Papillon 0.5.4 – Solaris Security Module Documentation and Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle Solaris: the Carrier-Grade Operating System Technical Brief
An Oracle White Paper February 2011 Oracle Solaris: The Carrier-Grade Operating System Oracle White Paper—Oracle Solaris: The Carrier-Grade OS Executive Summary.............................................................................1 ® Powering Communication—The Oracle Solaris Ecosystem..............3 Integrated and Optimized Stack ......................................................5 End-to-End Security ........................................................................5 Unparalleled Performance and Scalability.......................................6 Increased Reliability ........................................................................7 Unmatched Flexibility ......................................................................7 SCOPE Alliance ..............................................................................7 Security................................................................................................8 Security Hardening and Monitoring .................................................8 Process and User Rights Management...........................................9 Network Security and Encrypted Communications .......................10 Virtualization ......................................................................................13 Oracle VM Server for SPARC .......................................................13 Oracle Solaris Zones .....................................................................14 Virtualized Networking...................................................................15 -

Software Security for Open-Source Systems
Open-Source Security Software Security for Open-Source Systems Debate over whether open-source software development leads to more or less secure software has raged for years. Neither is in- trinsically correct: open-source software gives both attackers and defenders greater power over system security. Fortunately, several security-enhancing technologies for open-source sys- tems can help defenders improve their security. classify methods that CRISPIN ome people have claimed that open-source ensure and enforce COWAN software is intrinsically more secure than closed the “nothing else” part into three broad categories: WireX source,1 and others have claimed that it’s not.2 Communications Neither case is absolutely true: they are essen- • Software auditing, which prevents vulnerabilities by Stially flip sides of the same coin. Open source gives both searching for them ahead of time, with or without auto- attackers and defenders greater analytic power to do matic analysis something about software vulnerabilities. If the defender • Vulnerability mitigation, which are compile-time tech- does nothing about security, though, open source just niques that stop bugs at runtime gives that advantage away to the attacker. • Behavior management, which are operating system fea- However, open source also offers great advantages to tures that either limit potential damage or block specif- the defender, giving access to security techniques that are ic behaviors known to be dangerous normally infeasible with closed-source software. Closed source forces users to accept the level of security diligence Software auditing that the vendor chooses to provide, whereas open source The least damaging software vulnerability is the one that lets users (or other collectives of people) raise the bar on never happens. -

Solaris 10 End of Life
Solaris 10 end of life Continue Oracle Solaris 10 has had an amazing OS update, including ground features such as zones (Solaris containers), FSS, Services, Dynamic Tracking (against live production operating systems without impact), and logical domains. These features have been imitated in the market (imitation is the best form of flattery!) like all good things, they have to come to an end. Sun Microsystems was acquired by Oracle and eventually, the largest OS known to the industry, needs to be updated. Oracle has set a retirement date of January 2021. Oracle indicated that Solaris 10 systems would need to raise support costs. Oracle has never provided migratory tools to facilitate migration from Solaris 10 to Solaris 11, so migration to Solaris has been slow. In September 2019, Oracle decided that extended support for Solaris 10 without an additional financial penalty would be delayed until 2024! Well its March 1 is just a reminder that Oracle Solaris 10 is getting the end of life regarding support if you accept extended support from Oracle. Combined with the fact gdpR should take effect on May 25, 2018 you want to make sure that you are either upgraded to Solaris 11.3 or have taken extended support to obtain any patches for security issues. For more information on tanningix releases and support dates of old and new follow this link ×Sestive to abort the Unix Error Operating System originally developed by Sun Microsystems SolarisDeveloperSun Microsystems (acquired by Oracle Corporation in 2009)Written inC, C'OSUnixWorking StateCurrentSource ModelMixedInitial release1992; 28 years ago (1992-06)Last release11.4 / August 28, 2018; 2 years ago (2018-08-28)Marketing targetServer, PlatformsCurrent: SPARC, x86-64 Former: IA-32, PowerPCKernel typeMonolithic with dynamically downloadable modulesDefault user interface GNOME-2-LicenseVariousOfficial websitewww.oracle.com/solaris Solaris is the own operating system Of Unix, originally developed by Sunsystems. -

