Insights:Security in PC and LAPTOP SECURITY in THIS ISSUE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Unisys Company Overview Disclaimer
Unisys Company Overview Disclaimer • This presentation includes certain financial measures not presented in accordance with U.S. generally accepted accounting principles (“GAAP”), including, but not limited to, EBITDA, Adjusted EBITDA, Free Cash Flow, Adjusted Free Cash Flow, and constant currency, and certain ratios and other metrics derived therefrom. These non-GAAP financial measures are not measures of financial performance in accordance with GAAP and may exclude items that are significant in understanding and assessing the Company’s financial results. • Therefore, these measures should not be considered in isolation or as an alternative to cash flows from operations or other measures of profitability, liquidity or performance under GAAP. You should be aware that the Company’s presentation of these measures may not be comparable to similarly-titled measures used by other companies. Reconciliations of all non-GAAP financial measures are available in this presentation. © 2016 Unisys Corporation. All rights reserved. 2 Unisys at a Glance >1,500 >20,000 130+ $3.0B Global clients Associates Countries 2015 globally served revenue >60 million air cargo 300 government transactions per agencies worldwide month More than 90 of the Fortune Global 500 companies Over half of the top 25 global banks and 18 of the top 25 Building one of the 10 of the world’s global airlines largest cloud-based, on top insurance demand U.S. state companies government computing environments © 2016 Unisys Corporation | All rights reserved. 3 Key Company Highlights 1 Diversified Revenue Model 2 Long-Standing Relationships with Blue-chip Client Base 3 Leading-Edge Technological Solutions 4 Recurring Service Revenue with Large Contractual Backlog 5 Financial Progress 6 Experienced Management Team © 2016 Unisys Corporation. -

Cynthia Kyriazis Is a Productivity Strategist, Organization Consultant, Time Management Coach, Speaker, and Author
Cynthia Kyriazis is a productivity strategist, organization consultant, time management coach, speaker, and author. She leads decision-makers, their teams, and staff in navigating the 24/7 demands on their time and energy by developing a clear line of sight on what’s important and a plan for how to get there. 80% of Cynthia’s clients report saving at least 45 minutes a day in real time and 91% have improved their overall productivity. Cynthia possesses a 20-year track record of success in serving Fortune 500 companies, entrepreneurial businesses, government, and non-profit agencies. Regardless of the organization size, Cynthia guides leaders and Cynthia star performers to make choices that create and sustain a productive kyriazis mindset, and positively impact both personal growth and organizational profitability. Cynthia is the Amazon best-selling author of Get Organized. Get Focused. Get Productivity Moving. How to Overcome Productivity Potholes. She has also been featured & Organization as an expert on Forbes.com, Wall Street Journal online, the Philadelphia Consultant Inquirer, Legal Intelligencer, and many regional publications, radio, and television shows – and was named one of the “28 Best Online Productivity Experts” by New York Times best-selling author Hank Reardon in his book Time Management 2.0. Organizations Qualifications & Education We Have Served • Past-Secretary to the National Association of Professional Organizers (NAPO) • American Diabetes Association • Past-President of the Kansas City chapter of the International Society for • Avery Dennison Performance Improvement (KC-ISPI) • Bayer HealthCare • Consultant to the American Coaching Association • Campbell Soup Company • Certified Professional Behavioral Analyst (CPBA) • Cerner • Certified Professional Values Analyst (CPVA) • Cisco • B.S., Communication, University of Kansas • Coca Cola Bottling • Eli Lily Endorsements • GlaxoSmithKline • G.E. -
Astrazeneca-Oxford Vaccine Approved for Use in the U.K
P2JW366000-6-A00100-17FFFF5178F ****** THURSDAY,DECEMBER 31,2020~VOL. CCLXXVI NO.154 WSJ.com HHHH $4.00 DJIA 30409.56 À 73.89 0.2% NASDAQ 12870.00 À 0.2% STOXX 600 400.25 g 0.3% 10-YR. TREAS. À 3/32 , yield 0.926% OIL $48.40 À $0.40 GOLD $1,891.00 À $10.50 EURO $1.2300 YEN 103.21 Deadly Attack at Airport Targets New Yemen Government U.S. IPO What’s News Market Reaches Business&Finance Record nvestorspiled into IPOs Iat a record rate in 2020, with companies raising Total $167.2 billion via 454 of- ferings on U.S. exchanges this year through Dec. 24. Few see signs of letup Few expect the euphoria after companies raise to wear off soon. A1 more than $167 billion Detenteisending in the global fight over tech taxes, despite pandemic with Franceresuming collec- tion of itsdigital-services tax BY MAUREEN FARRELL and the U.S. poised to retali- atewith tariffs.Other coun- Defying expectations,inves- tries areset to join the fray. A1 S tors piled intoinitial public of- China finished 2020 PRES feringsatarecordrateiN with a 10th consecutive TED 2020, and few expect the eu- month of expansion in its CIA phoria to wear off soon. manufacturing sector. A7 SO Companies raised $167.2 AS TheEUand China agreed TENSIONS HIGH: People fled after an explosion Wednesday at the airport in Aden, Yemen, moments after members of the billion through 454 offerings in principle on an invest- country’s newly sworn-in cabinet arrived. At least 22 people were killed, but all the members of the cabinet were safe. -

