Esoteric Programming Languages
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Radare2 Book
Table of Contents introduction 1.1 Introduction 1.2 History 1.2.1 Overview 1.2.2 Getting radare2 1.2.3 Compilation and Portability 1.2.4 Compilation on Windows 1.2.5 Command-line Flags 1.2.6 Basic Usage 1.2.7 Command Format 1.2.8 Expressions 1.2.9 Rax2 1.2.10 Basic Debugger Session 1.2.11 Contributing to radare2 1.2.12 Configuration 1.3 Colors 1.3.1 Common Configuration Variables 1.3.2 Basic Commands 1.4 Seeking 1.4.1 Block Size 1.4.2 Sections 1.4.3 Mapping Files 1.4.4 Print Modes 1.4.5 Flags 1.4.6 Write 1.4.7 Zoom 1.4.8 Yank/Paste 1.4.9 Comparing Bytes 1.4.10 Visual mode 1.5 Visual Disassembly 1.5.1 2 Searching bytes 1.6 Basic Searches 1.6.1 Configurating the Search 1.6.2 Pattern Search 1.6.3 Automation 1.6.4 Backward Search 1.6.5 Search in Assembly 1.6.6 Searching for AES Keys 1.6.7 Disassembling 1.7 Adding Metadata 1.7.1 ESIL 1.7.2 Scripting 1.8 Loops 1.8.1 Macros 1.8.2 R2pipe 1.8.3 Rabin2 1.9 File Identification 1.9.1 Entrypoint 1.9.2 Imports 1.9.3 Symbols (exports) 1.9.4 Libraries 1.9.5 Strings 1.9.6 Program Sections 1.9.7 Radiff2 1.10 Binary Diffing 1.10.1 Rasm2 1.11 Assemble 1.11.1 Disassemble 1.11.2 Ragg2 1.12 Analysis 1.13 Code Analysis 1.13.1 Rahash2 1.14 Rahash Tool 1.14.1 Debugger 1.15 3 Getting Started 1.15.1 Registers 1.15.2 Remote Access Capabilities 1.16 Remoting Capabilities 1.16.1 Plugins 1.17 Plugins 1.17.1 Crackmes 1.18 IOLI 1.18.1 IOLI 0x00 1.18.1.1 IOLI 0x01 1.18.1.2 Avatao 1.18.2 R3v3rs3 4 1.18.2.1 .intro 1.18.2.1.1 .radare2 1.18.2.1.2 .first_steps 1.18.2.1.3 .main 1.18.2.1.4 .vmloop 1.18.2.1.5 .instructionset 1.18.2.1.6 -

Magazin Rist 2014.Cdr
RISTian Annual Magazine 2014-15 REGIONAL INSTITUTE OF SCIENCE & TECHNOLOGY Techno City, Kling Road, 9th Mile, Ri-Bhoi, Meghalaya-793101 MAGAZINE COMMITTEE Patron : Mr. M. Hoque, Chairman, ERDF Advisors : Dr. P.C. Mahanta, Director, RIST Dr. U.K. Sharma, Executive Director, RIST Mr. N.I. Laskar, Director, Corporate Communication, RIST Mr. J.U. Choudhury, HR, ERDF EDITORIAL BOARD Co-ordinator: Mr. A.H. Barbhuiya, Registrar, RIST Faculty Editors: Mr. Nabendu Kumar Deb, Asst. Prof. (Physics), Deptt. Of Basic Science and Humanities. Ms. Nabamita Boral, Asst. Prof. (English), Deptt. Of Basic Science and Humanities. Ms. Mandira Baruah, Asst. Prof., Deptt. Of Electrical and Electronics Ms. Baishali Sharma, Administrative Assistant, RIST. Student Editors: Sagorika Raj Chakraborty, 4th sem, EEE Sauvik Dey, 6th sem, CE Gagandeep Kaur, 8th Sem, CSE. Rashmita Mudoi, 8th sem, CSE. Student Co-ordinators: Chinmoyuri Bora, 6th Sem, ECE. Abdul Ghani Kamson, 6th Sem, ECE. Sudeep Sinha, 6th sem, CSE. Saurav Jyoti Das, 6th sem, EEE Illustrator: Santoj Hazarika, 8th Sem, ME Layout & Designing: Giasuddin Ahmed, Graphic Designer, ERDF Jitu Mahanta, DTP Operator, ERDF Printed at : Aman Udyog Pvt. Ltd. Christian Basti, Guwahati-5 i From the faculty editors' desk... “The true sign of intelligence is not knowledge but imagination.” Albert Einstein RISTian is a forum in which the students, faculty members and staffs (RIST Community) can portray their literary talents. This volume, which is n the second, has contributions from the RIST Community in the form of essays, poems, facts, sketches, etc. We offer heartiest thanks to all the contributors. a Putting a magazine together is no cake-walk. -

