Improving the Security of Mobile Devices Through Multi-Dimensional and Analog Authentication" (2018)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Open Yibo Wu Final.Pdf
The Pennsylvania State University The Graduate School RESOURCE-AWARE CROWDSOURCING IN WIRELESS NETWORKS A Dissertation in Computer Science and Engineering by Yibo Wu c 2018 Yibo Wu Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy May 2018 The dissertation of Yibo Wu was reviewed and approved∗ by the following: Guohong Cao Professor of Computer Science and Engineering Dissertation Adviser, Chair of Committee Robert Collins Associate Professor of Computer Science and Engineering Sencun Zhu Associate Professor of Computer Science and Engineering Associate Professor of Information Sciences and Technology Zhenhui Li Associate Professor of Information Sciences and Technology Bhuvan Urgaonkar Associate Professor of Computer Science and Engineering Graduate Program Chair of Computer Science and Engineering ∗Signatures are on file in the Graduate School. Abstract The ubiquity of mobile devices has opened up opportunities for a wide range of applications based on photo/video crowdsourcing, where the server collects a large number of photos/videos from the public to obtain desired information. How- ever, transmitting large numbers of photos/videos in a wireless environment with bandwidth constraints is challenging, and it is hard to run computation-intensive image processing techniques on mobile devices with limited energy and computa- tion power to identify the useful photos/videos and remove redundancy. To address these challenges, we propose a framework to quantify the quality of crowdsourced photos/videos based on the accessible geographical and geometrical information (called metadata) including the orientation, position, and all other related param- eters of the built-in camera. From metadata, we can infer where and how the photo/video is taken, and then only transmit the most useful photos/videos. -

Boosting the Guessing Attack Performance on Android Lock Patterns with Smudge Attacks
Boosting the Guessing Attack Performance on Android Lock Patterns with Smudge Attacks Seunghun Cha1, Sungsu Kwag1, Hyoungshick Kim1 and Jun Ho Huh2 1Department of Software, Sungkyunkwan University, Republic of Korea 2Honeywell ACS Labs, Golden Valley, MN USA {sh.cha, kssu1994, hyoung}@skku.edu [email protected] ABSTRACT 3 × 3 grid. This scheme has quickly emerged as the most popular Android allows 20 consecutive fail attempts on unlocking a de- locking method for Android devices [22]. Many users perceive vice. This makes it difficult for pure guessing attacks to crack patterns as quicker and less error-prone unlocking method than user patterns on a stolen device before it permanently locks it- PIN [23]. It is unclear, however, whether their security is guar- self. We investigate the effectiveness of combining Markov model- anteed in practice. Several studies [19, 21] demonstrated that the based guessing attacks with smudge attacks on unlocking Android space of real patterns might be much smaller than the theoretical devices within 20 attempts. Detected smudges are used to pre- space, making password guessing attacks feasible. compute all the possible segments and patterns, significantly reduc- To mitigate guessing attacks, Android only allows up to 20 con- ing the pattern space that needs to be brute-forced. Our Markov- secutive fail unlock attempts—after 20 consecutive fail attempts, model was trained using 70% of a real-world pattern dataset that Android displays the “Too many pattern attempts” error message, consists of 312 patterns. We recruited 12 participants to draw the and asks the user to log in with a Google account to unlock the de- remaining 30% on Samsung Galaxy S4, and used smudges they left vice. -