Hardening Linux
eBooks-IT.org 4444_FM_final.qxd 1/5/05 12:39 AM Page i eBooks-IT.org Hardening Linux JAMES TURNBULL 4444_FM_final.qxd 1/5/05 12:39 AM Page ii eBooks-IT.org Hardening Linux Copyright © 2005 by James Turnbull All rights reserved. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the copyright owner and the publisher. ISBN (pbk): 1-59059-444-4 Printed and bound in the United States of America 987654321 Trademarked names may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, we use the names only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. Lead Editor: Jim Sumser Technical Reviewer: Judith Myerson Editorial Board: Steve Anglin, Dan Appleman, Ewan Buckingham, Gary Cornell, Tony Davis, Jason Gilmore, Chris Mills, Dominic Shakeshaft, Jim Sumser Project Manager: Kylie Johnston Copy Edit Manager: Nicole LeClerc Copy Editor: Kim Wimpsett Production Manager: Kari Brooks-Copony Production Editor: Kelly Winquist Compositor: Linda Weidemann Proofreader: Lori Bring Indexer: Kevin Broccoli Artist: Kinetic Publishing Services, LLC Cover Designer: Kurt Krames Manufacturing Manager: Tom Debolski Distributed to the book trade in the United States by Springer-Verlag New York, Inc., 233 Spring Street, 6th Floor, New York, NY 10013, and outside the United States by Springer-Verlag GmbH & Co. KG, Tiergartenstr. 17, 69112 Heidelberg, Germany. In the United States: phone 1-800-SPRINGER, fax 201-348-4505, e-mail [email protected], or visit http://www.springer-ny.com. -

Sun SPARC Enterprise T5440 Servers
Sun SPARC Enterprise® T5440 Server Just the Facts SunWIN token 526118 December 16, 2009 Version 2.3 Distribution restricted to Sun Internal and Authorized Partners Only. Not for distribution otherwise, in whole or in part T5440 Server Just the Facts Dec. 16, 2009 Sun Internal and Authorized Partner Use Only Page 1 of 133 Copyrights ©2008, 2009 Sun Microsystems, Inc. All Rights Reserved. Sun, Sun Microsystems, the Sun logo, Sun Fire, Sun SPARC Enterprise, Solaris, Java, J2EE, Sun Java, SunSpectrum, iForce, VIS, SunVTS, Sun N1, CoolThreads, Sun StorEdge, Sun Enterprise, Netra, SunSpectrum Platinum, SunSpectrum Gold, SunSpectrum Silver, and SunSpectrum Bronze are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the United States and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. UNIX is a registered trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. T5440 Server Just the Facts Dec. 16, 2009 Sun Internal and Authorized Partner Use Only Page 2 of 133 Revision History Version Date Comments 1.0 Oct. 13, 2008 - Initial version 1.1 Oct. 16, 2008 - Enhanced I/O Expansion Module section - Notes on release tabs of XSR-1242/XSR-1242E rack - Updated IBM 560 and HP DL580 G5 competitive information - Updates to external storage products 1.2 Nov. 18, 2008 - Number -

Opensolaris Et La Sécurité Master 2 SSI Université Du Sud, Toulon Et Du Var
David Pauillac OpenSolaris et la sécurité Master 2 SSI Université du Sud, Toulon et du Var novembre 2007 ii Copyright c 2007 David PAUILLAC. Ce document est distribué sous Licence GNU Free Documentation License 1. Vous pouvez copier et/ou distribuer ce document à condition de respecter les termes de la GFDL, version 1.2 ou toute version publiée ultérieurement par la Free Software Foundation. Une copie de la licence est incluse en annexe C intitulée “GNU Free Documentation License”. Les nom et logos OpenSolaris sont des marques déposées par Sun Microsystem. 1. GFDL David Pauillac c novembre 2007 - OpenSolaris et la sécurité Avant-propos À propos du document Ce document, à l’origine, était destiné aux étudiants de master2 SSI de l’université de Sud, Toulon et du Var. Cependant, j’espère qu’il pourra ser- vir aussi aux administrateurs devant (ou désirant) utiliser un système basé sur OpenSolaris (tel que le système de Sun Microsystem, Solaris, largement répandu). Il m’a semblé intéressant de comparer, lorsque celà est nécessaire, OpenSo- laris et GNU/Linux ; en effet, ce dernier est bien plus connu dans le monde universitaire que le système ouvert de Sun Microsystem. Ainsi, le but de ce document n’est pas de remplacer la documentation fournie avec le système Solaris, mais juste de fournir des informations impor- tantes pour installer, configurer et sécuriser un système basé sur OpenSolaris, que ce soit sur un serveur ou sur une station de travail. Pour toute remarque ou question, vous pouvez contacter l’auteur à l’adresse suivante: [email protected] En introduction, il m’a semblé important de retracer brièvement l’histoire des systèmes UNIX ainsi que de traiter certains points théoriques de ce type de systèmes d’exploitation. -

