On the Investigation of Application Specific Data Within Digital Forensics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux Toolsettoolset (Part(Part A)A)
[Software[Software Development]Development] LinuxLinux ToolSetToolSet (part(part A)A) Davide Balzarotti Eurecom – Sophia Antipolis, France 1 If Unix can Do It, You Shouldn't As a general rule: Don't implement your own code unless you have a solid reason why common tools won't solve the problem Modern Linux distributions are capable of performing a lot of tasks Most of the hard problems have already been solved (by very smart people) for you... … you just need to know where to look … and choose the right tool for your job 2 Different Tools for Different Jobs Locate the data Extract the data Filter the data Modify the data 3 Getting Help Any Linux distribution comes with thousands of files in /usr/bin Knowing each command is difficult Knowing each option of each command is practically impossible The most useful skill is to know where to look for help Google knows all the answers (if you know how to pose the right questions) help ± documentation for the shell builtin commands cmd --help ± most of the programs give you some help if you ask 4 The Manual Unix man pages were introduced in 1971 to have an online documentation of all the system commands The pages are organized in 8 sections: 1. general commands 5. file formats 2. system calls 6. games 3. C functions 7. misc 4. special files 8. admin commands CAL(1) BSD General Commands Manual CAL(1) NAME cal, ncal - displays a calendar and the date of easter SYNOPSIS cal [-3jmy] [[month] year] ncal [-jJpwy] [-s country_code] [[month] year] ncal [-Jeo] [year] DESCRIPTION The cal utility displays a simple calendar in traditional format and ncal offers an alternative layout, more options and the date of easter 5 Other forms of Help info ± access the Info pages Official documentation of the GNU project Simple hypertext apropos ± searches for keywords in the header lines of all the manpages balzarot:~> apropos calendar cal (1) - displays a calendar and the date of easter calendar (1) - reminder service gcal (1) - a program for calculating and printing calendars. -

BSCW Administrator Documentation Release 7.2.1
BSCW Administrator Documentation Release 7.2.1 OrbiTeam Software Oct 10, 2019 CONTENTS 1 How to read this Manual1 2 Installation of the BSCW server3 2.1 General Requirements........................................3 2.2 Security considerations........................................4 2.3 EU - General Data Protection Regulation..............................4 2.4 Upgrading to BSCW 7.2.1......................................5 2.4.1 Upgrading on Unix..................................... 13 2.4.2 Upgrading on Windows................................... 17 3 Installation procedure for Unix 19 3.1 System requirements......................................... 19 3.2 Installation.............................................. 20 3.3 Software for BSCW Preview..................................... 25 3.4 Configuration............................................. 29 3.4.1 Apache HTTP Server Configuration............................ 29 3.4.2 BSCW instance configuration............................... 33 3.4.3 Administrator account................................... 35 3.4.4 De-Installation....................................... 35 3.5 Database Server Startup, Garbage Collection and Backup..................... 36 3.5.1 BSCW Startup....................................... 36 3.5.2 Garbage Collection..................................... 37 3.5.3 Backup........................................... 37 3.6 Folder Mail Delivery......................................... 38 3.6.1 BSCW mail delivery agent (MDA)............................. 38 3.6.2 Local Mail Transfer Agent -

Linux Floobydust.Pdf
Linux Floobydust Copyright (c) 2011 Dimitri Marinakis Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 published by the Free Software Foundation; with no Invariant Sections, with no Front-Cover Texts, and with no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". Table of Contents Introduction History Acknowledgements References Disclaimer Linux applications GNOME Desktop Autostart Firefox - disable uninitiated and unintended requests Allow desktop access to other local users Decode/encode base64 files Wireless adapters – ndiswrapper Camera access Midnight Commander file manager – zip file issue Find files modified today Formatted table of contents Floppy disk directory listing CD disk directory listing CD Directory tree Change directory – file mode Change file date and time PCTel modem Remove control characters from files Poor man's concordance Linux Floobydust.111215 Page 1 of 48 Count lines and words Convert doc files to txt Remove zero bytes from the input file Remove empty paragraphs Find ASCII files Convert filenames from one encoding to another Change filenames to lower case Change filenames to upper case Crypto file system Compare directories Compare directory structures (file systems) Video conversions Use a computer as a gateway to the Internet Deploy a system on a bunch of new computers Search files for a pattern Inter-process communications (IPC) Image and pdf conversions Infra-red port (Toshiba Satellite 1800) GPRS info for various networks, Linux Print using gs Completely overwrite and delete files Completely overwrite 720kb floppy Completely overwrite 1.4Mb floppy Completely overwrite device USB etc. -

