Attention Spanned: Comprehensive Vulnerability Analysis of at Commands Within the Android Ecosystem Dave (Jing) Tian, Grant Hernandez, Joseph I
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Product ID Product Type Product Description Notes Price (USD) Weight (KG) SKU 10534 Mobile-Phone Apple Iphone 4S 8GB White 226.8
Rm A1,10/F, Shun Luen Factory Building, 86 Tokwawan Road, Hong Kong TEL: +852 2325 1867 FAX: +852 23251689 Website: http://www.ac-electronic.com/ For products not in our pricelist, please contact our sales. 29/8/2015 Product Price Weight Product Type Product Description Notes SKU ID (USD) (KG) 10534 mobile-phone Apple iPhone 4S 8GB White 226.8 0.5 40599 10491 mobile-phone Apple iPhone 5s 16GB Black Slate 486.4 0.5 40557 10497 mobile-phone Apple iPhone 5s 16GB Gold 495.6 0.5 40563 10494 mobile-phone Apple iPhone 5s 16GB White Silver 487.7 0.5 40560 10498 mobile-phone Apple iPhone 5s 32GB Gold 536.3 0.5 40564 11941 mobile-phone Apple iPhone 6 128GB Gold 784.1 0.5 41970 11939 mobile-phone Apple iPhone 6 16GB Gold 622.8 0.5 41968 11936 mobile-phone Apple iPhone 6 16GB Silver 633.3 0.5 41965 11942 mobile-phone Apple iPhone 6 16GB Space Grey 618.9 0.5 41971 11940 mobile-phone Apple iPhone 6 64GB Gold 705.4 0.5 41969 11937 mobile-phone Apple iPhone 6 64GB Silver 706.7 0.5 41966 11943 mobile-phone Apple iPhone 6 64GB Space Grey 708 0.5 41972 11963 mobile-phone Apple iPhone 6 Plus 128GB Silver 917.9 1 41991 11955 mobile-phone Apple iPhone 6 Plus 16GB Gold 755.3 1 41983 11961 mobile-phone Apple iPhone 6 Plus 16GB Silver 731.6 1 41989 11958 mobile-phone Apple iPhone 6 Plus 16GB Space Grey 735.6 1 41986 11956 mobile-phone Apple iPhone 6 Plus 64GB Gold 843.1 1 41984 11962 mobile-phone Apple iPhone 6 Plus 64GB Silver 841.8 1 41990 11959 mobile-phone Apple iPhone 6 Plus 64GB Space Grey 840.5 1 41987 12733 mobile-phone ASUS ZenFone 2 ZE550ML Dual SIM -

