Everything Counts in Small Amounts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bringing GNU Emacs to Native Code
Bringing GNU Emacs to Native Code Andrea Corallo Luca Nassi Nicola Manca [email protected] [email protected] [email protected] CNR-SPIN Genoa, Italy ABSTRACT such a long-standing project. Although this makes it didactic, some Emacs Lisp (Elisp) is the Lisp dialect used by the Emacs text editor limitations prevent the current implementation of Emacs Lisp to family. GNU Emacs can currently execute Elisp code either inter- be appealing for broader use. In this context, performance issues preted or byte-interpreted after it has been compiled to byte-code. represent the main bottleneck, which can be broken down in three In this work we discuss the implementation of an optimizing com- main sub-problems: piler approach for Elisp targeting native code. The native compiler • lack of true multi-threading support, employs the byte-compiler’s internal representation as input and • garbage collection speed, exploits libgccjit to achieve code generation using the GNU Com- • code execution speed. piler Collection (GCC) infrastructure. Generated executables are From now on we will focus on the last of these issues, which con- stored as binary files and can be loaded and unloaded dynamically. stitutes the topic of this work. Most of the functionality of the compiler is written in Elisp itself, The current implementation traditionally approaches the prob- including several optimization passes, paired with a C back-end lem of code execution speed in two ways: to interface with the GNU Emacs core and libgccjit. Though still a work in progress, our implementation is able to bootstrap a func- • Implementing a large number of performance-sensitive prim- tional Emacs and compile all lexically scoped Elisp files, including itive functions (also known as subr) in C. -

Wisp: Whitespace to Lisp
wisp: Whitespace to Lisp Dr. Arne Babenhauserheide <2013-03-26 Di> » I love the syntax of Python, but crave the simplicity and power of Lisp.« display "Hello World!" 7! (display "Hello World!") define : factorial n (define (factorial n) if : zero? n 7! (if (zero? n) . 1 1 * n : factorial {n - 1} (* n (factorial {n - 1})))) Wisp basics • Wisp turns indentation into lisp expressions. • Why Wisp? • Get it – from its Mercurial repository: hg clone https://hg.sr.ht/~arnebab/wisp – Or via GNU Guix: guix install guile guile-wisp – Or via the package guile-wisp-hg for Arch Linux. – Or via ./configure; make install from the releases. • See more examples and tests. 1 »ArneBab’s alternate sexp syntax is best I’ve seen; pythonesque, hides parens but keeps power« — Christopher Webber in twitter, in identi.ca and in their blog: Wisp: Lisp, minus the parentheses ~ wow ~ »Wisp allows people to see code how Lispers perceive it. Its structure becomes apparent.« — Ricardo Wurmus in IRC, paraphrasing the wisp statement from his talk at FOSDEM 2019 about Guix for reproducible science in HPC. ^¨ Yay! ^¨ with (open-file "with.w" "r") as port format #t "~a\n" : read port Familiar with-statement in 25 lines. 2 ↓ skip updates and releases ↓ Update (2021-05-21): If you use GNU Guix, you can get an instant wisp shell with a single command: guix environment --ad-hoc guile guile-wisp -- wisp That’s the guix wisp insta-REPL ^¨ $ guix environment --ad-hoc guile guile-wisp -- wisp GNU Guile 3.0.7 Copyright (C) 1995-2021 Free Software Foundation, Inc. -

A Reader Framework for Guile for Guile-Reader 0.6.2
A Reader Framework for Guile for Guile-Reader 0.6.2 Ludovic Court`es Edition 0.6.2 8 March 2017 This file documents Guile-Reader. Copyright c 2005, 2006, 2007, 2008, 2009, 2012, 2015, 2017 Ludovic Court`es Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this manual under the con- ditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this manual into another lan- guage, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. i Table of Contents A Reader Framework for Guile ................ 1 1 Introduction............................... 3 2 Overview .................................. 5 3 Quick Start................................ 7 4 API Reference............................. 9 4.1 Token Readers .............................................. 9 4.1.1 Defining a New Token Reader............................ 9 4.1.2 Token Reader Calling Convention ........................ 9 4.1.3 Invoking a Reader from a Token Reader ................. 10 4.1.4 Token Reader Library .................................. 11 4.1.5 Limitations............................................ 16 4.1.5.1 Token Delimiters ................................. -

