Cryptographic Hash Functions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IMPLEMENTATION and BENCHMARKING of PADDING UNITS and HMAC for SHA-3 CANDIDATES in FPGAS and ASICS by Ambarish Vyas a Thesis Subm
IMPLEMENTATION AND BENCHMARKING OF PADDING UNITS AND HMAC FOR SHA-3 CANDIDATES IN FPGAS AND ASICS by Ambarish Vyas A Thesis Submitted to the Graduate Faculty of George Mason University in Partial Fulfillment of The Requirements for the Degree of Master of Science Computer Engineering Committee: Dr. Kris Gaj, Thesis Director Dr. Jens-Peter Kaps. Committee Member Dr. Bernd-Peter Paris. Committee Member Dr. Andre Manitius, Department Chair of Electrical and Computer Engineering Dr. Lloyd J. Griffiths. Dean, Volgenau School of Engineering Date: ---J d. / q /9- 0 II Fall Semester 2011 George Mason University Fairfax, VA Implementation and Benchmarking of Padding Units and HMAC for SHA-3 Candidates in FPGAs and ASICs A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science at George Mason University By Ambarish Vyas Bachelor of Science University of Pune, 2009 Director: Dr. Kris Gaj, Associate Professor Department of Electrical and Computer Engineering Fall Semester 2011 George Mason University Fairfax, VA Copyright c 2011 by Ambarish Vyas All Rights Reserved ii Acknowledgments I would like to use this oppurtunity to thank the people who have supported me throughout my thesis. First and foremost my advisor Dr.Kris Gaj, without his zeal, his motivation, his patience, his confidence in me, his humility, his diverse knowledge, and his great efforts this thesis wouldn't be possible. It is difficult to exaggerate my gratitude towards him. I also thank Ekawat Homsirikamol for his contributions to this project. He has significantly contributed to the designs and implementations of the architectures. Additionally, I am indebted to my student colleagues in CERG for providing a fun environment to learn and giving invaluable tips and support. -

Intro to Cryptography 1 Introduction 2 Secure Password Manager
Programming Assignment 1 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, Feb. 8, 11:59pm 1 Introduction In many software systems today, the primary weakness often lies in the user’s password. This is especially apparent in light of recent security breaches that have highlighted some of the weak passwords people commonly use (e.g., 123456 or password). It is very important, then, that users choose strong passwords (or “passphrases”) to secure their accounts, but strong passwords can be long and unwieldy. Even more problematic, the user generally has many different services that use password authentication, and as a result, the user has to recall many different passwords. One way for users to address this problem is to use a password manager, such as LastPass and KeePass. Password managers make it very convenient for users to use a unique, strong password for each service that requires password authentication. However, given the sensitivity of the data contained in the password manager, it takes considerable care to store the information securely. In this assignment, you will be writing a secure and efficient password manager. In your implemen- tation, you will make use of various cryptographic primitives we have discussed in class—notably, authenticated encryption and collision-resistant hash functions. Because it is ill-advised to imple- ment your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic tem- plate, which you will be able to fill in to satisfy the functionality and security properties described below. -

Lecture9.Pdf
Merkle- Suppose H is a Damgaord hash function built from a secure compression function : several to build a function ways keyed : m : = H Ilm 1 . end FCK ) (k ) Prep key , " " ↳ - Insecure due to structure of Merkle : can mount an extension attack: H (KH m) can Barnyard given , compute ' Hlkllmllm ) by extending Merkle- Danged chain = : m : 2 . FCK ) 11k) Append key , Hlm ↳ - - to : Similar to hash then MAC construction and vulnerable same offline attack adversary finds a collision in the - - > Merkle and uses that to construct a for SHA I used PDF files Barnyard prefix forgery f , they ↳ - Structure in SHA I (can matches exploited collision demonstration generate arbitrary collisions once prefix ) ' = : FCK m - H on h 3. method , ) ( K HMH K) for reasonable randomness ( both Envelope pseudo assumptions e.g , : = - = i - - : F ( m m } : h K m h m k 4. nest ( ki ) H Ck H (k m ( , and m ( ) is a PRF both Two , kz , ) (ka HH , )) F- , ) ) Falk , ) , ) key , - of these constructions are secure PRFS on a variable size domain hash- based MAC ✓ a the - nest with correlated : HMAC is PRF / MAC based on two key (though keys) : = m H H ka m HMACCK ( K H ( , )) , ) , where k ← k ④ and kz ← k to , ipad opad and and are fixed ( in the HMAC standard) ipad opad strings specified I 0×36 repeated %x5C repeated : k . a Since , and ka are correlated need to make on h remains under Sety , stronger assumption security leg , pseudorandom related attack) Instantiations : denoted HMAC- H where H is the hash function Typically , HMAC- SHAI %" - - HMAC SHA256 -

