CIS Apple Ios 12 Benchmark
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Learning with Ipad Preparing Students for Careers
Learning with iPad Preparing students for careers Mobile technology is changing the way we learn and work. It’s driving transformation in businesses of all sizes and across all industries. This digital transformation is redefining what career readiness means and driving a shift in the skills students need to be successful. Learning with iPad prepares them for a world that’s increasingly mobile, global, and connected. Learning with iPad: Preparing students for careers | 1 Get students career ready with iPad We live in an age of unprecedented information, access, and connection. Technology has changed the way we communicate, engage, and live. Companies are leveraging technology to create new models for how they work, and they’re defining new jobs that didn’t exist 10 years ago. Employers are finding that soft skills like problem-solving, creativity, collaboration, communication, and adapting to change are more important than ever. iPad can help engage students as they build these skills and prepare for high-demand careers and industries. With its built-in features, access to a breadth of resources, and free Apple-designed learning resources, iPad can help students collaborate, brainstorm, and use design thinking to create solutions to real-world problems. And with advanced technologies designed to make augmented reality experiences more powerful and engaging, iPad creates an experience that’s simply not possible on other platforms. This guide can show you how iPad helps empower students to become better communicators, skilled collaborators, -

Apple Ipad Pro Wi-Fi Cellular 10.5" 512GB Guld Apple Ios 12 Beskrivelse Apple Ipad Pro 10.5" Wifi + 4G 512GB - Gold
Apple iPad Pro Wi-Fi Cellular 10.5" 512GB Guld Apple iOS 12 Beskrivelse Apple iPad Pro 10.5" WiFi + 4G 512GB - Gold Features Den mest avancerede skærm på hele kloden iPad har altid været den ultimative Multi-Touch-oplevelse. Og den redesignede Retina-skærm på iPad Pro sætter en helt ny standard. Ikke alene har den højere lysstyrke og mindre genskin - den har også langt hurtigere reaktionstid end nogen forgænger. Uanset om du scroller løs i Safari eller spiller tunge 3D-spil, går alt så utroligt jævnt og hurtigt, at du helt sikkert bliver revet med. Stærkere end de fleste computere A10X Fusion-chippen med 64-bit-arkitektur og seks kerner giver dig masser af power mellem hænderne. Så meget at du kan redigere 4K-video på farten. Rendere en detaljeret 3D-model. Eller oprette og markere i komplekse dokumenter og præsentationer. Helt nemt - og på en enhed, der stadig har batteritid til en hel dag. Yderst spidskompetent iPad Pro-skærmens opdateringsfrekvens er blevet forbedret, så Apple Pencil gengiver dine strøg endnu mere præcist og naturligt. Apple Pencil er det eneste digitale skriveredskab, der giver dig mulighed for at skrive, lave markeringer og tegne med så præcist et pixel-niveau. Et kæmpe spring for iPad iOS 11 får alt på din iPad til at virke mere levende end nogensinde før. De nye funktioner og muligheder gør, at du kan endnu mere, både hurtigere og nemmere, så du får en endnu mere personlig iPad-oplevelse med masser af power. Brug den til lige præcis det, du vil. For det kan du nu. -
Download Ios 12.1 Beta Profile Download Ios 12.1 Beta Profile