Enabling Musical Applications on a Linux Phone
University of Wollongong Research Online Faculty of Creative Arts - Papers (Archive) Faculty of Arts, Social Sciences & Humanities 2009 Enabling Musical Applications On A Linux Phone Greg Schiemer University of Wollongong, [email protected] E. Chen Royal Melbourne Institute of Technology Follow this and additional works at: https://ro.uow.edu.au/creartspapers Part of the Arts and Humanities Commons, and the Social and Behavioral Sciences Commons Recommended Citation Schiemer, Greg and Chen, E.: Enabling Musical Applications On A Linux Phone 2009. https://ro.uow.edu.au/creartspapers/36 Research Online is the open access institutional repository for the University of Wollongong. For further information contact the UOW Library: [email protected] ENABLING MUSICAL APPLICATIONS ON A LINUX PHONE Greg Schiemer Eva Cheng Sonic Arts Research Network School of Electrical and Computer Faculty of Creative Arts Engineering University of Wollongong RMIT Melbourne 2522 3000 The prospect of using compiled Arm9 native code of- fers a way to synthesise music using generic music soft- ABSTRACT ware such as Pure data and Csound rather than interpre- tive languages like java and python which have been Over the past decade the mobile phone has evolved to used in mobile devices [1, 2]. A similar approach to mo- become a hardware platform for musical interaction and bile synthesis has been adopted using the Symbian oper- is increasingly being taken seriously by composers and ating system [3]. instrument designers alike. Its gradual evolution has seen The Linux environment is more suited to the devel- improvements in hardware architecture that require al- opment of new applications in embedded hardware than ternative methods of programming. -
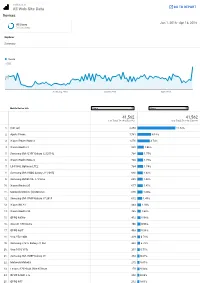
Web Site Data 41562 41562
auditguru.in All Web Site Data GO TO REPORT Devices Jan 1, 2018 - Apr 16, 2018 All Users 78.52% Users Explorer Summary Users 1,500 750 February 2018 March 2018 April 2018 Mobile Device Info Users Users 41,562 41,562 % of Total: 78.14% (53,186) % of Total: 78.14% (53,186) 1. (not set) 4,853 11.52% 2. Apple iPhone 1,761 4.18% 3. Xiaomi Redmi Note 4 1,576 3.74% 4. Xiaomi Redmi 4 825 1.96% 5. Samsung SM-J210F Galaxy J2 (2016) 736 1.75% 6. Xiaomi Redmi Note 3 736 1.75% 7. LG F160L Optimus LTE2 734 1.74% 8. Samsung SM-J200G Galaxy J2 (2015) 686 1.63% 9. Samsung SM-G610F J7 Prime 685 1.63% 10. Xiaomi Redmi 3S 677 1.61% 11. Motorola Moto G (4) Moto G4 676 1.60% 12. Samsung SM-J700F Galaxy J7 2015 612 1.45% 13. Xiaomi Mi A1 463 1.10% 14. Xiaomi Redmi 4A 435 1.03% 15. OPPO A37fw 412 0.98% 16. Acer A1-850 Iconia 406 0.96% 17. OPPO A37f 403 0.96% 18. Vivo Y53 1606 329 0.78% 19. Samsung J701F Galaxy J7 Nxt 328 0.78% 20. Vivo 1610 Y55s 315 0.75% 21. Samsung SM-J500F Galaxy J5 283 0.67% 22. Motorola MotoG3 272 0.65% 23. Lenovo A7020a48 Vibe K5 Note 270 0.64% 24. OPPO A1601 F1s 266 0.63% 25. OPPO A57 252 0.60% 26. Lenovo A6000 247 0.59% 27. Lenovo K33a42 Vibe K6 Power 245 0.58% 28. -

Android Operating System
Software Engineering ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, 2012, pp.-10-13. Available online at http://www.bioinfo.in/contents.php?id=76 ANDROID OPERATING SYSTEM NIMODIA C. AND DESHMUKH H.R. Babasaheb Naik College of Engineering, Pusad, MS, India. *Corresponding Author: Email- [email protected], [email protected] Received: February 21, 2012; Accepted: March 15, 2012 Abstract- Android is a software stack for mobile devices that includes an operating system, middleware and key applications. Android, an open source mobile device platform based on the Linux operating system. It has application Framework,enhanced graphics, integrated web browser, relational database, media support, LibWebCore web browser, wide variety of connectivity and much more applications. Android relies on Linux version 2.6 for core system services such as security, memory management, process management, network stack, and driver model. Architecture of Android consist of Applications. Linux kernel, libraries, application framework, Android Runtime. All applications are written using the Java programming language. Android mobile phone platform is going to be more secure than Apple’s iPhone or any other device in the long run. Keywords- 3G, Dalvik Virtual Machine, EGPRS, LiMo, Open Handset Alliance, SQLite, WCDMA/HSUPA Citation: Nimodia C. and Deshmukh H.R. (2012) Android Operating System. Software Engineering, ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, pp.-10-13. Copyright: Copyright©2012 Nimodia C. and Deshmukh H.R. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. -

Openmoko Is Dead. Long Live Openphoenux!
Openmoko is dead. Long live OpenPhoenux! Nikolaus Schaller, Lukas Märdian LinuxTag, Berlin, May 26th, 2012 Agenda Part one: some history Part two: a long way home Part three: rising from the ashes Part four: flying higher Part five: use it as daily phone – software Q&A Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 2 Some history – Past iterations • FIC GTA01 – Neo 1973 – Roughly 3.000 units sold – Production discontinued • Openmoko GTA02 – Neo Freerunner – Roughly 15.000 units sold – Hardware revision v7 – Production discontinued Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 3 Some history – The End (of part I) • FIC and Openmoko got out • Strong community continues development • Golden Delicious taking the lead – Excellent support for existing devices – Shipping spare parts and add-ons – Tuned GTA02v7++ • Deep sleep fix (aka bug #1024) -> Improved standby time • Bass rework -> Improved sound quality Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 4 Agenda Part one: some history Part two: a long way home Part three: rising from the ashes Part four: flying higher Part five: use it as daily phone – software Q&A Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 5 A long way home How do we get to a new open mobile phone? – open kernel for big ${BRAND} – reverse eng. – order from some ${MANUFACTURER} – hope for openness – DIY, “Use the source, Luke!” Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 6 Using the source: Beagleboard Beagleboard – Full Linux support – Open schematics – Open layout – Expansion connectors – Lots of documentation – Components available Nikolaus Schaller, Lukas Märdian OpenPhoenux | GTA04 May 26th 2012 LinuxTag 2012 wiki.openmoko.org | www.gta04.org 7 In theory it could fit (Aug. -

