Německý Jazyk
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Инструкция Для Телефона Siemens CX75
Ba Cover CX75.qxd 04.04.2005 10:51 Uhr Seite 1 ss Siemens Aktiengesellschaft, issued by Communications, Haidenauplatz 1 D-81667 Munich © Siemens AG 2005 All rights reserved. Subject to availability. Rights of modification reserved. Siemens Aktiengesellschaft www.siemens.com/cx75 Designed for life CX75 black LIEBREICH, Medienproduktion right page (1) of CX75 FUG ru, A31008-H7420-A15-1-5619 (11.05.2005, 11:11) Template: X75, Version 2.1; VAR 2.1; Version X75, Template: Содержание 1 Содержание Меры предосторожности ................ 3 Телеф.справ. ................................... 36 Обзор .................................................. 5 Новая запись ................................. 36 Дисплейные символы ..................... 7 Вызовы (поиск записи) ................. 37 Подготовка к работе ......................... 9 Изменение ..................................... 37 Установка SIM-карты и <Другие справ.> ............................ 38 Спис.вызовов .................................. 39 аккумулятора .................................. 9 Установка Время/стоим. ................................... 40 мультимедийной карты ................ 10 Камера ............................................... 41 date: 050128 issue VAR Language: ru; Зарядка аккумулятора .................. 11 Режим фотосъемки ...................... 42 Включение/выключение/ Режим видеосъемки ..................... 42 PIN-код .............................................. 13 Входящие ......................................... 44 g_ru_050511_vz_pk_druck\PHO_IVZ.fm Ввод PIN-кода -

BURY Compatibility List Generator
Compatibility list CC 9060 Time Updated: 2014-09-03 / v.75 Device software version: Display SW: 141 on No call call key level keys Card SMS Type future Profile Phone strength activation conference SMS / Popup between calls A2DP supported Phone s REDIAL reject waiting call Multiparty call: init / private mode with Activation Bluetooth Phone book entries: Display: GSM-signal Multiparty call: Swap E-mail read Function Messages: Download Call lists: Missed calls connection with device Multiparty call: accept / Work with activeCradle Display: Battery charge Bluetooth connection to used to test/ Comments after ignition is switched Multiparty call: merge to Call lists: Received calls Multiparty call: hold on 1 Messages: Receive new Phone book entries: SIM Display: Service provider this option will be used in the last connected phone OPP: Synch. phone book Call lists: Dialled numbers Bluetooth device / phones Possibility to switch car kit outgoing call during active Version of phone software 1 Apple iPhone ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 1 ✓ ✓ ✓ ✓ ✓ 3.0 (7a341) 2 Apple iPhone 3GS ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 1 ✓ ✓ ✓ ✓ ✓ ✓ 6.0 (10a403) 3 Apple iPhone 4 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 1 ✓ ✓ ✓ ✓ ✓ ✓ 7.0.2 (11a501) 4 Apple iPhone 4S ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 1 ✓ ✓ ✓ ✓ ✓ ✓ 7.0.2 (11a501) 5 Apple iPhone 5 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 1 ✓ ✓ ✓ ✓ ✓ 7.0.2 (11a501) 6 Apple iPhone 5c ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 1 ✓ ✓ ✓ ✓ ✓ 7.0.2 (11a501) 7 Apple iPhone 5s ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 1 ✓ ✓ ✓ ✓ ✓ 7.0.3 (11b511) 8 BlackBerry 7100 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 1 ✓ ✓ ✓ v4.0.2.16 (platform 1.8.0.132) ✓ 9 BlackBerry -

A Fugitive Success That Finland Is Quickly Becoming a Victim of Its Own Success
