Mcafee Foundstone Fsl Update
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows Kernel Hijacking Is Not an Option: Memoryranger Comes to The
WINDOWS KERNEL HIJACKING IS NOT AN OPTION: MEMORYRANGER COMES TO THE RESCUE AGAIN Igor Korkin, PhD Independent Researcher Moscow, Russian Federation [email protected] ABSTRACT The security of a computer system depends on OS kernel protection. It is crucial to reveal and inspect new attacks on kernel data, as these are used by hackers. The purpose of this paper is to continue research into attacks on dynamically allocated data in the Windows OS kernel and demonstrate the capacity of MemoryRanger to prevent these attacks. This paper discusses three new hijacking attacks on kernel data, which are based on bypassing OS security mechanisms. The first two hijacking attacks result in illegal access to files open in exclusive access. The third attack escalates process privileges, without applying token swapping. Although Windows security experts have issued new protection features, access attempts to the dynamically allocated data in the kernel are not fully controlled. MemoryRanger hypervisor is designed to fill this security gap. The updated MemoryRanger prevents these new attacks as well as supporting the Windows 10 1903 x64. Keywords: hypervisor-based protection, Windows kernel, hijacking attacks on memory, memory isolation, Kernel Data Protection. 1. INTRODUCTION the same high privilege level as the OS kernel, and they also include a variety The security of users’ data and of vulnerabilities. Researchers applications depends on the security of consider that “kernel modules (drivers) the OS kernel code and data. Modern introduce additional attack surface, as operating systems include millions of they have full access to the kernel’s lines of code, which makes it address space” (Yitbarek and Austin, impossible to reveal and remediate all 2019). -

Microsoft Security Update for January 2020 Fixes 49 Security Vulnerabilities
Microsoft Security Update for January 2020 Fixes 49 Security Vulnerabilities Overview Microsoft released the January security update on Tuesday, fixing 49 security issues ranging from simple spoofing attacks to remote code execution, discovered in products like .NET Framework, Apps, ASP.NET, Common Log File System Driver, Microsoft Dynamics, Microsoft Graphics Component, Microsoft Office, Microsoft Scripting Engine, Microsoft Windows, Microsoft Windows Search Component, Windows Hyper-V, Windows Media, Windows RDP, Windows Subsystem for Linux, and Windows Update Stack. Of the vulnerabilities fixed by Microsoft's this monthly update, a total of eight critical vulnerabilities exist in the .NET Framework, ASP.NET, Microsoft Scripting Engine, and Windows RDP. In addition, there are 41 important vulnerabilities. Critical Vulnerabilities The following are eight critical vulnerabilities covered in this update. @NSFOUS 2020 http://www.nsfocus.com Windows RDP CVE-2020-0609、CVE-2020-0610 These two remote code execution vulnerabilities in the Windows Remote Desktop Gateway (RD Gateway) could be exploited by unauthenticated attackers. If the two vulnerabilities are exploited successfully, arbitrary code may be executed on the target system, allowing the attacker to install the program, view, change or delete data, or create a new account with full user rights. To exploit this vulnerability, an attacker needs to send a specially crafted request to the RD gateway of the target system via RDP. This update addresses these issues by correcting the way the RD gateway handles connection requests. For more details about the vulnerabilities and download updates, please refer to Microsoft's official security advisories: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0609 https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0610 CVE-2020-0611 This is a remote code execution vulnerability in Windows Remote Desktop clients. -