Securing Linux
466_HTC_Linux_FM.qxd 10/2/07 10:05 AM Page iii How to Cheat at Securing Linux Mohan Krishnamurthy Eric S. Seagren Raven Alder Aaron W. Bayles Josh Burke Skip Carter Eli Faskha 466_HTC_Linux_FM.qxd 10/2/07 10:05 AM Page iv Elsevier, Inc., the author(s), and any person or firm involved in the writing, editing, or production (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY.You may have other legal rights, which vary from state to state. In no event will Makers be liable to you for damages, including any loss of profits, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you. You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and files. Syngress Media®, Syngress®,“Career Advancement Through Skill Enhancement®,”“Ask the Author UPDATE®,” and “Hack Proofing®,” are registered trademarks of Elsevier, Inc.“Syngress:The Definition of a Serious Security Library”™,“Mission Critical™,” and “The Only Way to Stop a Hacker is to Think Like One™” are trademarks of Elsevier, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies. PUBLISHED BY Syngress Publishing, Inc. -

Using Internal Sensors for Computer Intrusion Detection
USING INTERNAL SENSORS FOR COMPUTER INTRUSION DETECTION A Thesis Submitted to the Faculty of Purdue University by Diego Zamboni CERIAS TR 2001-42 Center for Education and Research in Information Assurance and Security, Purdue University August 2001 USING INTERNAL SENSORS FOR COMPUTER INTRUSION DETECTION A Thesis Submitted to the Faculty of Purdue University by Diego Zamboni In Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy August 2001 ii To my parents for giving me life, and to Susana for sharing it with me. iii ACKNOWLEDGMENTS As usual, a large number of people were very important for the completion of this thesis work, and I would like to acknowledge at least some of them. First the official acknowledgments: Portions of the research contributing to this dis- sertation were supported by the various sponsors of CERIAS, and my stay at Purdue was partially funded by a Fulbright/Conacyt fellowship. Their support is gratefully acknowl- edged. I would like to thank my advisor, Eugene Spafford. He received me with open arms from my first day at Purdue, and provided continuous guidance and support throughout my stay here. For that I am very, very grateful. I would like to acknowledge the other members of my Ph.D. committee: Stephanie For- rest, Mikhail Atallah, Jens Palsberg and Carla Brodley. They provided invaluable feedback and advice for my work and for this dissertation. Many people contributed significantly to my work, and my deepest gratitude goes to all of them. Susana Soriano, Benjamin Kuperman, Thomas Daniels, Florian Kerschbaum, Rajeev Gopalakrishna and Jim Early provided me with many hours of discussion, continu- ously questioned my assumptions, and led to many new ideas. -

Red Hat Enterprise Linux: Your Solaris Alternative
RED HAT ENTERPRISE LINUX: YOUR SOLARIS ALTERNATIVE 2 INTRODUCTION 3 FACTORS THAT INFLUENCE OPERATING SYSTEM CHOICE New projects Mandated migration 4 BUSINESS REQUIREMENTS TO CONSIDER Strength of ISV support Application migration considerations Performance Availability and scalability Security 11 TOTAL COST OF OWNERSHIP (TCO) Feature of comparison 13 DETAILED COMPARISON OF SELECTED FEATURES Filesystems and volume managers: Ext3, Ext4, XFS vs. UFS and ZFS DTrace vs SystemTap Software management 18 CONCLUSION Platform support Customer value www.redhat.com Red Hat Enterprise Linux: Your Solaris Alternative INTRODUCTION There were two primary reasons that IT professionals previously chose the Oracle Sun SPARC platform to power their IT infrastructures: the performance of the hardware and the robustness of the Solaris operating system. As the price, performance, and reliability of industry-standard x86_64 servers have increased to the point where they can meet and exceed these features, the reasons to continue buying SPARC hardware have become less and less compelling. This is particularly true with with large, multi-core x86 systems that are designed specifically for Linux©, such as the latest 128-core systems. Similarly, Linux, and in particular, Red Hat© Enterprise Linux, have emerged as the operating system of choice to leverage the benefits of open, industry-standard architectures. Selecting an operating system for your IT infrastructure has long-term consequences. The selection process must take into account not only the technical features of the current operating system, but the ability for the operating system to enable and support your future business requirements. While Oracle has quelled some worry over their commitment to Solaris, the move to Solaris 11 will likely be as painful as the move from Solaris 8/9 to Solaris 10, as Solaris 11 is significantly different from Solaris 10. -

