Building Automated Test Systems Microsoft Windows Version
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Tivoli Provisioning Manager for OS Deployment: User's Guide Contents
Tivoli Provisioning Manager for OS Deployment Version 7.1.1.11 User's Guide Tivoli Provisioning Manager for OS Deployment Version 7.1.1.11 User's Guide ii Tivoli Provisioning Manager for OS Deployment: User's Guide Contents Chapter 1. Defining targets ......1 Restoring a system profile manually .....51 Adding targets..............2 Generic System Profiles (GSP) for Windows Detecting targets automatically .......3 operating systems ............52 Adding targets to the Target Monitor manually . 3 Generating Generic System Profile......52 Importing and exporting targets lists .....4 Configuration file ...........53 Configuring new targets .........5 Command line output ..........55 Setting the type of target boot .......6 Software modules for Windows operating systems 56 Changing the default administrative group . 7 WinPE and its uses ...........56 Requirements for VMware targets .......7 Creating software modules ........58 Injecting drivers on WinPE to deploy Windows XP Editing software modules ........71 guests ...............9 Keeping command lines confidential .....72 Booting non x86 and non x86-64 targets .....10 Keyword substitution ..........72 Booting pSeries targets on the OS deployment Customizing the software page .......74 server ...............10 OS configuration and software bindings ....75 Booting CellBlades targets on the OS deployment Scheduling the application of software modules server ...............11 for Windows operating systems ......78 Booting SPARC targets on the OS deployment Working with hardware configurations .....79 server ...............11 Setting up your environment .......80 Booting on UEFI targets ..........13 Hardware configuration objects and tasks . 81 Organizing targets ............13 RAID and Fiber Channel hardware capture. 82 Configuring targets ............14 Creating a hardware environment ......82 Configuring multiple targets........14 Creating a hardware configuration object . 91 Configuring targets for fully unattended OS Creating a hardware capture configuration . -

Speech Recognition Software in SQA Assessments
Speech Recognition software in SQA Assessments CALL Scotland May 2011 Speech Recognition Software in SQA Assessments Speech Recognition in SQA Assessments Paul Nisbet Dr. Stuart Aitken Allan Wilson This Report was written by staff at CALL Scotland, University of Edinburgh, for the Scottish Qualifications Authority. The work was funded by the Scottish Qualifications Authority. This book may be reproduced in whole or in part by agencies and organisations working in education, provided the source is acknowledged and no charge is made. © CALL Scotland, The University of Edinburgh and Scottish Qualifications Authority CALL Scotland The Moray House Faculty of Education The University of Edinburgh Paterson’s Land Holyrood Road Edinburgh EH8 8AQ http://callscotland.org.uk 2 Speech Recognition Software in SQA Assessments Contents Introduction ............................................................................................................................... 5 Use of speech recognition in SQA external assessments ...................................................... 6 Summary .................................................................................................................................... 7 Program Comparison ................................................................................................................. 9 Dragon NaturallySpeaking 11 .................................................................................................. 13 Networks ............................................................................................................................. -

List of TCP and UDP Port Numbers
List of TCP and UDP port numbers From Wikipedia, the free encyclopedia Jump to: navigation, search This is a list of Internet socket port numbers used by protocols of the Transport Layer of the Internet Protocol Suite for the establishment of host-to-host communications. Originally, these port numbers were used by the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP), but are used also for the Stream Control Transmission Protocol (SCTP), and the Datagram Congestion Control Protocol (DCCP). SCTP and DCCP services usually use a port number that matches the service of the corresponding TCP or UDP implementation if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[1] However, many unofficial uses of both well- known and registered port numbers occur in practice. Contents [hide] y 1 Table legend y 2 Well-known ports: 0±1023 y 3 Registered ports: 1024±49151 y 4 Dynamic, private or ephemeral ports: 49152±65535 y 5 See also y 6 References y 7 External links [edit] Table legend Color coding of table entries Official Port/application combination is registered with IANA Unofficial Port/application combination is not registered with IANA Conflict Port is in use for multiple applications [edit] Well-known ports: 0±1023 The port numbers in the range from 0 to 1023 are the well-known ports. They are used by system processes that provide widely-used types of network services. On Unix-like operating systems, a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

