Energy Balanced Sub-Round Local Topology Management for Wireless Sensor Network
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Novel Measurement System for Mechanical Parts
Sensors and Materials, Vol. 28, No. 9 (2016) 1043–1051 1043 MYU Tokyo S & M 1266 A Novel Measurement System for Mechanical Parts Kuo-Yi Huang,* Yuh-Chung Hu,1 Mu-Tian Yan,2 and Liang-Shun Chang2 Department of Bio-Industrial Mechatronics Engineering, National Chung Hsing University, Tai-Chung 402, Taiwan 1Department of Mechanical and Electromechanical Engineering, National Ilan University, Ilan 260, Taiwan 2Department of Mechatronic Engineering, Huafan University, New Taipei City 223, Taiwan (Received December 21, 2015; accepted June 1, 2016) Keywords: mechanical parts (MPs), wire EDM, break profiles, image processing In this paper, a novel measurement system simply comprising a scanner is proposed to measure the profiles of mechanical parts (MPs) fabricated by wire electrical discharge machining (EDM). The scanner is used to acquire images of MPs, and a novel measurement procedure is employed, wherein the edge bands of MP images are extracted and then break profiles are fitted and linked to achieve more accurate profiles of MPs. The Sobel filter and image processing techniques are employed to segment edge bands of the MP images. The central moment and polynomial curve fitting are then used to find break profiles in edge bands. Finally, a Bezier curve is employed to link break profiles of edge bands of the images. Experimental results show that the proposed system is accurate and can effectively yield an estimate of the profile of an MP image. This method is immediately applicable in industry to measure MPs because of its simplicity. 1. -

A Flexible Proximity Sensor Fully Fabricated by Inkjet Printing
Sensors 2010, 10, 5054-5062; doi:10.3390/s100505054 OPEN ACCESS sensors ISSN 1424-8220 www.mdpi.com/journal/sensors Article A Flexible Proximity Sensor Fully Fabricated by Inkjet Printing Chin-Tsan Wang 1, Kuo-Yi Huang 2, David T. W. Lin 3, Wei-Chia Liao 1, Hua-Wei Lin 1 and Yuh-Chung Hu 1,* 1 Department of Mechanical and Electromechanical Engineering, National ILan University, ILan 260, Taiwan; E-Mails: [email protected] (C.-T.W.); [email protected] (W.-C.L.); [email protected] (H.-W.L.) 2 Department of Mechatronic Engineering, Huafan University, Taipei 223, Taiwan; E-Mail: [email protected] 3 Graduate Institute of Mechatronic System Engineering, National University of Tainan, Tainan 70005, Taiwan; E-Mail: [email protected] * Author to whom correspondence should be addressed; E-Mail: [email protected]; Tel.: +886-3-9357400-685; Fax: +886-3-9322610. Received: 9 March 2010; in revised form: 11 May 2010 / Accepted: 14 May 2010 / Published: 19 May 2010 Abstract: A flexible proximity sensor fully fabricated by inkjet printing is proposed in this paper. The flexible proximity sensor is composed of a ZnO layer sandwiched in between a flexible aluminum sheet and a web-shaped top electrode layer. The flexible aluminum sheet serves as the bottom electrode. The material of the top electrode layer is nano silver. Both the ZnO and top electrode layers are deposited by inkjet printing. The fully inkjet printing process possesses the advantages of direct patterning and low-cost. It does not require photolithography and etching processes since the pattern is directly printed on the flexible aluminum sheet. -

