The Evolution of Internet Congestion
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Pando Booster Free Download
Pando booster free download CLICK TO DOWNLOAD pando media booster free download - Bass Booster For Media Player, Volume Booster, Free Game Booster, and many more programs. Pando is free, secure software that makes sending, receiving, and publishing files up to 1GB in size a breeze. Need to e-mail large attachments, IM a folder, orSubcategory: P2P & File-Sharing Software. Pando Media Booster is a small application that accelerates the download of large games and software through Pando Content Delivery Cloud. Pando Media Booster, also known as PMB (or renuzap.podarokideal.ru), is used to download some of the most popular MMOs in the industry, such as MapleStory, League of Legends, LOTRO, and many more.4/5(29). Pando also employs a redundancy checker for every byte that the client downloads, which avoids errors or corrupt data that would otherwise be present in other forms of game or software download and installation packages. The Pando Media Booster uses the same protocol and technique as Pando’s other products; it uses the BitTorrent protocol to. Pinnacle Studio 16 Pando Media Booster corel paint shop pro x8 has stopped working microsoft powerpoint templates used photoshop software for saleflip4mac player pro free rosetta stone cheapest latin america spanish microsoft access comprehensive pdf freeIn some cases with Studio 16 download installations Pando Media Booster may fail. Easily download and send large files, media and entire folders for free with Pando, the award-winning, personal file sharing software. Pando is installed by 25 million people, and % Clean: no spyware or . 7/9/ · Please visit the main page of Media - Pando Media Booster on Software Informer. -

P2P Business Applications: Future and Directions
Communications and Network, 2012, 4, 248-260 http://dx.doi.org/10.4236/cn.2012.43029 Published Online August 2012 (http://www.SciRP.org/journal/cn) P2P Business Applications: Future and Directions Pankaj Pankaj, Micki Hyde, James A. Rodger MIS and Decision Sciences, Eberly College of Business & Information Technology, Indiana University of Pennsylvania, Indiana, USA Email: [email protected] Received May 20, 2012; revised June 18, 2012; accepted July 17, 2012 ABSTRACT Since the launch of Napster in June 1999, peer-to-peer technology (P2P) has become synonymous with file sharing ap- plications that are the bane of the recording industry due to copyright infringements and consequent revenue losses. P2P promised a revolution in business computing which has not arrived. It has become synonymous with illegal file sharing and copyright violations. Meanwhile the information systems industry has undergone a paradigm change, and we are supposedly living in a world of cloud computing and mobile devices. It is pertinent to examine if P2P, as a revolution- ary technology, is still relevant and important today and will be in future. One has to examine this question in the con- text of the fact that P2P technologies have matured but have however had limited adoption outside file-sharing in the consumer space. This paper provides a detailed analysis of P2P computing and offers some propositions to answer the question of the relevancy of P2P. It is proposed that P2P is still a relevant technology but may be reshaped in the com- ing years in a different form as compared to what exists today. -

Application Note Pre-Deployment and Network Readiness Assessment Is
Application Note Contents Title Six Steps To Getting Your Network Overview.......................................................... 1 Ready For Voice Over IP Pre-Deployment and Network Readiness Assessment Is Essential ..................... 1 Date January 2005 Types of VoIP Overview Performance Problems ...... ............................. 1 This Application Note provides enterprise network managers with a six step methodology, including pre- Six Steps To Getting deployment testing and network readiness assessment, Your Network Ready For VoIP ........................ 2 to follow when preparing their network for Voice over Deploy Network In Stages ................................. 7 IP service. Designed to help alleviate or significantly reduce call quality and network performance related Summary .......................................................... 7 problems, this document also includes useful problem descriptions and other information essential for successful VoIP deployment. Pre-Deployment and Network IP Telephony: IP Network Problems, Equipment Readiness Assessment Is Essential Configuration and Signaling Problems and Analog/ TDM Interface Problems. IP Telephony is very different from conventional data applications in that call quality IP Network Problems: is especially sensitive to IP network impairments. Existing network and “traditional” call quality Jitter -- Variation in packet transmission problems become much more obvious with time that leads to packets being the deployment of VoIP service. For network discarded in VoIP -