Professor Charles Sabel from Columbia Law School and Professor AnnaLee Saxenian from UC Berkeley argue in their book A Fugitive Success that Finland is quickly becoming a victim of its own success. In recent decades Finnish firms in the forest products and telecommunications industries have become world leaders. But the kind of discipline that made this success possible, and the public policies that furthered it, is unlikely to secure it in the future. Efficiency improvements and incremental A Fugitive Success innovations along the current business trajectory will gradually lead these industries into a dead-end unless they use innovation as a vehicle for transforming themselves into new higher value businesses. Saxenian and Sabel raise some serious concerns about the readiness of these industries, and the Finnish innovation system as a whole, for the needed transformation. A Fugitive Success is required reading for A Fugitive Success those involved in the development of the Finnish innovation environment and Finland’s Economic Future implementing the new national innovation strategy. Charles Sabel and AnnaLee Saxenian Sitra Reports 80 Sitra Reports the Finnish Innovation Fund ISBN 978-951-563-639-3 Itämerentori 2, P.O. Box 160, FI-00181 Helsinki, Finland, www.sitra.fi/en ISSN 1457-5728 80 Telephone +358 9 618 991, fax +358 9 645 072 URL: http://www.sitra.fi A Fugitive Success Finland’s Economic Future Sitra Reports 80 A Fugitive Success Finland’s Economic Future Charles Sabel AnnaLee Saxenian Sitra • HelSinki 3 Sitra Reports 80 Layout: Sisko Honkala Cover picture: Shutterstock © Sabel, Saxenian and Sitra ISBN 978-951-563-638-6 (paperback) ISSN 1457-571X (paperback) ISBN 978-951-563-639-3 (URL:http://www.sitra.fi) ISSN 1457-5728 (URL:http://www.sitra.fi) The publications can be ordered from Sitra, tel. -

Anssi Cebit Final
Nokia Mobile Phones – The next phase Nokia Investor seminar CeBIT 2002 Anssi Vanjoki Executive Vice President Nokia Mobile Phones 1 © NOKIA 2000 Outline • Nokia’s new product launches • Nokia 3410 • Nokia 3510 • Nokia 6310i • Nokia 9210i • Nokia 7210 • Mobile Device technology evolution • Convergence in Mobility • Summary 2 © NOKIA 2000 New Product Launches 3 © NOKIA 2000 • RealOne Player for streaming video • Flash Player allowing playback of Macromedia flash content • Considerably faster data processing • New web browser for JavaScripts support and HTML 4.01 compatibility • Enhanced security with Nokia VPN Client • Nokia GPS module for route assistance 4 © NOKIA 2000 Nokia and RealNetworks alliance • RealOne player to be included in Nokia’s Symbian based handsets • RealOne player to be licensed in Nokia Series 60 platform • RealSystem Streaming Server Software included in Nokia’s infrastructure solutions for mobile operators 5 © NOKIA 2000 • JavaTM 2 Micro Edition (J2ME TM) • Picture editor • 3D graphics engine • WAP 1.1 with push funtionality • 5 games: Link5, Space impact, Bantumi, Snake II, Bumper 6 © NOKIA 2000 • GPRS • Polyphonic (MIDI) sounds • Value added services (VAS) over Multimedia messaging (MMS) receive • Fun gaming concept • sounds, multiple keypress, vibra 7 © NOKIA 2000 FUNctional Accessory Covers 8 © NOKIA 2000 FILENAMEs.PPT/ DATE / NN • Tri-band GSM, GPRS, HSCSD • Multimedia messaging (MMS) • Java 2 Micro Edition (J2ME) • Series 40 user interface • High quality color display • Polyphonic (MIDI) sounds • Stereo FM radio • Integrated handsfree speaker Lord of the Clouds: Sumea ® 9 © NOKIA 2000 • Tri-band GSM, GPRS, HSCSD • Multimedia messaging (MMS) • Java 2 Micro Edition (J2ME) • Series 40 user interface • High quality color display • Polyphonic (MIDI) sounds • Stereo FM radio • Integrated handsfree speaker 10 © NOKIA 2000 • Tri-band GSM, GPRS, HSCSD • Java 2 Micro Edition (J2ME) • Bluetooth, infrared, cable • Wallet with WIM 11 © NOKIA 2000 Leadership in Product Portfolio 22 mobile phones announced in 2001. -