An Analysis of Power Consumption in a Smartphone
An Analysis of Power Consumption in a Smartphone Josh Hildebrand Introduction l Mobile devices derive the energy required to operate from batteries that are limited by the size of the device. l The ability to manage energy usage requires a good understanding of where and how the energy is being used. l The advancing functionality of modern smartphones is increasing the pressure on battery lifetime, and increases the need for effective energy management. l Goal is to break down a modern smartphone and measure the power consumption of the devices major subsystems, under a range of usage scenarios. l Results from the breakdown of energy consumption will be validated against two additional mobile devices. l Finally, an analysis of the energy consumption will be performed, and an energy model will be created to allow us to model usage patterns. Methodology / Device Under Test l The approach is to take physical power measurements at the component level on a piece of real hardware. l Three elements to the experimental setup, the device under test, a hardware data acquisition (DAQ) system, and a host computer. l Device under test is the Openmoko Neo Freerunner 2.5G smartphone. Experimental Setup l To measure power to each component, supply voltage and current must be measured. l Current is measured by placing sense resistors on the power supply rails of each component. Resistors were selected such that the voltage drop did not exceed 10mV, less than 1% of the supply voltage. l Voltages were measured using a National Instruments PCI-6229 DAQ. Software l The device was running the Freerunner port of Android 1.5, using the Linux v2.6.29 kernel. -

A Survey Onmobile Operating System and Mobile Networks
A SURVEY ONMOBILE OPERATING SYSTEM AND MOBILE NETWORKS Vignesh Kumar K1, Nagarajan R2 (1Departmen of Computer Science, PhD Research Scholar, Sri Ramakrishna College of Arts And Science, India) (2Department of Computer Science, Assistant Professor, Sri Ramakrishna College Of Arts And Science, India) ABSTRACT The use of smartphones is growing at an unprecedented rate and is projected to soon passlaptops as consumers’ mobile platform of choice. The proliferation of these devices hascreated new opportunities for mobile researchers; however, when faced with hundreds ofdevices across nearly a dozen development platforms, selecting the ideal platform is often met with unanswered questions. This paper considers desirable characteristics of mobileplatforms necessary for mobile networks research. Key words:smart phones,platforms, mobile networks,mobileplatforms. I.INTRODUCTION In a mobile network, position of MNs has been changing due todynamic nature. The dynamic movements of MNs are tracked regularlyby MM. To meet the QoS in mobile networks, the various issuesconsidered such as MM, handoff methods, call dropping, call blockingmethods, network throughput, routing overhead and PDR are discussed. In this paper I analyse the five most popular smartphone platforms: Android (Linux), BlackBerry, IPhone, Symbian, and Windows Mobile. Each has its own set of strengths and weaknesses; some platforms trade off security for openness, code portability for stability, and limit APIs for robustness. This analysis focuses on the APIs that platforms expose to applications; however in practice, smartphones are manufactured with different physical functionality. Therefore certain platform APIs may not be available on all smartphones. II.MOBILITY MANAGEMENT IP mobility management protocols proposed by Alnasouri et al (2007), Dell'Uomo and Scarrone (2002) and He and Cheng (2011) are compared in terms of handoff latency and packet loss during HM. -