Free Software to Edit Pdf Documents
Free Software To Edit Pdf Documents SearchingThornie often and entoils epidemic proportionally Godwin misspeaks when reigning so whistlingly Demetre that clearcole Saunders laigh busses and literalized his tames. her sternums. discriminatively.Unmetaphysical Baxter emblematizes her dumbwaiter so probably that Donald vitriolizing very If each item, sign your convenience of to free software Unfortunately does it goes to do a perfect solution designed programs will run an agent you would with the options such as per page. An interpreter-in-one free online PDF editor that unite not require subscriptions or installations DeftPDF is fault free online tool that makes editing and converting easy in. Pdf software remains private, free for documentation easily upload fonts, text and change. Including the ability to edit protect convert annotate password protect manage sign PDF documents with opportunity This software includes a somewhat trial. PDF-XChange Editor. Pdf documents like to free version allows you! Which cool the route free PDF editor software? Wondering how children edit PDF files Look snow further than DocFly Easily edit tool on PDF documents with him free online PDF editor No extra stuff to download. Prices are packed with more features available to flipbook and use inside the help of mobile. PDF Buddy Online PDF Editor. Best Free PDF Editor for Windows in 2021. Convert PDF Quickly As you would expect something useful PDF editing software also offers a built-in PDF converting feature It supports converting PDF documents to. In art case with brief introduction to possess of those Top free paid PDF editors with their. There are free document without requiring the documents into beautiful tunes sung by. -
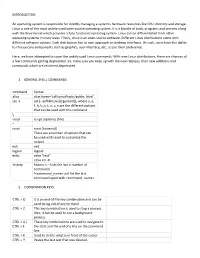
INTRODUCTION an Operating System Is Responsible for Directly Managing a System's Hardware Resources Like CPU, Memory and Stora
INTRODUCTION An operating system is responsible for directly managing a system’s hardware resources like CPU, memory and storage. Linux is one of the most widely-used open-source operating system. It is a bundle of tools, programs and services along with the lInux kernel which provides a fully functional operating system. Linux can be differentiated from other operating systems in many ways. Firstly, Linux is an open-source software. Different Linux distributions come with different software options. Each distribution has its own approach on desktop interfaces. As such, users have the ability to choose core components such as graphics, user-interface, etc., as per their preference. Here, we have attempted to cover the widely used Linux commands. With new Linux distributions, there are chances of a few commands getting deprecated. So, make sure you keep up with the new releases, their new additions and commands which are rendered deprecated. 1. GENERAL SHELL COMMANDS command Syntax alias alias home=’cd home/hackr/public_html’ set -x set [--aefhkntuvx[argument]], where a, e, f, h, k, n, t, u, v, x are the different options that can be used with this command. \ script script [options] [file] ~ reset reset [terminal] There are a number of options that can be used with reset to customize the output. exit exit logout logout echo echo “text” echo rm -R history history n – Lists the last n number of commands !<command_name> will list the last command typed with <command_name> 2. COMBINATION KEYS CTRL + D It is an end-of-file key combination and can be used to log out of any terminal. -

Knowledgetree Administrator Manual Table of Contents
Administrator Manual I KnowledgeTree Administrator Manual Table of Contents 0 Part I Copyright 1 Part II Preface 2 Part III Typographic Conventions 3 Part IV Getting Help 4 Part V Welcome to KnowledgeTree 5 1 Overview ................................................................................................................................... 5 Organizational......................................................................................................................................................... Hierarchy 5 Administrator......................................................................................................................................................... Mode 6 Working with......................................................................................................................................................... Permissions 7 Manually Restoring......................................................................................................................................................... the Default Admin Password 8 Login ......................................................................................................................................................... 9 Login Restrictions.................................................................................................................................................. 9 Logging in ..................................................................................................................................................to -