Terraillon Wellness Coach Supported Devices
Terraillon Wellness Coach Supported Devices Warning This document lists the smartphones compatible with the download of the Wellness Coach app from the App Store (Apple) and Play Store (Android). Some models have been tested by Terraillon to check the compatibility and smooth operation of the Wellness Coach app. However, many models have not been tested. Therefore, Terraillon doesn't ensure the proper functioning of the Wellness Coach application on these models. If your smartphone model does not appear in the list, thank you to send an email to [email protected] giving us the model of your smartphone so that we can activate if the application store allows it. BRAND MODEL NAME MANUFACTURER MODEL NAME OS REQUIRED ACER Liquid Z530 acer_T02 Android 4.3+ ACER Liquid Jade S acer_S56 Android 4.3+ ACER Liquid E700 acer_e39 Android 4.3+ ACER Liquid Z630 acer_t03 Android 4.3+ ACER Liquid Z320 T012 Android 4.3+ ARCHOS 45 Helium 4G a45he Android 4.3+ ARCHOS 50 Helium 4G a50he Android 4.3+ ARCHOS Archos 45b Helium ac45bhe Android 4.3+ ARCHOS ARCHOS 50c Helium ac50che Android 4.3+ APPLE iPhone 4S iOS8+ APPLE iPhone 5 iOS8+ APPLE iPhone 5C iOS8+ APPLE iPhone 5S iOS8+ APPLE iPhone 6 iOS8+ APPLE iPhone 6 Plus iOS8+ APPLE iPhone 6S iOS8+ APPLE iPhone 6S Plus iOS8+ APPLE iPad Mini 1 iOS8+ APPLE iPad Mini 2 iOS8+ 1 / 48 www.terraillon.com Terraillon Wellness Coach Supported Devices BRAND MODEL NAME MANUFACTURER MODEL NAME OS REQUIRED APPLE iPad Mini 3 iOS8+ APPLE iPad Mini 4 iOS8+ APPLE iPad 3 iOS8+ APPLE iPad 4 iOS8+ APPLE iPad Air iOS8+ -
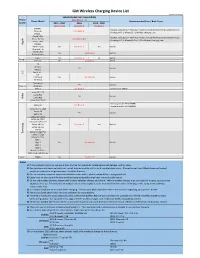
GM Wireless Charging Device List
GM Wireless Charging Device List Revision: Aug 30, 2019 Vehicle Model Year Compatibility Phone ( See Notes 1 - 7) Phone Model Recommended Case / Back Cover Brand 2015 - 2017 2018 2019 - 2020 (See Note 8) (See Note 8) (See Note 9) iPhone 6 ŸBEZALEL Latitude [Qi + PMA] Dual-Mode Universal Wireless Charging Receiver Case iPhone 6s See Note: A ŸAircharge MFi Qi iPhone 6S / 6 Wireless Charging Case iPhone 7 iPhone 6 Plus ŸBEZALEL Latitude [Qi + PMA] Dual-Mode Universal Wireless Charging Receiver Case e iPhone 6s Plus See Note: A & B l ŸAircharge MFi Qi iPhone 6S Plus / 6 Plus Wireless Charging Case p iPhone 7 Plus p A iPhone 8 iPhone X (10) No See Note: C Yes Built-in iPhone Xs / Xr iPhone 8 Plus No See Note: B Built-in iPhone Xs Max Pixel 3 No See Note: C Yes Built-in Google Pixel 3XL No See Note: B Built-in G6 Nexus 4 Yes Built-in Nexus 5 G Spectrum 2 L V30 V40 ThinQ No See Note: B Built-in G7 ThinQ Droid Maxx Yes Built-in Motorola Droid Mini Moto X See Note: A Incipio model: MT231 Lumia 830 / 930 a i Lumia 920 k Yes Built-in o Lumia 928 N Lumia 950 / 950 XL ŸSamsung model: EP-VG900BBU Galaxy S5 See Note: A ŸSamsung model: EP-CG900IBA Galaxy S6 / S6 Edge Galaxy S8 Yes Built-in Galaxy S9 Galaxy S10 / S10e Galaxy S6 Active Galaxy S7 / S7 Active g Galaxy S8 Plus No See Note: C Yes Built-in n u Galaxy S9 Plus s m S10 5G a Galaxy S6 Edge Plus S Galaxy S7 Edge Galaxy S10 Plus Note 5 Note 7 No See Note: B Built-in Note 8 Note 9 Note 10 / 10 Plus Note 10 5G / 10 Plus 5G Xiami MIX2S No See Note: B Built-in Notes: 1) If phone does not charge: remove it from charger for 3 seconds, rotate phone 180 degrees, and try again. -