03.031 Socc04 Final 2(R)
STATEOF CENTER CITY 2008 Prepared by Center City District & Central Philadelphia Development Corporation May 2008 STATEOF CENTER CITY 2008 Center City District & Central Philadelphia Development Corporation 660 Chestnut Street Philadelphia PA, 19106 215.440.5500 www.CenterCityPhila.org TABLEOFCONTENTSCONTENTS INTRODUCTION 1 OFFICE MARKET 2 HEALTHCARE & EDUCATION 6 HOSPITALITY & TOURISM 10 ARTS & CULTURE 14 RETAIL MARKET 18 EMPLOYMENT 22 TRANSPORTATION & ACCESS 28 RESIDENTIAL MARKET 32 PARKS & RECREATION 36 CENTER CITY DISTRICT PERFORMANCE 38 CENTER CITY DEVELOPMENTS 44 ACKNOWLEDGEMENTS 48 Center City District & Central Philadelphia Development Corporation www.CenterCityPhila.org INTRODUCTION CENTER CITY PHILADELPHIA 2007 was a year of positive change in Center City. Even with the new Comcast Tower topping out at 975 feet, overall office occupancy still climbed to 89%, as the expansion of existing firms and several new arrivals downtown pushed Class A rents up 14%. For the first time in 15 years, Center City increased its share of regional office space. Healthcare and educational institutions continued to attract students, patients and research dollars to downtown, while elementary schools experienced strong demand from the growing number of families in Center City with children. The Pennsylvania Convention Center expansion commenced and plans advanced for new hotels, as occupancy and room rates steadily climbed. On Independence Mall, the National Museum of American Jewish History started construction, while the Barnes Foundation retained designers for a new home on the Benjamin Franklin Parkway. Housing prices remained strong, rents steadily climbed and rental vacancy rates dropped to 4.6%, as new residents continued to flock to Center City. While the average condo sold for $428,596, 115 units sold in 2007 for more than $1 million, double the number in 2006. -

NACD Public Company Full Board Members
NACD Public Company Full Board Members: Rank | Company Rank | Company Rank | Company Rank | Company A.O. Smith Corp. Analog Devices Bridge Housing Corporation Clearwire Corp. AAA Club Partners Ansys, Inc. Briggs & Stratton Corp. Cliffs Natural Resources Inc. AARP Foundation Apogee Enterprises, Inc. Brightpoint, Inc. Cloud Peak Energy Inc. Aastrom Biosciences, Inc. Apollo Group, Inc. Bristow Group Inc. CME Group Acadia Realty Trust Applied Industrial Technologies, Broadwind Energy CoBiz, Inc. ACI Worldwide, Inc. Inc. Brookdale Senior Living Inc. Coherent, Inc. Acme Packet, Inc. Approach Resources, Inc. Bryn Mawr Bank Corporation Coinstar, Inc. Active Power, Inc. ArcelorMittal Buckeye Partners L.P. Colgate-Palmolive Co. ADA-ES, Inc. Arch Coal, Inc. Buffalo Wild Wings, Inc. Collective Brands, Inc. Adobe Systems, Inc. Archer Daniels Midland Co. Bunge Limited Commercial Metals Co. Advance Auto Parts ARIAD Pharmaceuticals, Inc. CA Holding Community Health Systems Advanced Energy Industries, Inc. Arkansas Blue Cross Blue Shield CACI International, Inc. Compass Minerals Aerosonic Corp. Arlington Asset Investment Corp. Cal Dive International, Inc. Comverse Technology, Inc. Aetna, Inc. Arthur J. Gallagher & Co. Calamos Asset Management, Inc. Conmed Corp. AFC Enterprises, Inc. Asbury Automobile Cameco Corp. Connecticut Water Service, Inc. AG Mortgage Investment Trust Inc. Aspen Technology, Inc. Cameron ConocoPhillips Agilent Technologies Associated Banc-Corp.5 Campbell Soup Co. CONSOL Energy Inc. Air Methods Corp. Assurant, Inc. Capella Education Co. Consolidated Edison Co. Alacer Gold Corp. Assured Guaranty Ltd. Capital One Financial Corp. Consolidated Graphics, Inc. Alaska Air Group, Inc. ATMI Capstead Mortgage Corp. Consolidated Water Co., Ltd. Alaska Communication Systems Atwood Oceanics, Inc. Cardtronics, Inc. Continental Resources, Inc. Group, Inc. Auxilium Pharmaceuticals Inc. -