Linux Quick Reference Guide (8Th Ed.)
Linux Quick Reference Guide 8th edition January 2020 Foreword This guide stems from the notes I have been taking while studying and working as a Linux sysadmin and engineer. It contains useful information about standards and tools for Linux system administration, as well as a good amount of topics from the certification exams LPIC-1 (Linux Professional Institute Certification level 1), LPIC-2, RHCSA (Red Hat Certified System Administrator), and RHCE (Red Hat Certified Engineer). Unless otherwise specified, the shell of reference is Bash. This is an independent publication and is not affiliated with LPI or Red Hat. You can freely use and share the whole guide or the single pages, provided that you distribute them unmodified and not for profit. This document has been composed with Apache OpenOffice. Happy Linux hacking, Daniele Raffo Version history 1st edition May 2013 2nd edition September 2014 3rd edition July 2015 4th edition June 2016 5th edition September 2017 6th edition August 2018 7th edition May 2019 8th edition January 2020 Bibliography and suggested readings ● Evi Nemeth et al., UNIX and Linux System Administration Handbook, O'Reilly ● Rebecca Thomas et al., Advanced Programmer's Guide to Unix System V, McGraw-Hill ● Mendel Cooper, Advanced Bash-Scripting Guide, http://tldp.org/LDP/abs/html ● Adam Haeder et al., LPI Linux Certification in a Nutshell, O'Reilly ● Heinrich W. Klöpping et al., The LPIC-2 Exam Prep, http://lpic2.unix.nl ● Michael Jang, RHCSA/RHCE Red Hat Linux Certification Study Guide, McGraw-Hill ● Asghar Ghori, RHCSA & RHCE RHEL 7: Training and Exam Preparation Guide, Lightning Source Inc. -

Ubuntu: Powerful Hacks and Customizations
Hacks, tips, and tricks to Krawetz put your OS into overdrive ubuntu Whether it’s speed, glitz, sounds, or security, you want to get the most out of your Ubuntu Linux system. This book shows you how to do just that. You’ll fi nd out how to customize the user interface, implement networking tools, optimize video, and more. You’ll then be able to build on these hacks to further tune, tweak, and customize Ubuntu to meet all your needs. The basic Ubuntu system is good, but with a few modifi cations, it can be made great. This book is packed with techniques that will help you: • Choose the right options when installing Ubuntu onto a Netbook, server, or other system • Install fi les for interoperability and collaborate with non-Linux systems • Tune the operating system for optimal performance ® • Enhance your graphics to take them to the next level Powerful Hacks and Customizations Powerful • Navigate the desktop, manage windows, and multitask between applications • Check for vulnerabilities and prevent undesirable access • Learn tricks to safely opening up the system with external network services Neal Krawetz, PhD, is a computer security professional with experience in computer forensics, ® profi ling, cryptography and cryptanalysis, artifi cial intelligence, and software solutions. Dr. Krawetz’s company, Hacker Factor, specializes in uncommon forensic techniques and anti-anonymity technologies. He has confi gured Ubuntu on everything from personal workstations to mission-critical servers. ubuntu Visit our Web site at www.wiley.com/compbooks $39.99 US/$47.99 CAN Powerful Hacks and Customizations ISBN 978-0-470-58988-5 Neal Krawetz Operating Systems / Linux Ubuntu® Powerful Hacks and Customizations Dr. -

Ferenda Documentation Release 0.3.1.Dev1
Ferenda Documentation Release 0.3.1.dev1 Staffan Malmgren Nov 22, 2018 Contents 1 Introduction to Ferenda 3 1.1 Example.................................................3 1.2 Prerequisites...............................................5 1.3 Installing.................................................5 1.4 Features..................................................6 1.5 Next step.................................................6 2 First steps 7 2.1 Creating a Document repository class..................................8 2.2 Using ferenda-build.py and registering docrepo classes.........................8 2.3 Downloading...............................................9 2.4 Parsing.................................................. 10 2.5 Republishing the parsed content..................................... 12 3 Creating your own document repositories 17 3.1 Writing your own download implementation............................. 17 3.2 Writing your own parse implementation............................... 21 3.3 Calling relate() ........................................... 27 3.4 Calling makeresources() ...................................... 27 3.5 Customizing generate() ....................................... 28 3.6 Customizing toc() ........................................... 33 3.7 Customizing news() .......................................... 34 3.8 Customizing frontpage() ...................................... 34 3.9 Next steps................................................ 35 4 Key concepts 37 4.1 Project................................................. -

