Design for Re-Engineering the Web
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Open Source Used in Cisco 7600 Wireless Security Gateway Release 4.4
Open Source Used In Cisco 7600 Wireless Security Gateway Release 4.4 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Open Source Used In Cisco 7600 Wireless Security Gateway Release 4.4 1 Text Part Number: 78EE117C99-66606837 Open Source Used In Cisco 7600 Wireless Security Gateway Release 4.4 2 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-66606837 Contents 1.1 Apache HTTP Server 2.2.3 :5.0.0.0801182 1.1.1 Available under license 1.2 audit 1.2.9 :7.0.0 1.2.1 Available under license 1.3 base-passwd 3.5.7 :11.0.0.0801182 1.3.1 Available under license 1.4 bash 3.0 :6.0.2.0801182 1.4.1 Available under license 1.5 binutils 2.17.50 :10.0.5.0801182 1.5.1 Available under license 1.6 busybox 1.6.0 :7.0.2.0801182 1.6.1 Available under license 1.7 busybox-static 1.6.0 :7.0.2.0801182 1.7.1 Available under license 1.8 cron 3.0pl1 :5.0.2.0801182 1.8.1 Available under license 1.9 db 4.3.28 :1.0.0.0801182 1.9.1 Available under license 1.10 e2fsprogs 1.41.3 :1.0.0 1.10.1 Available -

The Origins of the Underline As Visual Representation of the Hyperlink on the Web: a Case Study in Skeuomorphism
The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Romano, John J. 2016. The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism. Master's thesis, Harvard Extension School. Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:33797379 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism John J Romano A Thesis in the Field of Visual Arts for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2016 Abstract This thesis investigates the process by which the underline came to be used as the default signifier of hyperlinks on the World Wide Web. Created in 1990 by Tim Berners- Lee, the web quickly became the most used hypertext system in the world, and most browsers default to indicating hyperlinks with an underline. To answer the question of why the underline was chosen over competing demarcation techniques, the thesis applies the methods of history of technology and sociology of technology. Before the invention of the web, the underline–also known as the vinculum–was used in many contexts in writing systems; collecting entities together to form a whole and ascribing additional meaning to the content. -

Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe
Weblint: Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe Abstract Weblint is a utility for checking the syntax and style of HTML pages. It was inspired by lint [15], which performs a similar function for C and C++ programmers. Weblint does not aspire to be a strict SGML validator, but to provide helpful comments for humans. The importance of quality assurance for web sites is introduced, and one particular area, validation of HTML, is described in more detail. The bulk of the paper is devoted to weblint: what it is, how it is used, and the design and implementation of the current development version. 1. Introduction The conclusion opens with a summary of the information and opinions given in this paper. A Web sites are becoming an increasingly critical part of selection of the lessons learned over the last four years how many companies do business. For many companies is given, followed by plans for the future, and related web sites are their business. It is therefore critical that ideas. owners of web sites perform regular testing and analysis, to ensure quality of service. 2. Web Site Quality Assurance There are many different checks and analyses which The following are some of the questions you should be you can run on a site. For example, how usable is your asking yourself if you have a web presence. I have site when accessed via a modem? An incomplete list of limited the list to those points which are relevant to similar analyses are given at the start of Section 2. -

Formal Aspects of Mobile Code Security
FORMAL ASPECTS OF MOBILE CODE SECURITY RICHARD DREWS DEAN ADISSERTATION PRESENTED TO THE FACULTY OF PRINCETON UNIVERSITY IN CANDIDACY FOR THE DEGREE OF DOCTOR OF PHILOSOPHY RECOMMENDED FOR ACCEPTANCE BY THE DEPARTMENT OF COMPUTER SCIENCE JANUARY 1999 c Copyright by Richard Drews Dean, 1998. All Rights Reserved Abstract We believe that formal methods of all kinds are critical to mobile code security, as one route to gaining the assurance level necessary for running potentially hos- tile code on a routine basis. We begin by examining Java, and understanding the weaknesses in its architecture, on both design and implementation levels. Iden- tifying dynamic linking as a key problem, we produce a formal model of linking, and prove desirable properties about our model. This investigation leads to a deep understanding of the underlying problem. Finally, we turn our attention to crypto- graphic hash functions, and their analysis with binary decision diagrams (BDDs). We show that three commonly used hash functions (MD4, MD5, and SHA-1) do not offer ideal strength against second preimages. The ability of a cryptographic hash function to resist the finding of second preimages is critical for its use in digi- tal signature schemes: a second preimage enables the forgery of digital signatures, which would undermine confidence in digitally signed mobile code. Our results show that modern theorem provers and BDD-based reasoning tools are effective for reasoning about some of the key problems facing mobile code security today. iii Acknowledgments My advisor, Andrew Appel, offered sure guidance through what turned out to be an exceptionally smooth journey through graduate school. -