Functional Package Management with Guix
Functional Package Management with Guix Ludovic Courtès Bordeaux, France [email protected] ABSTRACT 1. INTRODUCTION We describe the design and implementation of GNU Guix, a GNU Guix1 is a purely functional package manager for the purely functional package manager designed to support a com- GNU system [20], and in particular GNU/Linux. Pack- plete GNU/Linux distribution. Guix supports transactional age management consists in all the activities that relate upgrades and roll-backs, unprivileged package management, to building packages from source, honoring the build-time per-user profiles, and garbage collection. It builds upon the and run-time dependencies on packages, installing, removing, low-level build and deployment layer of the Nix package man- and upgrading packages in user environments. In addition ager. Guix uses Scheme as its programming interface. In to these standard features, Guix supports transactional up- particular, we devise an embedded domain-specific language grades and roll-backs, unprivileged package management, (EDSL) to describe and compose packages. We demonstrate per-user profiles, and garbage collection. Guix comes with a how it allows us to benefit from the host general-purpose distribution of user-land free software packages. programming language while not compromising on expres- siveness. Second, we show the use of Scheme to write build Guix seeks to empower users in several ways: by offering the programs, leading to a \two-tier" programming system. uncommon features listed above, by providing the tools that allow users to formally correlate a binary package and the Categories and Subject Descriptors \recipes" and source code that led to it|furthering the spirit D.4.5 [Operating Systems]: Reliability; D.4.5 [Operating of the GNU General Public License|, by allowing them to Systems]: System Programs and Utilities; D.1.1 [Software]: customize the distribution, and by lowering the barrier to Applicative (Functional) Programming entry in distribution development. -

Article Title
International In-house Counsel Journal Vol. 10, No. 38, Winter 2017, 1 Open Source Software: Compliance and Risk Mitigation SHILPI SNEHA In-house Counsel, India 1. Introduction – a brief history of where it all began The proprietorship of software was not a familiar concept in the 50’s and 60’s. The hardware and software were seen as an inseparable “system” and the cost for the operating system or any associated software used to be included in the price of the hardware. The human readable form of software i.e. source code were distributed along with the hardware to ensure that the user can make their own changes or modification for smooth running of the hardware. Users generally distributed the software, bug-fixes and any modification with each other freely as there were no strict licensing terms and even if there were few organisations who included license terms, enforcement of such terms was not usual. With the increase in many organisations and corporations who invested time and resources for development and betterment of software and the industry itself, software became the source of revenue opening a huge consumer market and protection of the software or its source code became the need for these corporations to survive beneficially. Upon being adequately famous and having dependable customer base, in the 1980s, AT&T stopped the free distribution and started charging for patches. One can also refer to the famous open-letter written by Bill Gates to the “hobbyist” (as the earlier free distributors or contributors were known as) in 1976 wherein he clearly mentioned the discontent on the free distribution of Microsoft’s proprietary software in as many words as possible. -

Weak References Data Structures and Implementation
Weak References Data Structures and Implementation Bruno Haible ILOG GmbH 24 April 2005 What is a Weak Pointer? ● Garbage collection preserves all objects that are reachable from the root set. ● A weak pointer holds its object without causing it to be reachable. What is a Weak Hashtable? ● A weak hash-table holds its key-value pairs without causing them to be reachable. ● Four kinds: – :key – :value – :key-and-value – :key-or-value A Strong Feature ● Adding extra info to sealed objects. ● Memoizing prior results. ● Uniquification. ● Hash consing. ● Avoiding attach/detach protocols. ● Global garbage collection. Caveats ● Extra time spent in GC (for W weak pointers: – O(W²) in some implementations, – O(W) in other implementations) Weak Datastructures ● Weak pointer ● Weak “and” relation ● Weak “or” relation ● Weak association (= weak mapping) ● Weak “and” mapping ● Weak “or” mapping ● Weak association list ● Weak hash-table Primitive Weak Datastructures ● Weak pointers ● Weak :key mappings ● Weak hash-tables The others can be emulated. Levels of Support 1.Support for weak pointers. 2.Support for weak :key mappings or weak hash-tables, with “key not in value” restriction. 3.Support for weak :key mappings or weak hash-tables, without restriction. 4.Scalable support for weak :key mappings or weak hash-tables. Implementations of Level 1 ● Common Lisp: GNU clisp 2.33.80, OpenMCL 0.14.1, Allegro CL 6.2, LispWorks 4.3, Corman Lisp 1.1, CMUCL 19a, SBCL 0.8.20 ● Scheme: GNU guile 1.7.1, MIT Scheme 7.7.1, BBN Scheme, MzScheme 205, Scheme48 ● Other -