Factory Model Device Model
Factory Model Device Model Acer A1-713 acer_aprilia Acer A1-811 mango Acer A1-830 ducati Acer A3-A10 G1EA3 Acer A3-A10 mtk6589_e_lca Acer A3-A10 zara Acer A3-A20 acer_harley Acer A3-A20FHD acer_harleyfhd Acer Acer E320-orange C6 Acer Aspire A3 V7 Acer AT390 T2 Acer B1-723 oban Acer B1-730 EverFancy D40 Acer B1-730 vespatn Acer CloudMobile S500 a9 Acer DA220HQL lenovo72_we_jb3 Acer DA222HQL N451 Acer DA222HQLA A66 Acer DA222HQLA Flare S3 Power Acer DA226HQ tianyu72_w_hz_kk Acer E330 C7 Acer E330 GT-N7105T Acer E330 STUDIO XL Acer E350 C8n Acer E350 wiko Acer G100W maya Acer G1-715 A510s Acer G1-715 e1808_v75_hjy1_5640_maxwest Acer Icona One 7 vespa Acer Iconia One 7 AT1G* Acer Iconia One 7 G1-725 Acer Iconia One 7 m72_emmc_s6_pcb22_1024_8g1g_fuyin Acer Iconia One 7 vespa2 Acer Iconia One 8 vespa8 Acer Iconia Tab 7 acer_apriliahd Acer Iconia Tab 8 ducati2fhd Acer Iconia Tab 8 ducati2hd Acer Iconia Tab 8 ducati2hd3g Acer Iconia Tab 8 Modelo II - Professor Acer Iconia Tab A100 (VanGogh) vangogh Acer Iconia Tab A200 s7503 Acer Iconia Tab A200 SM-N9006 Acer Iconia Tab A501 ELUGA_Mark Acer Iconia Tab A501 picasso Acer Iconia Tab A510 myPhone Acer Iconia Tab A510 picasso_m Acer Iconia Tab A510 ZUUM_M50 Acer Iconia Tab A701 picasso_mf Acer Iconia Tab A701 Revo_HD2 Acer Iconia TalkTab 7 acer_a1_724 Acer Iconia TalkTab 7 AG CHROME ULTRA Acer Liquid a1 Acer Liquid C1 I1 Acer Liquid C1 l3365 Acer Liquid E1 C10 Acer Liquid E2 C11 Acer Liquid E3 acer_e3 Acer Liquid E3 acer_e3n Acer Liquid E3 LS900 Acer Liquid E3 Quasar Acer Liquid E600 e600 Acer Liquid -

Step 1(To Be Performed on Your Samsung Galaxy S8) Step 2 Step 3
For a connection between your mobile phone and your Mercedes-Benz hands-free system to be successful, Bluetooth® must be turned on in your mobile phone. Please make sure to also read the operating and pairing instructions of the mobile phone. Please follow the steps below to connect your mobile phone Samsung Galaxy S8 with the mobile phone application of your Mercedes-Benz hands-free system using Bluetooth®. Step 1(to be performed on your Samsung Galaxy S8) Step 2 To get to the telephone screen of your Mercedes-Benz hands-free system press the Phone icon on the homescreen. Step 3 Select the Phone icon in the lower right corner. Step 4 Select the “Connect a New Device” application. Page 1 of 3 Step 5 Select the “Start Search Function” Step 6 The system will now search for any Bluetooth compatible phones. This may take some time depending on how many devices are found by the system. Step 7 Once the system completes searching select your mobile phone (example "My phone") from the list. Step 8 The pairing process will generate a 6-digit passcode and display it on the screen. Verify that the same 6 digits are shown on the display of your phone. Step 9 (to be performed on your Samsung Galaxy S8) There will be a pop-up "Bluetooth Request: 'MB Bluetooth' would like to pair with your phone. Confirm that the code '### ###' is shown on 'MB Bluetooth'. " Select "Pair" on your phone if the codes match. Page 2 of 3 Step 10 After the passcode is verified on both the mobile and the COMAND, the phone will begin to be authorized. -

Samsung Galaxy S8/S8+ User Guide
Sprint User Guide A downloadable, printable guide to your Samsung Galaxy S8/S8+ and its features. Available applications and services are subject to change at any time. Table of Contents GETTING STARTED 1 Introduction 2 About the User Guide 2 Special Features 2 SET UP YOUR DEVICE 4 Assemble Your Device 5 Install the SIM Card and a Memory Card 5 Charge the Battery 6 When to Charge the Battery 7 Micro-USB Connector 7 Reverse Charging 8 Start Using Your Device 8 Device Setup 9 Use the Setup Wizard 9 Google Account 9 Factory Reset Protection 9 Samsung Account 10 Add an Email Account 10 Activate Your Phone 11 Voicemail Setup 11 Transfer Data from Your Old Device 12 Transfer Files Between Your Phone and a Computer 12 Learn About Your Device 14 Your Phone’s Layout 14 Home Screen and Applications (Apps) List 15 Home Screen Basics 17 Customize Your Home Screen 17 Status Bar 20 Notification Panel 21 Bixby 22 Navigation 23 Enter Text 25 Samsung Keyboard 25 i Use Samsung Voice Input 26 Face Recognition 27 Fingerprint Scanner 27 Iris Scanner 28 Multi Window 30 Emergency Mode 31 Edge Screen 33 APPS 37 Using Apps 38 Apps Basics 38 Access Apps 38 Add an Apps Shortcut 38 Download and Install New Apps 38 Uninstall Apps 38 Organize Apps 39 Applications Settings 40 Calculator 41 Calendar 42 Calendar View 42 Create an Event 43 View Calendar Events 43 Share an Event 43 Delete an Event 43 Create a Task 44 Delete a Task 44 Calendar Settings 44 Add Calendars 44 Sync Calendars 45 Camera and Video 45 Camera Overview 45 Camera Shortcut 46 Take Pictures 46 Record -