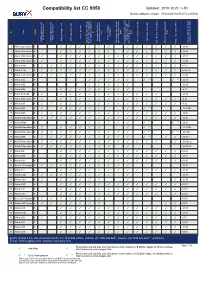
BURY Compatibility List Generator
Compatibility list CC 9050 Updated: 2010-12-21 / v.51 Device software version: APP:04.03.02/ DSW:01.02.0f/ BTS:01.47.12 (CC 9051M V06b) on No key keys Card Type tags) Profile activation service provider Phone s REDIAL A2DP from phone A2DP from device / private mode with Battery charge level Activation Bluetooth GSM-signal strength Call lists Missed calls A2DP supported start A2DP supported start connection with device Call lists Received calls Bluetooth connection to used to test/ Comments after ignition is switched Access to mobile phone Phone book entries SIM voice-dial function (voice the last connected phone Call lists Dialled numbers Phone book entries Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Nokia 2323 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 06.46 2 Nokia 2330 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 06.46 3 Nokia 2700 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 07.15 4 Nokia 2730 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 10.40 5 Nokia 3109c hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v07.21 6 Nokia 3110c hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ vp sk4.80 7 Nokia 3120 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 10.00 8 Nokia 3230 hf ✓ ✓ ✓ ✓ ✓ ✓ ** ✓ ** v 04.14 9 Nokia 3250 hf ✓ ✓ ✓ ✓ ✓ v 03.24 10 Nokia 3650 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 4.17 11 Nokia 3710 fold hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 03.80 12 Nokia 3720 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 3.92 13 Nokia 5200 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 3.92 14 Nokia 5230 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ** v 12.0.089 15 Nokia 5300 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 03.92 16 Nokia 5310 XpressMusic -

Cell Phones and Pdas
eCycle Group - Check Prices Page 1 of 19 Track Your Shipment *** Introductory Print Cartridge Version Not Accepted February 4, 2010, 2:18 pm Print Check List *** We pay .10 cents for all cell phones NOT on the list *** To receive the most for your phones, they must include the battery and back cover. Model Price Apple Apple iPhone (16GB) $50.00 Apple iPhone (16GB) 3G $75.00 Apple iPhone (32GB) 3G $75.00 Apple iPhone (4GB) $20.00 Apple iPhone (8GB) $40.00 Apple iPhone (8GB) 3G $75.00 Audiovox Audiovox CDM-8930 $2.00 Audiovox PPC-6600KIT $1.00 Audiovox PPC-6601 $1.00 Audiovox PPC-6601KIT $1.00 Audiovox PPC-6700 $2.00 Audiovox PPC-XV6700 $5.00 Audiovox SMT-5500 $1.00 Audiovox SMT-5600 $1.00 Audiovox XV-6600WOC $2.00 Audiovox XV-6700 $3.00 Blackberry Blackberry 5790 $1.00 Blackberry 7100G $1.00 Blackberry 7100T $1.00 Blackberry 7105T $1.00 Blackberry 7130C $2.00 http://www.ecyclegroup.com/checkprices.php?content=cell 2/4/2010 eCycle Group - Check Prices Page 2 of 19 Search for Pricing Blackberry 7130G $2.50 Blackberry 7290 $3.00 Blackberry 8100 $19.00 Blackberry 8110 $18.00 Blackberry 8120 $19.00 Blackberry 8130 $2.50 Blackberry 8130C $6.00 Blackberry 8220 $22.00 Blackberry 8230 $15.00 Blackberry 8300 $23.00 Blackberry 8310 $23.00 Blackberry 8320 $28.00 Blackberry 8330 $5.00 Blackberry 8350 $20.00 Blackberry 8350i $45.00 Blackberry 8520 $35.00 Blackberry 8700C $6.50 Blackberry 8700G $8.50 Blackberry 8700R $7.50 Blackberry 8700V $6.00 Blackberry 8703 $1.00 Blackberry 8703E $1.50 Blackberry 8705G $1.00 Blackberry 8707G $5.00 Blackberry 8707V -

