Chapter 7 NP Completeness
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Midterm Study Sheet for CS3719 Regular Languages and Finite
Midterm study sheet for CS3719 Regular languages and finite automata: • An alphabet is a finite set of symbols. Set of all finite strings over an alphabet Σ is denoted Σ∗.A language is a subset of Σ∗. Empty string is called (epsilon). • Regular expressions are built recursively starting from ∅, and symbols from Σ and closing under ∗ Union (R1 ∪ R2), Concatenation (R1 ◦ R2) and Kleene Star (R denoting 0 or more repetitions of R) operations. These three operations are called regular operations. • A Deterministic Finite Automaton (DFA) D is a 5-tuple (Q, Σ, δ, q0,F ), where Q is a finite set of states, Σ is the alphabet, δ : Q × Σ → Q is the transition function, q0 is the start state, and F is the set of accept states. A DFA accepts a string if there exists a sequence of states starting with r0 = q0 and ending with rn ∈ F such that ∀i, 0 ≤ i < n, δ(ri, wi) = ri+1. The language of a DFA, denoted L(D) is the set of all and only strings that D accepts. • Deterministic finite automata are used in string matching algorithms such as Knuth-Morris-Pratt algorithm. • A language is called regular if it is recognized by some DFA. • ‘Theorem: The class of regular languages is closed under union, concatenation and Kleene star operations. • A non-deterministic finite automaton (NFA) is a 5-tuple (Q, Σ, δ, q0,F ), where Q, Σ, q0 and F are as in the case of DFA, but the transition function δ is δ : Q × (Σ ∪ {}) → P(Q). -

Chapter 6 Formal Language Theory
Chapter 6 Formal Language Theory In this chapter, we introduce formal language theory, the computational theories of languages and grammars. The models are actually inspired by formal logic, enriched with insights from the theory of computation. We begin with the definition of a language and then proceed to a rough characterization of the basic Chomsky hierarchy. We then turn to a more de- tailed consideration of the types of languages in the hierarchy and automata theory. 6.1 Languages What is a language? Formally, a language L is defined as as set (possibly infinite) of strings over some finite alphabet. Definition 7 (Language) A language L is a possibly infinite set of strings over a finite alphabet Σ. We define Σ∗ as the set of all possible strings over some alphabet Σ. Thus L ⊆ Σ∗. The set of all possible languages over some alphabet Σ is the set of ∗ all possible subsets of Σ∗, i.e. 2Σ or ℘(Σ∗). This may seem rather simple, but is actually perfectly adequate for our purposes. 6.2 Grammars A grammar is a way to characterize a language L, a way to list out which strings of Σ∗ are in L and which are not. If L is finite, we could simply list 94 CHAPTER 6. FORMAL LANGUAGE THEORY 95 the strings, but languages by definition need not be finite. In fact, all of the languages we are interested in are infinite. This is, as we showed in chapter 2, also true of human language. Relating the material of this chapter to that of the preceding two, we can view a grammar as a logical system by which we can prove things. -
Deterministic Finite Automata 0 0,1 1
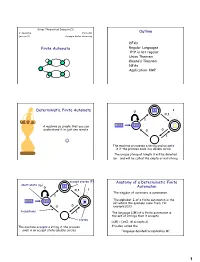
Great Theoretical Ideas in CS V. Adamchik CS 15-251 Outline Lecture 21 Carnegie Mellon University DFAs Finite Automata Regular Languages 0n1n is not regular Union Theorem Kleene’s Theorem NFAs Application: KMP 11 1 Deterministic Finite Automata 0 0,1 1 A machine so simple that you can 0111 111 1 ϵ understand it in just one minute 0 0 1 The machine processes a string and accepts it if the process ends in a double circle The unique string of length 0 will be denoted by ε and will be called the empty or null string accept states (F) Anatomy of a Deterministic Finite start state (q0) 11 0 Automaton 0,1 1 The singular of automata is automaton. 1 The alphabet Σ of a finite automaton is the 0111 111 1 ϵ set where the symbols come from, for 0 0 example {0,1} transitions 1 The language L(M) of a finite automaton is the set of strings that it accepts states L(M) = {x∈Σ: M accepts x} The machine accepts a string if the process It’s also called the ends in an accept state (double circle) “language decided/accepted by M”. 1 The Language L(M) of Machine M The Language L(M) of Machine M 0 0 0 0,1 1 q 0 q1 q0 1 1 What language does this DFA decide/accept? L(M) = All strings of 0s and 1s The language of a finite automaton is the set of strings that it accepts L(M) = { w | w has an even number of 1s} M = (Q, Σ, , q0, F) Q = {q0, q1, q2, q3} Formal definition of DFAs where Σ = {0,1} A finite automaton is a 5-tuple M = (Q, Σ, , q0, F) q0 Q is start state Q is the finite set of states F = {q1, q2} Q accept states : Q Σ → Q transition function Σ is the alphabet : Q Σ → Q is the transition function q 1 0 1 0 1 0,1 q0 Q is the start state q0 q0 q1 1 q q1 q2 q2 F Q is the set of accept states 0 M q2 0 0 q2 q3 q2 q q q 1 3 0 2 L(M) = the language of machine M q3 = set of all strings machine M accepts EXAMPLE Determine the language An automaton that accepts all recognized by and only those strings that contain 001 1 0,1 0,1 0 1 0 0 0 1 {0} {00} {001} 1 L(M)={1,11,111, …} 2 Membership problem Determine the language decided by Determine whether some word belongs to the language. -