download ios 12.1 beta profile Download ios 12.1 beta profile. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 66ab045d4d70fac0 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download ios 12.1 beta profile. Apple has released the first macOS Monterey public beta, giving more people the chance to install it and see what everyone will be using when the software is made available later this year. Those who are on the public beta program can now download macOS Monterey via the Software Update portion of the System Preferences app, assuming they have the correct beta profile installed. Apple gives public beta testers the chance to try macOS, iOS, iPadOS, tvOS, and watchOS betas out ahead of public release, all of which can be installed via the Apple Beta Software Program website. Help make the next releases of iOS, iPadOS, macOS, tvOS and watchOS our best yet. As a member of the Apple Beta Software Program, you can take part in shaping Apple software by test-driving pre-release versions and letting us know what you think. -

Download Ios 12 Eta Download Ios 12 Eta
download ios 12 eta Download ios 12 eta. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67d363cfac2d15fe • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download iOS 12 Beta 1 IPSW for iPhone and iPad. iOS 12 beta 1 IPSW firmware can now be downloaded for installation on iPhone 5s, SE, 6, 6s, Plus, 7, 8, X, and iPad Mini 2 and above, as well as iPod Touch 6G. Introduced at WWDC 2018, it’s available for those on the Apple Developer Program. iOS 12 is the latest update from Apple for iDevices and boasts a number of new features. Its public release is slated for fall, 2018. You can download iOS 12 beta 1 ISPW firmware file for your device right now. iOS 12 Beta 1 IPSW Download Is Now Available for iPhone X, 8, 7+, 7, 6s, 6, SE, 5s, iPod & iPad. Interested in trying out this early beta of iOS 12? Well then, follow the steps we’ve listed below. -

Apple Ipad User Guide Ios 12.Pdf
Apple Ipad User Guide Ios 12 Browse Manuals by Product. Previous iPad User Guide for iPadOS · Web / Apple Books. Sep 24, 2019. iPhone User Guide for iOS 13 · Web / Apple Books. View the iPad User Guide in Safari, add a bookmark or save it as a shortcut on the Home screen for easy access. Or download it from Apple Books and read it. Browse Manuals by Product. Previous. Apple Watch. iPhone. iPad. Mac notebooks. Mac desktops. Apple TV. HomePod. iPod. Peripherals. Professional. Apple iPad Manual / User Guide This is the official Apple iPad User Guide in iOS 12 or update your iPad with iOS 12 learn a complete guide iOS 12 user guide. Apple Ipad User Guide Ios 12 Click Here --> iPad User Guide for iOS 12. iPad User Guide iOS 12.3. Apple Inc. What We Like. The web version is interactive. In-depth guides. Includes. in PDF version to your device (You can download iOS 12 manual for iPhone, iOS 12 manual for iPod, iOS 12 Manual for iPad) you. Amazon.com: The iPad User's Guide to iOS 12: Tips, Tricks & Tutorials for Using iOS 12 on the iPad (iOS User Series) (Volume 2) (9781726244497): Berner. iPad. User Guide. For iOS 8.1 Software (February 2015) 12 SIM card tray in iCloud, and access them from your iPad, iPhone, iPod touch, Mac, or PC. iPad User Guide for iOS 12 - Download iOS 12 or update your iPad with iOS 12 learn a complete guide iOS 12 user guide on iPad X / iPad X Pro and get iOS 12. -

Ipad Pro 10.5" Teardown Guide ID: 92534 - Draft: 2021-05-12