Investigaciòn Sobre Automatizaciòn De Fuerza De Ventas Móvil
INVESTIGACIÒN SOBRE AUTOMATIZACIÒN DE FUERZA DE VENTAS MÓVIL MILENA ANDREA CASTILLO RUANO UNIVERSIDAD AUTÓNOMA DE OCCIDENTE FACULTAD DE INGENIERIAS DEPARTAMENTO DE AUTOMATICA Y ELECTRÓNICA PROGRAMA DE INGENIERÍA ELECTRONICA SANTIAGO DE CALI 2007 INVESTIGACIÓN SOBRE AUTOMATIZACIÓN DE FUERZA DE VENTAS MOVIL MILENA ANDREA CASTILLO RUANO Pasantía para optar el título de Ingeniera Electrónica Director Académico HÉCTOR JOSÉ GÓMEZ GONZÁLES Ingeniero Electrónico UNIVERSIDAD AUTÓNOMA DE OCCIDENTE FACULTAD DE INGENIERIAS DEPARTAMENTO DE AUTOMATICA Y ELECTRÓNICA PROGRAMA DE INGENIERÍA ELECTRONICA SANTIAGO DE CALI 2007 Nota de aceptación: Aprobado por el comité de grado en cumplimiento de los requisitos exigidos por la Universidad Autónoma de Occidente para optar al titulo de ingeniera electrónica. Ing. JUANA MARIA CAMPO Jurado Ing. ROBERTO DE JESÚS VEGA Jurado Santiago de Cali, febrero 8 de 2007 CONTENIDO Pág. GLOSARIO 10 RESUMEN 14 INTRODUCCIÓN 15 1. PLANTEAMIENTO DEL PROBLEMA 16 2. OBJETIVOS 17 2.1 OBJETIVO GENERAL 17 2.2 OBJETIVOS ESPECÍFICOS 17 3. JUSTIFICACIÓN 18 4. AUTOMATIZACION DE FUERZA DE VENTAS 19 4.1 DESCRIPCION DE LA IMPLEMENTACIÓN 19 4.1.1 DESCRIPCIÓN DE LA PLATAFORMA EMPLEADA 19 4.1.2 DESCRIPCIÓN DEL USUARIO 20 4.2 ARQUITECTURA DE LA APLICACIÓN 22 4.2.1 CORRIENDO EL PROYECTO 22 4.2 ESTABLECIMIENTO DE BENEFICIOS QUE SE DESEAN LOGRAR 30 4.3 CALIDAD DEL SERVICIO 30 5. INTRODUCCION A J2ME 31 5.1 ARQUITECTURA 31 5.1.1 SISTEMA OPERATIVO 31 5.1.2 JAVA VIRTUAL MACHINE (JVM) 31 5.1.3 CONFIGURACIÓN 32 5.1.4 PERFIL (PROFILE) 34 5.2 MIDP 34 5.2.1 -

Listado Liberaciones 9 Sept 2011
TODO EN ACCESORIOS TARIFA LIBERACIÓN TELÉFONOS MÓVILES ALCATEL PVD PVP PVD PVP PVD PVP Alcatel 153 3 9 Alcatel E221 3 9 Alcatel OT-565 3 9 Alcatel 155 3 9 Alcatel E227 3 9 Alcatel OT-600 3 9 Alcatel 156 3 9 Alcatel E230 3 9 Alcatel OT-606 3 9 Alcatel 303 3 9 Alcatel E252 3 9 Alcatel OT-660 3 9 Alcatel 311 3 9 Alcatel E256 3 9 Alcatel OT-708 3 9 Alcatel 320 3 9 Alcatel E257 3 9 Alcatel OT-710 3 9 Alcatel 331 3 9 Alcatel E259 3 9 Alcatel OT-799 3 9 Alcatel 332 3 9 Alcatel E260 3 9 Alcatel OT-800 3 9 Alcatel 355 3 9 Alcatel E265 3 9 Alcatel OT-802 3 9 Alcatel 363 3 9 Alcatel E801 3 9 Alcatel OT-806 3 9 Alcatel 50X 3 9 Alcatel Easy 3 9 Alcatel OT-808 3 9 Alcatel 511 3 9 Alcatel ELLE 3 9 Alcatel OT-809 3 9 Alcatel 512 3 9 Alcatel Mandarina 3 9 Alcatel OT-810 3 9 Alcatel 525 3 9 Alcatel Max db 3 9 Alcatel OT-811 3 9 Alcatel 526 3 9 Alcatel Misssixty 3 9 Alcatel OT-812 3 9 Alcatel 531 3 9 Alcatel OT-090 3 9 Alcatel OT-813 3 9 Alcatel 535 3 9 Alcatel OT-103 3 9 Alcatel OT-814 3 9 Alcatel 556 3 9 Alcatel OT-104 3 9 Alcatel OT-880 3 9 Alcatel 565 3 9 Alcatel OT-105 3 9 Alcatel OT-B331 3 9 Alcatel 70X 3 9 Alcatel OT-108 3 9 Alcatel OT-BIC 3 9 Alcatel 715 3 9 Alcatel OT-109 3 9 Alcatel OT-C700 3 9 Alcatel 715 3 9 Alcatel OT-111 3 9 Alcatel OT-C701 3 9 Alcatel 735 3 9 Alcatel OT-1650 3 9 Alcatel OT-F331 3 9 Alcatel 756 3 9 Alcatel OT-203 3 9 Alcatel OT-S319 3 9 Alcatel 757 3 9 Alcatel OT-204 3 9 Alcatel OT-S320 3 9 Alcatel 835 3 9 Alcatel OT-206 3 9 Alcatel OT-S321 3 9 Alcatel C550 3 9 Alcatel OT-208 3 9 Alcatel OT-S520 3 9 Alcatel C551 3 9 Alcatel -

Mobile Connection Explorer for Windows Introduction and Features