The Comprehensive LATEX Symbol List
The Comprehensive LATEX Symbol List Scott Pakin <[email protected]>∗ 22 September 2005 Abstract This document lists 3300 symbols and the corresponding LATEX commands that produce them. Some of these symbols are guaranteed to be available in every LATEX 2ε system; others require fonts and packages that may not accompany a given distribution and that therefore need to be installed. All of the fonts and packages used to prepare this document—as well as this document itself—are freely available from the Comprehensive TEX Archive Network (http://www.ctan.org/). Contents 1 Introduction 7 1.1 Document Usage . 7 1.2 Frequently Requested Symbols . 7 2 Body-text symbols 8 Table 1: LATEX 2ε Escapable “Special” Characters . 8 Table 2: Predefined LATEX 2ε Text-mode Commands . 8 Table 3: LATEX 2ε Commands Defined to Work in Both Math and Text Mode . 8 Table 4: AMS Commands Defined to Work in Both Math and Text Mode . 9 Table 5: Non-ASCII Letters (Excluding Accented Letters) . 9 Table 6: Letters Used to Typeset African Languages . 9 Table 7: Letters Used to Typeset Vietnamese . 9 Table 8: Punctuation Marks Not Found in OT1 . 9 Table 9: pifont Decorative Punctuation Marks . 10 Table 10: tipa Phonetic Symbols . 10 Table 11: tipx Phonetic Symbols . 11 Table 13: wsuipa Phonetic Symbols . 12 Table 14: wasysym Phonetic Symbols . 12 Table 15: phonetic Phonetic Symbols . 12 Table 16: t4phonet Phonetic Symbols . 13 Table 17: semtrans Transliteration Symbols . 13 Table 18: Text-mode Accents . 13 Table 19: tipa Text-mode Accents . 14 Table 20: extraipa Text-mode Accents . -

Socket Extensions for Esoteric Languages
Annals of the University of Craiova, Mathematics and Computer Science Series Volume 41(2), 2014, Pages 271{279 ISSN: 1223-6934 Socket extensions for esoteric languages Radu Dragos¸and Diana Halit¸a˘ Abstract. In this paper we have advanced the first interpreter for the brainfuck (BF) esoteric programming language, entirely written in awk, a fast text processing programming language. However, the main objective remained introducing socket communication to brainfuck pro- gramming language. In order to achieve that goal, we have improved the brainfuck language with a byte long instruction through which it is allowed socket communication. For that, we have advanced a series of procedures in order to test the compatibility of our brainfuck interpreter. Moreover, we have maintained brainfucks minimalism, which is one of the special char- acteristics of this programming language. In the end, we succeeded to map a minimalistic programming language to the client-server paradigm. 2010 Mathematics Subject Classification. 68N15 - Programming languages, 68N20 - Compilers and interpreters. Key words and phrases. brainfuck, socket, interpreter, esoteric languages. 1. Introduction This paper describes a simple interpreter for the brainfuck (BF) esoteric programming language, written in AWK. It is compatible with almost any version of AWK that is supplied within UNIX systems. The interpreter illustrates the use of AWK in implementing small programs using BF language, mainly for proof of concept reasons. 1.1. Motivation. Even if BF is known for its extreme minimalism and it is designed to challenge programmers, it is not usually suitable for practical use. However, the motivation of developing such an application comes from the usage of a simple and easy syntax which can help programmers to deeply understand other programming languages and besides that, other programming paradigms. -