Leveraging Forticlient with Microsoft Defender: 6 Use Cases
SOLUTION BRIEF Leveraging FortiClient with Microsoft Defender: 6 Use Cases Executive Overview A compromised endpoint can quickly infect an entire enterprise network—which FortiClient Features Include: is why endpoint devices are now a favorite target for cyber criminals. More than an endpoint protection platform that provides automated, next-generation threat nnSecurity Fabric Connector. protection, FortiClient connects endpoints with the Security Fabric. It enables Enables endpoint visibility and endpoint visibility and compliance throughout the Security Fabric architecture. compliance throughout the Combining FortiClient with OS-embedded protection, such as Microsoft Security Fabric architecture. Defender or Microsoft Defender ATP, enhances these capabilities, providing nnVulnerability scanning. an integrated endpoint and network security solution that reinforces enterprise Detects and patches endpoint defenses, reduces complexity, and enhances the end-user experience. vulnerabilities. nn Improving Protection of Endpoint Devices Anti-malware protection. Employs machine learning (ML), FortiClient provides automated threat protection and endpoint vulnerability scanning to help artificial intelligence (AI), and maintain endpoint security hygiene and deliver risk-based visibility across the Fortinet Security cloud-based threat detection Fabric architecture. As a result, organizations can identify and remediate vulnerabilities or in addition to pattern-based compromised hosts across the entire attack surface. malware detection. In some cases, customers may wish to take advantage of certain FortiClient features while nnAnti-exploit engine. Uses leaving existing third-party protections in place. For example, in instances where there are signatureless, behavior-based policies in an organization that require two different antivirus (AV) vendors on an endpoint protection against memory and for governance or compliance reasons, the need for FortiClient alongside a third-party AV fileless attacks; detects exploit solution such as Microsoft Defender is necessitated. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Microsoft Expands Capabilities and Platforms for Microsoft Defender ATP
REPORT REPRINT Microsoft expands capabilities and platforms for Microsoft Defender ATP JULY 31 2020 By Fernando Montenegro The company has been pouring significant resources into growing its capabilities as a provider of security functionality. It appears to be making significant inroads into the endpoint security space, given its role behind the Windows OS and on account of its Defender ATP offering, which was recently updated. THIS REPORT, LICENSED TO MICROSOFT, DEVELOPED AND AS PROVIDED BY 451 RESEARCH, LLC, WAS PUBLISHED AS PART OF OUR SYNDICATED MARKET INSIGHT SUBSCRIPTION SER- VICE. IT SHALL BE OWNED IN ITS ENTIRETY BY 451 RESEARCH, LLC. THIS REPORT IS SOLELY INTENDED FOR USE BY THE RECIPIENT AND MAY NOT BE REPRODUCED OR RE-POSTED, IN WHOLE OR IN PART, BY THE RECIPIENT WITHOUT EXPRESS PERMISSION FROM 451 RESEARCH. ©2020 451 Research, LLC | WWW.451RESEARCH.COM REPORT REPRINT Introduction Endpoint security had been growing in importance as a key component of security architecture even before the COVID-19 health crisis. Back then, key trends such as user mobility, BYOD and increased use of encryption already meant that properly securing and capturing telemetry from endpoints was crucial for protection, detection and incident response. The COVID-19 crisis merely accelerated this as network connectivity patterns changed and corporate offices sat empty. In recent years the endpoint security market has seen significant change, including the rise in popularity of Microsoft’s offerings, particularly its Microsoft Defender Advanced Threat Protection (MDATP) component. The company has been expanding the capabilities of the product as it adds support for new environments and partners. -

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -

3700Document22374461
Copyright (c) 2018, Oracle. All rights reserved. RES QA / Test – Microsoft Patch Security Report (Doc ID 2237446.1) To Bottom Modified: 16-Apr-2018 Type: REFERENCE In this Document Purpose Scope Details Windows Security Updates Miscellaneous Information Internet Explorer 7 Known Issues Internet Explorer 8 Known Issues Internet Explorer 9 Known Issues Internet Explorer 10 Known Issues Internet Explorer 11 Known Issues Adobe Known Issues Non-Security, High Priority Updates Microsoft Security Essentials References APPLIES TO: Oracle Hospitality RES 3700 - Version 4.9.0 and later Information in this document applies to any platform. PURPOSE The Security Report contains a listing of select Microsoft patches that are directly related to the RES and E7 applications and have been tested against the RES and E7 applications to validate there are no issues or identify any updates that should NOT be installed. The list is not inclusive of ALL Microsoft patches. This report is updated monthly for patches released monthly and YTD cumulative. SCOPE This document is intended for support employees and users of the RES E7 products. DETAILS WARNING: On Workstation 2015 – POSReady 2009, the Microsoft “Optional Hardware” Update, “MosChip Semiconductor Technology Ltd – Bus Controllers and Ports – PCI Multi-IO Controller” is incompatible with the RES IDN Driver, and will cause IDN Printing to fail. Even if this update is uninstalled, IDN printing could be effected adversely. DO NOT INSTALL THIS Optional MICROSOFT UPDATE. If this was already done, reload the Ghost image for the 2015 posted on MOS, and reload all other applicable Microsoft Updates. As of August of 2016 the RES Microsoft security bulletin has been split off from the combined RES/e7 bulletin. -

