present – 10,000 feet view • Business Impact • Key Characteristics – what does it look like? – Anti-Forensics techniques – Propagation methods • What is the motive (what are they looking for)? • Tying it all up – what does it look like when successful (video). • Anything in it for us to learn from? – Looking forward on extrusion testing methodologies 3 BlackHat Europe – Amsterdam 2008 Some Terminology • Crimeware – what we refer to most malware these days is actually crimeware – malware with specific goals for making $$$ for the attackers. • Attackers – not to be confused with malicious code writers, security researchers, hackers, crackers, etc… These guys are the Gordon Gecko‟s of the web security field. The buy low, and capitalize on the investment. • Smart (often mislead) guys write the crimeware and get paid to do so. 4 BlackHat Europe – Amsterdam 2008 How Do Cybercriminals Steal Business Data? Criminals’ activity in the cyberspace Federal Prosecutor: “Cybercrime Is Funding Organized Crime” 5 BlackHat Europe – Amsterdam 2008 The Business Impact Of Crimeware Criminals target sensitive business data -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

SMM Rootkits
SMM Rootkits: A New Breed of OS Independent Malware Shawn Embleton Sherri Sparks Cliff Zou University of Central Florida University of Central Florida University of Central Florida [email protected] [email protected] [email protected] ABSTRACT 1. INTRODUCTION The emergence of hardware virtualization technology has led to A rootkit consists of a set of programs that work to subvert the development of OS independent malware such as the Virtual control of an Operating System from its legitimate users [16]. If Machine based rootkits (VMBRs). In this paper, we draw one were asked to classify viruses and worms by a single defining attention to a different but related threat that exists on many characteristic, the first word to come to mind would probably be commodity systems in operation today: The System Management replication. In contrast, the single defining characteristic of a Mode based rootkit (SMBR). System Management Mode (SMM) rootkit is stealth. Viruses reproduce, but rootkits hide. They hide is a relatively obscure mode on Intel processors used for low-level by compromising the communication conduit between an hardware control. It has its own private memory space and Operating System and its users. Secondary to hiding themselves, execution environment which is generally invisible to code rootkits are generally capable of gathering and manipulating running outside (e.g., the Operating System). Furthermore, SMM information on the target machine. They may, for example, log a code is completely non-preemptible, lacks any concept of victim user’s keystrokes to obtain passwords or manipulate the privilege level, and is immune to memory protection mechanisms. -

Cross Site Scripting Attacks Xss Exploits and Defense.Pdf
436_XSS_FM.qxd 4/20/07 1:18 PM Page ii 436_XSS_FM.qxd 4/20/07 1:18 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and deliv- ering those books in media and formats that fit the demands of our customers. We are also committed to extending the utility of the book you purchase via additional mate- rials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value- added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of expertise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in downloadable Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -
Design Decisions for a Structured Front End to LATEX Documents
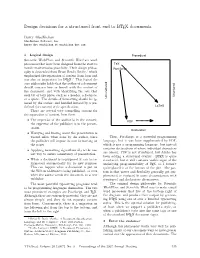
Design decisions for a structured front end to LATEX documents Barry MacKichan MacKichan Software, Inc. barry dot mackichan at mackichan dot com 1 Logical design Procedural Scientific WorkPlace and Scientific Word are word processors that have been designed from the start to TeX handle mathematics gracefully. Their design philos- PostScript ophy is descended from Brian Reid’s Scribe,1 which emphasized the separation of content from form and 2 was also an inspiration for LATEX. This logical de- sign philosophy holds that the author of a document should concern him- or herself with the content of the document, and with identifying the role that each bit of text plays, such as a header, a footnote, Structured or a quote. The details of formatting should be ig- Unstructured nored by the author, and handled instead by a pre- defined (or custom) style specification. LaTeX There are several very compelling reasons for the separation of content from form. • The expertise of the author is in the content; PDF the expertise of the publisher is in the presen- tation. Declarative • Worrying and fussing about the presentation is wasted effort when done by the author, since Thus, PostScript is a powerful programming the publisher will impose its own formatting on language, but it was later supplemented by PDF, the paper. which is not a programming language, but instead contains declarations of where individual characters • Applying formatting algorithmically is the eas- are placed. PDF is not structured, but Adobe has iest way to assure consistency of presentation. been adding a structural overlay. LATEX is quite • When a document is re-purposed it can be re- structured, but it still contains visible signs of the formatted automatically for its new purpose. -

