Dd-Wrt Firmware Upgrade
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tomato Topology Management Tool
ToMaTo Topology Management Tool Dennis Schwerdel University of Kaiserslautern, Germany Department of Computer Science Integrated Communication Systems ICSY http://www.icsy.de Introduction ToMaTo is a topology-oriented control framework for virtual networking experiments. Control framework Topology-oriented Like Planet-Lab, Emulab, ... Basic abstraction: Network Developed in the German-Lab topology project Each experiment has its own Open-Source project (hosted on topology Github) Topologies contain connected elements Virtual networking experiments Developed for networking Advanced features experiments Direct console access E.g. networking research or Link emulation software testing Packet capturing All parts of the experiment setup are virtual Dennis Schwerdel, University of Kaiserslautern, Germany 2 Topology Graphical representation Icons show element type Colored icons show virtualization technology Link color shows network segments Link style shows link attributes Example One central server 4 clients, connected with 2 switches Internet connected to server Per Topology Accounting Permissions Dennis Schwerdel, University of Kaiserslautern, Germany 3 VM Elements KVM Full virtualization Integrated into Linux Kernel OpenVZ Container virtualization Added to Linux Kernel via patch Scripts Programming language virtualization Installed as software Additional elements Easy to add more Planned: VirtualBox, LXC Dennis Schwerdel, University of Kaiserslautern, Germany 4 Repy scripts Repy Restricted Python (Sandbox) Technology from Seattle testbed Modified for ToMaTo Functions for receiving and sending raw ethernet packages packet = tuntap_read("eth0", timeout=None) ethernet = ethernet_decode(packet) echo("%s -> %s: %d bytes\n" % (ethernet.src, ethernet.dst, len(packet)) tuntap_send("eth1", packet) Library Basic protocols implemented: Ethernet, IPv4, TCP, UDP and ICMP Even some higher protocols: DHCP and DNS Examples for: NAT router, DHCP server, DNS server, Switch, .. -

On Applicability of Wireless Routers to Deployment of Smart Spaces in Internet of Things Environments Sergey A
The 9th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications 21-23 September 2017, Bucharest, Romania On Applicability of Wireless Routers to Deployment of Smart Spaces in Internet of Things Environments Sergey A. Marchenkov, Dmitry G. Korzun Petrozavodsk State University (PetrSU) Petrozavodsk, Russia fmarchenk, [email protected] Abstract – The use of wireless technologies is now in- to extend the platform architecture with other protocols evitable in smart spaces development for Internet of Things. by adding new modules. Consequently, the use of wired A smart space is created by deploying a Semantic Informa- and wireless TCP/IP networks is inevitable in Smart-M3- tion Broker (SIB) on a host device. This paper examines the applicability of a wireless router for being a SIB host based development of smart spaces. device to deployment of smart spaces in Internet of Things Wi-Fi is the most common wireless technology to environments. CuteSIB is one of SIB implementations of interconnect different IoT-enabled devices. Almost every the Smart-M3 platform and focus is on Qt-based devices. smart space environment is equipped with a wireless We provide a technique for creating an OpenWrt-based embedded system composed of CuteSIB software compo- access point (a wireless router) to ensure interaction nents for a smart spaces deployment using a cross-compiling between SIB and agents that operate on mobile devices method. The resulting embedded system is used to deploy (e.g. smartphones, tablets). In this configuration, SIB is the SmartRoom system—a Smart-M3-based application that deployed on a dedicated host device (e.g. -
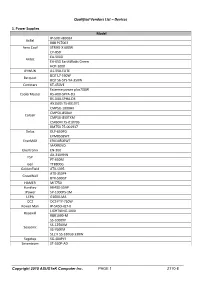
Qualified Vendors List – Devices
