SSL/TLS Authenticity of Public Keys
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Using Frankencerts for Automated Adversarial Testing of Certificate
Using Frankencerts for Automated Adversarial Testing of Certificate Validation in SSL/TLS Implementations Chad Brubaker ∗ y Suman Janay Baishakhi Rayz Sarfraz Khurshidy Vitaly Shmatikovy ∗Google yThe University of Texas at Austin zUniversity of California, Davis Abstract—Modern network security rests on the Secure Sock- many open-source implementations of SSL/TLS are available ets Layer (SSL) and Transport Layer Security (TLS) protocols. for developers who need to incorporate SSL/TLS into their Distributed systems, mobile and desktop applications, embedded software: OpenSSL, NSS, GnuTLS, CyaSSL, PolarSSL, Ma- devices, and all of secure Web rely on SSL/TLS for protection trixSSL, cryptlib, and several others. Several Web browsers against network attacks. This protection critically depends on include their own, proprietary implementations. whether SSL/TLS clients correctly validate X.509 certificates presented by servers during the SSL/TLS handshake protocol. In this paper, we focus on server authentication, which We design, implement, and apply the first methodology for is the only protection against man-in-the-middle and other large-scale testing of certificate validation logic in SSL/TLS server impersonation attacks, and thus essential for HTTPS implementations. Our first ingredient is “frankencerts,” synthetic and virtually any other application of SSL/TLS. Server authen- certificates that are randomly mutated from parts of real cer- tication in SSL/TLS depends entirely on a single step in the tificates and thus include unusual combinations of extensions handshake protocol. As part of its “Server Hello” message, and constraints. Our second ingredient is differential testing: if the server presents an X.509 certificate with its public key. -

A Focus on S/MIME
The University of Saskatchewan Department of Computer Science Technical Report #2011-03 Cryptographic Security for Emails: A Focus on S/MIME Minhaz Fahim Zibran Department of Computer Science University of Saskatchewan Email: [email protected] Abstract In this paper I present a study on \S/MIME", which has become the industry standard for secure email exchange. Based on existing literature review, the study examines S/MIME in depth with specific emphasis on its architecture, strengths, and deficiencies. The study also identifies usability issues related to S/MIME enabled email clients, which indicate scopes for further improvements in those implementations. Obstacles in the adoption of S/MIME are also identified indicating what is required for its successful adoption in the community. In presenting the study, the paper contributes in two ways: (a) for any newcomer in the field of cryptography this paper will be a useful resource to quickly learn about S/MIME in a fair level of detail, (b) the indication about limitations of S/MIME and its implementations reveals an avenue for further research in the area of email security, which may result in improvement of S/MIME itself, or its implementations in the email clients. Keywords: Email Security, S/MIME, MIME, PGP, PKI, Certificate, Email Authentication, Email Encryption, Key Management 1 Introduction Email has been a very common medium of communication these days. It somewhat re- places the traditional surface mail and many of the traditional ways of communication [32]. Today people send and read emails from their personal computers, business workstation, PDAs and even cell phones. -

Installing Fake Root Keys in a PC
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Royal Holloway - Pure Installing Fake Root Keys in a PC Adil Alsaid and Chris J. Mitchell Information Security Group Royal Holloway, University of London Egham, Surrey TW20 0EX fA.Alsaid, [email protected] Abstract. If a malicious party can insert a self-issued CA public key into the list of root public keys stored in a PC, then this party could potentially do considerable harm to that PC. In this paper, we present a way to achieve such an attack for the Internet Explorer web browser root key store, which avoids attracting the user's attention. A realisation of this attack is also described. Finally, countermeasures that can be deployed to prevent such an attack are outlined. 1 Introduction As is widely known [10], most web browsers (e.g. Microsoft Internet Explorer or Netscape) have a repository of root public keys designed for use in verify- ing digitally signed public key certi¯cates. These public keys are bundled with distributions of the web browser, and are used to verify certi¯cates for applet providers [13]. Speci¯cally, web-sites may download applets to a user PC without the PC user knowing it. Depending on the security settings selected by the PC user, these applets may be executed with or without further checks. Typically, the browser will only execute the applet if the following conditions are satis¯ed. 1. The applet must be digitally signed, and the signature must verify correctly. 2. -