Study in Taiwan - 7% Rich and Colorful Culture - 15% in Taiwan, Ancient Chinese Culture Is Uniquely Interwoven No.7 in the Fabric of Modern Society
Le ar ni ng pl us a d v e n t u r e Study in Foundation for International Cooperation in Higher Education of Taiwan (FICHET) Address: Room 202, No.5, Lane 199, Kinghua Street, Taipei City, Taiwan 10650, R.O.C. Taiwan Website: www.fichet.org.tw Tel: +886-2-23222280 Fax: +886-2-23222528 Ministry of Education, R.O.C. Address: No.5, ZhongShan South Road, Taipei, Taiwan 10051, R.O.C. Website: www.edu.tw www.studyintaiwan.org S t u d y n i T a i w a n FICHET: Your all – inclusive information source for studying in Taiwan FICHET (The Foundation for International Cooperation in Higher Education of Taiwan) is a Non-Profit Organization founded in 2005. It currently has 114 member universities. Tel: +886-2-23222280 Fax: +886-2-23222528 E-mail: [email protected] www.fichet.org.tw 加工:封面全面上霧P 局部上亮光 Why Taiwan? International Students’ Perspectives / Reasons Why Taiwan?1 Why Taiwan? Taiwan has an outstanding higher education system that provides opportunities for international students to study a wide variety of subjects, ranging from Chinese language and history to tropical agriculture and forestry, genetic engineering, business, semi-conductors and more. Chinese culture holds education and scholarship in high regard, and nowhere is this truer than in Taiwan. In Taiwan you will experience a vibrant, modern society rooted in one of world’s most venerable cultures, and populated by some of the most friendly and hospitable people on the planet. A great education can lead to a great future. What are you waiting for? Come to Taiwan and fulfill your dreams. -

OCLC Update Luncheon Online Information 2002 December 3
OCLC Online Computer Library Center OCLC CJK User Group –April 8, 2006 OCLC Online Computer Library Center Congratulations on 20 years of cooperation! CJK Records in WorldCat 1986 80,000 2006 2,849,000 1.3 m Chinese 1.3 m Japanese 200 k Korean OCLC Online Computer Library Center WorldCat Gold Records OCLC Online Computer Library Center Making WorldCat More Global Waseda University—1.5 million records Singapore National Union Catalog—1.4 million records Harvard YenChing Library—325,000 records Hong Kong Chinese Authority File (HKCA-N)— 130,000 Chinese records 2005 WorldCat/RLIN Record Exchange—225,771 OCLC Online Computer Library Center WorldCat—Original Records 134, 531 University of Hong Kong 78,773 UC Berkeley 45,593 UCLA 45, 396 University of Washington 33,057 The Ohio State University 20,120 University of Pittsburgh OCLC Online Computer Library Center 1 Billion—11 August 2005 OCLC Online Computer Library Center OCLC Participants OCLC Online Computer Library Center Perceptions of Libraries and Information Resources OCLC Online Computer Library Center Migration Update OCLC Online Computer Library Center OCLC Online Computer Library Center Since July 2005 WorldCat script support: Connexion: Cyrillic Local holdings maintenance Greek MARC 21 Format for Hebrew Holdings Data Thai FirstSearch Tamil Dissertations & theses database OCLC Online Computer Library Center On the horizon Baker & Taylor—OCLC cataloging records Content cooperative pilot Remote circulation pilot OCLC Online Computer Library Center Terminologies Service -