Authenticated Key-Exchange: Protocols, Attacks, and Analyses
The HMAC construction: A decade later Ran Canetti IBM Research What is HMAC? ● HMAC: A Message Authentication Code based on Cryptographic Hash functions [Bellare-C-Krawczyk96]. ● Developed for the IPSec standard of the Internet Engineering Task Force (IETF). ● Currently: - incorporated in IPSec, SSL/TLS, SSH, Kerberos, SHTTP, HTTPS, SRTP, MSEC, ... - ANSI and NIST standards - Used daily by all of us. Why is HMAC interesting? ● “Theoretical” security analysis impacts the security of real systems. ● Demonstrates the importance of modelling and abstraction in practical cryptography. ● The recent attacks on hash functions highlight the properties of the HMAC design and analysis. ● Use the HMAC lesson to propose requirements for the next cryptographic hash function. Organization ● Authentication, MACs, Hash-based MACs ● HMAC construction and analysis ● Other uses of HMAC: ● Pseudo-Random Functions ● Extractors ● What properties do we want from a “cryptographic hash function”? Authentication m m' A B The goal: Any tampering with messages should be detected. “If B accepts message m from A then A has sent m to B.” • One of the most basic cryptographic tasks • The basis for any security-conscious interaction over an open network Elements of authentication The structure of typical cryptographic solutions: • Initial entity authentication: The parties perform an initial exchange, bootstrapping from initial trusted information on each other. The result is a secret key that binds the parties to each other. • Message authentication: The parties use the key to authenticate exchanged messages via message authentication codes. Message Authentication Codes m,t m',t' A B t=FK(m) t' =? FK(m') • A and B obtain a common secret key K • A and B agree on a keyed function F • A sends t=FK(m) together with m • B gets (m',t') and accepts m' if t'=FK(m'). -

User Authentication and Cryptographic Primitives
User Authentication and Cryptographic Primitives Brad Karp UCL Computer Science CS GZ03 / M030 16th November 2016 Outline • Authenticating users – Local users: hashed passwords – Remote users: s/key – Unexpected covert channel: the Tenex password- guessing attack • Symmetric-key-cryptography • Public-key cryptography usage model • RSA algorithm for public-key cryptography – Number theory background – Algorithm definition 2 Dictionary Attack on Hashed Password Databases • Suppose hacker obtains copy of password file (until recently, world-readable on UNIX) • Compute H(x) for 50K common words • String compare resulting hashed words against passwords in file • Learn all users’ passwords that are common English words after only 50K computations of H(x)! • Same hashed dictionary works on all password files in world! 3 Salted Password Hashes • Generate a random string of bytes, r • For user password x, store [H(r,x), r] in password file • Result: same password produces different result on every machine – So must see password file before can hash dictionary – …and single hashed dictionary won’t work for multiple hosts • Modern UNIX: password hashes salted; hashed password database readable only by root 4 Salted Password Hashes • Generate a random string of bytes, r Dictionary• For user password attack still x, store possible [H(r,x after), r] in attacker seespassword password file file! Users• Result: should same pick password passwords produces that different aren’t result close to ondictionary every machine words. – So must see password file -

Hash Functions
Hash Functions A hash function is a function that maps data of arbitrary size to an integer of some fixed size. Example: Java's class Object declares function ob.hashCode() for ob an object. It's a hash function written in OO style, as are the next two examples. Java version 7 says that its value is its address in memory turned into an int. Example: For in an object of type Integer, in.hashCode() yields the int value that is wrapped in in. Example: Suppose we define a class Point with two fields x and y. For an object pt of type Point, we could define pt.hashCode() to yield the value of pt.x + pt.y. Hash functions are definitive indicators of inequality but only probabilistic indicators of equality —their values typically have smaller sizes than their inputs, so two different inputs may hash to the same number. If two different inputs should be considered “equal” (e.g. two different objects with the same field values), a hash function must re- spect that. Therefore, in Java, always override method hashCode()when overriding equals() (and vice-versa). Why do we need hash functions? Well, they are critical in (at least) three areas: (1) hashing, (2) computing checksums of files, and (3) areas requiring a high degree of information security, such as saving passwords. Below, we investigate the use of hash functions in these areas and discuss important properties hash functions should have. Hash functions in hash tables In the tutorial on hashing using chaining1, we introduced a hash table b to implement a set of some kind. -