iPad Pro 10.5" Teardown Guide ID: 92534 - Draft: 2021-05-12 iPad Pro 10.5" Teardown Teardown of the iPad Pro 10.5" performed on June 13, 2017. Written By: Adam O'Camb This document was generated on 2021-05-15 05:56:18 PM (MST). © iFixit — CC BY-NC-SA www.iFixit.com Page 1 of 18 iPad Pro 10.5" Teardown Guide ID: 92534 - Draft: 2021-05-12 INTRODUCTION Apple is at it again, trying to win over the workforce with yet another iPad Pro (this time with a brand- new 10.5" screen size). We expect to see Apple put points on the board with some silicon slam dunks, but what else puts this Pro in the big leagues? Is this new iPad a knock out of the park or is it just KO'd? Only one way to know! Let's play ball tear it down! Care to keep up? We do move fast, but we love our teammates. Stay in the race by following us on Facebook, Instagram, or Twitter for the latest teardown news. [video: https://www.youtube.com/watch?v=DepdFt8ZxNc] TOOLS: iOpener (1) Suction Handle (1) iFixit Opening Picks set of 6 (1) Phillips #00 Screwdriver (1) Halberd Spudger (1) Plastic Cards (1) Tweezers (1) iPad Battery Isolation Pick (1) This document was generated on 2021-05-15 05:56:18 PM (MST). © iFixit — CC BY-NC-SA www.iFixit.com Page 2 of 18 iPad Pro 10.5" Teardown Guide ID: 92534 - Draft: 2021-05-12 Step 1 — iPad Pro 10.5" Teardown You can relax now—this iPad is a professional. -

Apple Ipad and Iphone Mobile Devices with Ios 12
Apple Inc. Apple iPad and iPhone Mobile Devices with iOS 12 Security Target PP_MD_V3.1 with EP_MDM_AGENT_V3.0, PP_WLAN_CLI_EP_V1.0, MOD_VPN_CLI_V2.1. Version 1.6 2019-03-12 VID: 10937 Prepared for: Prepared by: Apple Inc. atsec information security Corp. One Apple Park Way 9130 Jollyville Road, Suite 260 MS 927-1CPS Austin, TX 78759 Cupertino, CA 95014 www.atsec.com www.apple.com © 2019 Apple Inc. This document may be reproduced and distributed only in its original entirety without revision VID: 10937 Table of Contents Revision History ....................................................................................................................... 9 1 Security Target Introduction .......................................................................................... 11 1.1 Security Target Reference ............................................................................................... 11 1.2 TOE Reference .................................................................................................................. 11 1.3 TOE Overview .................................................................................................................... 11 1.4 TOE Description ................................................................................................................. 12 1.4.1 General information .............................................................................................. 12 1.4.2 Obtaining the mobile devices............................................................................. -

Mobile Device Management Protocol Reference
Mobile Device Management Protocol Reference Developer Contents 1 About Mobile Device Management 7 At a Glance ................................................ 8 The MDM Check-in Protocol Lets a Device Contact Your Server ................... 8 The MDM Protocol Sends Management Commands to the Device .................. 8 The Way You Design Your Payload Matters .............................. 8 The Device Enrollment Program Lets You Configure Devices with the Setup Assistant ........ 8 The Volume Purchase Program Lets You Assign App Licenses to Users and Devices ......... 9 Apple Push Notification Certificates Can Be Generated Through the Apple Push Certificates Portal .. 9 See Also ................................................. 9 2 MDM Check-in Protocol 10 Structure of a Check-in Request ...................................... 10 Supported Check-in Commands ..................................... 11 Authenticate Message ........................................ 11 TokenUpdate Message ........................................ 12 CheckOut .............................................. 13 3 Mobile Device Management Protocol 14 Structure of MDM Payloads ........................................ 16 Structure of MDM Messages ....................................... 18 MDM Command Payloads ......................................... 20 MDM Result Payloads ........................................... 20 MDM Protocol Extensions ......................................... 21 macOS Extensions .......................................... 21 Network User Authentication -