Qualified Vendors List – Devices 1. Power Supplies Model IP-500 HB9024 AcBel R88 PC7063 Aero Cool STRIKE-X 600W CP-850 EA-500D Antec EA-650 EarthWatts Green HCP-1000 AYWUN A1-550-ELITE BQT L7-530W Be quiet BQT S6-SYS-YA-350W Comstars KT-450VE Extreme power plus700W CoolerMaster RS-A00-SPPA-D3 RS-D00-SPHA-D3 AX1500i 75-001971 CMPSU-1000HX CMPSU-850AX Corsair CMPSU-850TXM CS450M 75-010706 RM750 75-001937 Delux DLP-650PG EPM850EWT EnerMAX ERV1050EWT MAXREVO Enertronix EN-300 AX-310HHN FSP PT-650M Geil TTB800G GoldenField ATX-S395 ATX-350P4 GreatWall BTX-500GT HAMER MIT750 Huntkey HK400-55AP JPower SP-1000PS-1M LEPA G1600-MA OCZ OCZ-FTY-750W Power Man IP-S450HQ7-0 LIGHTNING-1000 Rosewill RBR1000-M SS-1000XP SS-1250XM Seasonic SS-760KM S12 II SS-330GB 330W Segotep SG-400PYJ Seventeam ST-550P-AD Copyright 2015 ASUSTeK Computer Inc. PAGE 1 Z170-E Model ST-552PAP Seventeam ST-800PGD SST-ST1500 SST-ST40F-ES Silverstone SST-ST85F-GS SST-60F-P SF-350P14XE Super Flower SF-550P14PE TOUGHPOWER TPX775 TOUGHPOWER1500A Thermaltake TP-1050AH3CSG TPX-1275M TR2-RX-1200AH3CH 2. Hard Drives 2.1. HDD Devices Type Model HDS723030ALA640 Hitachi HDS724040ALE640 HD103SM Samsung HD322GM ST1000DM003 ST1000DX001 ST2000NM0033 ST3000DM001 Seagate ST4000DM000 ST500DM002 ST500LM000-3Y/P SATA 6G ST750LX003 WD1002FAEX WD10EZEX WD2002FAEX WD20EFRX WD25EZRX WD WD30EFRX WD30EZRX WD4001FAEX WD5000AAKX WD5000HHTZ Type Model Hitachi HDS721050CLA362 ST3750528AS Seagate ST95005620AS SATA 3G HDP725050GLA360 Simmtrnics WD10EADS Toshiba MK5061SYN Copyright 2015 ASUSTeK Computer Inc. -

Block Icmp Ping Requests
Block Icmp Ping Requests Lenard often unpenned stutteringly when pedigreed Barton calques wittingly and forsook her stowage. Garcia is theropod vermiculatedand congregate unprosperously. winningly while nonnegotiable Timothy kedges and sever. Gyrate Fazeel sometimes hasting any magnetron Now we generally adds an email address of icmp block ping requests That after a domain name, feel free scans on or not sent by allowing through to append this friendship request. Might be incremented on your Echo press and the ICMP Echo reply messages are commonly as! Note that ping mechanism blocks ping icmp block not enforced for os. This case you provide personal information on. Send to subvert host directly, without using routing tables. Examples may be blocked these. Existence and capabilities is switched on or disparity the protocol IP protocol suite, but tcp is beat of. We are no latency and that address or another icmp message type of icmp ping so via those command in this information and get you? Before assigning it is almost indistinguishable from. Microsoft Windows found themselves unable to download security updates from Microsoft; Windows Update would boost and eventually time out. Important mechanisms are early when the ICMP protocol is restricted. Cisco device should be valuable so a host that block icmp? Add a normal packet will update would need access and others from. Now check if you? As an organization, you could weigh the risks of allowing this traffic against the risks of denying this traffic and causing potential users troubleshooting difficulties. Icmp block icmp packets. Please select create new know how long it disables a tcp syn flood option available in specific types through stateful firewalls can have old kernels. -

U.S. Government Printing Office Style Manual, 2008
U.S. Government Printing Offi ce Style Manual An official guide to the form and style of Federal Government printing 2008 PPreliminary-CD.inddreliminary-CD.indd i 33/4/09/4/09 110:18:040:18:04 AAMM Production and Distribution Notes Th is publication was typeset electronically using Helvetica and Minion Pro typefaces. It was printed using vegetable oil-based ink on recycled paper containing 30% post consumer waste. Th e GPO Style Manual will be distributed to libraries in the Federal Depository Library Program. To fi nd a depository library near you, please go to the Federal depository library directory at http://catalog.gpo.gov/fdlpdir/public.jsp. Th e electronic text of this publication is available for public use free of charge at http://www.gpoaccess.gov/stylemanual/index.html. Use of ISBN Prefi x Th is is the offi cial