Configuration Sheets
PRIMERGY RX600 S4 Configuration Sheets About this manual A Configuration Sheets of Hardware Use this form to record the hardware configuration and various settings of your server. B Configuration Sheets of BIOS Setup Utility Parameters Use this form to record the settings of the BIOS Setup Utility. C Configuration Sheets of Remote Management Controller's Web Interface Use this form to record the settings of the Remote Management Controller Web interface. D Design Sheet of the RAID Configuration Use this form to record the definitions of the disk groups (or the physical packs) and the logical drives in the RAID configuration (array configuration). E Design Sheet Use this form to record the software settings. F Accident Sheet Use this form to record any failures that occur in your server. 1 Product Names The following expressions and abbreviations are used to describe the product names used in this manual. Product names Expressions and abbreviations PRIMERGY RX600 S4 This server or the server Windows Server 2003 R2, Windows Microsoft® Windows Server® 2003 R2, Standard Edition Standard Edition 2003 Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2, Enterprise Edition Enterprise Edition Windows Server 2003 , Microsoft® Windows Server® 2003 , Enterprise Edition Enterprise Edition Windows Server 2003, Microsoft® Windows Server® 2003, Standard Edition Standard Edition Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2, Standard x64 Edition Standard x64 Edition Windows Server 2003 R2, Microsoft® Windows Server® 2003 R2 , Enterprise x64 Edition Enterprise x64 Edition Windows Server 2003, Microsoft® Windows Server® 2003, Standard x64 Edition Standard x64 Edition Windows Server 2003 , Microsoft® Windows Server® 2003 , Enterprise x64 Edition Enterprise x64 Edition Microsoft® Windows Server® 2003 Service Pack SP ■Trademarks Microsoft, Windows, MS, Windows Server are registered trademarks of the Microsoft Corporation in the USA and other countries. -

Microsoft Defender ATP.Pdf
Traditional Approach THE SENSORS FABRIC WE DEPLOY Threat Intelligence (TIaaS) Data Loss Prevention Cloud (Office IP/DLP) Directory Services Malware Detection Cloud DC Management User/Entity Behavior Analytics (AAD) (Office ATP/Sonar) (ASC) (AADIP) Classification and Information Protection (AIP) Cloud Application Federation Services Security Broker (ADFS) (MCAS) User/Entity Behavior Analytics (ATA) On Premises On Premises Directory Mobile Device Management DC Management Services (Intune) (OMS) (AD) Endpoint Protection (Defender) LOCALIZED INTELLIGENCE Threat Intelligence (TIaaS) Cloud Data Loss Prevention Directory Services (Office IP/DLP) Malware Detection Cloud DC Management User/Entity Behavior Analytics (AAD) (Office ATP) (ASC) (AADIP) Classification and Information Protection (AIP) Cloud Application Federation Services Security Broker (ADFS) (MCAS) User/Entity Behavior Analytics (ATA) On Premises On Premises Directory Mobile Device Management DC Management Services (Intune) (OMS) (AD) Endpoint Protection (Defender) Microsoft Azure Windows Defender Advanced Threat Protection rules Require the device to be at or under the machine risk score: Set up a connection to Windows Defender Advanced Threat Protection Microsoft 365 ATP | Windows Machine Search for machine, user, file, IP and URL [email protected] Smith m Security operation dashboard Open incidents Statistics Attention required (41) Incidents severities Incident in-progress #1067 In progress Jon-Smith-Lap HIGH MEDIUM LOW INFORMATIONAL Golden ticket compromise: user permissions -