Editorial Chih-Cheng Tseng* Sungyoung Lee Neeli Rashmi
Int. J. Sensor Networks, Vol. 10, Nos. 1/2, 2011 1 Editorial Chih-Cheng Tseng* Department of Electrical Engineering, National Ilan University, Yi-Lan, Taiwan Email: [email protected] *Corresponding author Sungyoung Lee Department of Computer Engineering, Kyung Hee University, Global Campus, Seocheon-dong, Giheung-gu, Yongin-si, Gyeonggi-do, South Korea Email: [email protected] Neeli Rashmi Prasad Center for TeleInfrastruktur (CTIF) Aalborg University, Aalborg, Denmark Email: [email protected] Michał Wódczak Telcordia Technologies, Inc., ul. Umultowska 85, 61–614 Poznań, Poland Email: [email protected] Biographical notes: Chih-Cheng Tseng received his BS and MS from the National Taiwan University of Science and Technology, Taipei, Taiwan, in 1994 and 1997 respectively, all in Electronic Engineering. He received his PhD from the Graduate Institute of Communications Engineering, National Taiwan University, Taipei, Taiwan in 2007. He is currently an Assistant Professor of the Department of Electrical Engineering, National Ilan University, Yi-Lan, Taiwan. His research interests include the design and performance evaluation of protocols for mobile communications and wireless ad hoc/sensor networks. Sungyoung Lee received his BS from Korea University, Seoul, Korea. He got his MS and PhD degrees in Computer Science from Illinois Institute of Technology (IIT), Chicago, Illinois, USA in 1987 and 1991 respectively. He has been a Professor in the Department of Computer Engineering, Kyung Hee University, Korea since 1993. He is a founding director of the Ubiquitous Computing Laboratory, and has been affiliated with a director of Neo Medical ubiquitous-Life Care Information Technology Research Center, Kyung Hee University since 2006. -
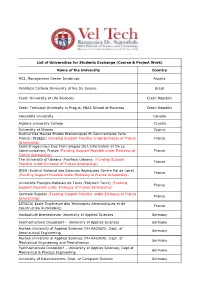
List of Universities Possible (For Students Exchange Or Mobility)
List of Universities for Students Exchange (Course & Project Work) Name of the University Country MCI, Management Center Innsbruck Austria Pontifical Catholic University of Rio De Janerio Brazil Czech University of Life Sciences Czech Republic Czech Technical University in Prague, MIAS School of Business Czech Republic Concordia University Canada Algebra University College Croatia University of Nicosia Cyprus Institut Des Hautes Etudes Economiques Et Commerciales Paris France (INSEEC) (Funding Support Possible under Embassy of France France Scholarship) Ecole D'ingennieur Des Technologies De L'information Et De La Communication, France (Funding Support Possible under Embassy of France France Scholarship) The University of Orleans (Polytech Orleans) (Funding Support France Possible under Embassy of France Scholarship) INSA (Institut National des Sciences Appliquees Centre Val de Loire) France (Funding Support Possible under Embassy of France Scholarship) Université François-Rabelais de Tours (Polytech Tours) (Funding France Support Possible under Embassy of France Scholarship) Centrale Supelec (Funding Support Possible under Embassy of France France Scholarship) ESTACA( Ecole Supérieure des Techniques Aéronautiques et de France Construction Automobile) Hochschule Bremerhaven University of Applied Sciences Germany Fachhochschule Dusseldorf – University of Applied Sciences Germany Aachen University of Applied Sciences (FH AACHEN), Dept. of Germany Aeronautical Engineering Aachen University of Applied Sciences (FH AACHEN), Dept. of Germany -

The Rankings of Research Funding Among Universities in Taiwan
Mar. 2010, Volume 7, No.3 (Serial No.64) US-China Education Review, ISSN 1548-6613, USA The rankings of research funding among universities in Taiwan WANG Ru-Jer (Department of Education, Graduate Institute of Educational Policy and Administration, National Taiwan Normal University, Taipei 106, Taiwan) Abstract: With the current trend that universities around the world have gradually stepped into higher education systems of popularization, there has been more diversity in universities; hence it has become necessary to increase the transparency of university governance. Since that university classification or university ranking is a powerful mechanism to demonstrate the diversity of an institute, the rankings of research funding have become desirable and also of great value. The main purpose of this study is to analyze the rankings of research funding among universities in Taiwan, and make relevant suggestions based on the findings. A secondary data analysis was conducted on the data obtained from the database of National Science Council, in order to develop the rankings of research funding among 164 universities in Taiwan. Based on the results, the conclusions are as follows: (1) The top three universities which won the funding of the National Science Council Research Project with the best overall strength were National Taiwan University, National Cheng Gung University, and National Chiao Tung University; (2) The top three universities which won the funding of the National Science Council Research Project with the best average faculty strength were National Tsing Hua University, National Chiao Tung University, and National Taiwan University. It is suggested that, when rating the strength of a university to win the research funding, both overall strength and average faculty strength should be considered to avoid the unfairness towards universities of smaller scale. -

