Software Defined Radio Localization Using 802.11-Style Communications Brian Shaw Worcester Polytechnic Institute
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Linux Gamers' HOWTO
The Linux Gamers’ HOWTO Peter Jay Salzman Frédéric Delanoy Copyright © 2001, 2002 Peter Jay Salzman Copyright © 2003, 2004 Peter Jay SalzmanFrédéric Delanoy 2004-11-13 v.1.0.6 Abstract The same questions get asked repeatedly on Linux related mailing lists and news groups. Many of them arise because people don’t know as much as they should about how things "work" on Linux, at least, as far as games go. Gaming can be a tough pursuit; it requires knowledge from an incredibly vast range of topics from compilers to libraries to system administration to networking to XFree86 administration ... you get the picture. Every aspect of your computer plays a role in gaming. It’s a demanding topic, but this fact is shadowed by the primary goal of gaming: to have fun and blow off some steam. This document is a stepping stone to get the most common problems resolved and to give people the knowledge to begin thinking intelligently about what is going on with their games. Just as with anything else on Linux, you need to know a little more about what’s going on behind the scenes with your system to be able to keep your games healthy or to diagnose and fix them when they’re not. 1. Administra If you have ideas, corrections or questions relating to this HOWTO, please email me. By receiving feedback on this howto (even if I don’t have the time to answer), you make me feel like I’m doing something useful. In turn, it motivates me to write more and add to this document. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -
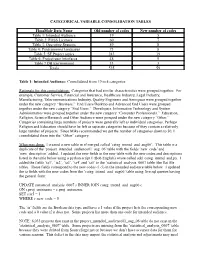
Categorical Variable Consolidation Tables
CATEGORICAL VARIABLE CONSOLIDATION TABLES FlossMole Data Name Old number of codes New number of codes Table 1: Intended Audience 19 5 Table 2: FOSS Licenses 60 7 Table 3: Operating Systems 59 8 Table 4: Programming languages 73 8 Table 5: SF Project topics 243 19 Table 6: Project user interfaces 48 9 Table 7 DB Environment 33 3 Totals 535 59 Table 1: Intended Audience: Consolidated from 19 to 4 categories Rationale for this consolidation: Categories that had similar characteristics were grouped together. For example, Customer Service, Financial and Insurance, Healthcare Industry, Legal Industry, Manufacturing, Telecommunications Industry, Quality Engineers and Aerospace were grouped together under the new category “Business.” End Users/Desktop and Advanced End Users were grouped together under the new category “End Users.” Developers, Information Technology and System Administrators were grouped together under the new category “Computer Professionals.” Education, Religion, Science/Research and Other Audience were grouped under the new category “Other.” Categories containing large numbers of projects were generally left as individual categories. Perhaps Religion and Education should have be left as separate categories because of they contain a relatively large number of projects. Since Mike recommended we get the number of categories down to 50, I consolidated them into the “Other” category. What was done: I created a new table in sf merged called ‘categ_intend_aud_aug06’. This table is a duplicate of the ‘project_intended_audience01_aug_06’ table with the fields ‘new_code’ and ‘new_description’ added. I updated the new fields in the new table with the new codes and descriptions listed in the table below using a python script I (Bob English) wrote called add_categ_intend_aud.py. -