Mobile Connection Explorer 15 May 2013 for Windows Version 21 Introduction and Features Public version Gemfor s.r.o. Tyršovo nám. 600 252 63 Roztoky Czech Republic Gemfor s.r.o. Tyršovo nám. 600 252 63 Roztoky Czech Republic e-mail: [email protected] Contents Contents ...................................................................................................................... 2 History ......................................................................................................................... 3 1. Scope ..................................................................................................................... 3 2. Abbreviations ......................................................................................................... 4 3. Solution .................................................................................................................. 5 4. Specification ........................................................................................................... 5 5. Product description ................................................................................................. 9 5.1 Supported operating systems ....................................................................... 9 5.2 Hardware device connections ....................................................................... 9 5.3 Network connection types ............................................................................. 9 5.4 Customizable graphical skin ...................................................................... -

Dreambox - Siemens
GSM-Support ul. Bitschana 2/38, 31-420 Kraków, Poland mobile +48 608107455, NIP PL9451852164 REGON: 120203925 www.gsm-support.net DreamBox - Siemens DreamBox is a service software device for servicing and repairing Siemens phone models. It can unlock and flash C65, C66, C6C, C6V, C72, C75, CF75, CX65, CX70, CX75, CX7I, M65, M75, ME75, M6C S65, SK65, SK6R, SL65 without disassembling the phone, as well as many other phone models. Writes full flash/language at very high speed, automatic boot selection, partial flashing of ALL blocks, reports phone diagnostic codes, supports original Siemens flash file format (Winswup), works with custom settings. - unlock all locks and phone code - allow SP-Lock to any network - read/write EEPROM, firmware, flash - fast read/write language packs/T9 packs - repair all dead phones - repair IMEI - soft works at all known SW versions - works on all Windows systems (win95, win98, win ME, win2000, winXP etc.) - can flash and communicate with phones on high speeds (921600 bps ) on every PC - many boxes can be connected to one PC - fast flashing, stable work on every PC -remote UPDATE function (box firmware and software can be updgraded remotely) - from one side DreamBox is connected to PC through USB interface. From another, device has 2 inputs for connection with a phone. - can use other flash formats. DreamBox Service Software is an interface used with DreamBox to read/write flash, unlock/relock, restore/change imei, repair, read/write settings of the phone and other functions. Functional Operations Reading Phone Information This function allows you to gather important information about the phone (IMEI, flash model, SW version etc.) Reading full flash memory Use this chapter for reading and saving phone full flash. -

MOBILE GAMING: a Framework for Evaluating the Industry 2000-2005 JUSSI-PEKKA PARTANEN Copyright (C) 2001 Gaptime Century, Ltd