Summary Report 2020 Awards, Winners, Comments
Independent Tests of Anti-Virus Software Summary Report 2020 Awards, winners, comments TEST PERIOD : 2020 LANGUAGE : ENGLISH LAST REVISION : 15TH JANUARY 2021 WWW.AV-COMPARATIVES.ORG Summary Report 2020 www.av-comparatives.org Content INTRODUCTION 3 MANAGEMENT SUMMARY 5 ANNUAL AWARDS 9 PRICING 16 USER EXPERIENCE REVIEW 18 AVAST FREE ANTIVIRUS 21 AVG ANTIVIRUS FREE 24 AVIRA ANTIVIRUS PRO 27 BITDEFENDER INTERNET SECURITY 30 ESET INTERNET SECURITY 34 F-SECURE SAFE 38 G DATA INTERNET SECURITY 41 K7 TOTAL SECURITY 45 KASPERSKY INTERNET SECURITY 48 MCAFEE TOTAL PROTECTION 52 MICROSOFT DEFENDER ANTIVIRUS 55 NORTONLIFELOCK NORTON 360 DELUXE 58 PANDA FREE ANTIVIRUS 61 TOTAL AV ANTIVIRUS PRO 64 TOTAL DEFENSE ESSENTIAL ANTI-VIRUS 67 TREND MICRO INTERNET SECURITY 70 VIPRE ADVANCED SECURITY 73 FEATURELIST COMES HERE 76 COPYRIGHT AND DISCLAIMER 77 2 Summary Report 2020 www.av-comparatives.org Introduction About AV-Comparatives We are an independent test lab, providing rigorous testing of security software products. We were founded in 2004 and are based in Innsbruck, Austria. AV-Comparatives is an ISO 9001:2015 certified organisation. We received the TÜV Austria certificate for our management system for the scope: “Independent Tests of Anti-Virus Software”. http://www.av-comparatives.org/iso-certification/ AV-Comparatives is the first certified EICAR Trusted IT-Security Lab http://www.av-comparatives.org/eicar-trusted-lab/ At the end of every year, AV-Comparatives releases a Summary Report to comment on the various consumer anti-virus products tested over the course of the year, and to highlight the high-scoring products of the different tests that took place over the twelve months. -

Linux Networking 101
The Gorilla ® Guide to… Linux Networking 101 Inside this Guide: • Discover how Linux continues its march toward world domination • Learn basic Linux administration tips • See how easy it can be to build your entire network on a Linux foundation • Find out how Cumulus Linux is your ticket to networking freedom David M. Davis ActualTech Media Helping You Navigate The Technology Jungle! In Partnership With www.actualtechmedia.com The Gorilla Guide To… Linux Networking 101 Author David M. Davis, ActualTech Media Editors Hilary Kirchner, Dream Write Creative, LLC Christina Guthrie, Guthrie Writing & Editorial, LLC Madison Emery, Cumulus Networks Layout and Design Scott D. Lowe, ActualTech Media Copyright © 2017 by ActualTech Media. All rights reserved. No portion of this book may be reproduced or used in any manner without the express written permission of the publisher except for the use of brief quotations. The information provided within this eBook is for general informational purposes only. While we try to keep the information up- to-date and correct, there are no representations or warranties, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the information, products, services, or related graphics contained in this book for any purpose. Any use of this information is at your own risk. ActualTech Media Okatie Village Ste 103-157 Bluffton, SC 29909 www.actualtechmedia.com Entering the Jungle Introduction: Six Reasons You Need to Learn Linux ....................................................... 7 1. Linux is the future ........................................................................ 9 2. Linux is on everything .................................................................. 9 3. Linux is adaptable ....................................................................... 10 4. Linux has a strong community and ecosystem ........................... 10 5. -
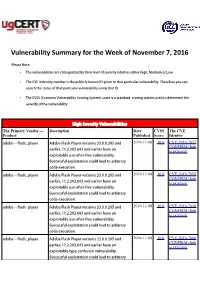
Vulnerability Summary for the Week of November 7, 2016
Vulnerability Summary for the Week of November 7, 2016 Please Note: • The vulnerabilities are cattegorized by their level of severity which is either High, Medium or Low. • The !" indentity number is the #ublicly $nown %& given to that #articular vulnerability. Therefore you can search the status of that #articular vulnerability using that %&. • The !'S (Common !ulnerability 'coring System) score is a standard scoring system used to determine the severity of the vulnerability. High Severity Vulnerabilities The Primary Vendor --- Description Date CVSS The CVE Product Published Score Identity adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7857 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7858 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7859 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable use*after*free vulnerability. 'uccessful e5#loitation could lead to arbitrary code e5ecution. adobe ** flash+#layer ,dobe -lash Player versions ./.0.0..01 and 2016-11-08 10.0 CVE-2016-7860 CONFIRM (link earlier, 22...20..64/ and earlier have an is external) e5#loitable type confusion vulnerability.