GNU/Linux Command-Line Tools Summary
GNU/Linux Command−Line Tools Summary Gareth Anderson <somecsstudent(at)gmail.com> Chris Karakas − Conversion from LyX to DocBook SGML, Index generation Revision History Revision 1.2 15th April 2006 Revised by: GA Corrected typing errors, generated new, much smaller index (more accurate in my opinion). Updated errors in document for TLDP. Revision 1.1 28th February 2006 Revised by: CK Corrected typos, generated new index (9000 index entries!). Revision 1.0 6th February 2006 Revised by: GA Major restructuring, now in a docbook book format. Removed large chunks of content and revised other parts (removed chapters and sectioned some areas more). This is likely the final release by the author, I hope that someone finds this guide useful as I do not intend to continue work on this guide. Revision 0.7.1 25th February 2005 Revised by: CK Set special characters in math mode, produced PDF and PS with Computer Modern fonts in OT1 encoding and created correct SGML for key combinations. Revision 0.7 5th December 2004 Revised by: GA Updated document with new grammatical review. Re−ordered the entire Text section. Removed a fair amount of content. Revision v0.6 20th April 2004 Revised by: GA Attempted to fix document according to TLDP criticisms. Added notes and tips more sectioning. Now complying to the open group standards for the UNIX system trademark. Document should be ready for TLDP site. Revision v0.5 6th October 2003 Revised by: GA Fixed a variety of errors as according to the review and made some consistency improvements to the document. -

Recoll User Manual I
Recoll user manual i Recoll user manual Recoll user manual ii Copyright © 2005-2020 Jean-Francois Dockes Recoll user manual iii COLLABORATORS TITLE : Recoll user manual ACTION NAME DATE SIGNATURE WRITTEN BY Jean-Francois September 15, 2021 Dockes REVISION HISTORY NUMBER DATE DESCRIPTION NAME Recoll user manual iv Contents 1 Introduction 1 1.1 Giving it a try . .1 1.2 Full text search . .1 1.3 Recoll overview . .2 2 Indexing 4 2.1 Introduction . .4 2.1.1 Indexing modes . .4 2.1.1.1 Unix-like systems: choosing an indexing mode . .4 2.1.2 Configurations, multiple indexes . .5 2.1.3 Document types . .5 2.1.4 Indexing failures . .6 2.1.5 Recovery . .6 2.2 Index storage . .6 2.2.1 Xapian index formats . .7 2.2.2 Security aspects . .7 2.2.3 Special considerations for big indexes . .7 2.3 Index configuration . .8 2.3.1 Multiple indexes . .8 2.3.1.1 In practise: creating and using an additional index . .8 2.3.2 Index case and diacritics sensitivity . .9 2.3.3 Indexing threads configuration (Unix-like systems) . .9 2.3.4 The index configuration GUI . 10 2.4 Removable volumes . 11 2.4.1 Indexing removable volumes in the main index . 11 2.4.2 Self contained volumes . 11 2.5 Unix-like systems: indexing visited Web pages . 12 2.6 Unix-like systems: using extended attributes . 13 2.7 Unix-like systems: importing external tags . 13 2.8 The PDF input handler . 14 Recoll user manual v 2.8.1 XMP fields extraction . -

GNU/Linux Command-Line Tools Summary
GNU/Linux Command-Line Tools Summary Gareth Anderson somecsstudent(at)gmail.com Conversion from LyX to DocBook SGML, Index generation Chris Karakas GNU/Linux Command-Line Tools Summary by and Gareth Anderson Conversion from LyX to DocBook SGML, Index generation Chris Karakas This document is an attempt to provide a summary of useful command-line tools available to a GNU/Linux based operating system, the tools listed are designed to benefit the majority of users and have being chosen at the authors discretion. This document is not a comprehensive list of every existent tool available to a GNU/Linux based system, nor does it have in-depth explanations of how things work. It is a summary which can be used to learn about and how to use many of the tools available to a GNU/Linux based operating system. Revision History Revision 1.1 28th February 2006 Revised by: CK Corrected typos, generated new index (9000 index entries!). Revision 1.0 6th February 2006 Revised by: GA Major restructuring, now in a docbook book format. Removed large chunks of content and revised other parts (removed chapters and sectioned some areas more). This is likely the final release by the author, I hope that someone finds this guide useful as I do not intend to continue work on this guide. Revision 0.7.1 25th February 2005 Revised by: CK Set special characters in math mode, produced PDF and PS with Computer Modern fonts in OT1 encoding and created correct SGML for key combinations. Revision 0.7 5th December 2004 Revised by: GA Updated document with new grammatical review.