Migrating to Oracle Solaris with Oracle Database 11G on Intel Xeon
A migration guide commissioned by Intel Corp. and Oracle Table of contents Table of contents ....................................................................... 2 Preface ...................................................................................... 4 Introduction ............................................................................... 5 Scope of this Guide ..................................................................................... 5 A move that will yield real benefits ............................................................ 6 Features of the Sun Fire X4800 Server with the Intel Xeon Processor 7500 series ........................................................................................................... 6 Features of Oracle Solaris 10 ...................................................................... 7 Planning the migration .............................................................. 9 Considerations for moving your applications ............................................. 9 Java-based applications ...............................................................................9 A note about application data ......................................................................9 Considerations for moving platforms ......................................................... 9 Application compatibility ..............................................................................9 Difference in operating systems ...................................................................9 Considerations -

Operating System Stability and Security Through Process Homeostasis
Operating System Stability and Security through Process Homeostasis by Anil Buntwal Somayaji B.S., Massachusetts Institute of Technology, 1994 DISSERTATION Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy Computer Science The University of New Mexico Albuquerque, New Mexico May 2002 c 2002, Anil Buntwal Somayaji ! iii Dedication To all those system administrators who spend their days nursemaiding our computers. iv Acknowledgments Graduate school has turned out to be a long, difficult, but rewarding journey for me, and I would not have made it this far without the help of many, many people. I cannot hope to completely document how these influences have helped me grow; nevertheless, I must try and acknowledge those who have accompanied me. First, I would like to thank my committee: David Ackley, Rodney Brooks, Barney Maccabe, Margo Seltzer, and especially my advisor, Stephanie Forrest. They all had to read through a rougher manuscript than I would have liked, and had to do so under significant time pressures. They provided invaluable feedback on my ideas and experiments. Most importantly, they have been my teachers. I’m also grateful to have been part of the Adaptive Computation Group at the University of New Mexico and to have been a member of the complex adaptive systems community here in New Mexico. Fellow graduate students at UNM and colleagues at the Santa Fe Institute have shaped my thoughts and have inspired me to do my best work. I will miss all of you. The Computer Science Department at UNM has been my home for the past several years. -
Trusted Solaris History
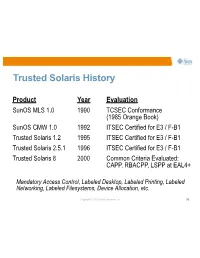
Trusted Solaris History Product Year Evaluation SunOS MLS 1.0 1990 TCSEC Conformance (1985 Orange Book) SunOS CMW 1.0 1992 ITSEC Certified for E3 / F-B1 Trusted Solaris 1.2 1995 ITSEC Certified for E3 / F-B1 Trusted Solaris 2.5.1 1996 ITSEC Certified for E3 / F-B1 Trusted Solaris 8 2000 Common Criteria Evaluated: CAPP, RBACPP, LSPP at EAL4+ Mandatory Access Control, Labeled Desktop, Labeled Printing, Labeled Networking, Labeled Filesystems, Device Allocation, etc. Copyright © 2009 Sun Microsystems, Inc. 79 Trusted Solaris History Product Year Evaluation SunOS MLS 1.0 1990 TCSEC Conformance (1985 Orange Book) SunOS CMW 1.0 1992 ITSEC Certified for E3 / F-B1 Trusted Solaris 1.2 1995 ITSEC Certified for E3 / F-B1 Trusted Solaris 2.5.1 1996 ITSEC Certified for E3 / F-B1 Trusted Solaris 8 2000 Common Criteria Evaluated: CAPP, RBACPP, LSPP at EAL4+ Mandatory Access Control, Labeled Desktop, Labeled Printing, Labeled Networking, Labeled Filesystems, Device Allocation, etc. Copyright © 2009 Sun Microsystems, Inc. 79 Solaris Trusted Extensions •A redesign of the Trusted Solaris product using a layered architecture. •An extension of the Solaris 10 security foundation providing access control policies based on the sensitivity/label of objects. •A set of label-aware services which implement multilevel security. Copyright © 2009 Sun Microsystems, Inc. 80 Extending Solaris 10 Security Features •Process Rights Management (Privileges) >Fine-grained privileges for X windows >Rights management applied to desktop actions •User Rights Management (RBAC) >Labels and clearances >Additional desktop policies •Solaris Containers (Zones) >Unique Sensitivity Labels >Trusted (label-based) Networking Copyright © 2009 Sun Microsystems, Inc. 81 Trusted Extensions in a Nutshell •Every object has a label associated with it.