An Infrastructure to Support Interoperability in Reverse Engineering Nicholas Kraft Clemson University, [email protected]
Clemson University TigerPrints All Dissertations Dissertations 5-2007 An Infrastructure to Support Interoperability in Reverse Engineering Nicholas Kraft Clemson University, [email protected] Follow this and additional works at: https://tigerprints.clemson.edu/all_dissertations Part of the Computer Sciences Commons Recommended Citation Kraft, Nicholas, "An Infrastructure to Support Interoperability in Reverse Engineering" (2007). All Dissertations. 51. https://tigerprints.clemson.edu/all_dissertations/51 This Dissertation is brought to you for free and open access by the Dissertations at TigerPrints. It has been accepted for inclusion in All Dissertations by an authorized administrator of TigerPrints. For more information, please contact [email protected]. AN INFRASTRUCTURE TO SUPPORT INTEROPERABILITY IN REVERSE ENGINEERING A Dissertation Presented to the Graduate School of Clemson University In Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy Computer Science by Nicholas A. Kraft May 2007 Accepted by: Dr. Brian A. Malloy, Committee Chair Dr. Harold C. Grossman Dr. James F. Power Dr. Roy P. Pargas ABSTRACT An infrastructure that supports interoperability among reverse engineering tools and other software tools is described. The three major components of the infrastruc- ture are: (1) a hierarchy of schemas for low- and middle-level program representation graphs, (2) g4re, a tool chain for reverse engineering C++ programs, and (3) a repos- itory of reverse engineering artifacts, including the previous two components, a test suite, and tools, GXL instances, and XSLT transformations for graphs at each level of the hierarchy. The results of two case studies that investigated the space and time costs incurred by the infrastructure are provided. The results of two empirical evaluations that were performed using the api module of g4re, and were focused on computation of object-oriented metrics and three-dimensional visualization of class template diagrams, respectively, are also provided. -

Cisco Jabber for Windows 10.5 Licensing Information
Open Source Used In Cisco Jabber for Windows 10.5 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-61900240 78EE117C99-61900240 Open Source Used In Cisco Jabber for Windows 10.5 1 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-61900240 Contents 1.1 base64.cpp 1.0 1.1.1 Available under license 1.2 boost 1.51.0 1.2.1 Notifications 1.2.2 Available under license 1.3 boost 1.46.1 1.3.1 Notifications 1.3.2 Available under license 1.4 ccard 1.0 1.4.1 Available under license 1.5 curl 7.35 1.5.1 Available under license 1.6 curl/apache-portions 7.35 1.6.1 Available under license 1.7 e2fsprogs-lib-uuid 1.41.8 1.7.1 Available under license 1.8 Expat XML Parser - expat 1.95.8 1.8.1 Available under license 1.9 glib 2.27.1 1.9.1 Available under license 1.10 gstreamer 0.10.35.1 1.10.1 Available under license 1.11 gstreamer-plugins-bad 0.10.22.1 1.11.1 Available under license 1.12 gstreamer-plugins-base 0.10.35.1 1.12.1 Available under license 78EE117C99-61900240 -

Jabber SDK 9.2 Open Source Documentation
Open Source Used In Jabber SDK 9.2 This document contains the licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of the source code to which you are entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-34115968 Contents 1.1 AES-128 3.0 1.1.1 Available under license 1.2 APR 1.4.6 1.2.1 Available under license 1.3 APR-UTIL 1.4.1 1.3.1 Available under license 1.4 Base64 not versioned 1.4.1 Available under license 1.5 base64.cpp 1.0 1.5.1 Available under license 1.6 csf2g_boost_1.44-modified 1.44 1.6.1 Available under license 1.7 curl 7.25.0 1.7.1 Available under license 1.8 expat 2.1.0 Open Source Used In Jabber SDK 9.2 1 1.8.1 Available under license 1.9 FireBreath 1.6.0 1.9.1 Available under license 1.10 glib 2.27.1 1.10.1 Available under license 1.11 gstreamer 0.10.35.1 1.11.1 Available under license 1.12 gstreamer-plugins-bad 0.10.22.1 1.12.1 Available under license 1.13 gstreamer-plugins-base 0.10.35.1 1.13.1 Available under license 1.14 gstreamer-plugins-good 0.10.30.1 1.14.1 Available under license 1.15 jQuery 1.4.2 1.15.1 Available under license 1.16 ldns 1.6.13 1.16.1 Available under license 1.17 liboil 0.3.16.1 1.17.1 Available under license 1.18 libxml2 2.7.7 1.18.1 Available under license 1.19 libxml2-2.7.7 -