Strategies for Talent Management
STRATEGIES FOR TALENT MANAGEMENT: Greater Philadelphia Companies in Action August 2008 Prepared by the CEO Council for Growth in partnership with the Council for Adult and Experiential Learning Dear Regional Business Leader: On behalf of Mark S. Schweiker, Chairman of the CEO Council for Growth (CEO Council) – a tri-state, eleven county business leadership group – we are excited to present the following report, entitled “Strategies for Talent Management: Greater Philadelphia Companies in Action.” The research provides insights into some of the successful ways organizations are developing their talent and how others can strengthen their current talent management efforts. It focuses on talent management strategies as well as one specific tactic – tuition assistance programs. Human capital is clearly one of the critical issues that impacts the Greater Philadelphia region’s ability to grow and prosper. The CEO Council is committed to ensuring a steady and talented supply of quality workers for this region. While this report is focused on that later part of the talent continuum, we understand that quality early childhood and K-12 education is a key part of the foundation for our region’s success. In June of 2006, the CEO Council’s Human Capital Working Group released the final report of its Human Capital Needs Assessment. In it you indicated that the following were your two biggest challenges: 1. Hiring highly skilled and experienced mid-level professionals/managers; and 2. Recruiting diverse employees. As a natural progression from the survey, the Human Capital Working Group commissioned the Council for Adult and Experiential Learning (CAEL) in partnership with CEO Council staff to complete the research contained in this report. -

Corporations with Matching Gift Programs
Corporations with Matching Gift Programs You can double your donation by asking your employer if they have a matching gift program. We’ve compiled this list of companies that match from outside sources, so we can’t guarantee its accuracy or completeness. Ask your employer if your donation is eligible! Abbot Laboratories Bechtel Group, Inc. Accenture Becton Dickinson ADVANTA Behring Diagnostics, Inc. Aetna, Inc. Beneficial Management Corporation Air Products & Chemicals, Inc. BOC Gases Allendale Mutual Insurance Company The Boeing Company Alliance Capital Bristol-Meyers Squibb Company Management Corporation, LP Brown & Williamson Tobacco Corporation AlliedSignal, Inc. Allmerica Financial Campbell Soup Company AMBAC, Inc. Cape Savings Bank Amerada Hess Corporation Cargill, Inc. American Cyanamid Company Carolina Power & Light Company American Express Company Carter-Wallace, Inc. American Home Products Corporation CBS, Inc. American Standard, Inc. Certain Teed Corporation Amgen, Inc. CGU Ammirati Puris Lintas Chase Manhattan Foundation The ARA Group, Inc. Chrysler Corporation Aramark Chubb & Son, Inc. ARCO Chemical Company Ciba Corning Diagnostics Corp. Arthur Anderson LLP Ciba-Geigy Corporation Aon Corporation Ciba Specialty Chemicals Applied Technology CIGNA Corporation Arthur Young CITGO Petroleum Corporation Atlantic City Electric Company Liz Claiborne Atlantic Electric CMS Energy AT&T CNA Insurance Company Automatic Data Processing, Inc. Coca Cola Aventis Behring L.L.C. Colgate-Palmolive Company Aventis Pharmaceuticals Products, Inc. Computer Associates International, Inc. Avery Dennison Corporation ConAgra, Inc. Avon Products, Inc. Conectiv Congoleum Corporation Ball Corporation Consumers Water Company Bankers Trust Company The Continental Corporation Bank of America Corning Incorporated Bank of Montreal Comair, Inc. The Bank of New York Crompton & Knowles Corporation Bankers Trust Company CSX, Inc. -