Annotea: an Open RDF Infrastructure for Shared Web Annotations
Proceedings of the WWW 10th International Conference, Hong Kong, May 2001. Annotea: An Open RDF Infrastructure for Shared Web Annotations Jos´eKahan,1 Marja-Riitta Koivunen,2 Eric Prud’Hommeaux2 and Ralph R. Swick2 1 W3C INRIA Rhone-Alpes 2 W3C MIT Laboratory for Computer Science {kahan, marja, eric, swick}@w3.org Abstract. Annotea is a Web-based shared annotation system based on a general-purpose open RDF infrastructure, where annotations are modeled as a class of metadata.Annotations are viewed as statements made by an author about a Web doc- ument. Annotations are external to the documents and can be stored in one or more annotation servers.One of the goals of this project has been to re-use as much existing W3C technol- ogy as possible. We have reacheditmostlybycombining RDF with XPointer, XLink, and HTTP. We have also implemented an instance of our system using the Amaya editor/browser and ageneric RDF database, accessible through an Apache HTTP server. In this implementation, the merging of annotations with documents takes place within the client. The paper presents the overall design of Annotea and describes some of the issues we have faced and how we have solved them. 1Introduction One of the basic milestones in the road to a Semantic Web [22] is the as- sociation of metadata to content. Metadata allows the Web to describe properties about some given content, even if the medium of this content does not directly provide the necessary means to do so. For example, ametadata schema for digital photos [15] allows the Web to describe, among other properties, the camera model used to take a photo, shut- ter speed, date, and location. -
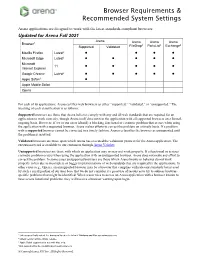
Browser Requirements & Recommended
Browser Requirements & Recommended System Settings Arena applications are designed to work with the latest standards-compliant browsers. Updated for Arena Fall 2021 Arena 1 Arena Arena Arena Browser 4 4 4 Supported Validated FileDrop PartsList Exchange Mozilla Firefox Latest2 l l l l Microsoft Edge Latest2 l l l l l Microsoft 11 l l l l l Internet Explorer Google Chrome Latest2 l l l l l Apple Safari3 l Apple Mobile Safari Opera For each of its applications, Arena certifies web browsers as either “supported,” “validated,” or “unsupported.” The meaning of each classification is as follows: Supported browsers are those that Arena believes comply with any and all web standards that are required for an application to work correctly, though Arena itself does not test the application with all supported browsers on a formal, ongoing basis. However, if we or our users identify a blocking functional or cosmetic problem that occurs when using the application with a supported browser, Arena makes efforts to correct the problem on a timely basis. If a problem with a supported browser cannot be corrected in a timely fashion, Arena reclassifies the browser as unsupported until the problem is resolved. Validated browsers are those upon which Arena has executed the validation protocol for the Arena application. The execution record is available to our customers through Arena Validate. Unsupported browsers are those with which an application may or may not work properly. If a functional or serious cosmetic problem occurs when using the application with an unsupported browser, Arena does not make any effort to correct the problem. -

University of the Philippines Manila College of Arts and Sciences Department of Physical Sciences and Mathematics
UNIVERSITY OF THE PHILIPPINES MANILA COLLEGE OF ARTS AND SCIENCES DEPARTMENT OF PHYSICAL SCIENCES AND MATHEMATICS Health Insurance Corporation Customer Relationship Management Tool (HICorpCRM) A special problem in partial fulfillment of the requirements for the degree of Bachelor of Science in Computer Science Submitted by: Paul John N. Macaraeg June 2015 Permission is given for the following people to have access to this SP: Available to the general public Yes Available only after consultation with author/ SP adviser No Available only to those bound by confidentiality agreement No ACCEPTANCE SHEET The Special Problem entitled “Health Insurance Corporation Customer Relationship Management Tool (HICorpCRM)” prepared and submitted by Paul John N. Macaraeg in partial fulfillment of the requirements for the degree of Bachelor of Science in Computer Science has been examined and is recommended or acceptance. Ma. Sheila A. Magboo, M.Sc. Adviser EXAMINERS: Approved Disapproved 1. Gregorio B. Baes, Ph.D. 2. Avegail D. Carpio, M.Sc. 3. Perlita E. Gasmen, M.Sc. 4. Richar Bryann L. Chua, M.Sc. 5. Vincent Peter C. Magboo, M.D., M.Sc. 6. Bernie B. Terrado, M.Sc. Accepted and approved as partial fulfillment of the requirements for the degree of Bachelor of Science in Computer Science. Ma. Sheila A. Magboo, M.Sc. Marcelina B. Lirazan, Ph.D. Unit Head Chair Mathematical and Computing Sciences Unit Department of Physical Sciences Department of Physical Sciences and Mathematics and Mathematics Alex C. Gonzaga, Ph.D., Dr.Eng. Dean College of Arts and Sciences iii Abstract The health insurance industry is saturated by big companies competing for market share. -