Latency and Throughput Optimization in Modern Networks: a Comprehensive Survey Amir Mirzaeinnia, Mehdi Mirzaeinia, and Abdelmounaam Rezgui
READY TO SUBMIT TO IEEE COMMUNICATIONS SURVEYS & TUTORIALS JOURNAL 1 Latency and Throughput Optimization in Modern Networks: A Comprehensive Survey Amir Mirzaeinnia, Mehdi Mirzaeinia, and Abdelmounaam Rezgui Abstract—Modern applications are highly sensitive to com- On one hand every user likes to send and receive their munication delays and throughput. This paper surveys major data as quickly as possible. On the other hand the network attempts on reducing latency and increasing the throughput. infrastructure that connects users has limited capacities and These methods are surveyed on different networks and surrond- ings such as wired networks, wireless networks, application layer these are usually shared among users. There are some tech- transport control, Remote Direct Memory Access, and machine nologies that dedicate their resources to some users but they learning based transport control, are not very much commonly used. The reason is that although Index Terms—Rate and Congestion Control , Internet, Data dedicated resources are more secure they are more expensive Center, 5G, Cellular Networks, Remote Direct Memory Access, to implement. Sharing a physical channel among multiple Named Data Network, Machine Learning transmitters needs a technique to control their rate in proper time. The very first congestion network collapse was observed and reported by Van Jacobson in 1986. This caused about a I. INTRODUCTION thousand time rate reduction from 32kbps to 40bps [3] which Recent applications such as Virtual Reality (VR), au- is about a thousand times rate reduction. Since then very tonomous cars or aerial vehicles, and telehealth need high different variations of the Transport Control Protocol (TCP) throughput and low latency communication. -

Lab 6: Understanding Traditional TCP Congestion Control (HTCP, Cubic, Reno)
NETWORK TOOLS AND PROTOCOLS Lab 6: Understanding Traditional TCP Congestion Control (HTCP, Cubic, Reno) Document Version: 06-14-2019 Award 1829698 “CyberTraining CIP: Cyberinfrastructure Expertise on High-throughput Networks for Big Science Data Transfers” Lab 6: Understanding Traditional TCP Congestion Control Contents Overview ............................................................................................................................. 3 Objectives............................................................................................................................ 3 Lab settings ......................................................................................................................... 3 Lab roadmap ....................................................................................................................... 3 1 Introduction to TCP ..................................................................................................... 3 1.1 TCP review ............................................................................................................ 4 1.2 TCP throughput .................................................................................................... 4 1.3 TCP packet loss event ........................................................................................... 5 1.4 Impact of packet loss in high-latency networks ................................................... 6 2 Lab topology............................................................................................................... -

Network Neutrality: a Matter Suitable for Public Policy
Prof. Ing. Vittorio Trecordi Comitato Scientifico FUB Politecnico di Milano – ICT Consulting SpA “Neutralità della rete e aspetti socio-economici” Roma – May 14, 2009 Putting things into context Network Neutrality: a matter suitable for public policy X Network Neutrality is about establishing policy rules on the behaviour of network providers - The focus is on broadband Internet X The term is being used in a lot of different contexts, covers a number of topics and creates matters suitable for public policy in many regions of the World: - Protection against anti-economic behaviours: • Traffic discrimination (e.g. prioritization) to favour the business of the network provider - Protection of individual rights: • Inspecting traffic to apply traffic management policies or to derive information suitable for targeted advertisement (Privacy concern) • Discriminating the access to network resources (Digital Divide, Free Speech, limitation of end-users’ property rights and barriers to innovation) - Protection of commercial rights : • Inspecting traffic and blocking protocols used to share contents (Digital rights protection) - Protection against terrorism and crime: • Inspecting and blocking traffic that compromise the capability to identify users and to apply content interception (Non-repudiation and lawful interception) Intervento di Vittorio Trecordi – Comitato Scientifico FUB Date: 14/05/2009 Neutralità della rete e aspetti socio-economici Pagina 2 Putting things into context Network Neutrality: a matter suitable for public policy X Distinguish -