Geometric Image Transformations for Smudge-Resistant User Authentication
SmudgeSafe: Geometric Image Transformations for Smudge-resistant User Authentication Stefan Schneegass1, Frank Steimle1, Andreas Bulling2, Florian Alt3, Albrecht Schmidt1 1University of Stuttgart 2Max Planck Institute for Informatics 3University of Munich HCI Group Perceptual User Interfaces Group Media Informatics Group fi[email protected] [email protected] florian.alt@ifi.lmu.de ABSTRACT Touch-enabled user interfaces have become ubiquitous, such as on ATMs or portable devices. At the same time, authenti- cation using touch input is problematic, since finger smudge traces may allow attackers to reconstruct passwords. We present SmudgeSafe, an authentication system that uses ran- dom geometric image transformations, such as translation, ro- tation, scaling, shearing, and flipping, to increase the security of cued-recall graphical passwords. We describe the design space of these transformations and report on two user studies: A lab-based security study involving 20 participants in attack- ing user-defined passwords, using high quality pictures of real smudge traces captured on a mobile phone display; and an in- the-field usability study with 374 participants who generated more than 130,000 logins on a mobile phone implementation of SmudgeSafe. Results show that SmudgeSafe significantly increases security compared to authentication schemes based on PINs and lock patterns, and exhibits very high learnability, efficiency, and memorability. (a) (b) Author Keywords Figure 1. Entering a graphical password on a touch-enabled mobile de- vice leaves a smudge trace on the display that may allow an attacker to Graphical passwords; Touch input; Finger smudge traces reconstruct the password (a). SmudgeSafe applies random affine geo- metric transformations to the image underlying the password for subse- ACM Classification Keywords quent logins (here: rotation) to increase smudge resistance (b). -

Nexus-4 User Manual
NeXus-4 User Manual Version 2.0 0344 Table of contents 1 Service and support 3 1.1 About this manual 3 1.2 Warranty information 3 2 Safety information 4 2.1 Explanation of markings 4 2.2 Limitations of use 5 2.3 Safety measures and warnings 5 2.4 Precautionary measures 7 2.5 Disclosure of residual risk 7 2.6 Information for lay operators 7 3 Product overview 8 3.1 Product components 8 3.2 Intended use 8 3.3 NeXus-4 views 9 3.4 User interface 9 3.5 Patient connections 10 3.6 Device label 10 4 Instructions for use 11 4.1 Software 11 4.2 Powering the NeXus-4 12 4.3 Transfer data to PC 12 4.4 Perform measurement 13 4.5 Mobility 13 5 Operational principles 14 5.1 Bipolar input channels 14 5.2 Auxiliary input channel 14 5.3 Filtering 14 6 Maintenance 15 7 Electromagnetic guidance 16 8 Technical specifications 19 2 1 Service and support 1.1 About this manual This manual is intended for the user of the NeXus-4 system – referred to as ‘product’ throughout this manual. It contains general operating instructions, precautionary measures, maintenance instructions and information for use of the product. Read this manual carefully and familiarize yourself with the various controls and accessories before starting to use the product. This product is exclusively manufactured by Twente Medical Systems International B.V. for Mind Media B.V. Distribution and service is exclusively performed by or through Mind Media B.V. -
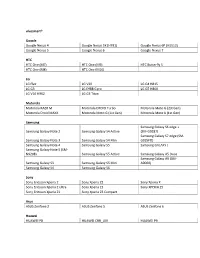
Vívosmart® Google Google Nexus 4 Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Nexus 5 Google Nexus 6 Google Nexus
vívosmart® Google Google Nexus 4 Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Nexus 5 Google Nexus 6 Google Nexus 7 HTC HTC One (M7) HTC One (M9) HTC Butterfly S HTC One (M8) HTC One (M10) LG LG Flex LG V20 LG G4 H815 LG G3 LG E988 Gpro LG G5 H860 LG V10 H962 LG G3 Titan Motorola Motorola RAZR M Motorola DROID Turbo Motorola Moto G (2st Gen) Motorola Droid MAXX Motorola Moto G (1st Gen) Motorola Moto X (1st Gen) Samsung Samsung Galaxy S6 edge + Samsung Galaxy Note 2 Samsung Galaxy S4 Active (SM-G9287) Samsung Galaxy S7 edge (SM- Samsung Galaxy Note 3 Samsung Galaxy S4 Mini G935FD) Samsung Galaxy Note 4 Samsung Galaxy S5 Samsung GALAXY J Samsung Galaxy Note 5 (SM- N9208) Samsung Galaxy S5 Active Samsung Galaxy A5 Duos Samsung Galaxy A9 (SM- Samsung Galaxy S3 Samsung Galaxy S5 Mini A9000) Samsung Galaxy S4 Samsung Galaxy S6 Sony Sony Ericsson Xperia Z Sony Xperia Z2 Sony Xperia X Sony Ericsson Xperia Z Ultra Sony Xperia Z3 Sony XPERIA Z5 Sony Ericsson Xperia Z1 Sony Xperia Z3 Compact Asus ASUS Zenfone 2 ASUS Zenfone 5 ASUS Zenfone 6 Huawei HUAWEI P8 HUAWEI CRR_L09 HUAWEI P9 Oppo OPPO X9076 OPPO X9009 Xiaomi XIAOMI 2S XIAOMI 3 XIAOMI 5 XIAOMI Note One Plus OnePlus 3 (A3000) vívosmart® 3 Google Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Pixel HTC HTC One (M9) HTC One (M10) HTC U11 HTC One (A9) HTC U Ultra LG LG V10 H962 LG G4 H815 LG G6 H870 LG V20 LG G5 H860 Motorola Motorola Moto Z Samsung Samsung Galaxy Note 3 Samsung Galaxy S6 Samsung Galaxy J5 Samsung Galaxy S6 edge + Samsung Galaxy Note 4 (SM-G9287) Samsung Galaxy -