GNU Guix Reference Manual Using the GNU Guix Functional Package Manager
GNU Guix Reference Manual Using the GNU Guix Functional Package Manager The GNU Guix Developers Edition 34cf1f4 29 September 2021 Copyright c 2012, 2013, 2014, 2015, 2016, 2017, 2018, 2019, 2020, 2021 Ludovic Court`es Copyright c 2013, 2014, 2016 Andreas Enge Copyright c 2013 Nikita Karetnikov Copyright c 2014, 2015, 2016 Alex Kost Copyright c 2015, 2016 Mathieu Lirzin Copyright c 2014 Pierre-Antoine Rault Copyright c 2015 Taylan Ulrich Bayırlı/Kammer Copyright c 2015, 2016, 2017, 2019, 2020, 2021 Leo Famulari Copyright c 2015, 2016, 2017, 2018, 2019, 2020 Ricardo Wurmus Copyright c 2016 Ben Woodcroft Copyright c 2016, 2017, 2018, 2021 Chris Marusich Copyright c 2016, 2017, 2018, 2019, 2020, 2021 Efraim Flashner Copyright c 2016 John Darrington Copyright c 2016, 2017 Nikita Gillmann Copyright c 2016, 2017, 2018, 2019, 2020 Jan Nieuwenhuizen Copyright c 2016, 2017, 2018, 2019, 2020, 2021 Julien Lepiller Copyright c 2016 Alex ter Weele Copyright c 2016, 2017, 2018, 2019, 2020, 2021 Christopher Baines Copyright c 2017, 2018, 2019 Cl´ement Lassieur Copyright c 2017, 2018, 2020, 2021 Mathieu Othacehe Copyright c 2017 Federico Beffa Copyright c 2017, 2018 Carlo Zancanaro Copyright c 2017 Thomas Danckaert Copyright c 2017 humanitiesNerd Copyright c 2017, 2021 Christine Lemmer-Webber Copyright c 2017, 2018, 2019, 2020, 2021 Marius Bakke Copyright c 2017, 2019, 2020 Hartmut Goebel Copyright c 2017, 2019, 2020, 2021 Maxim Cournoyer Copyright c 2017, 2018, 2019, 2020, 2021 Tobias Geerinckx-Rice Copyright c 2017 George Clemmer Copyright c 2017 Andy Wingo Copyright c 2017, 2018, 2019, 2020 Arun Isaac Copyright c 2017 nee Copyright c 2018 Rutger Helling Copyright c 2018, 2021 Oleg Pykhalov Copyright c 2018 Mike Gerwitz Copyright c 2018 Pierre-Antoine Rouby Copyright c 2018, 2019 G´abor Boskovits Copyright c 2018, 2019, 2020 Florian Pelz Copyright c 2018 Laura Lazzati Copyright c 2018 Alex Vong Copyright c 2019 Josh Holland Copyright c 2019, 2020 Diego Nicola Barbato Copyright c 2019 Ivan Petkov Copyright c 2019 Jakob L. -