Trojans and Malware on the Internet an Update
Attitude Adjustment: Trojans and Malware on the Internet An Update Sarah Gordon and David Chess IBM Thomas J. Watson Research Center Yorktown Heights, NY Abstract This paper continues our examination of Trojan horses on the Internet; their prevalence, technical structure and impact. It explores the type and scope of threats encountered on the Internet - throughout history until today. It examines user attitudes and considers ways in which those attitudes can actively affect your organization’s vulnerability to Trojanizations of various types. It discusses the status of hostile active content on the Internet, including threats from Java and ActiveX, and re-examines the impact of these types of threats to Internet users in the real world. Observations related to the role of the antivirus industry in solving the problem are considered. Throughout the paper, technical and policy based strategies for minimizing the risk of damage from various types of Trojan horses on the Internet are presented This paper represents an update and summary of our research from Where There's Smoke There's Mirrors: The Truth About Trojan Horses on the Internet, presented at the Eighth International Virus Bulletin Conference in Munich Germany, October 1998, and Attitude Adjustment: Trojans and Malware on the Internet, presented at the European Institute for Computer Antivirus Research in Aalborg, Denmark, March 1999. Significant portions of those works are included here in original form. Descriptors: fidonet, internet, password stealing trojan, trojanized system, trojanized application, user behavior, java, activex, security policy, trojan horse, computer virus Attitude Adjustment: Trojans and Malware on the Internet Trojans On the Internet… Ever since the city of Troy was sacked by way of the apparently innocuous but ultimately deadly Trojan horse, the term has been used to talk about something that appears to be beneficial, but which hides an attack within. -

Rootkits, Part 1 of 3: the Growing Threat
White Paper | April 2006 Rootkits, Part 1 of 3: The Growing Threat www.mcafee.com White Paper | 2006 Page Table of Contents Key Findings 3 Abstract 3 A Brief History of Stealth Malware (a.k.a. Rootkits) 3 Rootkits, Malware, and Controversy 4 Rootkit Technology Trends 5 Works Cited 7 www.mcafee.com White Paper | 2006 Page Key Findings netstat, ls, and passwd. Because these same tools could be used by an attacker to hide any trace of intrusion, the term 1. In just three short years, the use of stealth techniques in rootkit became associated with stealth. When these same malicious software (malware) has grown by more than strategies were applied to the Windows environment, the 600 percent. rootkit name transferred with them. Today, rootkit is a term . From 000 to 005, rootkit complexity grew by more commonly used to describe malware—such as Trojans, than 400 percent, and year-over-year, Q1 2005 to 2006, worms, and viruses—that actively conceals its existence complexity has grown by more than 900 percent. and actions from users and other system processes. The share of Linux-based techniques has gone from The practice of hiding malware from the prying eyes of a high of roughly 71 percent of all malware stealth users and security products dates back to the very first PC 1 components in 001 to a negligible number in virus, Brain, which was released in 1986. Brain escaped 005, while the number of Windows®-based stealth detection by intercepting PC boot-sector interrogations and components has increased by ,00 percent in the same redirecting the read operations to elsewhere on the disk. -

An Adaptive Multi-Layer Botnet Detection Technique Using Machine Learning Classifiers
applied sciences Article An Adaptive Multi-Layer Botnet Detection Technique Using Machine Learning Classifiers Riaz Ullah Khan 1,* , Xiaosong Zhang 1, Rajesh Kumar 1 , Abubakar Sharif 1, Noorbakhsh Amiri Golilarz 1 and Mamoun Alazab 2 1 Center of Cyber Security, School of Computer Science & Engineering, University of Electronic Science and Technology of China, Chengdu 611731, China; [email protected] (X.Z.); [email protected] (R.K.); [email protected] (A.S.); [email protected] (N.A.G.) 2 College of Engineering, IT and Environment, Charles Darwin University, Casuarina 0810, Australia; [email protected] * Correspondence: [email protected]; Tel.: +86-155-2076-3595 Received: 19 March 2019; Accepted: 24 April 2019; Published: 11 June 2019 Abstract: In recent years, the botnets have been the most common threats to network security since it exploits multiple malicious codes like a worm, Trojans, Rootkit, etc. The botnets have been used to carry phishing links, to perform attacks and provide malicious services on the internet. It is challenging to identify Peer-to-peer (P2P) botnets as compared to Internet Relay Chat (IRC), Hypertext Transfer Protocol (HTTP) and other types of botnets because P2P traffic has typical features of the centralization and distribution. To resolve the issues of P2P botnet identification, we propose an effective multi-layer traffic classification method by applying machine learning classifiers on features of network traffic. Our work presents a framework based on decision trees which effectively detects P2P botnets. A decision tree algorithm is applied for feature selection to extract the most relevant features and ignore the irrelevant features. -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14.