Adaptive Method for Packet Loss Types in Iot: an Naive Bayes Distinguisher
electronics Article Adaptive Method for Packet Loss Types in IoT: An Naive Bayes Distinguisher Yating Chen , Lingyun Lu *, Xiaohan Yu * and Xiang Li School of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China; [email protected] (Y.C.); [email protected] (X.L.) * Correspondence: [email protected] (L.L.); [email protected] (X.Y.) Received: 31 December 2018; Accepted: 23 January 2019; Published: 28 January 2019 Abstract: With the rapid development of IoT (Internet of Things), massive data is delivered through trillions of interconnected smart devices. The heterogeneous networks trigger frequently the congestion and influence indirectly the application of IoT. The traditional TCP will highly possible to be reformed supporting the IoT. In this paper, we find the different characteristics of packet loss in hybrid wireless and wired channels, and develop a novel congestion control called NB-TCP (Naive Bayesian) in IoT. NB-TCP constructs a Naive Bayesian distinguisher model, which can capture the packet loss state and effectively classify the packet loss types from the wireless or the wired. More importantly, it cannot cause too much load on the network, but has fast classification speed, high accuracy and stability. Simulation results using NS2 show that NB-TCP achieves up to 0.95 classification accuracy and achieves good throughput, fairness and friendliness in the hybrid network. Keywords: Internet of Things; wired/wireless hybrid network; TCP; naive bayesian model 1. Introduction The Internet of Things (IoT) is a new network industry based on Internet, mobile communication networks and other technologies, which has wide applications in industrial production, intelligent transportation, environmental monitoring and smart homes. -

David D. Clark
Designs for an Internet David D. Clark Dra Version 3.0 of Jan 1, 2017 David D. Clark Designs for an Internet Status is version of the book is a pre-release intended to get feedback and comments from members of the network research community and other interested readers. Readers should assume that the book will receive substantial revision. e chapters on economics, management and meeting the needs of society are preliminary, and comments are particularly solicited on these chapters. Suggestions as to how to improve the descriptions of the various architectures I have discussed are particularly solicited, as are suggestions about additional citations to relevant material. For those with a technical background, note that the appendix contains a further review of relevant architectural work, beyond what is in Chapter 5. I am particularly interesting in learning which parts of the book non-technical readers nd hard to follow. Revision history Version 1.1 rst pre-release May 9 2016. Version 2.0 October 2016. Addition of appendix with further review of related work. Addition of a ”Chapter zero”, which provides an introduction to the Internet for non-technical readers. Substantial revision to several chapters. Version 3.0 Jan 2017 Addition of discussion of Active Nets Still missing–discussion of SDN in management chapter. ii 178 David D. Clark Designs for an Internet A note on the cover e picture I used on the cover is not strictly “architecture”. It is a picture of the Memorial to the Mur- dered Jews of Europe, in Berlin, which I photographed in 2006. -
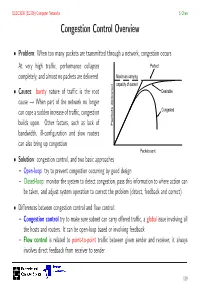
Congestion Control Overview
ELEC3030 (EL336) Computer Networks S Chen Congestion Control Overview • Problem: When too many packets are transmitted through a network, congestion occurs At very high traffic, performance collapses Perfect completely, and almost no packets are delivered Maximum carrying capacity of subnet • Causes: bursty nature of traffic is the root Desirable cause → When part of the network no longer can cope a sudden increase of traffic, congestion Congested builds upon. Other factors, such as lack of Packets delivered bandwidth, ill-configuration and slow routers can also bring up congestion Packets sent • Solution: congestion control, and two basic approaches – Open-loop: try to prevent congestion occurring by good design – Closed-loop: monitor the system to detect congestion, pass this information to where action can be taken, and adjust system operation to correct the problem (detect, feedback and correct) • Differences between congestion control and flow control: – Congestion control try to make sure subnet can carry offered traffic, a global issue involving all the hosts and routers. It can be open-loop based or involving feedback – Flow control is related to point-to-point traffic between given sender and receiver, it always involves direct feedback from receiver to sender 119 ELEC3030 (EL336) Computer Networks S Chen Open-Loop Congestion Control • Prevention: Different policies at various layers can affect congestion, and these are summarised in the table • e.g. retransmission policy at data link layer Transport Retransmission policy • Out-of-order caching -