Proceedings of ELS 2013 6Th European Lisp Symposium June 3 – 4 2013 Madrid, Spain
Proceedings of ELS 2013 6th European Lisp Symposium June 3 – 4 2013 Madrid, Spain Organization Programme Chairs • Christian Queinnec, UPMC, France • Manuel Serrano, INRIA, France Local Chair • Juan José Garcia-Ripoll, IFF, Madrid Programme Committee • Pascal Costanza, Intel, Belgium • Ludovic Courtès, Inria, France • Theo D’Hondt, Vrije Universiteit Brussel, Belgium • Erick Gallesio, University of Nice-Sophia Antipolis • Florian Loitsch, Google, Denmark • Kurt Noermark, Aalborg University, Denmark • Christian Queinnec, UPMC, France • Olin Shivers, Northeastern University, USA • Manuel Serrano, Inria, France • Didier Verna, Epita Research Lab, France ELS 2013 iii Sponsors EPITA 14-16 rue Voltaire FR-94276 Le Kremlin-Bicêtre CEDEX France www.epita.fr LispWorks Ltd. St John’s Innovation Centre Cowley Road Cambridge CB4 0WS England www.lispworks.com Franz Inc. 2201 Broadway, Suite 715 Oakland, CA 94612 www.franz.com Clozure Associates Boston, MA 02205-5071 USA www.clozure.com INRIA Domaine de Voluceau Rocquencourt - BP 105 78153 Le Chesnay Cedex France www.inria.fr Association of Lisp Users USA www.alu.org iv ELS 2013 Contents Organization iii Programme Chairs . iii Local Chair . iii Programme Committee . iii Sponsors . iv Invited Talks 1 Asynchronous Programming in Dart – Florian Loitsch ...................1 Lisp and Music Research – Gérard Assayag ..........................1 Streams-Based, Multi-Threaded News Classification – Jason Cornez ...........1 Session I 3 Functional Package Management with Guix – Ludovic Courtès ..............4 Data-Transformer: an Example of Data-Centered Toolset – Mikhail Raskin ........ 15 The Leonardo System and Software Individuals – Erik Sandewall ............. 18 Session II 25 Tutorial: Typed Racket – Sam Tobin-Hochstadt ........................ 26 Platforms for Games and Evaluation of Lisp Code – Arturo de Salabert ......... -

Functional Package Management with Guix Ludovic Courtès
Functional Package Management with Guix Ludovic Courtès To cite this version: Ludovic Courtès. Functional Package Management with Guix. European Lisp Symposium, Jun 2013, Madrid, Spain. hal-00824004 HAL Id: hal-00824004 https://hal.inria.fr/hal-00824004 Submitted on 20 May 2013 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Functional Package Management with Guix Ludovic Courtès Bordeaux, France [email protected] ABSTRACT 1. INTRODUCTION We describe the design and implementation of GNU Guix, a GNU Guix1 is a purely functional package manager for the purely functional package manager designed to support a com- GNU system [20], and in particular GNU/Linux. Pack- plete GNU/Linux distribution. Guix supports transactional age management consists in all the activities that relate upgrades and roll-backs, unprivileged package management, to building packages from source, honoring the build-time per-user profiles, and garbage collection. It builds upon the and run-time dependencies on packages, installing, removing, low-level build and deployment layer of the Nix package man- and upgrading packages in user environments. In addition ager. Guix uses Scheme as its programming interface. In to these standard features, Guix supports transactional up- particular, we devise an embedded domain-specific language grades and roll-backs, unprivileged package management, (EDSL) to describe and compose packages. -