Stack Overflow Considered Harmful? the Impact of Copy&Paste On
Organizing Committee of IEEE AINA-2012 General Co-Chairs Takuo Nakashima, Tokai University, Japan Hui-Huang Hsu, Tamkang University, Taiwan Wenny Rahayu, La Trobe University, Australia Program Committee Co-Chairs Tomoya Enokido, Rissho University, Japan Markus Aleksy, ABB AG, Germany Jong Hyuk Park, Seoul National University of Science and Technology (SeoulTech), Korea Workshops Co-Chairs Fatos Xhafa, Technical University of Catalonia, Spain Minoru Uehara, Toyo University, Japan David Taniar, Monash University, Australia Sang-Soo Yeo, Mokwon University, Korea Program Vice Chairs and Research Tracks 1. Opportunistic and Delay Tolerant Networks Stephane Maag, TELECOM SudParis, France Jung-Shian Li, National Cheng Kung University, Taiwan 2. Ad Hoc, Mesh and Sensor Networks Han-Chieh Chao, National Ilan University, Taiwan Sherali Zeadally, University of the District of Columbia, USA Whai-En Chen, National Ilan University, Taiwan 3. Pervasive/Ubiquitous Computing and Services Mikko Rissanen, ABB Corporate Research, Sweden Joseph Kee-Yin Ng, Hong Kong Baptist University, Hong Kong 4. Vehicular Networks and Applications Vamsi Krishna Paruchuri, University of Central Arkansas, USA Hiroshi Shigeno, Keio University, Japan 5. Distributed and Parallel Systems Cho-Li Wang, University of Hong Kong, Hong Kong Anne Benoit, ENS Lyon et IUF, France Weisong Shi, Wayne State University, USA 6. Distributed Database and Data Mining Akimitsu Kanzaki, Osaka University, Japan Eric Pardede, La Trobe University, Australia xxii 7. Grid, P2P and Scalable Computing Heinz Kredel, University of Mannheim, Germany Hanh Le, University of Cape Town, South Africa 8. Internet Computing and Web Applications Yuka Kato, Advanced Institute of Industrial Technology, Japan Ralf Gitzel, ABB Corporate Research Center, Germany 9. -

The Effect of Tertiary Education Expansion on Fertility: a Note on Identification
DISCUSSION PAPER SERIES IZA DP No. 14672 ‘Bachelors’ and Babies: The Effect of Tertiary Education Expansion on Fertility Tushar Bharati Simon Chang Qing Li AUGUST 2021 DISCUSSION PAPER SERIES IZA DP No. 14672 ‘Bachelors’ and Babies: The Effect of Tertiary Education Expansion on Fertility Tushar Bharati Qing Li University of Western Australia Business Shanghai University School Simon Chang University of Western Australia Business School and IZA AUGUST 2021 Any opinions expressed in this paper are those of the author(s) and not those of IZA. Research published in this series may include views on policy, but IZA takes no institutional policy positions. The IZA research network is committed to the IZA Guiding Principles of Research Integrity. The IZA Institute of Labor Economics is an independent economic research institute that conducts research in labor economics and offers evidence-based policy advice on labor market issues. Supported by the Deutsche Post Foundation, IZA runs the world’s largest network of economists, whose research aims to provide answers to the global labor market challenges of our time. Our key objective is to build bridges between academic research, policymakers and society. IZA Discussion Papers often represent preliminary work and are circulated to encourage discussion. Citation of such a paper should account for its provisional character. A revised version may be available directly from the author. ISSN: 2365-9793 IZA – Institute of Labor Economics Schaumburg-Lippe-Straße 5–9 Phone: +49-228-3894-0 53113 Bonn, Germany -

Kenneth Smith
Kenneth Smith Title Lecturer Extension 5347 number E-mail [email protected] M.Ed. in Second Language Education, University of Massachusetts, USA. Education Current PhD Candidate in School of Linguistics and Applied Language Studies (LALS) Victoria University of Wellington, New Zealand Wenzao Ursuline University of Languages Kaohsiung, Taiwan August 2000 – present Nanhua University Chiayi, Taiwan August 1999 – July 2000 Experience University of Massachusetts/Amherst International Programs Office Intensive English Program Amherst, Massachusetts September 1996 – May 1999 5-Year Junior College English Reading and Writing (2) Practical English Writing I Current 5 Year Junior College – Honors Program English Reading and Writing (2) courses English Listening and Conversation 4-Year College – Evening School Selected English Readings Second Language Acquisition Specialization Extensive Reading Journal Articles: Krashen, S., Mason, B., and Smith, K. (2014). Can We Increase the Power of Reading by Adding Communicative Output Activities? A Comment on Song and Sardegna (2014). RELC Journal , 45(2), pp. 211-212. [Can We Increase the Power of Reading by Adding Communicative Output Activities? A Comment on Song and Sardegna (2014).] Smith, K. (2012a). A Comparison Study of Pure Extensive Reading, Intensive Reading, and Extensive Reading with Supplementation. (Originally published under the title, A Comparison of “Pure” Extensive Reading with Supplemental Activities; IJFLT, Fall 2006, Vol. 2, Num. 2 ). In K.S. Cho, S. Krashen, SY Lee, B, Mason, and K. Smith (Eds.), SSR in Asia: Empirical studies of sustained silent reading in English as a foreign language pp. 24-28. Language Magazine. Retrieved from http://languagemagazine.com/?page_id=4273 [A Comparison Study of Pure Extensive Reading, Intensive Reading, and Extensive Reading with Supplementation.] Smith, K. -