Pathword: a Multimodal Password Entry Method for Ad-Hoc
Poster Session 1 ICMI’18, October 16-20, 2018, Boulder, CO, USA Pa thWord: A Multimodal Password Entry Method for Ad-hoc Authentication Based on Digit Shape and Smooth Pursuit Eye Movements Hassoumi Almoctar Pourang Irani École Nationale de l’Aviation Civile University of Manitoba Toulouse, France Winnipeg, Manitoba, Canada [email protected] [email protected] Vsevolod Peysakhovich Chrisophe Hurter ISAE-SUPAERO École Nationale de l’Aviation Civile Toulouse, France Toulouse, France [email protected] [email protected] ABSTRACT 6.71 cm (2.64 in) We present PathWord (PATH passWORD), a multimodal digit entry 1.9 cm method for ad-hoc authentication based on known digits shape and in) (5.44 cm 13.83 1.9 cm user relative eye movements. PathWord is a touch-free, gaze-based input modality, which attempts to decrease shoulder suring attacks when unlocking a system using PINs. The system uses a modiied web camera to detect the user’s eye. This enables suppressing direct touch, making it diicult for passer-bys to be aware of the input digits, thus reducing shoulder suring and smudge attacks. Figure 1. Patthword overview: (Left) A user’s eye, as seen through the infrared In addition to showing high accuracy rates (Study 1: 87.1% success- eye camera, following the red stimulus moving on the digit "3". The pupil cen- ful entries) and strong conidentiality through detailed evaluations ter implicitly draws the digit shape. (Middle Left) PathWord’s interface. On with 42 participants (Study 2), we demonstrate how PathWord con- each digit, a stimulus is drawn and travels its shape. -

Providing a Secure Hybrid Method for Graphical Password Authentication to Prevent Shoulder Surfing, Smudge and Brute Force Attack Faraji Sepideh
World Academy of Science, Engineering and Technology International Journal of Computer and Information Engineering Vol:13, No:12, 2019 Providing a Secure Hybrid Method for Graphical Password Authentication to Prevent Shoulder Surfing, Smudge and Brute Force Attack Faraji Sepideh attacks, such as brute force attack, dictionary attack, social Abstract—Nowadays, purchase rate of the smart device is engineering attack, guessing attack and many others [6]. increasing and user authentication is one of the important issues in A graphical password has been proposed as a possible information security. Alphanumeric strong passwords are difficult to alternative to a text-based password. According to memorize and also owners write them down on papers or save them psychological studies, pictures are generally easier to in a computer file. In addition, text password has its own flaws and is vulnerable to attacks. Graphical password can be used as an remember or recognized than text [7]. The graphical password alternative to alphanumeric password that users choose images as a technique is developed by Blonder in 1996 [8]. The purpose of password. This type of password is easier to use and memorize and this system is increasing the security space and avoiding the also more secure from pervious password types. In this paper we weakness of conventional password [9]. However, existing have designed a more secure graphical password system to prevent graphical password schemes are also vulnerable to various shoulder surfing, smudge and brute force attack. This scheme is a attacks, among which shoulder surfing, smudge attack, and combination of two types of graphical passwords recognition based and Cued recall based. -