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

Towards a Hybrid Public Key Infrastructure (PKI): a Review
Towards a Hybrid Public Key Infrastructure (PKI): A Review Priyadarshi Singh, Abdul Basit, N Chaitanya Kumar, and V. Ch. Venkaiah School of Computer and Information Sciences, University of Hyderabad, Hyderabad-500046, India Abstract. Traditional Certificate- based public key infrastructure (PKI) suffers from the problem of certificate overhead like its storage, verification, revocation etc. To overcome these problems, idea of certificate less identity-based public key cryptography (ID-PKC) was proposed by Shamir. This is suitable for closed trusted group only. Also, this concept has some inherent problems like key escrow problem, secure key channel problem, identity management overhead etc. Later on, there had been several works which tried to combine both the cryptographic techniques such that the resulting hybrid PKI framework is built upon the best features of both the cryptographic techniques. It had been shown that this approach solves many problems associated with an individual cryptosystem. In this paper, we have reviewed and compared such hybrid schemes which tried to combine both the certificate based PKC and ID-based PKC. Also, the summary of the comparison, based on various features, is presented in a table. Keywords: Certificate-based PKI; Identity-based public key cryptography (ID-PKC); Hybrid PKI 1 INTRODUCTION Public key infrastructure (PKI) and public key cryptography (PKC) [12] plays a vital role with four major components of digital security: authentication, integrity, confidentiality and non-repudiation. Infact, PKI enables the use of PKC through key management. The ”efficient and secure management of the key pairs during their whole life cycle" is the purpose of PKI, which involves key generation, key distribution, key renewal, key revocation etc [11]. -

Security Target Document
Security Target Document Passport Certificate Server Ver. 4.1.1 Prepared for: Common Criteria EAL2 (augmented) 30 April 2002 2225 Sheppard Ave, Suite 1700 Toronto, Ontario, Canada M2J 5C2 TEL: 416-756-2324 FAX: 416-756-7346 [email protected] www.dvnet.com Passport Certificate Server V.4.1.1 Security Target 30 April 2002 Common Criteria EAL 2 (augmented) Version 1.00 TABLE OF CONTENTS 1 Introduction ............................................................................................................................................ 1 1.1 Security Target Identification......................................................................................................... 1 1.2 Security Target Overview............................................................................................................... 1 1.3 Common Criteria Conformance .....................................................................................................1 2 TOE Description..................................................................................................................................... 2 2.1 Product Deployment....................................................................................................................... 2 2.2 Product Functions........................................................................................................................... 2 2.3 Product Description ........................................................................................................................ 3 2.3.1 Platform -
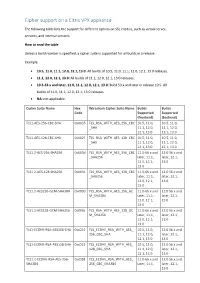
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Analysis of SSL Certificate Reissues and Revocations in the Wake
Analysis of SSL Certificate Reissues and Revocations in the Wake of Heartbleed Liang Zhang David Choffnes Dave Levin Tudor Dumitra¸s Northeastern University Northeastern University University of Maryland University of Maryland [email protected] [email protected] [email protected] [email protected] Alan Mislove Aaron Schulman Christo Wilson Northeastern University Stanford University Northeastern University [email protected] [email protected] [email protected] ABSTRACT Categories and Subject Descriptors Central to the secure operation of a public key infrastruc- C.2.2 [Computer-Communication Networks]: Net- ture (PKI) is the ability to revoke certificates. While much work Protocols; C.2.3 [Computer-Communication Net- of users' security rests on this process taking place quickly, works]: Network Operations; E.3 [Data Encryption]: in practice, revocation typically requires a human to decide Public Key Cryptosystems, Standards to reissue a new certificate and revoke the old one. Thus, having a proper understanding of how often systems admin- istrators reissue and revoke certificates is crucial to under- Keywords standing the integrity of a PKI. Unfortunately, this is typi- Heartbleed; SSL; TLS; HTTPS; X.509; Certificates; Reissue; cally difficult to measure: while it is relatively easy to deter- Revocation; Extended validation mine when a certificate is revoked, it is difficult to determine whether and when an administrator should have revoked. In this paper, we use a recent widespread security vul- 1. INTRODUCTION nerability as a natural experiment. Publicly announced in Secure Sockets Layer (SSL) and Transport Layer Secu- April 2014, the Heartbleed OpenSSL bug, potentially (and rity (TLS)1 are the de-facto standards for securing Internet undetectably) revealed servers' private keys. -

A Practical Evaluation of a High-Security Energy-Efficient
sensors Article A Practical Evaluation of a High-Security Energy-Efficient Gateway for IoT Fog Computing Applications Manuel Suárez-Albela * , Tiago M. Fernández-Caramés , Paula Fraga-Lamas and Luis Castedo Department Computer Engineering, Faculty of Computer Science, Universidade da Coruña, 15071 A Coruña, Spain; [email protected] (T.M.F.-C.); [email protected] (P.F.-L.); [email protected] (L.C.) * Correspondence: [email protected]; Tel.: +34-981-167-000 (ext. 6051) Received: 28 July 2017; Accepted: 19 August 2017; Published: 29 August 2017 Abstract: Fog computing extends cloud computing to the edge of a network enabling new Internet of Things (IoT) applications and services, which may involve critical data that require privacy and security. In an IoT fog computing system, three elements can be distinguished: IoT nodes that collect data, the cloud, and interconnected IoT gateways that exchange messages with the IoT nodes and with the cloud. This article focuses on securing IoT gateways, which are assumed to be constrained in terms of computational resources, but that are able to offload some processing from the cloud and to reduce the latency in the responses to the IoT nodes. However, it is usually taken for granted that IoT gateways have direct access to the electrical grid, which is not always the case: in mission-critical applications like natural disaster relief or environmental monitoring, it is common to deploy IoT nodes and gateways in large areas where electricity comes from solar or wind energy that charge the batteries that power every device. In this article, how to secure IoT gateway communications while minimizing power consumption is analyzed. -