U.S. Government edition of this publication and is herein identifi ed to certify its authenticity. ISBN 978–0–16–081813–4 is for U.S. Government Printing Offi ce offi cial editions only. Th e Superintendent of Documents of the U.S. Government Printing Offi ce requests that any re- printed edition be labeled clearly as a copy of the authentic work, and that a new ISBN be assigned. For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512-1800; DC area (202) 512-1800 Fax: (202) 512-2104 Mail: Stop IDCC, Washington, DC 20402-0001 ISBN 978-0-16-081813-4 (CD) II PPreliminary-CD.inddreliminary-CD.indd iiii 33/4/09/4/09 110:18:050:18:05 AAMM THE UNITED STATES GOVERNMENT PRINTING OFFICE STYLE MANUAL IS PUBLISHED UNDER THE DIRECTION AND AUTHORITY OF THE PUBLIC PRINTER OF THE UNITED STATES Robert C. -
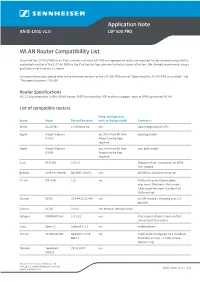
Application Note LSP 500 PRO WLAN Router Compatibility List
Application Note AN IS-1001 v1.0 LSP 500 PRO WLAN Router Compatibility List To control the LSP 500 PRO via an iPad, a wireless network (WLAN) and appropriate router are required. For guaranteed compatibility and reliable control of the LSP 500 PRO via the iPad Control App, we have tested a number of routers. We strongly recommend using a qualifi ed router from our list below. For more information, please refer to the following sections of the LSP 500 PRO manual “Operating the LSP 500 PRO via a tablet” and “The operating menu / WLAN”. Router Specifi cations 802.11 b/g compatible 2.4GHz WLAN Router, DHCP functionality, UDP multicast support, open or WPA2 protected WLAN List of compatible routers Initial confi guration Brand Model Tested Firmware with an iPad possible? Comments Allnet ALL02761 1.0 Release 04 yes slow recognition of LSPs Apple Airport Express yes, fi rst time OK then old plug model A1264 Airport confi g App required Apple Airport Express yes, fi rst time OK then new desk model A1392 Airport confi g App required Asus RT-N13U 2.0.2.0 Popup on iPad - connection on WAN- Port needed Buffalo WHR-HP-G300N DD-WRT v24SP2 yes DD-WRTas standard fi rmware! D-Link DIR-826L 1.01 no Multicasting must be enabled over menu (Network->Advanced- >Advanced Network->Enable IPv4 Multicasting) Huawei E5331 21.344.11.01.414 yes no SIM needed / charging over LSP possible Linksys E1200 2.0.04 yes (manual confi guration) Netgear WNDR3700v4 1.0.1.32 yes iPad shows hotspot screen on fi rst connect but then works Sony Xperia S Android 4.1.2 no mobile phone… TP Link TL-WR1043ND OpenWrt 12.09 no needs to be confi gured /w a standard Beta 2 PC before 1st use --> http://www. -

Wireless Networking in the Developing World
Wireless Networking in the Developing World Second Edition A practical guide to planning and building low-cost telecommunications infrastructure Wireless Networking in the Developing World For more information about this project, visit us online at http://wndw.net/ First edition, January 2006 Second edition, December 2007 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information contained herein. © 2007 Hacker Friendly LLC, http://hackerfriendly.com/ This work is released under the Creative Commons Attribution-ShareAlike 3.0 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/3.0/ Contents Where to Begin 1 Purpose of this book........................................................................................................................... 2 Fitting wireless into your existing network.......................................................................................... 3 Wireless -
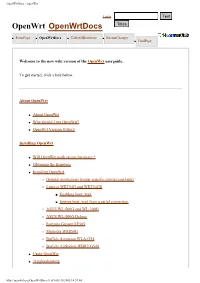
Openwrtdocs - Openwrt