Prezentacja I Zastosowanie Systemu Internetowych Pomiarów Obrazów Fotogrametrycznych
Artur Janowski Zygmunt Paszotta Jakub Szulwic PREZENTACJA I ZASTOSOWANIE SYSTEMU INTERNETOWYCH POMIARÓW OBRAZÓW FOTOGRAMETRYCZNYCH Streszczenie. W referacie zaprezentowane zostają funkcjonujące rozwiązania powstałe w ramach badań i prac doktorskich, a odnoszące się do rozwiązywania zadań fotogrametrii lotniczej w środowisku internetowym. Pierwotny zamysł systemu internetowych pomiarów obrazów fotogrametrycznych (SIPOF) zrodził się w projekcie badawczym prowadzonym w zespole dra hab. Zygmunta Paszotty, prof. UWM, na Uniwersytecie Warmińsko-Mazurskim w Olsztynie. Zasadnicze badania były realizowane w ramach studiów nad rozprawami doktorskimi autorów. Efekty badań zostały wdrożone w formie funkcjonującego systemu umożliwiającego realizację internetowych pomiarów na zdjęciach fotogrametrycznych nazwanego SIPOF. Referat jest skróconym przewodnikiem po systemie; prezentuje jego funkcjonalność oraz przedstawia możliwości wykorzystania w edukacji, nauce i gospodarce. SIPOF był prezentowany w ośrodkach edukacyjno-badawczych w Polsce oraz zagranicą i spotkał się z zainteresowaniem podmiotów gospodarczych. Komercjalizacja pracy naukowej zaowocowała dalszą koncepcją udostępniania fotogrametrycznych opracowań rastrowych jako nośników informacji kartometrycznej dla użytkownika specjalistycznego i masowego. Przedstawienie funkcjonującego systemu internetowych pomiarów fotogrametrycznych opartego przede wszystkim na kliencie informatycznym implementowanym w graficznej przeglądarce internetowej stanowi tło dla oczekiwań , jakie pokładane są przez użytkownika -

Arena Training Guide for Administrators Table of Contents
Arena training guide for administrators Table of contents Preface 4 About this guide 4 Get to know Axiell 4 About Arena 5 Liferay 5 Portlets 5 Language handling 5 Styling 5 Arena architecture 6 Administration in Arena 7 Arena articles 7 Signing in to Arena 7 Signing in to Liferay 8 The Arena administration user interface 8 Accounts 11 User types in Arena 11 Permissions 12 Managing users in Liferay 14 Managing a roles in Liferay 16 Arena portal site administration 17 Admin: installation details 17 Site settings 19 Managing pages 21 Page permissions 21 Navigation 21 Configuring pages 21 Creating a page 22 Deleting a page 23 Arena Nova 25 Focus shortcuts 25 That’s how it works-articles 25 News articles 26 Event articles 26 Branch articles 26 FAQ articles 27 Image resources and image handling 27 Portlets in Arena 28 Symbols in the list of portlets 28 Portlets required for basic Arena functionality 28 Placement of portlets 29 Configuring portlets 30 The control toolbar 30 Look and feel 30 2 Assigning user permissions to portlets and pages 30 Liferay articles 32 Creating a Liferay article 32 Adding a Liferay article on a page 32 Arena articles 33 Approving articles 33 Handling abuse and reviews 34 Admin: moderation 34 Searching in catalogue records 36 Single words 36 Phrases 36 Multiple words 36 Truncation 36 Boolean operators 36 Fuzzy search and the similarity factor 36 Search parameters for catalogue records 37 Search parameters for Arena articles 40 Examples 40 Linking and syntaxes 41 Dynamic links 41 Syntax for similar titles 42 Syntax for other titles by the same author 42 Syntax for dynamic news list 42 3 Preface Simple, stylish and engaging, Arena is perfect for archives, libraries and museums to showcase and organize their collections in the public domain. -