Information Display Magazine May/June 2018 Vol 34 No 3 2018
THE FUTURE LOOKS RADIANT ENSURING QUALITY FOR THE NEXT GENERATION OF DISPLAY DEVICES Radiant light & color measurement solutions replicate human visual perception to evaluate how users will experience new technology including OLED and microLED displays. Visit us at Booth #729 Display Week 2018 May 22-24 | Los Angeles, CA ID TOC Issue3 p1_Layout 1 4/25/2018 7:12 AM Page 1 Information SOCIETY FOR INFORMATION DISPLAY SID MAY/JUNE 2018 2018 DISPLAY VOL. 34, NO. 3 ON THE COVER: The winners of this year’s Display Industry Awards are, clockwise from upper right: Sharp’s 70-in. 8K LCD TV; LG Displays’ UHD Crystal Sound OLED; contents Apple’s iPhone X; Apple’s iPad Pro Display; Synaptics’ Clear ID Optical In-Display 2 Editorial: Return to Southern California Fingerprint Sensor; Kolon’s Colorless Polyimide; n By Stephen Atwood and Continental Automotive Systems’ 3D Touch Surface Display. 4 President’s Corner: What’s Next (in Display Technology)? 6 Industry News n By Jenny Donelan 8 2018 Display Industry Awards: This Year’s Winners Are a Fun and Compelling Group Each year, SID’s Display Industry Awards Committee selects products that have advanced the state of the art of display technology in the categories of Display of the Year, Display Component of the Year, and Display Application of the Year. n Compiled by Jenny Donelan 12 Display History: David Sarnoff, Display Industry Visionary His many contributions to the display industry are closely linked to the pioneering of Cover Design: Jodi Buckley flat-panel displays and the invention and eventual success of the LCD. -
Device Type Device Name Level 1 DRM Apple Phone & Tablet Iphone
Compatible Device List Device Type: Apple: Phone & tablet Device Name: iPhone (iOS 12+): • SE (gen 1-2) • 6S, 6S+ • 7, 7+ • 8, 8+ • XR, X, XS, XS Max • 11 Pro, 11 Pro Max iPad (iOS 12 - iPadOS 13+): • iPad Air 2, iPad mini 4, iPad Gen 5 • iPad Pro 9.7",10.5", 11" (gen 1-2), 12.9" (gen 1-2) Device Type: Android, Phone & tablet Device Name: VARIOUS (Android 8+) Google: • Pixel 3, 3XL, 3A, 3AXL, 4, 4XL • Pixel Slate Samsung: • Galaxy S9, S9+, S10E, S10, S10+ • Note 9, 10, 10+ • Fold • Tab 5SE, S6 OnePlus: • 6T, 7T, 7 Pro, 8, 8 Pro LG: • K30, K40, G8, G8X, Q7 Plus Device Type: TV, Streaming stick Device Name Amazon Fire TV (Fire OS 5+) • Fire TV Stick Gen 2 (2016), Basic Edition (2017), Fire TV Stick 4K (2018) Roku (OS 8+) • 3600X, 3700X, 3710X, 3800X, 3810X, 3900X, 3910X Device Type: TV, Retail Streaming set-top-box Device Name: Apple (OS 12+) • Apple TV (A1625), Apple TV 4K (A1842) • Planned to support in 2020 - Apple TV (T1125) Android (OS 8+) • nVidia • Shield TV (2017, 2019) • Shield TV Pro (2017, 2019) • Xiaomi • Mi Box, Mi Box S 4K HDR Amazon Fire TV (Fire OS 5+) • Fire TV Gen 3, pendant (2017) • Fire TV Cube (Gen 1, Gen 2) PLANNED TO SUPPORT IN 2020 • Jetstream AGT418 STB Apple 1 Device Type: TV, Operator Tier Streaming set-top-box Device Name: Android (OS 8+) • KAON KSTB2020 • AMINO KAMAI 7BA • ARRIS VIP6102W PLANNED TO SUPPORT IN 2020: • AMINO AMIGO 7X V2 • SDMC DV8219 • EVOLUTION DIGITAL EVO PRO Device Type: TV, Accessories Device Name: Amazon Fire TV • Amazon Fire TV Remote: 165 Device Type: TV, Smart Soundbar Device Name: SUPPORTED -