Interactive Proofs 1 1 Pspace ⊆ IP
CS294: Probabilistically Checkable and Interactive Proofs January 24, 2017 Interactive Proofs 1 Instructor: Alessandro Chiesa & Igor Shinkar Scribe: Mariel Supina 1 Pspace ⊆ IP The first proof that Pspace ⊆ IP is due to Shamir, and a simplified proof was given by Shen. These notes discuss the simplified version in [She92], though most of the ideas are the same as those in [Sha92]. Notes by Katz also served as a reference [Kat11]. Theorem 1 ([Sha92]) Pspace ⊆ IP. To show the inclusion of Pspace in IP, we need to begin with a Pspace-complete language. 1.1 True Quantified Boolean Formulas (tqbf) Definition 2 A quantified boolean formula (QBF) is an expression of the form 8x19x28x3 ::: 9xnφ(x1; : : : ; xn); (1) where φ is a boolean formula on n variables. Note that since each variable in a QBF is quantified, a QBF is either true or false. Definition 3 tqbf is the language of all boolean formulas φ such that if φ is a formula on n variables, then the corresponding QBF (1) is true. Fact 4 tqbf is Pspace-complete (see section 2 for a proof). Hence to show that Pspace ⊆ IP, it suffices to show that tqbf 2 IP. Claim 5 tqbf 2 IP. In order prove claim 5, we will need to present a complete and sound interactive protocol that decides whether a given QBF is true. In the sum-check protocol we used an arithmetization of a 3-CNF boolean formula. Likewise, here we will need a way to arithmetize a QBF. 1.2 Arithmetization of a QBF We begin with a boolean formula φ, and we let n be the number of variables and m the number of clauses of φ. -