Atif Ghauri, Cissp, Ccsa, Cism Principal
ATIF GHAURI, CISSP, CCSA, CISM PRINCIPAL Atif is a renowned cybersecurity expert with 20 years of experience in management consulting, technical and sales operations, product management, and business development. He is an innovator in cybersecurity, receiving a patent in security analytics on embedded consumer devices monitoring user activity anomalies. Prior to joining Mazars USA, Atif led a three year $250 million dollar geographical expansion initiative as Chief Technology Officer of a global cybersecurity firm. He went on to head sales and strategy for the company’s most profitable and fastest growing business as Senior Vice President of Managed Security Services. Before that, Atif held leadership roles for both business and technology organizations at Comcast. He was head of Business Operations for Xfinity Home. He also served as Chief Product Security Officer for the technology engineering group, where he directed all security work streams to launch next generation X1 Platform, including invention and deployment of his patented fraud detection technology operational on millions of subscriber devices. Before arriving at Comcast, Atif was Director of Security at Unisys, where he launched a global security practice focused in Application Security. He started his career as a Managing Consultant at IBM Global Services implementing security for Fortune 100 companies. Atif received the IBM Professional Excellence Award for service delivery excellence, awarded to only 11 professionals worldwide. Atif serves as an Adjunct Professor in Cybersecurity at Drexel University. He received a Master’s in Technology Management from the Wharton School at University of Pennsylvania and a Bachelor's from Schreyer Honors College at Penn State University. -
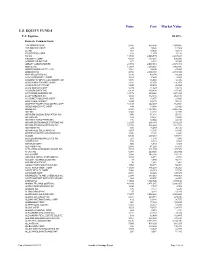
Usef-I Q2 2021
Units Cost Market Value U.S. EQUITY FUND-I U.S. Equities 88.35% Domestic Common Stocks 10X GENOMICS INC 5,585 868,056 1,093,655 1ST SOURCE CORP 249 9,322 11,569 2U INC 301 10,632 12,543 3D SYSTEMS CORP 128 1,079 5,116 3M CO 11,516 2,040,779 2,287,423 A O SMITH CORP 6,897 407,294 496,998 AARON'S CO INC/THE 472 8,022 15,099 ABBOTT LABORATORIES 24,799 2,007,619 2,874,948 ABBVIE INC 17,604 1,588,697 1,982,915 ABERCROMBIE & FITCH CO 1,021 19,690 47,405 ABIOMED INC 9,158 2,800,138 2,858,303 ABM INDUSTRIES INC 1,126 40,076 49,938 ACACIA RESEARCH CORP 1,223 7,498 8,267 ACADEMY SPORTS & OUTDOORS INC 1,036 35,982 42,725 ACADIA HEALTHCARE CO INC 2,181 67,154 136,858 ACADIA REALTY TRUST 1,390 24,572 30,524 ACCO BRANDS CORP 1,709 11,329 14,749 ACI WORLDWIDE INC 6,138 169,838 227,965 ACTIVISION BLIZZARD INC 13,175 839,968 1,257,422 ACUITY BRANDS INC 1,404 132,535 262,590 ACUSHNET HOLDINGS CORP 466 15,677 23,020 ADAPTHEALTH CORP 1,320 39,475 36,181 ADAPTIVE BIOTECHNOLOGIES CORP 18,687 644,897 763,551 ADDUS HOMECARE CORP 148 13,034 12,912 ADOBE INC 5,047 1,447,216 2,955,725 ADT INC 3,049 22,268 32,899 ADTALEM GLOBAL EDUCATION INC 846 31,161 30,151 ADTRAN INC 892 10,257 18,420 ADVANCE AUTO PARTS INC 216 34,544 44,310 ADVANCED DRAINAGE SYSTEMS INC 12,295 298,154 1,433,228 ADVANCED MICRO DEVICES INC 14,280 895,664 1,341,320 ADVANSIX INC 674 15,459 20,126 ADVANTAGE SOLUTIONS INC 1,279 14,497 13,800 ADVERUM BIOTECHNOLOGIES INC 1,840 7,030 6,440 AECOM 5,145 227,453 325,781 AEGLEA BIOTHERAPEUTICS INC 287 1,770 1,998 AEMETIS INC 498 6,023 5,563 AERSALE CORP -