The Intercal Programming Language Revised Reference Manual
THE INTERCAL PROGRAMMING LANGUAGE REVISED REFERENCE MANUAL Donald R. Woods and James M. Lyon C-INTERCAL revisions: Louis Howell and Eric S. Raymond Copyright (C) 1973 by Donald R. Woods and James M. Lyon Copyright (C) 1996 by Eric S. Raymond Redistribution encouragedunder GPL (This version distributed with C-INTERCAL 0.15) -1- 1. INTRODUCTION The names you are about to ignore are true. However, the story has been changed significantly.Any resemblance of the programming language portrayed here to other programming languages, living or dead, is purely coincidental. 1.1 Origin and Purpose The INTERCAL programming language was designed the morning of May 26, 1972 by Donald R. Woods and James M. Lyon, at Princeton University.Exactly when in the morning will become apparent in the course of this manual. Eighteen years later (give ortakeafew months) Eric S. Raymond perpetrated a UNIX-hosted INTERCAL compiler as a weekend hack. The C-INTERCAL implementation has since been maintained and extended by an international community of technomasochists, including Louis Howell, Steve Swales, Michael Ernst, and Brian Raiter. (There was evidently an Atari implementation sometime between these two; notes on it got appended to the INTERCAL-72 manual. The culprits have sensibly declined to identify themselves.) INTERCAL was inspired by one ambition: to have a compiler language which has nothing at all in common with anyother major language. By ’major’ was meant anything with which the authors were at all familiar,e.g., FORTRAN, BASIC, COBOL, ALGOL, SNOBOL, SPITBOL, FOCAL, SOLVE, TEACH, APL, LISP,and PL/I. For the most part, INTERCAL has remained true to this goal, sharing only the basic elements such as variables, arrays, and the ability to do I/O, and eschewing all conventional operations other than the assignment statement (FORTRAN "="). -

Trinary CPE Report
Ternary Computing Testbed 3!Trit Computer Architecture Je" Connelly Computer Engineering Department August 29th, 2008 with contributions from Chirag Patel and Antonio Chavez Advised by Professor Phillip Nico California Polytechnic State University of San Luis Obispo Table of Contents 1. Introduction 1 1.1. Method 1 1.2. Plan 2 1.3. Team and Individual Responsibilities 2 1.3.1. Jeff Connelly 2 1.3.2. Antonio Chavez 2 1.3.3. Chirag Patel 3 2. Background Theory 3 2.1. Base 3 3 2.1.1. Compared to Analog 3 2.1.2. Compared to Digital 4 2.1.3. Compared to Base e 5 2.1.4. Trits, Tribbles, and Trytes 7 2.1.5. Base 9 and 27 9 2.1.6. Text 10 2.2. Logic and Arithmetic 10 3. Application Description 10 3.1. Christmas Lights Game 10 3.2. Guessing Game 11 4. Architecture Description 11 4.1. Power Supply 12 4.2. Instruction Memory 13 4.2.1. Experimental Results 16 4.3. Program Counter 16 4.4. Clock Generator 17 4.5. Processor 18 4.5.1. Registers 18 4.5.2. Input and Output 19 4.5.3. 3-Trit Instruction Set 20 4.5.4. LWI Instruction Example (also known as TCA0) 21 4.5.5. CMP Instruction 25 4.5.5.1. ALU 26 4.5.5.2. CMP Instruction Example 29 4.5.6. BE Instruction 31 4.5.6.1. BE Instruction Example 32 4.5.7. Guessing Game Program 33 5. Evaluation 38 6. Conclusion and Future Directions 39 7. -
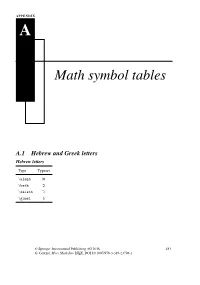
Math Symbol Tables
APPENDIX A Math symbol tables A.1 Hebrew and Greek letters Hebrew letters Type Typeset \aleph ℵ \beth ℶ \daleth ℸ \gimel ℷ © Springer International Publishing AG 2016 481 G. Grätzer, More Math Into LATEX, DOI 10.1007/978-3-319-23796-1 482 Appendix A Math symbol tables Greek letters Lowercase Type Typeset Type Typeset Type Typeset \alpha \iota \sigma \beta \kappa \tau \gamma \lambda \upsilon \delta \mu \phi \epsilon \nu \chi \zeta \xi \psi \eta \pi \omega \theta \rho \varepsilon \varpi \varsigma \vartheta \varrho \varphi \digamma ϝ \varkappa Uppercase Type Typeset Type Typeset Type Typeset \Gamma Γ \Xi Ξ \Phi Φ \Delta Δ \Pi Π \Psi Ψ \Theta Θ \Sigma Σ \Omega Ω \Lambda Λ \Upsilon Υ \varGamma \varXi \varPhi \varDelta \varPi \varPsi \varTheta \varSigma \varOmega \varLambda \varUpsilon A.2 Binary relations 483 A.2 Binary relations Type Typeset Type Typeset < < > > = = : ∶ \in ∈ \ni or \owns ∋ \leq or \le ≤ \geq or \ge ≥ \ll ≪ \gg ≫ \prec ≺ \succ ≻ \preceq ⪯ \succeq ⪰ \sim ∼ \approx ≈ \simeq ≃ \cong ≅ \equiv ≡ \doteq ≐ \subset ⊂ \supset ⊃ \subseteq ⊆ \supseteq ⊇ \sqsubseteq ⊑ \sqsupseteq ⊒ \smile ⌣ \frown ⌢ \perp ⟂ \models ⊧ \mid ∣ \parallel ∥ \vdash ⊢ \dashv ⊣ \propto ∝ \asymp ≍ \bowtie ⋈ \sqsubset ⊏ \sqsupset ⊐ \Join ⨝ Note the \colon command used in ∶ → 2, typed as f \colon x \to x^2 484 Appendix A Math symbol tables More binary relations Type Typeset Type Typeset \leqq ≦ \geqq ≧ \leqslant ⩽ \geqslant ⩾ \eqslantless ⪕ \eqslantgtr ⪖ \lesssim ≲ \gtrsim ≳ \lessapprox ⪅ \gtrapprox ⪆ \approxeq ≊ \lessdot -