Interactive Proofs for Quantum Computations
Innovations in Computer Science 2010 Interactive Proofs For Quantum Computations Dorit Aharonov Michael Ben-Or Elad Eban School of Computer Science, The Hebrew University of Jerusalem, Israel [email protected] [email protected] [email protected] Abstract: The widely held belief that BQP strictly contains BPP raises fundamental questions: Upcoming generations of quantum computers might already be too large to be simulated classically. Is it possible to experimentally test that these systems perform as they should, if we cannot efficiently compute predictions for their behavior? Vazirani has asked [21]: If computing predictions for Quantum Mechanics requires exponential resources, is Quantum Mechanics a falsifiable theory? In cryptographic settings, an untrusted future company wants to sell a quantum computer or perform a delegated quantum computation. Can the customer be convinced of correctness without the ability to compare results to predictions? To provide answers to these questions, we define Quantum Prover Interactive Proofs (QPIP). Whereas in standard Interactive Proofs [13] the prover is computationally unbounded, here our prover is in BQP, representing a quantum computer. The verifier models our current computational capabilities: it is a BPP machine, with access to few qubits. Our main theorem can be roughly stated as: ”Any language in BQP has a QPIP, and moreover, a fault tolerant one” (providing a partial answer to a challenge posted in [1]). We provide two proofs. The simpler one uses a new (possibly of independent interest) quantum authentication scheme (QAS) based on random Clifford elements. This QPIP however, is not fault tolerant. Our second protocol uses polynomial codes QAS due to Ben-Or, Cr´epeau, Gottesman, Hassidim, and Smith [8], combined with quantum fault tolerance and secure multiparty quantum computation techniques. -
6.045 Final Exam Name
6.045J/18.400J: Automata, Computability and Complexity Prof. Nancy Lynch 6.045 Final Exam May 20, 2005 Name: • Please write your name on each page. • This exam is open book, open notes. • There are two sheets of scratch paper at the end of this exam. • Questions vary substantially in difficulty. Use your time accordingly. • If you cannot produce a full proof, clearly state partial results for partial credit. • Good luck! Part Problem Points Grade Part I 1–10 50 1 20 2 15 3 25 Part II 4 15 5 15 6 10 Total 150 final-1 Name: Part I Multiple Choice Questions. (50 points, 5 points for each question) For each question, any number of the listed answersClearly may place be correct. an “X” in the box next to each of the answers that you are selecting. Problem 1: Which of the following are true statements about regular and nonregular languages? (All lan guages are over the alphabet{0, 1}) IfL1 ⊆ L2 andL2 is regular, thenL1 must be regular. IfL1 andL2 are nonregular, thenL1 ∪ L2 must be nonregular. IfL1 is nonregular, then the complementL 1 must of also be nonregular. IfL1 is regular,L2 is nonregular, andL1 ∩ L2 is nonregular, thenL1 ∪ L2 must be nonregular. IfL1 is regular,L2 is nonregular, andL1 ∩ L2 is regular, thenL1 ∪ L2 must be nonregular. Problem 2: Which of the following are guaranteed to be regular languages ? ∗ L2 = {ww : w ∈{0, 1}}. L2 = {ww : w ∈ L1}, whereL1 is a regular language. L2 = {w : ww ∈ L1}, whereL1 is a regular language. L2 = {w : for somex,| w| = |x| andwx ∈ L1}, whereL1 is a regular language. -

Distribution of Units of Real Quadratic Number Fields
Y.-M. J. Chen, Y. Kitaoka and J. Yu Nagoya Math. J. Vol. 158 (2000), 167{184 DISTRIBUTION OF UNITS OF REAL QUADRATIC NUMBER FIELDS YEN-MEI J. CHEN, YOSHIYUKI KITAOKA and JING YU1 Dedicated to the seventieth birthday of Professor Tomio Kubota Abstract. Let k be a real quadratic field and k, E the ring of integers and the group of units in k. Denoting by E( ¡ ) the subgroup represented by E of × ¡ ¡ ( k= ¡ ) for a prime ideal , we show that prime ideals for which the order of E( ¡ ) is theoretically maximal have a positive density under the Generalized Riemann Hypothesis. 1. Statement of the result x Let k be a real quadratic number field with discriminant D0 and fun- damental unit (> 1), and let ok and E be the ring of integers in k and the set of units in k, respectively. For a prime ideal p of k we denote by E(p) the subgroup of the unit group (ok=p)× of the residue class group modulo p con- sisting of classes represented by elements of E and set Ip := [(ok=p)× : E(p)], where p is the rational prime lying below p. It is obvious that Ip is inde- pendent of the choice of prime ideals lying above p. Set 1; if p is decomposable or ramified in k, ` := 8p 1; if p remains prime in k and N () = 1, p − k=Q <(p 1)=2; if p remains prime in k and N () = 1, − k=Q − : where Nk=Q stands for the norm from k to the rational number field Q. -