Team-Fly® Linux 3D Graphics Programming
Y L F M A E T Team-Fly® Linux 3D Graphics Programming Norman Lin Wordware Publishing, Inc. Library of Congress Cataloging-in-Publication Data Lin, Norman. Linux 3D graphics programming / by Norman Lin. p. cm. Includes bibliographical references and index. ISBN 1-55622-723-X (pbk.) 1. Computer graphics. 2. Linux. 3. Three-dimensional display systems. I. Title. T385 .L556 2001 006.6'93--dc21 00-69314 CIP © 2001, Wordware Publishing, Inc. All Rights Reserved 2320 Los Rios Boulevard Plano, Texas 75074 No part of this book may be reproduced in any form or by any means without permission in writing from Wordware Publishing, Inc. Printed in the United States of America ISBN 1-55622-723-X 10987654321 0103 Blender is a registered trademark of Not a Number B. V. Other product names mentioned are used for identification purposes only and may be trademarks of their respective companies. All inquiries for volume purchases of this book should be addressed to Wordware Publishing, Inc., at the above address. Telephone inquiries may be made by calling: (972) 423-0090 iii Contents Preface .........................................xiii Acknowledgments ...................................xv Introduction ......................................xvii Chapter 1 Introduction to 3D Graphics and Linux .........1 Why Linux ......................................3 Linux is Free and Open ..............................3 Linux is Powerful .................................4 Linux is Compatible ................................5 Linux is Contemporary ..............................6 -

Linux Assembly HOWTO I
Linux Assembly HOWTO i Linux Assembly HOWTO Ed. 0.7 Linux Assembly HOWTO ii Copyright © 2013 Leo Noordergraaf Copyright © 1999-2006 Konstantin Boldyshev Copyright © 1996-1999 Francois-Rene Rideau Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1; with no Invariant Sections, with no Front-Cover Texts, and no Back-Cover texts. Linux Assembly HOWTO iii Contents 1 Introduction 1 1.1 Legal Blurb . .1 1.2 Foreword . .1 1.3 Contributions . .1 1.4 Translations . .2 2 Do you need assembly? 3 2.1 Pros and Cons . .3 2.1.1 The advantages of Assembly . .3 2.1.2 The disadvantages of Assembly . .3 2.1.3 Assessment . .4 2.2 How to NOT use Assembly . .5 2.2.1 General procedure to achieve efficient code . .5 2.2.2 Languages with optimizing compilers . .5 2.2.3 General procedure to speed your code up . .5 2.2.4 Inspecting compiler-generated code . .6 2.3 Linux and assembly . .6 3 Assemblers 7 3.1 GCC Inline Assembly . .7 3.1.1 Where to find GCC . .7 3.1.2 Where to find docs for GCC Inline Asm . .7 3.1.3 Invoking GCC to build proper inline assembly code . .8 3.1.4 Macro support . .8 3.2 GAS..........................................................9 3.2.1 Where to find it . .9 3.2.2 What is this AT&T syntax . .9 3.2.3 Intel syntax . .9 3.2.4 16-bit mode . 10 3.2.5 Macro support . -

Linux Assembly HOWTO
Linux Assembly HOWTO Konstantin Boldyshev Linux Assembly <[email protected]> Francois−Rene Rideau Tunes project <[email protected]> 0.6g Edition Version 0.6g Copyright © 1999−2006 Konstantin Boldyshev Copyright © 1996−1999 Francois−Rene Rideau $Date: 2006/02/11 08:26:26 $ This is the Linux Assembly HOWTO, version 0.6g. This document describes how to program in assembly language using free programming tools, focusing on development for or from the Linux Operating System, mostly on IA−32 (i386) platform. Included material may or may not be applicable to other hardware and/or software platforms. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1; with no Invariant Sections, with no Front−Cover Texts, and no Back−Cover texts. Linux Assembly HOWTO Table of Contents Chapter 1. Introduction......................................................................................................................................1 1.1. Legal Blurb.......................................................................................................................................1 1.2. Foreword....................................................................................................................................1 Chapter 2. Do you need assembly?....................................................................................................................3 2.1. Pros and Cons...................................................................................................................................3 -