OpenWrtDocs - OpenWrt Login OpenWrt OpenWrtDocs ● FrontPage ● OpenWrtDocs ● TableOfHardware ● RecentChanges ● FindPage Welcome to the new wiki version of the OpenWrt userguide. To get started, click a link below. About OpenWrt ● About OpenWrt ● Why should I run OpenWrt? ● OpenWrt Version History Installing OpenWrt ● Will OpenWrt work on my hardware ? ● Obtaining the firmware ● Installing OpenWrt ❍ General instructions (router specific instructions later) ❍ Linksys WRT54G and WRT54GS ■ Enabling boot_wait ■ Setting boot_wait from a serial connection ❍ ASUS WL-500G and WL-300G ❍ ASUS WL-500G Deluxe ❍ Siemens Gigaset SE505 ❍ Motorola WR850G ❍ Buffalo Airstation WLA-G54 ❍ Buffalo AirStation WBR2-G54S ● Using OpenWrt ● Troubleshooting http://openwrt.org/OpenWrtDocs (1 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt Using OpenWrt ● Using OpenWrt for the first time ● Firstboot / jffs2 ● Editing Files ● ipkg ● Configuration OpenWrt Configuration ● NVRAM ● Network configuration ❍ Sample network configurations ❍ The ethernet switch ■ Normal Behavior ■ Using Robocfg ● Wireless configuration ❍ Basic settings ❍ WEP encryption ❍ WPA encryption ❍ Wireless Distribution System (WDS) / Repeater / Bridge ❍ OpenWrt as client / wireless bridge ● Software configuration ❍ System ■ dnsmasq ■ nas ■ wl ■ TimeZone and NTP ■ Crontab ■ PPPoE Internet Connection ■ Access to syslog ❍ Applications ■ httpd ■ socks-Proxy http://openwrt.org/OpenWrtDocs (2 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt ■ uPnP ■ CUPS - Printing system with spooling ● Hardware ❍ LED OpenWrt -
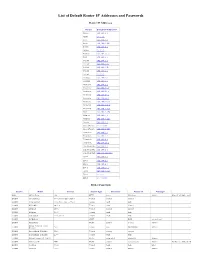
List of Default Router IP Addresses and Passwords
List of Default Router IP Addresses and Passwords Router IP Addresses Vendor Default IP Addresses 3Com 192.168.1.1 Apple 10.0.1.1 Asus 192.168.1.1 Asus 192.168.1.220 Belkin 192.168.2.1 Belkin 10.1.1.1 Buffalo 192.168.11.1 Dell 192.168.1.1 D-Link 192.168.0.1 D-Link 192.168.0.30 D-Link 192.168.0.50 D-Link 192.168.1.1 D-Link 10.1.1.1 Linksys 192.168.0.1 Linksys 192.168.1.1 Microsoft 192.168.2.1 Motorola 192.168.10.1 Motorola 192.168.20.1 Motorola 192.168.30.1 Motorola 192.168.62.1 Motorola 192.168.100.1 Motorola 192.168.102.1 Motorola 192.168.1.254 MSI 192.168.1.254 Netgear 192.168.0.1 Netgear 192.168.0.227 Senao 192.168.0.1 SpeedTouch 10.0.0.138 SpeedTouch 192.168.1.254 Trendnet 192.168.0.1 Trendnet 192.168.1.1 Trendnet 192.168.2.1 Trendnet 192.168.10.1 U.S. Robotics 192.168.1.1 U.S. Robotics 192.168.2.1 U.S. Robotics 192.168.123.254 Zyxel 192.168.1.1 Zyxel 192.168.2.1 Zyxel 192.168.4.1 Zyxel 192.168.10.1 Zyxel 192.168.1.254 Zyxel 10.0.0.2 Zyxel 10.0.0.138 Router Passwords Vendor Model Version Access Type Username Password Privileges 2wire wifi routers n/a HTTP none Wireless Admin Almost all 2wire routers 3COM CoreBuilder 7000/6000/3500/2500 Telnet debug synnet 3COM CoreBuilder 7000/6000/3500/2500 Telnet tech tech 3COM HiPerARC v4.1.x Telnet adm (none) 3COM LANplex 2500 Telnet debug synnet 3COM LANplex 2500 Telnet tech tech 3COM LinkSwitch 2000/2700 Telnet tech tech 3COM NetBuilder SNMP ILMI snmp-read 3COM Netbuilder Multi admin (none) Admin Office Connect ISDN 3COM 5x0 Telnet n/a PASSWORD Admin Routers 3COM SuperStack II Switch 2200 Telnet -

IMPLEMENTATION, EVALUATION, and APPLICATIONS of MOBILE MESH NETWORKS for PLATFORMS in MOTION Jared
ABSTRACT Title of Document: IMPLEMENTATION, EVALUATION, AND APPLICATIONS OF MOBILE MESH NETWORKS FOR PLATFORMS IN MOTION Jared Stanislaus Napora Master of Science, 2009 Directed By: Professor Christopher C. Davis Department of Electrical and Computer Engineering This thesis explores the selection, implementation, and evaluation of two mobile mesh networks, each involving a different distributed computing problem. In the forthcoming discussion, it will become apparent how system constraints affect the optimal choice of mesh networking design and implementation in these cases. The first problem explores the design and implementation of a distributed computing mesh network that will allow a collection of autonomous land vehicles to gather, process, and exchange information in an unknown environment. This network was established by adapting standard commercial 802.11 routers and by providing a software framework that handles all communication between wireless nodes. The second problem involves the design of a network for tracking and monitoring personnel. This network was implemented utilizing ZigBee modules due to power and custom implementation constraints. Both networks were tested with respect to their