Lecture 16 1 Interactive Proofs
Notes on Complexity Theory Last updated: October, 2011 Lecture 16 Jonathan Katz 1 Interactive Proofs Let us begin by re-examining our intuitive notion of what it means to \prove" a statement. Tra- ditional mathematical proofs are static and are veri¯ed deterministically: the veri¯er checks the claimed proof of a given statement and is either convinced that the statement is true (if the proof is correct) or remains unconvinced (if the proof is flawed | note that the statement may possibly still be true in this case, it just means there was something wrong with the proof). A statement is true (in this traditional setting) i® there exists a valid proof that convinces a legitimate veri¯er. Abstracting this process a bit, we may imagine a prover P and a veri¯er V such that the prover is trying to convince the veri¯er of the truth of some particular statement x; more concretely, let us say that P is trying to convince V that x 2 L for some ¯xed language L. We will require the veri¯er to run in polynomial time (in jxj), since we would like whatever proofs we come up with to be e±ciently veri¯able. A traditional mathematical proof can be cast in this framework by simply having P send a proof ¼ to V, who then deterministically checks whether ¼ is a valid proof of x and outputs V(x; ¼) (with 1 denoting acceptance and 0 rejection). (Note that since V runs in polynomial time, we may assume that the length of the proof ¼ is also polynomial.) The traditional mathematical notion of a proof is captured by requiring: ² If x 2 L, then there exists a proof ¼ such that V(x; ¼) = 1. -

(A) for Any Regular Expression R, the Set L(R) of Strings
Kleene’s Theorem Definition. Alanguageisregular iff it is equal to L(M), the set of strings accepted by some deterministic finite automaton M. Theorem. (a) For any regular expression r,thesetL(r) of strings matching r is a regular language. (b) Conversely, every regular language is the form L(r) for some regular expression r. L6 79 Example of a regular language Recall the example DFA we used earlier: b a a a a M ! q0 q1 q2 q3 b b b In this case it’s not hard to see that L(M)=L(r) for r =(a|b)∗ aaa(a|b)∗ L6 80 Example M ! a 1 b 0 b a a 2 L(M)=L(r) for which regular expression r? Guess: r = a∗|a∗b(ab)∗ aaa∗ L6 81 Example M ! a 1 b 0 b a a 2 L(M)=L(r) for which regular expression r? Guess: r = a∗|a∗b(ab)∗ aaa∗ since baabaa ∈ L(M) WRONG! but baabaa ̸∈ L(a∗|a∗b(ab)∗ aaa∗ ) We need an algorithm for constructing a suitable r for each M (plus a proof that it is correct). L6 81 Lemma. Given an NFA M =(Q, Σ, δ, s, F),foreach subset S ⊆ Q and each pair of states q, q′ ∈ Q,thereisa S regular expression rq,q′ satisfying S Σ∗ u ∗ ′ L(rq,q′ )={u ∈ | q −→ q in M with all inter- mediate states of the sequence of transitions in S}. Hence if the subset F of accepting states has k distinct elements, q1,...,qk say, then L(M)=L(r) with r ! r1|···|rk where Q ri = rs,qi (i = 1, . -

IP=PSPACE. Arthur-Merlin Games
Computational Complexity Theory, Fall 2010 10 November Lecture 18: IP=PSPACE. Arthur-Merlin Games Lecturer: Kristoffer Arnsfelt Hansen Scribe: Andreas Hummelshøj J Update: Ω(n) Last time, we were looking at MOD3◦MOD2. We mentioned that AND required size 2 MOD3◦ MOD2 circuits. We also mentioned, as being open, whether NEXP ⊆ (nonuniform)MOD2 ◦ MOD3 ◦ MOD2. Since 9/11-2010, this is no longer open. Definition 1 ACC0 = class of languages: 0 0 ACC = [m>2ACC [m]; where AC0[m] = class of languages computed by depth O(1) size nO(1) circuits with AND-, OR- and MODm-gates. This is in fact in many ways a natural class of languages, like AC0 and NC1. 0 Theorem 2 NEXP * (nonuniform)ACC . New open problem: Is EXP ⊆ (nonuniform)MOD2 ◦ MOD3 ◦ MOD2? Recap: We defined arithmetization A(φ) of a 3-SAT formula φ: A(xi) = xi; A(xi) = 1 − xi; 3 Y A(l1 _ l2 _ l3) = 1 − (1 − A(li)); i=1 m Y A(c1 ^ · · · ^ cm) = A(cj): j=1 1 1 X X ]φ = ··· P (x1; : : : ; xn);P = A(φ): x1=0 xn=0 1 Sumcheck: Given g(x1; : : : ; xn), K and prime number p, decide if 1 1 X X ··· g(x1; : : : ; xn) ≡ K (mod p): x1=0 xn=0 True Quantified Boolean Formulae: 0 0 Given φ ≡ 9x18x2 ::: 8xnφ (x1; : : : ; xn), where φ is a 3SAT formula, decide if φ is true. Observation: φ true , P1 Q1 P ··· Q1 P (x ; : : : ; x ) > 0, P = A(φ0). x1=0 x2=0 x3 x1=0 1 n Protocol: Can't we just do it analogous to Sumcheck? Id est: remove outermost P, P sends polynomial S, V checks if S(0) + S(1) ≡ K, asks P to prove Q1 P1 ··· Q1 P (a) ≡ S(a), where x2=0 x3=0 xn=0 a 2 f0; 1; : : : ; p − 1g is chosen uniformly at random. -