Principles of Autonomy and Decision Making Project Introduction
Principles of Autonomy and Decision Making Project This text is taken from the GNU Robots manual, written by Jim Hall. Introduction GNU Robots is a game/diversion where you construct a program for a little robot, then set him loose and watch him explore a world on his own. The robot program is written in Scheme, and is implemented using GNU Guile. The whole goal of GNU Robots is to get the highest score that you can. Robot actions But the question you’re probably waiting to have answered is: ”What can I make the little robot do?” That’s the list of ‘robot-*’ functions. Here is a table of all the GNU Robots functions, called primitives, that you can use in your robot program. Each primitive has an energy cost associated with it. Note that some primitives will take an argument, and some will not. If an argument is a number, I’ll print ‘N’ after the function name. If the argument is a GNU Robots ”thing” then I’ll print ‘TH’ after the function name. (Note that number arguments are just numbers, but “thing” arguments are strings enclosed in quotation marks.) If the primitive does not take an argument, I will print nothing. 1 PRIMITIVE ENERGY ACTION robot-turn N -2 Turns the robot N spaces to the right or left. If ‘N’ is a positive number, the robot turns to the right. If ‘N’ is negative, the robot turns to the left. Every turn has a cost of -2, so if you ‘robot-turn 2’ then the cost is -4 to your energy. -
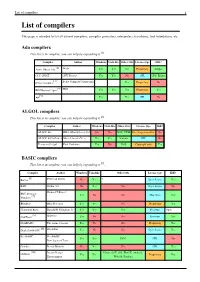
List of Compilers 1 List of Compilers
List of compilers 1 List of compilers This page is intended to list all current compilers, compiler generators, interpreters, translators, tool foundations, etc. Ada compilers This list is incomplete; you can help by expanding it [1]. Compiler Author Windows Unix-like Other OSs License type IDE? [2] Aonix Object Ada Atego Yes Yes Yes Proprietary Eclipse GCC GNAT GNU Project Yes Yes No GPL GPS, Eclipse [3] Irvine Compiler Irvine Compiler Corporation Yes Proprietary No [4] IBM Rational Apex IBM Yes Yes Yes Proprietary Yes [5] A# Yes Yes GPL No ALGOL compilers This list is incomplete; you can help by expanding it [1]. Compiler Author Windows Unix-like Other OSs License type IDE? ALGOL 60 RHA (Minisystems) Ltd No No DOS, CP/M Free for personal use No ALGOL 68G (Genie) Marcel van der Veer Yes Yes Various GPL No Persistent S-algol Paul Cockshott Yes No DOS Copyright only Yes BASIC compilers This list is incomplete; you can help by expanding it [1]. Compiler Author Windows Unix-like Other OSs License type IDE? [6] BaCon Peter van Eerten No Yes ? Open Source Yes BAIL Studio 403 No Yes No Open Source No BBC Basic for Richard T Russel [7] Yes No No Shareware Yes Windows BlitzMax Blitz Research Yes Yes No Proprietary Yes Chipmunk Basic Ronald H. Nicholson, Jr. Yes Yes Yes Freeware Open [8] CoolBasic Spywave Yes No No Freeware Yes DarkBASIC The Game Creators Yes No No Proprietary Yes [9] DoyleSoft BASIC DoyleSoft Yes No No Open Source Yes FreeBASIC FreeBASIC Yes Yes DOS GPL No Development Team Gambas Benoît Minisini No Yes No GPL Yes [10] Dream Design Linux, OSX, iOS, WinCE, Android, GLBasic Yes Yes Proprietary Yes Entertainment WebOS, Pandora List of compilers 2 [11] Just BASIC Shoptalk Systems Yes No No Freeware Yes [12] KBasic KBasic Software Yes Yes No Open source Yes Liberty BASIC Shoptalk Systems Yes No No Proprietary Yes [13] [14] Creative Maximite MMBasic Geoff Graham Yes No Maximite,PIC32 Commons EDIT [15] NBasic SylvaWare Yes No No Freeware No PowerBASIC PowerBASIC, Inc. -
A Survey of GNU Guile Software
A Survey of GNU Guile Software Erik Edrosa March 23, 2019 Erik Edrosa A Survey of GNU Guile Software March 23, 2019 1 / 31 Introduction About me GNU Guile user since 2014 Maintainer of Guile-CommonMark and Guile-Git C++ Software Developer from Miami, Florida Erik Edrosa A Survey of GNU Guile Software March 23, 2019 2 / 31 GNU Guile What is GNU Guile? GNU Ubiquitous Intelligent Language for Extensions The official extension language of the GNU project. Implementation of the Scheme programming language. Erik Edrosa A Survey of GNU Guile Software March 23, 2019 3 / 31 GNU Guile Origins of GNU Guile GNU Hackers were inspired by the customability and extendability of GNU Emacs They wanted to bring this to the rest of GNU Decided to use scheme, because it is simple and clean Should support multiple languages like Emacs Lisp and Tcl Erik Edrosa A Survey of GNU Guile Software March 23, 2019 4 / 31 Customizing and Extending Software Definitions Customizable easily alter the behavior of the software. Extensible can go beyond simple customizations and create new ways to use the software. Erik Edrosa A Survey of GNU Guile Software March 23, 2019 5 / 31 GNU Emacs GNU Emacs An extensible, customizable, free/libre text editor Also a calendar, email client, package manager, web browser, . and more! Find out more at https://www.gnu.org/s/emacs Erik Edrosa A Survey of GNU Guile Software March 23, 2019 6 / 31 GNU Emacs Extending Emacs with Commands Uses a command loop (defun hello (name) First reads a key sequence "Greets a person" Key sequence is translated