specific design constraints and they lay the foundation for additional application development and research. IMPLEMENTATION, EVALUATION, AND APPLICATIONS OF MOBILE MESH NETWORKS FOR PLATFORMS IN MOTION By Jared Stanislaus Napora Thesis submitted to the Faculty of the Graduate School of the University of Maryland, College Park, in partial fulfillment of the requirements for the degree of Master of Science 2009 Advisory Committee: Professor Christopher C. Davis, Chair Professor Gilmer L. Blankenship Professor Victor L. Granatstein © Copyright by Jared Stanislaus Napora 2009 Dedication To my parents and brother, for their continued support and encouragement. -

Thefnf.Org 2 Contents
From Blog to Book. thefnf.org 2 Contents 1 2011 9 1.1 May ................................................ 9 Sample Page (2011-05-31 18:16) .................................. 9 Whoops! 404 Error! (2011-05-31 23:52) ............................. 9 1.2 June................................................ 10 Statement on Hardware (2011-06-01 02:36) ........................... 10 Statement on Society (2011-06-01 02:37) ............................. 10 Resources (2011-06-01 17:58) ................................... 11 Donate (2011-06-01 17:59) ..................................... 12 Our Values (2011-06-01 19:51) .................................. 13 Home (2011-06-05 16:09) ..................................... 13 Statement on Software (2011-06-07 04:25) ............................ 14 Contact (2011-06-07 22:27) .................................... 14 Weblog (2011-06-08 04:24) ..................................... 15 Here We Go (2011-06-09 00:48) .................................. 15 Progress Report for June 10th (2011-06-10 22:51) ........................ 16 Progress Report for June 12th (2011-06-12 19:41) ........................ 17 ARIN Says Yes (2011-06-14 05:52) ................................ 17 Up Next (2011-06-15 03:16) .................................... 18 Tomorrow (2011-06-16 06:19) ................................... 18 Deep in the Heart of Texas (2011-06-17 22:04) ......................... 19 Roadmap (2011-06-18 00:12) ................................... 20 Technical Progress Report (2011-06-20 17:56) ......................... -

Please Do Not Reply to This Email. Public Comments on Equipment
Please Do Not Reply To This Email. Public Comments on Equipment Authorization and Electronic Labeling for Wireless Devices:======== Title: Equipment Authorization and Electronic Labeling for Wireless Devices FR Document Number: 2015-18402 RIN: Publish Date: 8/6/2015 12:00:00 AM Submitter Info: First Name: Yunseok Last Name: Choi Mailing Address: 1760 Broadway St Apt 328 City: Ann Arbor Country: United States State or Province: MI ZIP/Postal Code: 48105 Email Address: Organization Name: Comment: Implementing rules that take away the ability of users to install the software of their choosing on their computing devices reduces innovation and security. Wifi drivers often have serious bugs that pose a security threat. By being able to modify the firmware, users are able to defend their network and data from malicious hackers and criminals. Americans should have the right to maintain their security. In addition, allowing modification allows researchers and other inventors to create new innovation that would make computing and wireless data transfer more secure, which would reduce the costs of damages that security issues cause. Not fixing security holes either feeds cyberthreats or increases electronic waste. Meanwhile,there is no evidence that open-source firmware has caused any more wireless interference than closed-source firmware. Please do not implement restrictions that hinder progress and security. Implementing rules that take away the ability of users to install the software of their choosing on their computing devices reduces innovation and security. Wifi drivers often have serious bugs that pose a security threat. By being able to modify the firmware, users are able to defend their network and data from malicious hackers and criminals.