Formal Languages We’Ll Use the English Language As a Running Example
Formal Languages We’ll use the English language as a running example. Definitions. Examples. A string is a finite set of symbols, where • each symbol belongs to an alphabet de- noted by Σ. The set of all strings that can be constructed • from an alphabet Σ is Σ ∗. If x, y are two strings of lengths x and y , • then: | | | | – xy or x y is the concatenation of x and y, so the◦ length, xy = x + y | | | | | | – (x)R is the reversal of x – the kth-power of x is k ! if k =0 x = k 1 x − x, if k>0 ! ◦ – equal, substring, prefix, suffix are de- fined in the expected ways. – Note that the language is not the same language as !. ∅ 73 Operations on Languages Suppose that LE is the English language and that LF is the French language over an alphabet Σ. Complementation: L = Σ L • ∗ − LE is the set of all words that do NOT belong in the english dictionary . Union: L1 L2 = x : x L1 or x L2 • ∪ { ∈ ∈ } L L is the set of all english and french words. E ∪ F Intersection: L1 L2 = x : x L1 and x L2 • ∩ { ∈ ∈ } LE LF is the set of all words that belong to both english and∩ french...eg., journal Concatenation: L1 L2 is the set of all strings xy such • ◦ that x L1 and y L2 ∈ ∈ Q: What is an example of a string in L L ? E ◦ F goodnuit Q: What if L or L is ? What is L L ? E F ∅ E ◦ F ∅ 74 Kleene star: L∗. -

Lecture 14 1 Introduction 2 the IP Protocol 3 Graph Non-Isomorphism
6.841 Advanced Complexity Theory Apr 2, 2007 Lecture 14 Lecturer: Madhu Sudan Scribe: Nate Ince, Krzysztof Onak 1 Introduction The idea behind interactive proofs came from cryptography. Transferring coded massages usually involves a password known only to the sender and receiver, and a message. When you send an encrypted message, you have to show you know the password to show that your message is official. However, if we do this by sending the password with the message, there’s a high chance the password could be eavesdropped. So we would like a method to let you show you know the password without sending it. Goldwasser, Mikoli, and Rakoff were inspired by this to create the idea of the interactive proof. 2 The IP protocol Let L be some language. We say that L ∈ IP as a protocol between an exponential-time prover P and a polynomial time randomized verifier V so if x ∈ L, then the probabillity that after a completed exchange Π between P and V, P r[V (x, Π) = 1] ≥ 1 − 1/2|x| and if x∈ / L, then the probability that after a completed exchange Π0 between Q and V, where Q is any expon- tential algorithm, P r[V (x, Π0) = 1] ≤ 1/2|x|. We formally define an exchange between P and V as a series of questions and answers q1, a1, a2, q2 . , qn, an so that |qi|, |ai|, n ∈ poly(|x|), q1 = V (x), ai = P (x; q1, a1, . , qi), and qi = V (x, ; q1, a1, . , ai−1; ri−1) for all i ≤ n, where ri is a random string V uses at the ith exchange to determine all “random” decisions V makes.