List of Reviewers 2018
78 List of Reviewers 2018 We gratefully acknowledge the contribution of the following reviewers who reviewed papers for Research in Journal of Marine Science and Technology in 2018. Alberto Magreñán, University of La Rioja, Spain Apostolos D. Papanikolaou, National Technical University of Athens, Greece Bao-Shi Shiau, National Taiwan Ocean University, Taiwan (R.O.C.) Beom-Seon Jang, Seoul National University, Korea Bin Ji, Huazhong University Science and Technology, China Bo Zhou, Nanyang Technological University, Singapore Chen-Far Hung, National Taiwan University, Taiwan (R.O.C.) Cheng-Chi Chung, National Taiwan Ocean University, Taiwan (R.O.C.) Cheng-Wen Lin, China Corporation Register of Shipping (CR), Taiwan (R.O.C.) Cheng-Yi Chen, Cheng Shiu University, Taiwan (R.O.C.) Cheng-Yu Ku, National Taiwan Ocean University, Taiwan (R.O.C.) Chen-Huei Huang, National Chiayi University, Taiwan (R.O.C.) Chen-Ming Chu, National Iland Univerisity, Taiwan (R.O.C.) Cheung-Chieh Ku, National Taiwan Ocean University, Taiwan (R.O.C.) Chia Hao Chang, Tonghai University, Taiwan (R.O.C.) Chia-Chi Sung, National Taiwan University, Taiwan (R.O.C.) Chia-Ming Fan, National Taiwan Ocean University, Taiwan (R.O.C.) Chien-Chang Chou, National Kaohsiung University of Science and Technology, Taiwan (R.O.C.) Chien-Kuei Yang, Ming Chuan University, Taiwan (R.O.C.) Chih-Min Hsieh, National Kaohsiung University of Science and Technology, Taiwan (R.O.C.) Chih-Wei Yen, Industrial Technology Research Institute of Taiwan, R.O.C, Taiwan (R.O.C.) Ching-Hsiang Tseng, National -

Invited Speakers: Organizers: Contact
2020 NCTS Workshopon analysis and its applications in biology and physiology Date: 1/2-4/2020 Venue: R440, Astro-Math Bldg. Conventionally, analysis plays a crucial role to justify PDE (partial differential equation) models which come from various fields of biology and physiology. However, due to the complexity of recent achievements in bio- logical networks, protein structures and complex fluids, traditional PDE models are not sufficient to fit the need and new mathematical models have to be developed. Analytical techniques of variational and statisti- cal methods may provide tools to derive mathematical models for the studies of structural bioinformatics, drug discovery and data mining. The main goal of the workshop is to discuss the biological models of PDE, the solving methods (analytical and numerical methods) and the relation of mathematical results and bio- logical significance. The workshop will give an opportunity for researchers in related areas to share and dis- cuss their current research ideas. Invited Speakers: Luigi Catacuzzeno University of Perugia Shu-Wei Chang National Taiwan University Chiun-Chuan Chen National Taiwan University Ren-Shiang Chen Tunghai University Cheng-Ying Chou National Taiwan University Tom Chou University of California Los Angeles Maria Rita D'Orsogna California State University at Northridge Bob Eisenberg Rush University Nir Gavish Israel Institute of Technology Tzyy-Leng Horng Feng Chia University Chun-Hsiung Hsia National Taiwan University Chia-Yu Hsieh The Chinese University of Hong Kong Chiun-Chang