To Change Your Ud Password(S)
TO CHANGE YOUR UD PASSWORD(S) The MyCampus portal allows the user a single-signon for campus applications. IMPORTANT NOTICE AT BOTTOM OF THESE INSTRUCTIONS !! INITIAL PROCEDURE TO ALLOW YOU TO CHANGE YOUR PASSWORD ON THE UD NETWORK : 1. In your web browser, enter http://mycampus.dbq.edu . If you are logging in for the first time, you will be directed to answer (3) security questions. Also, be sure to answer one of the recovery methods. 2. Once the questions are answered, you will click on SUBMIT and then CONTINUE and then YES. 3. In one location, you will now find MyUD, Campus Portal, Email and UDOnline (Moodle). 4. You can now click on any of these apps and you will be logged in already. The email link will prompt you for the password a second time until we get all accounts set up properly. YOU MUST BE SURE TO LOGOUT OF EACH APPLICATION AFTER YOU’RE DONE USING IT !! TO CHANGE YOUR PASSWORD: 1. After you have logged into the MyCampus.dbq.edu website, you will see your username in the upper- right corner of the screen. 2. Click on your name and then go into My Account. 3. At the bottom, you will click on Change Password and then proceed as directed. 4. You can now logout. You will need to use your new password on your next login. Password must be a minimum of 6 characters and contain 3 of the following 4 categories: - Uppercase character - Lowercase character - Number - Special character You cannot use the previous password You’ll be required to change your password every 180 days. -
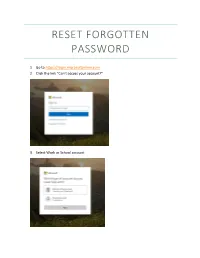
Reset Forgotten Password with Office365
RESET FORGOTTEN PASSWORD 1. Go to https://login.microsoftonline.com 2. Click the link “Can’t access your account?” 3. Select Work or School account 4. Enter in your User ID with the @uamont.edu at the end and then enter the characters as seen in the picture. You can click the refresh button for a different set of letters. 5. You will have 3 options to verify your account and reset your password. This information was set up when you registered with self-service password reset. If you have not registered, please go to https://aka.ms/ssprsetup and enter in your information. A step by step guide on how to do this can be found here. a. Text your mobile phone b. Call your mobile phone c. Answer Security Questions 6. Choose one option and enter the information requested 7. Click Text for text my mobile phone, Call for call my mobile phone, or click Next when you’ve answered all security questions. a. If you have selected Text my mobile phone you will be required to enter in a verification code and click Next b. If you have select Call my mobile phone you will receive a call and will need to enter # to verify. 8. Enter in your new password and click Finish a. Note: If you receive the message, “Unfortunately, your password contains a word, phrase, or pattern that makes it easily guessable. Please try again with a different password.” Please try to create a password that does not use any dictionary words. b. Passwords must meet 3 of the 4 following requirements i. -

Horner's Method: a Fast Method of Evaluating a Polynomial String Hash
Olympiads in Informatics, 2013, Vol. 7, 90–100 90 2013 Vilnius University Where to Use and Ho not to Use Polynomial String Hashing Jaku' !(CHOCKI, $ak&' RADOSZEWSKI Faculty of Mathematics, Informatics and Mechanics, University of Warsaw Banacha 2, 02-097 Warsaw, oland e-mail: {pachoc$i,jrad}@mimuw.edu.pl Abstract. We discuss the usefulness of polynomial string hashing in programming competition tasks. We sho why se/eral common choices of parameters of a hash function can easily lead to a large number of collisions. We particularly concentrate on the case of hashing modulo the size of the integer type &sed for computation of fingerprints, that is, modulo a power of t o. We also gi/e examples of tasks in hich strin# hashing yields a solution much simpler than the solutions obtained using other known algorithms and data structures for string processing. Key words: programming contests, hashing on strings, task e/aluation. 1. Introduction Hash functions are &sed to map large data sets of elements of an arbitrary length 3the $eys4 to smaller data sets of elements of a 12ed length 3the fingerprints). The basic appli6 cation of hashing is efficient testin# of equality of %eys by comparin# their 1ngerprints. ( collision happens when two different %eys ha/e the same 1ngerprint. The ay in which collisions are handled is crucial in most applications of hashing. Hashing is particularly useful in construction of efficient practical algorithms. Here e focus on the case of the %eys 'ein# strings o/er an integer alphabetΣ= 0,1,...,A 1 . 5he elements ofΣ are called symbols. -