Unit 1 Computer Fundamentals
15 MM VENKATESHWARA COMPUTER FUNDAMENTALS OPEN UNIVERSITY AND PROGRAMMING www.vou.ac.in COMPUTER FUNDAMENTALS AND PROGRAMMING AND FUNDAMENTALS COMPUTER COMPUTER FUNDAMENTALS BBA [BBA-304] VENKATESHWARA OPEN UNIVERSITYwww.vou.ac.in COMPUTER FUNDAMENTALS BBA [BBA-304] BOARD OF STUDIES Prof Lalit Kumar Sagar Vice Chancellor Dr. S. Raman Iyer Director Directorate of Distance Education SUBJECT EXPERT Prof. Saurabh Upadhya Professor Dr. Kamal Upreti Associate Professor Mr. Animesh Srivastav Associate Professor Hitendranath Bhattacharya Assistant Professor CO-ORDINATOR Mr. Tauha Khan Registrar Authors: B. Basavaraj: Unit (1.0-1.2.4, 1.4-1.5.2, 1.8-1.9) Copyright © Vikas® Publishing House, 2010 Vivek Kesari: Unit (1.6-1.7, 1.11) Copyright © Vivek Kesari, 2010 S. Mohan Naidu: Unit (2.0-2.3, 2.5, 2.7, 3.3, 3.6-3.9, 3.17-3.18, 3.20-3.21, 3.23) Copyright © S. Mohan Naidu, 2010 R. Subburaj: Unit (3.0-3.2, 3.4-3.5, 3.10-3.12, 3.19, 3.22) Copyright © Vikas® Publishing House, 2010 Vikas® Publishing House: Units (1.3, 1.10, 1.12-1.17, 2.4, 2.6, 2.8-2.13, 3.13-3.16, 3.24-3.32) Copyright © Vikas® Publishing House, 2010 All rights reserved. No part of this publication which is material protected by this copyright notice may be reproduced or transmitted or utilized or stored in any form or by any means now known or hereinafter invented, electronic, digital or mechanical, including photocopying, scanning, recording or by any information storage or retrieval system, without prior written permission from the Publisher. -