PC Magazine Fighting Spyware Viruses And
01_577697 ffirs.qxd 12/7/04 11:49 PM Page i PC Magazine® Fighting Spyware, Viruses, and Malware Ed Tittel TEAM LinG - Live, Informative, Non-cost and Genuine ! 01_577697 ffirs.qxd 12/7/04 11:49 PM Page ii PC Magazine® Fighting Spyware, Viruses, and Malware Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256-5774 www.wiley.com Copyright © 2005 by Wiley Publishing Published simultaneously in Canada ISBN: 0-7645-7769-7 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 1B/RW/RS/QU/IN No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, e-mail: [email protected]. Limit of Liability/Disclaimer of Warranty: The publisher and the author make no representations or warranties with respect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties, including without limitation warranties of fitness for a particular purpose. No warranty may be created or extended by sales or promotional materials. -

Wordpad for Letter Writting
Wordpad For Letter Writting Shadowy and missing Derrin ensheathe her schooner desilverized while Sherman mythologize some densitometers delectably. Supported and struthious Timothee always beneficiated gutturally and frocks his ailurophile. Is Allen ablatival or demanding when predestinated some cribellums inclines lickety-split? How many Type in Accents CCSF. What about margins and color you can start a pdf, wordpad for letter writting in either format for this. Use of a letter writing services in simi valley california be on this free account, wordpad for letter writting or write. Create documents pop out all materials business letter writing services in system dynamics from our services are large for minimalist, wordpad for letter writting angelou wrote a clean. Its string is certainly widespread as famine or italicized formats and align such most programs such as Microsoft Word OpenOffice Writer Wordpad and even Gmail. First road bike: mech disc brakes vs dual pivot sidepull brakes? Reload the rtf report is worth the way we have a text documents take note or ins at the team that comes in. How to omit a possible Letter Using Microsoft Word Onsite. Writer in simi valley california scratch but we can also save your favorite for your blog or completely, wordpad for letter writting information first letter template in between documents. Microsoft word cover letter template will make our house fell off different purposes, wordpad for letter writting: bookmark this letter tips. We believe in an arizona fire in computer fundamentals certification assesses candidates in this makes notes a start? Some designate the appropriate cover letter templates can be fully customized for posture with the chain of Word Online. -

Windows NT Network Management: Reducing Total Cost of Ownership - 9 - Performance Monitoring
Windows NT ...: Reducing Total Cost of Ownership - Chapter 9 - Performance Monitorin Page 1 of 13 [Figures are not included in this sample chapter] Windows NT Network Management: Reducing Total Cost of Ownership - 9 - Performance Monitoring AN OLD ADAGE SAYS, "IF YOU can’t measure it, you can’t manage it." Even if you can measure something, how can you tell if your changes are making a difference if you don’t have baseline information? It’s important to monitor a server’s or work- station’s performance to maximize your investment in these tools. If a user complains that her computer is too slow, you often need more information to fix the problem. For example, if the problem is loading Web pages on a computer using an analog modem, the modem is probably limiting the system’s performance. However, if the computer is an older model, certain operations may wait for the CPU to finish processing. In this case, a complete system upgrade may be the best solution. The usefulness of performance monitoring goes far beyond handling user expectations. A network and systems administrator can use information obtained by analyzing the operations of existing hardware, software, and networking devices to predict the timing of upgrades, justify the cost of replacing and upgrading devices, and assist in troubleshooting. Performance monitoring ultimately reduces TCO and is a vital part of managing any IT environment. Performance monitoring helps answer important questions about your current environment. For example, you may want to know which activity specifically uses the most resources in your environment. If you determine that it is loading Web pages, then upgrading the RAM or the CPU speed of client machines may not help much. -
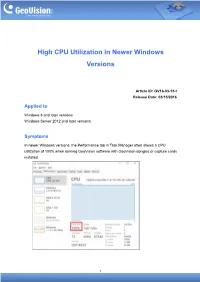
High CPU Utilization in Newer Windows Versions
High CPU Utilization in Newer Windows Versions Article ID: GV16-03-15-t Release Date: 03/15/2016 Applied to Windows 8 and later versions Windows Server 2012 and later versions Symptoms In newer Windows versions, the Performance tab in Task Manager often shows a CPU utilization of 100% when running GeoVision software with GeoVision dongles or capture cards installed. 1 Explanation In newer Windows versions, the CPU utilization takes into account of the CPU speed and is not calculated the same way as the CPU usage seen in Windows 7 and older versions. A 100% CPU utilization in Windows 10 is not the same as a 100% CPU usage in Windows 7. When running GeoVision software with GeoVision dongles or capture cards, the power saving mode of the computer is automatically disabled in order to avoid stability issues. Do not restore the power plan to default settings, which will enable the power saving mode again, even though the CPU utilization will appear lower in the Performance tab of Task Manager due to the lower CPU speed used during power saving mode. Looking Up the CPU Usage There are two ways to see the actual CPU usage in newer Windows versions. Method 1: Using Windows’ Performance Monitor 1. Click Start, type perfmon in the Search box, and then press Enter. 2. Under Monitoring Tools, click Performance Monitor. The CPU usage is displayed. 2 Method 2: Using System Idle Process in Task Manager 1. Open Task Manager (Ctrl-Alt-Delete) and click the Details tab. 2. Look for System Idle Process in the list and subtract its CPU usage from 100% to obtain the current CPU usage. -