Women on Boards the Forum of Executive Women Executive Suites Initiative
Women on Boards The Forum of Executive Women Executive Suites Initiative Improving corporate governance. Increasing shareholder value. The time is NOW. Citizens Bank of Pennsylvania is proud to support The Forum of Executive Women in a variety of ways, including underwriting The Forum's Women on Boards report for 2004. At Citizens Bank, where women comprise 50 percent of our Leadership Team, we believe that diversity, in all of its many manifestations, results in different perspectives, new ideas, and stronger outcomes. In embracing its mission to support colleagues, customers, and community, Citizens Bank applauds The Forum for its leadership in advocating for the advancement of women in our region. About The Forum of Executive Women Founded in 1977, The Forum of Executive Women is a membership organization of 300 women of influence in Greater Philadelphia. Its members hold top positions in every major segment of the community — from finance to manufacturing, from government to healthcare, from not-for-profits to communications, from the professions to technology. As the region's premier women's organization, The Forum fulfills its mission — to advance women leaders in Greater Philadelphia — by supporting women in leadership roles, promoting parity in the corporate world, mentoring young women, and providing a forum for the exchange of views, contacts, and information. The Forum's Executive Suites Initiative advocates and facilitates the increased representation of women on boards and in top management positions of major public companies in our region. Irene H. Hannan, President Sharon Hardy, Executive Director A Four-Year Snapshot of Women On Boards % of women on boards 12% 10% 8% 6% 4% Executive 2% Summary 0% 2000 2001 2002 2003 Ensuring the Research is Current and Comparable Companies in the technology/telecommunications category have the fewest women represented in all levels of Revenues change from year to year. -

Memo of Law ISO Motion for an Award Of
11 MAR 2021 06:19 pm E. MEENAN GOLDMAN SCARLATO & PENNY, P.C. LABATON SUCHAROW LLP Mark S. Goldman (PA Atty. No. 48049) Jonathan Gardner Eight Tower Bridge, Suite 1025 Alfred L. Fatale III 161 Washington Street Lisa Strejlau Conshohocken, PA 19428 140 Broadway Tel: (484) 342-0700 New York, NY 10005 [email protected] Tel: (212) 907-0700 [email protected] Liaison Counsel for Lead Plaintiffs and the [email protected] Settlement Class [email protected] Lead Counsel for Lead Plaintiffs and the Settlement Class IN THE COURT OF COMMON PLEAS OF PHILADELPHIA COUNTY, PENNSYLVANIA – CIVIL TRIAL DIVISION IN RE LIVENT CORPORATION CIVIL ACTION SECURITIES LITIGATION Consolidated Case No. 190501229 MEMORANDUM OF LAW IN SUPPORT OF LEAD COUNSEL’S MOTION FOR AN AWARD OF ATTORNEYS’ FEES AND PAYMENT OF EXPENSES Case ID: 190501229 Control No.: 21031165 TABLE OF CONTENTS TABLE OF AUTHORITIES .......................................................................................................... ii PRELIMINARY STATEMENT AND HISTORY OF THE CASE .............................................. 1 QUESTIONS PRESENTED ........................................................................................................... 3 LEGAL ARGUMENT .................................................................................................................... 4 I. PLAINTIFFS’ COUNSEL ARE ENTITLED TO AN AWARD OF ATTORNEYS’ FEES FROM THE COMMON FUND CREATED BY THEIR EFFORTS .......................................................................................................................... -

It Is Undisputed That ARAMARK, Inc. (“ARAMARK”) Acquired Servicemaster and Assumed Its Contractual Obligations with Greyhound
Case 2:06-cv-03049-LDD Document 39 Filed 01/16/09 Page 1 of 7 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF PENNSYLVANIA SELWYN NIEVES : CIVIL ACTION : v. : NO. 06-3049 : GREYHOUND LINES, INC., et al. : MEMORANDUM AND ORDER Kauffman, J. January 16, 2009 Now before the Court is the Motion for Summary Judgment (the “Motion”) of Defendant Servicemaster, TBS Division (“Servicemaster”). For the reasons discussed below, the Motion will be granted. I. BACKGROUND This action arises from a workplace injury sustained by Plaintiff Selwyn M. Nieves (“Plaintiff”) on July 4, 2004. As alleged in the Complaint, Defendant/Third-Party Plaintiff Mount Corporation (“Mount”) was, at all times relevant to this action, the owner of a maintenance facility (the “Greyhound Maintenance Center”) located at 710 N. Delaware Avenue in Philadelphia. Compl. ¶ 3. Pursuant to a written service agreement (the “Agreement”) with Defendant/Third-Party Plaintiff Greyhound Lines, Inc. (“Greyhound”), Servicemaster was responsible for maintaining the premises of the Greyhound Maintenance Center. Id. ¶ 4.1 1 It is undisputed that ARAMARK, Inc. (“ARAMARK”) acquired Servicemaster and assumed its contractual obligations with Greyhound. However, Plaintiff contends that ARAMARK did not assume Servicemaster’s contractual obligations until after the accident at issue in this case. -1- Case 2:06-cv-03049-LDD Document 39 Filed 01/16/09 Page 2 of 7 Plaintiff alleges that on July 4, 2004, “there existed a dangerous condition on certain concrete steps situated in the Greyhound Maintenance Center, to wit, a slippery substance which was allowed and permitted . to be on the steps with no warnings, barricades or similar precautions.” Id.