BLAKE2: Simpler, Smaller, Fast As MD5
BLAKE2: simpler, smaller, fast as MD5 Jean-Philippe Aumasson1, Samuel Neves2, Zooko Wilcox-O'Hearn3, and Christian Winnerlein4 1 Kudelski Security, Switzerland [email protected] 2 University of Coimbra, Portugal [email protected] 3 Least Authority Enterprises, USA [email protected] 4 Ludwig Maximilian University of Munich, Germany [email protected] Abstract. We present the hash function BLAKE2, an improved version of the SHA-3 finalist BLAKE optimized for speed in software. Target applications include cloud storage, intrusion detection, or version control systems. BLAKE2 comes in two main flavors: BLAKE2b is optimized for 64-bit platforms, and BLAKE2s for smaller architectures. On 64- bit platforms, BLAKE2 is often faster than MD5, yet provides security similar to that of SHA-3: up to 256-bit collision resistance, immunity to length extension, indifferentiability from a random oracle, etc. We specify parallel versions BLAKE2bp and BLAKE2sp that are up to 4 and 8 times faster, by taking advantage of SIMD and/or multiple cores. BLAKE2 reduces the RAM requirements of BLAKE down to 168 bytes, making it smaller than any of the five SHA-3 finalists, and 32% smaller than BLAKE. Finally, BLAKE2 provides a comprehensive support for tree-hashing as well as keyed hashing (be it in sequential or tree mode). 1 Introduction The SHA-3 Competition succeeded in selecting a hash function that comple- ments SHA-2 and is much faster than SHA-2 in hardware [1]. There is nev- ertheless a demand for fast software hashing for applications such as integrity checking and deduplication in filesystems and cloud storage, host-based intrusion detection, version control systems, or secure boot schemes. -

Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption
S S symmetry Article Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption Rafael Álvarez 1,* , Alicia Andrade 2 and Antonio Zamora 3 1 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain 2 Fac. Ingeniería, Ciencias Físicas y Matemática, Universidad Central, Quito 170129, Ecuador; [email protected] 3 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain; [email protected] * Correspondence: [email protected] Received: 2 November 2018; Accepted: 22 November 2018; Published: 3 December 2018 Abstract: Password-based key derivation functions (PBKDFs) are commonly used to transform user passwords into keys for symmetric encryption, as well as for user authentication, password hashing, and preventing attacks based on custom hardware. We propose two optimized alternatives that enhance the performance of a previously published PBKDF. This design is based on (1) employing a symmetric cipher, the Advanced Encryption Standard (AES), as a pseudo-random generator and (2) taking advantage of the support for the hardware acceleration for AES that is available on many common platforms in order to mitigate common attacks to password-based user authentication systems. We also analyze their security characteristics, establishing that they are equivalent to the security of the core primitive (AES), and we compare their performance with well-known PBKDF algorithms, such as Scrypt and Argon2, with favorable results. Keywords: symmetric; encryption; password; hash; cryptography; PBKDF 1. Introduction Key derivation functions are employed to obtain one or more keys from a master secret. This is especially useful in the case of user passwords, which can be of arbitrary length and are unsuitable to be used directly as fixed-size cipher keys, so, there must be a process for converting passwords into secret keys. -

Why Simple Hash Functions Work: Exploiting the Entropy in a Data Stream∗
Why Simple Hash Functions Work: Exploiting the Entropy in a Data Stream¤ Michael Mitzenmachery Salil Vadhanz School of Engineering & Applied Sciences Harvard University Cambridge, MA 02138 fmichaelm,[email protected] http://eecs.harvard.edu/»fmichaelm,salilg October 12, 2007 Abstract Hashing is fundamental to many algorithms and data structures widely used in practice. For theoretical analysis of hashing, there have been two main approaches. First, one can assume that the hash function is truly random, mapping each data item independently and uniformly to the range. This idealized model is unrealistic because a truly random hash function requires an exponential number of bits to describe. Alternatively, one can provide rigorous bounds on performance when explicit families of hash functions are used, such as 2-universal or O(1)-wise independent families. For such families, performance guarantees are often noticeably weaker than for ideal hashing. In practice, however, it is commonly observed that simple hash functions, including 2- universal hash functions, perform as predicted by the idealized analysis for truly random hash functions. In this paper, we try to explain this phenomenon. We demonstrate that the strong performance of universal hash functions in practice can arise naturally from a combination of the randomness of the hash function and the data. Speci¯cally, following the large body of literature on random sources and randomness extraction, we model the data as coming from a \block source," whereby each new data item has some \entropy" given the previous ones. As long as the (Renyi) entropy per data item is su±ciently large, it turns out that the performance when choosing a hash function from a 2-universal family is essentially the same as for a truly random hash function.