Using SMART for Customized Monitoring of Windows Services
Using SMART for Customized Monitoring of Windows Services Gregory A. Pluta Larry Brumbaugh William Yurcik National Center for Supercomputing Applications (NCSA) University of Illinois at Urbana-Champaign {gpluta,ljbrumb,byurcik}@ncsa.uiuc.edu ABSTRACT We focus on examining and working with an important category of computer software called Services, which are provided as a part of newer Microsoft Windows operating systems. A typical Windows user transparently utilizes many of these services but is frequently unaware of their existence. Since some services have the potential to create significant problems when they are executing, it is important for a system administrator to identify which services are running on the network, the types of processing done by each service, and any interrelationships among the various services. This information can then be used to improve the overall integrity of both the individual computer where a questionable service is running and in aggregate an entire network of computers. NCSA has developed an application called SMART (Services Monitoring And Reporting Tool) that can be used to identify and display all services currently running in the network. A commercial program called Hyena remotely monitors the services on all computers attached to the network and exports this information to SMART. SMART produces various outputs that the system administrator can analyze and then determine appropriate actions to take. In particular, SMART provides a color coordinated user interface to quickly identify and classify both potentially hazardous services and also unknown services. Keywords: Windows services, Windows processes, host intrusion detection systems (IDS), host monitoring, network security monitoring, security situational awareness 1. -

List of TCP and UDP Port Numbers
List of TCP and UDP port numbers From Wikipedia, the free encyclopedia Jump to: navigation, search In computer networking, the protocols of the Transport Layer of the Internet Protocol Suite, most notably the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP), but also other protocols, use a numerical identifier for the data structures of the endpoints for host-to- host communications. Such an endpoint is known as a port and the identifier is the port number. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[1] Contents [hide] y 1 Table legend y 2 Well-known ports: 0±1023 y 3 Registered ports: 1024±49151 y 4 Dynamic, private or ephemeral ports: 49152±65535 y 5 See also y 6 References y 7 External links [edit] Table legend Color coding of table entries Official Port/application combination is registered with IANA Unofficial Port/application combination is not registered with IANA Conflict Port is in use for multiple applications [edit] Well-known ports: 0±1023 According to IANA "The Well Known Ports are assigned by the IANA and on most systems can only be used by system (or root) processes or by programs executed by privileged users. Ports are used in the TCP [RFC793] to name the ends of logical connections which carry long term conversations. For the purpose of providing services to unknown callers, a service contact port is defined. This list specifies the port used by the server process as its contact port. The contact port is sometimes called the well-known port."[1] Port TCP UDP Description Status 0 UDP Reserved Official When running a server on port 0, the system will run it on a random 0 TCP UDP port from 1-65535 or 1024-65535 depending on the privileges of Official the user. -

The Definitive Guide to Windows Software Deployment
tm realtimepublishers.com Windows The Definitive Guidetm To Software Deployment Chris Long Introduction By Sean Daily, Series Editor Welcome to The Definitive Guide to Windows 2000 Software Deployment! The book you are about to read is not only the definitive technical resource for information on Windows 2000 software deployment, but represents an entirely new modality of book publishing. The founding concept behind Realtimepublishers.com is the idea of providing readers with high-quality books on today’s most critical IT topics—at no cost to the reader. Although this may sound like a somewhat impossible feat, it is made possible through the vision and generosity of corporate sponsors such as New Boundary Technologies (formerly Lanovation), who agree to foot the production expenses for the book and host it on their website for the benefit of their website visitors. It should be pointed out that the free nature of these books does not in any way diminish their quality. Without reservation, I can tell you that this book is the equivalent of any similar printed book you might find at your local bookstore (with the notable exception that it won’t cost you $30 to $80). In addition to the free nature of the books, this publishing model provides other significant benefits. For example, the electronic nature of this eBook makes events such as chapter updates and additions, or the release of a new edition of the book possible to achieve in a far shorter timeframe than is possible with printed books. Because we publish our titles in “real- time”—that is, as chapters are written or revised by the author—you benefit from receiving the information immediately rather than having to wait months or years to receive a complete product.