The Table of Equivalents / Replacements / Analogs of Windows Software in Linux
The table of equivalents / replacements / analogs of Windows software in Linux. Last update: 16.07.2003, 31.01.2005, 27.05.2005, 04.12.2006 You can always find the last version of this table on the official site: http://www.linuxrsp.ru/win-lin-soft/. This page on other languages: Russian, Italian, Spanish, French, German, Hungarian, Chinese. One of the biggest difficulties in migrating from Windows to Linux is the lack of knowledge about comparable software. Newbies usually search for Linux analogs of Windows software, and advanced Linux-users cannot answer their questions since they often don't know too much about Windows :). This list of Linux equivalents / replacements / analogs of Windows software is based on our own experience and on the information obtained from the visitors of this page (thanks!). This table is not static since new application names can be added to both left and the right sides. Also, the right column for a particular class of applications may not be filled immediately. In future, we plan to migrate this table to the PHP/MySQL engine, so visitors could add the program themselves, vote for analogs, add comments, etc. If you want to add a program to the table, send mail to winlintable[a]linuxrsp.ru with the name of the program, the OS, the description (the purpose of the program, etc), and a link to the official site of the program (if you know it). All comments, remarks, corrections, offers and bugreports are welcome - send them to winlintable[a]linuxrsp.ru. Notes: 1) By default all Linux programs in this table are free as in freedom. -
Making Sense of the Audio Stack on Unix
Making Sense of The Audio Stack On Unix Patrick Louis 2021-02-07 Published online on venam.nixers.net © Patrick Louis 2021 This publication is in copyright. Subject to statutory exception and to the provision of relevant collective licensing agreements, no reproduction of any part may take place without the written permission of the rightful author. First published eBook format 2021 The author has no responsibility for the persistence or accuracy of urls for external or third-party internet websites referred to in this publication, and does not guarantee that any content on such websites is, or will remain, accurate or appropriate. Contents Introduction 4 Hardware layer 6 Analog to Digital & Digital to Analog (ADC & DAC) 7 Libraries 10 Audio Driver 11 Advanced Linux Sound Architecture (ALSA) 15 Open Sound System (OSS) and SADA 22 Sound Servers 25 sndio 26 aRts (analog Real time synthesizer) and ESD or ESounD (Enlight- ened Sound Daemon) 28 PulseAudio 29 PulseAudio — What Is It? ........................ 29 Pulseaudio — Overall Design ....................... 30 Pulseaudio — Sink, Sink Input, Source, and Source Input ....... 32 Pulseaudio — Internal Concepts: Cards, Card Profile, Device Port, Device ................................. 34 Pulseaudio — Everything Is A Module Thinking ............ 35 Pulseaudio — Startup Process And Configuration ........... 36 Pulseaudio — Interesting Modules And Features ............ 38 Pulseaudio — Tools ............................ 40 Pulseaudio — Suspending ......................... 41 JACK 42 PipeWire 45 Conclusion 53 Bibliography 55 3 Introduction Come see my magical gramophone Audio on Unix is a little zoo, there are so many acronyms for projects and APIs that it’s easy to get lost. Let’s tackle that issue! Most articles are confusing because they either use audio technical jargon, or because they barely scratch the surface and leave people clueless. -

Linux Gaming Apis
Chapter 3 Linux Gaming APIs I still remember the first game programming book I ever read. By Dave Roberts, it was entitled PC Game Programming Explorer, and it demonstrated game programming with a game called Alien Alley. This was actually a neat game, especially for one intended as a book example: its graphics were smooth, the artwork was top-notch, and it ran well on my rather underpowered system. It would be easy for me to write such a game today, even in a matter of a few hours. But to a neophyte game programmer, it seemed a towering monolith. Back in the days of DOS-based gaming, programmers generally wrote games by issuing commands directly to the computer's hardware. There were only a few popular types of sound cards on the market, and many were at least partially compatible with Creative Labs' Sound Blaster. Input devices were trivial to program: accessing the mouse required only a few assembly language instructions (interrupt 33h, for those who remember), reading the joystick's position was a matter of a dozen lines of code, and there were several easy ways to collect keyboard input. Video programming was the hardest part of game development at the time: Although nearly every computer had a VGA-compatible display chip, coaxing fast and smooth graphics out of it took a significant amount of skill (due to some of the brain-dead limitations of the PC architecture). In fact, Alien Alley was mostly video code. Times have changed, arguably for the better. Very few game programmers actually write register-level video code these days; instead, they rely on 54 CHAPTER 3 prewritten interfaces (such as OpenGL, SDL, and DirectDraw).