Software Studies: a Lexicon, Edited by Matthew Fuller, 2008
fuller_jkt.qxd 4/11/08 7:13 AM Page 1 ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• S •••••••••••••••••••••••••••••••••••••new media/cultural studies ••••software studies •••••••••••••••••••••••••••••••••• ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• O ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• F software studies\ a lexicon ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• T edited by matthew fuller Matthew Fuller is David Gee Reader in ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• This collection of short expository, critical, Digital Media at the Centre for Cultural ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• W and speculative texts offers a field guide Studies, Goldsmiths College, University of to the cultural, political, social, and aes- London. He is the author of Media ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• thetic impact of software. Computing and Ecologies: Materialist Energies in Art and A digital media are essential to the way we Technoculture (MIT Press, 2005) and ••••••••••••••••••••••••••••••••••••• •••• •••••••••••••••••••••••••••••••••• work and live, and much has been said Behind the Blip: Essays on the Culture of ••••••••••••••••••••••••••••••••••••• -
Radare2 Book
Radare2 Book Table of Contents 1. introduction 2. Introduction i. History ii. Overview iii. Getting radare2 iv. Compilation and Portability v. Compilation on Windows vi. Command-line Flags vii. Basic Usage viii. Command Format ix. Expressions x. Rax2 xi. Basic Debugger Session xii. Contributing to radare2 3. Configuration i. Colors ii. Common Configuration Variables 4. Basic Commands i. Seeking ii. Block Size iii. Sections iv. Mapping Files v. Print Modes vi. Flags vii. Write viii. Zoom ix. Yank/Paste x. Comparing Bytes 5. Visual mode i. Visual Cursor ii. Visual Inserts iii. Visual XREFS iv. Visual Configuration Editor 6. Searching bytes i. Basic Searches ii. Configurating the Search iii. Pattern Search iv. Automatization v. Backward Search vi. Search in Assembly vii. Searching for AES Keys 7. Disassembling 2 Radare2 Book i. Adding Metadata ii. ESIL 8. Rabin2 i. File Identification ii. Entrypoint iii. Imports iv. Symbols (exports) v. Libraries vi. Strings vii. Program Sections 9. Radiff2 i. Binary Diffing 10. Rasm2 i. Assemble ii. Disassemble 11. Analysis i. Code Analysis 12. Rahash2 i. Rahash Tool 13. Debugger i. Registers 14. Remote Access Capabilities i. Remoting Capabilities 15. Plugins i. Plugins 16. Crackmes i. IOLI i. IOLI 0x00 ii. IOLI 0x01 17. Reference Card 3 Radare2 Book R2 "Book" Welcome to the Radare2 Book Webpage: https://www.gitbook.com/book/radare/radare2book/details Online: http://radare.gitbooks.io/radare2book/content/ PDF: https://www.gitbook.com/download/pdf/book/radare/radare2book Epub: https://www.gitbook.com/download/epub/book/radare/radare2book Mobi: https://www.gitbook.com/download/mobi/book/radare/radare2book introduction 4 Radare2 Book Introduction This book aims to cover most usage aspects of radare2. -

Department of Computer Science & Engineering
VOL X | JAN - 2018 CYBERBLITZ DEPARTMENT OF COMPUTER SCIENCE & ENGINEERING RAJAGIRI SCHOOL OF ENGINEERING & TECHNOLOGY RAJAGIRI VALLEY, KAKKANAD, KOCHI 682039, KERALA, INDIA INDEX DEPARTMENT VISION................................................................................................... 2 DEPARTMENT MISSION................................................................................................ 2 FROM HOD’S DESK...................................................................................................... 3 FACULTY CORNER HPC @ RSET...................................................................................................... 4 5G.................................................................................................................. 6 Will AI Replace Humans.................................................................................... 7 HPC Enhanced Real-Time Audio Processing........................................................ 9 Discovery Radiomics........................................................................................10 DevOps...........................................................................................................11 Weird Programming Languages.......................................................................13 STUDENT CORNER Artificial Intelligence and Its Implications for Humanity....................................16 A Programming Language for Quantum Computers...........................................18 Are Home Security Apps and Tech as Safe -

Weird Languages (1) for Software Studies Michael Mateas, [email protected]
Weird Languages (1) For Software Studies Michael Mateas, [email protected] Programming languages are often seen as given, an immutable logic within which everyday coding practice takes place. Viewed in this light, a programming language becomes a tool to be mastered, a means to an end. The practice of writing obfuscated code (see Montfort, this volume) exploits the syntactic and semantic play of a language to create code that, often humorously, comments on the constructs provided by a specific language. But the constructs and logics of languages are themselves contingent, abstractions pulled into being out of the space of computational possibility, and enforced and maintained by nothing more than programs, specifically the interpreters and compilers that implement the language. In the field of weird languages, also known as esoteric languages (2), programmers explore and exploit the play that is possible in programming language design. Weird programming languages are not designed for any real-world application or normal educational use; rather, they are intended to test the boundaries of programming language design itself. A quality they share with obfuscated code is that they often ironically comment on features of existing, traditional languages. There are literally dozens, if not hundreds of weird languages, commenting on many different aspects of language design, programming history and programming culture. A representative selection is considered here, with an eye towards understanding what these languages have to tell us about programming aesthetics. Languages are considered in terms of four dimensions of analysis: 1) parody, spoof, or explicit commentary on language features, 2) a tendency to reduce the number of operations and strive toward computational minimalism, 3) the use of structured play to explicitly encourage and support double-coding, and 4) the goal of creating a puzzle, and of making programming difficult.