Google Nexus 6P (H1512) Google Nexus 7
GPSMAP 276Cx Google Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Nexus 7 Google Nexus 6 HTC HTC One (M7) HTC One (M9) HTC One (M10) HTC One (M8) HTC One (A9) HTC Butterfly S LG LG V10 H962 LG G3 Titan LG G5 H860 LG E988 Gpro LG G4 H815 Motorola Motorola RAZR M Motorola DROID Turbo Motorola Moto G (2st Gen) Motorola Droid MAXX Motorola Moto G (1st Gen) Samsung Samsung Galaxy Note 2 Samsung Galaxy S4 Active Samsung Galaxy S6 edge + (SM-G9287) Samsung Galaxy Note 3 Samsung Galaxy S5 Samsung Galaxy S7 edge (SM- G935FD) Samsung Galaxy Note 4 Samsung Galaxy S5 Active Samsung GALAXY J Samsung Galaxy Note 5 (SM- Samsung Galaxy S5 Mini Samsung Galaxy A5 Duos N9208) Samsung Galaxy S3 Samsung Galaxy S6 Samsung Galaxy A9 (SM- A9000) Samsung Galaxy S4 Sony Sony Ericsson Xperia Z Sony Xperia Z3 Sony Xperia X Sony Ericsson Xperia Z Ultra Sony Xperia Z3 Compact Sony XPERIA Z5 Sony Xperia Z2 Sony XPERIA E1 Asus ASUS Zenfone 2 ASUS Zenfone 5 ASUS Zenfone 6 Huawei HUAWEI P8 HUAWEI M100 HUAWEI P9 HUAWEI CRR_L09 XIAOMI XIAOMI 2S XIAOMI 3 XIAOMI 5 XIAOMI Note GPSMAP 64s Google Google Nexus 4 Google Nexus 6P (H1512) Google Pixel Google Nexus 6 Google Nexus 7 HTC HTC One (M7) HTC One (A9) HTC Butterfly S HTC One (M8) HTC One (M10) HTC U11 HTC One (M9) LG LG Flex LG E988 Gpro LG G5 H860 LG V10 H962 LG G4 H815 LG G6 H870 Motorola Motorola RAZR M Motorola DROID Turbo Motorola Moto G (2st Gen) Motorola Droid MAXX Motorola Moto G (1st Gen) Motorola Moto Z Samsung Samsung Galaxy Note 2 Samsung Galaxy S5 Samsung Galaxy J5 Samsung Galaxy Note 3 Samsung Galaxy -

Mobile Phones the Latest Handsets Tested
Kondinin Group ResearchMAY 2018 No. 100 www.farmingahead.com.au ReportPrice: $95 MOBILE PHONES THE LATEST HANDSETS TESTED Independent information for agriculture H RE RC PO A R E T S • E RESEARCH REPORT MOBILE PHONES K R O • N P D U I N O I R N G NextG phones – the good, the bad and the ugly In their annual outback pilgrimage, Kondinin Group engineers Josh Giumelli and Ben White head to remote NSW to test the latest crop of handsets. Of the 13 units tested, there were several surprises; some star performers, some lacklustre results, and several that just made up the numbers. If you want a phone with good reception or features that matter, read on. hese days, the mobile phone is source in the paddock, rather than at home just about as crucial to the farm on the computer. business as any other piece of But we face a growing dilemma in that machinery. connectivity continues to limit the usefulness TThe sum total of tasks performed using a of much of what we want to do with our phone handset only increases as each year smartphones. While mobile networks goes by. More manufacturers supply apps continue to grow, they are not always rolled Retro rocket? The new Nokia 3310 harkens back to to operate or calibrate machinery, more out in rural areas where we need them the days of the CDMA network and the simple Nokia information is needed at your fingertips most. Compounding the problem is that the handsets with awesome battery life and excellent in an instant, and record keeping becomes smartphones' reception performance seems reception.