The Effects of Different Congestion Control Algorithms Over Multipath Fast Ethernet Ipv4/Ipv6 Environments
Proceedings of the 11th International Conference on Applied Informatics Eger, Hungary, January 29–31, 2020, published at http://ceur-ws.org The Effects of Different Congestion Control Algorithms over Multipath Fast Ethernet IPv4/IPv6 Environments Szabolcs Szilágyi, Imre Bordán Faculty of Informatics, University of Debrecen, Hungary [email protected] [email protected] Abstract The TCP has been in use since the seventies and has later become the predominant protocol of the internet for reliable data transfer. Numerous TCP versions has seen the light of day (e.g. TCP Cubic, Highspeed, Illinois, Reno, Scalable, Vegas, Veno, etc.), which in effect differ from each other in the algorithms used for detecting network congestion. On the other hand, the development of multipath communication tech- nologies is one today’s relevant research fields. What better proof of this, than that of the MPTCP (Multipath TCP) being integrated into multiple operating systems shortly after its standardization. The MPTCP proves to be very effective for multipath TCP-based data transfer; however, its main drawback is the lack of support for multipath com- munication over UDP, which can be important when forwarding multimedia traffic. The MPT-GRE software developed at the Faculty of Informatics, University of Debrecen, supports operation over both transfer protocols. In this paper, we examine the effects of different TCP congestion control mechanisms on the MPTCP and the MPT-GRE multipath communication technologies. Keywords: congestion control, multipath communication, MPTCP, MPT- GRE, transport protocols. 1. Introduction In 1974, the TCP was defined in RFC 675 under the Transmission Control Pro- gram name. Later, the Transmission Control Program was split into two modular Copyright © 2020 for this paper by its authors. -

What Causes Packet Loss IP Networks
What Causes Packet Loss IP Networks (Rev 1.1) Computer Modules, Inc. DVEO Division 11409 West Bernardo Court San Diego, CA 92127, USA Telephone: +1 858 613 1818 Fax: +1 858 613 1815 www.dveo.com Copyright © 2016 Computer Modules, Inc. All Rights Reserved. DVEO, DOZERbox, DOZER Racks and DOZER ARQ are trademarks of Computer Modules, Inc. Specifications and product availability are subject to change without notice. Packet Loss and Reasons Introduction This Document To stream high quality video, i.e. to transmit real-time video streams, over IP networks is a demanding endeavor and, depending on network conditions, may result in packets being dropped or “lost” for a variety of reasons, thus negatively impacting the quality of user experience (QoE). This document looks at typical reasons and causes for what is generally referred to as “packet loss” across various types of IP networks, whether of the managed and conditioned type with a defined Quality of Service (QoS), or the “unmanaged” kind such as the vast variety of individual and interconnected networks across the globe that collectively constitute the public Internet (“the Internet”). The purpose of this document is to encourage operators and enterprises that wish to overcome streaming video quality problems to explore potential solutions. Proven technology exists that enables transmission of real-time video error-free over all types of IP networks, and to perform live broadcasting of studio quality content over the “unmanaged” Internet! Core Protocols of the Internet Protocol Suite The Internet Protocol (IP) is the foundation on which the Internet was built and, by extension, the World Wide Web, by enabling global internetworking. -

Cdns, Real Time Streaming, Multimedia Platforms & Video Service Providers
Πολυμεσικό Υλικό στο Internet: Συγχρονισμός, Επεξεργασία και Διακίνηση Multimedia content delivery in the Internet: CDNs, Real Time Streaming, Multimedia platforms & video service providers Β. Μάγκλαρης <[email protected]> Μ. Γραμματικού <[email protected]> Δ. Καλογεράς <[email protected]> www.netmode.ntua.gr Outline • Content Delivery Networks (CDNs) • Video on Demand servers/clouds • Real Time Streaming Content Delivery Networks (CDNs) http://en.wikipedia.org/wiki/Content_delivery_network • The first generation CDNs were not encountered before the late 90′s • CDN is a large distributed system of servers deployed in multiple data centers across the Internet • It serves content to end-users with high availability and high performance • It serves a large fraction of the Internet content : – including web objects (text, graphics and scripts), downloadable objects (media files, software, documents), applications (e-commerce, portals), live steaming media, on-demand streaming media, and social networks Single server distribution and CDN distribution CDN Providers uses different Business Model • Google maintains it’s own delivery network consisting of large number of GGC (Google Global Cache) nodes placed on ISPs network and help in serving Google’s static content • Akamai (whose core business is into Cache delivery) put their servers on large number of edge networks but they stay as disconnected small islands • New comers in the industry like Limelight, Cloudflare put node in major datacenter and direct connection to major networks