Handset Industry 2013 Outlook
07 January 2013 Americas/United States Equity Research Telecommunications Equipment / MARKET WEIGHT Handset Industry 2013 Outlook Research Analysts INDUSTRY PRIMER Kulbinder Garcha 212 325 4795 [email protected] Bigger market, Apple and Samsung win Achal Sultania 44 20 7883 6884 ■ Market size underestimated for both smartphones/handsets. Our bottom-up [email protected] analysis suggests that the market underestimates the size of low-end ‘white- Talal Khan, CFA label’ smartphones, which causes us to restate our 2012/2013 volume estimates 212 325 8603 for the smartphone market higher by 6%/15% and 3%/4% for overall handsets. [email protected] We also raise our smartphone volume estimates by 20-25% long term and now Matthew Cabral estimate 1.43bn/1.74bn smartphones to be shipped in 2015/2017. We believe 212 538 6260 that the growth of ‘white-label’ smartphone market specifically poses a threat for [email protected] vendors like Nokia, RIMM, LG and possibly Samsung, given their exposure to feature phones and low-end smartphone segments. Ray Bao 212 325 1227 ■ Raising LT smartphone units to 1.74bn – a barbell develops for price points. [email protected] We believe that the addressable market for smartphones is 4.95bn longer term, Asian Research Analysts resulting in effective penetration of only 24% currently given our estimate of 1.2bn smartphone users by end of 2012. We expect effective smartphone Randy Abrams, CFA 886 2 2715 6366 penetration to rise to ~80% long term driving smartphone volumes of [email protected] 1.43bn/1.74bn units by 2015/2017 (26%/19% CAGR over this period). -

Augmented Unlocking Techniques for Smartphones Using Pre-Touch
Augmented Unlocking Techniques for Smartphones Using Pre-Touch Information Matthew Lakier Dimcho Karakashev Yixin Wang Ian Goldberg [email protected] [email protected] [email protected] [email protected] University of Waterloo University of Waterloo University of Waterloo University of Waterloo ABSTRACT Smartphones secure a significant amount of personal and private information, and are playing an increasingly important role in peo- ple’s lives. However, current techniques to manually authenticate to smartphones have failed in both not-so-surprising (shoulder surfing) and quite surprising (smudge attacks) ways. In this work, we propose a new technique called 3D Pattern. Our 3D Pattern technique takes advantage of pre-touch sensing, which could soon allow smartphones to sense a user’s finger position at some distance from the screen. We describe and implement the technique, and evaluate it in a small pilot study (n=6) by comparing it to PIN and pattern locks. Our results show that although our prototype takes longer to authenticate, it is completely immune to smudge attacks Figure 1: Study participant authenticating using our 3D Pat- and promises to be more resistant to shoulder surfing. tern technique. CCS CONCEPTS smartphones as a way to protect private information. Even users • Security and privacy ! Usability in security and privacy; • utilizing fingerprint readers are often required to enter a PINfor Human-centered computing ! Interaction techniques. added security, for example, when rebooting or authorizing pay- ments. However, common authentication techniques often have KEYWORDS surprising failure modes. We examine in particular the effect of authentication, mobile devices, pre-touch the “smudge attack” [1] whereby swiping an unlock pattern on the screen leaves a readily visible oily smudge that unintentionally ACM Reference Format: Matthew Lakier, Dimcho Karakashev, Yixin Wang, and Ian Goldberg. -

Evaluating Bluetooth Low Energy for Iot
Evaluating Bluetooth Low Energy for IoT Jonathan Furst¨ ∗, Kaifei Cheny, Hyung-Sin Kimy and Philippe Bonnet∗ ∗IT University of Copenhagen, yUC Berkeley [email protected], fkaifei, [email protected], [email protected] Abstract—Bluetooth Low Energy (BLE) is the short-range, While others have experienced similar phenomena [7], we single-hop protocol of choice for the edge of the IoT. Despite could not find systematic studies of BLE characteristics on its growing significance for phone-to-peripheral communication, smartphones in the literature. Most existing work focus on the BLE’s smartphone system performance characteristics are not well understood. As others, we experienced mixed erratic perfor- BLE performance of BLE SoCs [8], [9], [10], [11], [12], with- mance results in our BLE based smartphone-centric applications. out quantifying BLE performance in a smartphone context. In these applications, developers can only access low-level func- However, smartphones-peripheral systems represent a large set tionalities through multiple layers of OS and hardware abstrac- of BLE applications in the wild [1], [2], [3]. In our work, tions. We propose an experimental framework for such systems, we thus focus on two questions: (1) Can we show systematic with which we perform experiments on a variety of modern smartphones. Our evaluation characterizes existing devices and variations in BLE application behavior across smartphone gives new insight about peripheral parameters settings. We show models? (2) Can we define a model to characterize BLE that BLE performances vary significantly in non-trivial ways, performance on smartphones, that could inform application depending on SoC and OS with a vast impact on applications.