MOBILE GAMING: A Framework for Evaluating the Industry 2000-2005 JUSSI-PEKKA PARTANEN Copyright (C) 2001 Gaptime Century, Ltd. MOBILE GAMING: A FRAMEWORK FOR EVALUATING THE INDUSTRY 2000-2005 Abstract (English) Author: Jussi-Pekka Partanen, Gaptime Century Ltd. Report title: Mobile Gaming:A Framework for Evaluating the Industry 2000-2005 Date: 15.06.2001 Pages: 110 A mobile game is a commercial product that is distributed to the customer using mobile operator’s network. The game is an interactive product; many kinds of entertainment services are not covered by this report, such as joke or comics services or the popular ring tone and logo services. What distinguishes mobile games from other kinds of entertainment services is that the interactivity creates so-called stickiness for the service. The games may be addictive and offer something more than “disposable” fun, as operator logos do. The target of this study is to give an introduction to the mobile gaming industry and build a framework for analysing the success of mobile game products and companies. Currently the mobile gaming industry is in the introduction phase. Many start-up companies are developing different games and technologies and believe that they will be the winners when the market moves from introduction to the growth stage. At this point the company must have the critical mass in order to flourish, otherwise the companies with bigger better partnering networks and marketing and sales forces are eating the smaller one. The framework depends on the following methods: the industry and mobile game life cycle model, value distribution in the value delivery network and external company analysis. -

Catastrophic Cyber-Physical Malware∗
Catastrophic Cyber-Physical Malware∗ Suresh Kothari1, 2, Ganesh Ram Santhanam1, Payas Awadhutkar1, Benjamin Holland1, Jon Mathews2, and Ahmed Tamrawi2 1Department of Electrical and Computer Engineering, Iowa State University, Ames, IA 50011 2EnSoft Corp., 2625 N Loop Dr Suite 2580, Ames, IA 50010 Abstract With the advent of highly sophisticated cyber-physical malware (CPM) such as Industroyer, a cyber- attack could be as destructive as the terrorist attack on 9/11, and it would virtually paralyze the nation. We discuss as the major risks the vulnerability of: telecommunication infrastructure, industrial control systems (ICS), and mission-critical software. In differentiating CPM from traditional malware, the difference really comes from the open-ended possibilities for malware triggers resulting from the wide spectrum of sensor inputs, and the almost limitless application-specific possibilities for designing malicious payloads. Fundamentally, the challenges of detecting sophisticated CPM stem from the complexities inherent in the software at the heart of cyber-physical systems. We discuss three fundamental challenges: explosion of execution behaviors, computational intractability of checking feasible behaviors, and difficult-to-analyze programming constructs. In detecting novel CPM, the tasks are: developing plausible hypotheses for malware trigger and mali- cious payload, analyzing software to gather evidence based on CPM hypotheses, and verifying software to prove or refute a hypothesis based on the gathered evidence. We discuss research directions for effective automation to support these tasks. 1 Introduction The imminent danger of cyber-physical malware (CPM) is evident from attacks such as the power outage in Ukraine [122] or the hijacking of a Jeep Cherokee [83]. The net-centricity of modern systems offers an adversary affordable attack vectors through cyberspace against critical missions.