Analysis of SSL Certificate Reissues And
Analysis of SSL Certificate Reissues and Revocations in the Wake of Heartbleed Liang Zhang David Choffnes Dave Levin Tudor Dumitra¸s Northeastern University Northeastern University University of Maryland University of Maryland [email protected] [email protected] [email protected] [email protected] Alan Mislove Aaron Schulman Christo Wilson Northeastern University Stanford University Northeastern University [email protected] [email protected] [email protected] ABSTRACT Categories and Subject Descriptors Central to the secure operation of a public key infrastruc- C.2.2 [Computer-Communication Networks]: Net- ture (PKI) is the ability to revoke certificates. While much work Protocols; C.2.3 [Computer-Communication Net- of users' security rests on this process taking place quickly, works]: Network Operations; E.3 [Data Encryption]: in practice, revocation typically requires a human to decide Public Key Cryptosystems, Standards to reissue a new certificate and revoke the old one. Thus, having a proper understanding of how often systems admin- istrators reissue and revoke certificates is crucial to under- Keywords standing the integrity of a PKI. Unfortunately, this is typi- Heartbleed; SSL; TLS; HTTPS; X.509; Certificates; Reissue; cally difficult to measure: while it is relatively easy to deter- Revocation; Extended validation mine when a certificate is revoked, it is difficult to determine whether and when an administrator should have revoked. In this paper, we use a recent widespread security vul- 1. INTRODUCTION nerability as a natural experiment. Publicly announced in Secure Sockets Layer (SSL) and Transport Layer Secu- April 2014, the Heartbleed OpenSSL bug, potentially (and rity (TLS)1 are the de-facto standards for securing Internet undetectably) revealed servers' private keys. -

Security Policies for the Federal Public Key Infrastructure
Security Policies for the Federal Public Key Infrastructure Noel A. Nazario Security Technology Group National Institute of Standards and Technology Abstract This document discusses provisions for the handling of security policies in the proposed Federal Public Key Infrastructure (PKI). Federal PKI policies deal with the generation, deactivation, and dissemination of public key certificates, the integrity of the infrastructure, maintenance of records, identification of certificate holders, and the establishment of trust relationships between Certification Authorities (CAs). The verification of a digital signature is not sufficient indication of the trustworthiness of an electronic message or data file. The verifier needs to factor the trustworthiness of the CAs involved in the certification of the sender. To accomplish this, the verifier needs to examine the certificate policy for those CAs. The Federal PKI Technical Security Policy establishes guidelines for the operation of Federal CAs and the identification of the parties requesting certification. It also defines Policy Approving Authorities (PAA) responsible for assessing the policies and operational practices of all Federal CAs within a domain and assigning them corresponding Federal Assurance Levels. These assurance levels may be used in lieu of a certificate policy when making an on-line determination of the trustworthiness of a certificate. Key words Certificate policy, Federal Assurance Levels, PAA, PKI, Policy Approving Authority, public key infrastructure, security policy. SECURITY POLICIES FOR THE FEDERAL PUBLIC KEY INFRASTRUCTURE Noel A. Nazario NIST North, Room 426 820 West Diamond Avenue Gaithersburg, MD 20899 [email protected] Introduction and Background This paper discusses provisions for the handling of security policies in the proposed Federal Public Key Infrastructure (PKI). -

Certificate Transparency Using Blockchain
Certicate Transparency Using Blockchain D S V Madala1, Mahabir Prasad Jhanwar1, and Anupam Chattopadhyay2 1Department of Computer Science. Ashoka University, India 2School of Computer Science and Engineering. NTU, Singapore Abstract The security of web communication via the SSL/TLS protocols relies on safe distribu- tions of public keys associated with web domains in the form of X:509 certicates. Certicate authorities (CAs) are trusted third parties that issue these certicates. However, the CA ecosystem is fragile and prone to compromises. Starting with Google's Certicate Trans- parency project, a number of research works have recently looked at adding transparency for better CA accountability, eectively through public logs of all certicates issued by certica- tion authorities, to augment the current X:509 certicate validation process into SSL/TLS. In this paper, leveraging recent progress in blockchain technology, we propose a novel system, called CTB, that makes it impossible for a CA to issue a certicate for a domain without obtaining consent from the domain owner. We further make progress to equip CTB with certicate revocation mechanism. We implement CTB using IBM's Hyperledger Fabric blockchain platform. CTB's smart contract, written in Go, is provided for complete reference. 1 Introduction The overwhelming adoption of SSL/TLS (Secure Socket Layer/Transport Layer Security Proto- cols) [4, 33] for most HTTP trac has transformed the Internet into a communication platform with strong measures of condentiality and integrity. It is one