Statistics for Donauschwaben-Usa.Org (2009-03)
Statistics for donauschwaben-usa.org (2009-03) Statistics for: donauschwaben-usa.org Last Update: 03 Apr 2009 - 14:14 Reported period: Month Mar 2009 When: Monthly history Days of month Days of week Hours Who: Organizations Countries Full list Hosts Full list Last visit Unresolved IP Address Robots/Spiders visitors Full list Last visit Navigation: Visits duration File type Viewed Full list Entry Exit Operating Systems Versions Unknown Browsers Versions Unknown Referrers: Origin Referring search engines Referring sites Search Search Keyphrases Search Keywords Others: Miscellaneous HTTP Status codes Pages not found Summary Reported period Month Mar 2009 First visit 01 Mar 2009 - 00:17 Last visit 31 Mar 2009 - 23:17 Unique visitors Number of visits Pages Hits Bandwidth 2112 2781 15381 71620 4.59 GB Viewed traffic * (1.31 visits/visitor) (5.53 Pages/Visit) (25.75 Hits/Visit) (1732.12 KB/Visit) Not viewed traffic * 8539 10927 896.73 MB * Not viewed traffic includes traffic generated by robots, worms, or replies with special HTTP status codes. Monthly history Jan Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec 2009 2009 2009 2009 2009 2009 2009 2009 2009 2009 2009 2009 Month Unique visitors Number of visits Pages Hits Bandwidth Jan 2009 0 0 0 0 0 Feb 2009 0 0 0 0 0 Mar 2009 2112 2781 15381 71620 4.59 GB Apr 2009 0 0 0 0 0 May 2009 0 0 0 0 0 Jun 2009 0 0 0 0 0 Jul 2009 0 0 0 0 0 Aug 2009 0 0 0 0 0 Sep 2009 0 0 0 0 0 Oct 2009 0 0 0 0 0 Nov 2009 0 0 0 0 0 Dec 2009 0 0 0 0 0 Total 2112 2781 15381 71620 4.59 GB Days of month 01 02 03 04 05 06 07 08 -

Migrating from Java Applets to Plugin-Free Java Technologies
Migrating from Java Applets to plugin-free Java technologies An Oracle White Paper January, 2016 Migrating from Java Applets to plugin-free Java technologies Migrating from Java Applets to plugin-free Java technologies Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. Migrating from Java Applets to plugin-free Java technologies Executive Overview ........................................................................... 4 Browser Plugin Perspectives ............................................................. 4 Java Web Start .................................................................................. 5 Alternatives ....................................................................................... 6 Native Windows/OS X/Linux Installers ........................................... 6 Inverted Browser Control ............................................................... 7 Detecting Applets .............................................................................. 7 Migrating from Java Applets to plugin-free Java technologies Executive Overview With modern browser vendors working to restrict or reduce the support of plugins like -

World-Wide Web Proxies
World-Wide Web Proxies Ari Luotonen, CERN Kevin Altis, Intel April 1994 Abstract 1.0 Introduction A WWW proxy server, proxy for short, provides access to The primary use of proxies is to allow access to the Web the Web for people on closed subnets who can only access from within a firewall (Fig. 1). A proxy is a special HTTP the Internet through a firewall machine. The hypertext [HTTP] server that typically runs on a firewall machine. server developed at CERN, cern_httpd, is capable of run- The proxy waits for a request from inside the firewall, for- ning as a proxy, providing seamless external access to wards the request to the remote server outside the firewall, HTTP, Gopher, WAIS and FTP. reads the response and then sends it back to the client. cern_httpd has had gateway features for a long time, but In the usual case, the same proxy is used by all the clients only this spring they were extended to support all the within a given subnet. This makes it possible for the proxy methods in the HTTP protocol used by WWW clients. Cli- to do efficient caching of documents that are requested by ents don’t lose any functionality by going through a proxy, a number of clients. except special processing they may have done for non- native Web protocols such as Gopher and FTP. The ability to cache documents also makes proxies attrac- tive to those not inside a firewall. Setting up a proxy server A brand new feature is caching performed by the proxy, is easy, and the most popular Web client programs already resulting in shorter response times after the first document have proxy support built in.