Allow Use of Camera Allow Facetime (Supervised Only)
Allow use of camera Allow FaceTime (supervised only) Allow screenshots and screen recording Allow screen observation by Classroom app (Apple Education Support enabled, supervised only) Allow modifying the AirPlay and View Screen permission for managed classes (supervised only) Allow AirDrop (supervised only) Allow iMessage (supervised only) Allow voice dialing while device is locked Allow Siri Allow Siri Suggestions Allow proximity setup to new device (iOS 11 or later, supervised only) Allow installing apps using Apple Configurator and iTunes (iOS 9 or later) /Allow installing apps using App Store (iOS 5– iOS 8 only) Allow installing apps using App Store (iOS 9 or later, supervised only) Allow removing apps (supervised only) Allow removing system apps (iOS 11 or later, supervised only) Allow Apple Music (supervised only) Allow Radio (supervised only) Require iTunes Store password for all purchases Allow iCloud backup Allow iCloud documents & data (supervised only) Allow iCloud keychain Allow managed apps to store data in iCloud Allow backup of enterprise books Allow notes and highlights sync for enterprise books Allow iCloud Photo Sharing Allow iCloud Photo Library Allow My Photo Stream (disallowing can cause data loss) Allow automatic sync while roaming Force encrypted backups Force limited ad tracking Allow Erase All Content and Settings (supervised only) Allow users to accept untrusted TLS certificates Allow automatic updates to certificate trust settings Allow trusting new enterprise app authors Allow installing configuration profiles -
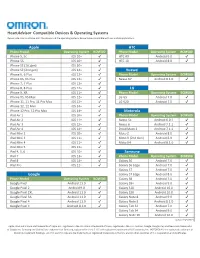
OMRON App Compatibility Matrix 172021.Xlsx
HeartAdvisor Compatible Devices & Operating Systems Please note: You must have both the device and the operating systems below to be compatible with our mobile applications. Apple HTC Phone Model Operating System BCM500 Phone Model Operating System BCM500 iPhone 5, 5c iOS 10+ ✔ HTC A9 Android 6.0 ✔ iPhone 5S iOS 10+ ✔ HTC 10 Android 8.0 ✔ iPhone SE (1st gen) iOS 10+ ✔ iPhone SE (2nd gen) iOS 14+ ✔ Huawei iPhone 6, 6 Plus iOS 12+ ✔ Phone Model Operating System BCM500 iPhone 6S, 6S Plus iOS 12+ ✔ Nexus 6P Android 8.1.0 ✔ iPhone 7, 7 Plus iOS 12+ ✔ iPhone 8, 8 Plus iOS 12+ ✔ LG iPhone X, XR iOS 11+ ✔ Phone Model Operating System BCM500 iPhone XS, XS Max iOS 12+ ✔ LG G5 Android 7.0 ✔ iPhone 11, 11 Pro, 11 Pro Max iOS 13+ ✔ LG V20 Android 7.0 ✔ iPhone 12, 12 Mini iOS 14+ ✔ iPhone 12 Pro, 12 Pro Max iOS 14+ ✔ Motorola iPad Air 1 iOS 10+ ✔ Phone Model Operating System BCM500 iPad Air 2 iOS 11+ ✔ Nexus 5x Android 6.0.1 ✔ iPad Air 3 iOS 12+ ✔ Nexus 6 Android 7.1.1 ✔ iPad Air 4 iOS 14+ ✔ Droid Maxx 2 Android 7.1.1 ✔ iPad Mini 2 iOS 10+ ✔ Moto Z Android 8.0 ✔ iPad Mini 3 iOS 11+ ✔ Moto X (2nd Gen) Android 6.0 ✔ iPad Mini 4 iOS 11+ ✔ Moto X4 Android 8.1.0 ✔ iPad Mini 5 iOS 12+ ✔ iPad 4, 5, 6 iOS 10+ ✔ Samsung iPad 7 iOS 13+ ✔ Phone Model Operating System BCM500 iPad 8 iOS 14+ ✔ Galaxy S6 Android 7.0 ✔ iPad Pro iOS 11+ ✔ Galaxy S6 Edge Android 7.0 ✔ Galaxy S7 Android 7.0 ✔ Google Galaxy S7 Edge Android 8.0 ✔ Phone Model Operating System BCM500 Galaxy S8 Android 7.0 ✔ Google Pixel Android 11.0 ✔ Galaxy S9+ Android 9.0 ✔ Google Pixel 2 Android 9.0 ✔ Galaxy S10 Android 10.0 ✔ Google Pixel 2XL Android 11.0 ✔ Galaxy S20 Android 10.0 ✔ Google Pixel 3A Android 11.0 ✔ Galaxy Note 8 Android 9.0 ✔ Google Pixel 4 Android 11.0 ✔ Galaxy Note 9 Android 8.1.0 ✔ Google Pixel C Android 8.1.0 ✔ Galaxy Tab S2 Android 7.0 ✔ Galaxy Tab S4 Android 9.0 ✔ Galaxy Note 10 Android 10.0 ✔ updated 3/5/2021 Apple, iPad and iPhone are trademarks of Apple Inc., registered in the U.S.