View the Slides
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Step 1(To Be Performed on Your Samsung Galaxy S8) Step 2 Step 3
For a connection between your mobile phone and your Mercedes-Benz hands-free system to be successful, Bluetooth® must be turned on in your mobile phone. Please make sure to also read the operating and pairing instructions of the mobile phone. Please follow the steps below to connect your mobile phone Samsung Galaxy S8 with the mobile phone application of your Mercedes-Benz hands-free system using Bluetooth®. Step 1(to be performed on your Samsung Galaxy S8) Step 2 To get to the telephone screen of your Mercedes-Benz hands-free system press the Phone icon on the homescreen. Step 3 Select the Phone icon in the lower right corner. Step 4 Select the “Connect a New Device” application. Page 1 of 3 Step 5 Select the “Start Search Function” Step 6 The system will now search for any Bluetooth compatible phones. This may take some time depending on how many devices are found by the system. Step 7 Once the system completes searching select your mobile phone (example "My phone") from the list. Step 8 The pairing process will generate a 6-digit passcode and display it on the screen. Verify that the same 6 digits are shown on the display of your phone. Step 9 (to be performed on your Samsung Galaxy S8) There will be a pop-up "Bluetooth Request: 'MB Bluetooth' would like to pair with your phone. Confirm that the code '### ###' is shown on 'MB Bluetooth'. " Select "Pair" on your phone if the codes match. Page 2 of 3 Step 10 After the passcode is verified on both the mobile and the COMAND, the phone will begin to be authorized. -

Samsung Galaxy S8/S8+ User Guide
Sprint User Guide A downloadable, printable guide to your Samsung Galaxy S8/S8+ and its features. Available applications and services are subject to change at any time. Table of Contents GETTING STARTED 1 Introduction 2 About the User Guide 2 Special Features 2 SET UP YOUR DEVICE 4 Assemble Your Device 5 Install the SIM Card and a Memory Card 5 Charge the Battery 6 When to Charge the Battery 7 Micro-USB Connector 7 Reverse Charging 8 Start Using Your Device 8 Device Setup 9 Use the Setup Wizard 9 Google Account 9 Factory Reset Protection 9 Samsung Account 10 Add an Email Account 10 Activate Your Phone 11 Voicemail Setup 11 Transfer Data from Your Old Device 12 Transfer Files Between Your Phone and a Computer 12 Learn About Your Device 14 Your Phone’s Layout 14 Home Screen and Applications (Apps) List 15 Home Screen Basics 17 Customize Your Home Screen 17 Status Bar 20 Notification Panel 21 Bixby 22 Navigation 23 Enter Text 25 Samsung Keyboard 25 i Use Samsung Voice Input 26 Face Recognition 27 Fingerprint Scanner 27 Iris Scanner 28 Multi Window 30 Emergency Mode 31 Edge Screen 33 APPS 37 Using Apps 38 Apps Basics 38 Access Apps 38 Add an Apps Shortcut 38 Download and Install New Apps 38 Uninstall Apps 38 Organize Apps 39 Applications Settings 40 Calculator 41 Calendar 42 Calendar View 42 Create an Event 43 View Calendar Events 43 Share an Event 43 Delete an Event 43 Create a Task 44 Delete a Task 44 Calendar Settings 44 Add Calendars 44 Sync Calendars 45 Camera and Video 45 Camera Overview 45 Camera Shortcut 46 Take Pictures 46 Record -

Google Nexus 6P (H1512) Google Nexus 7
GPSMAP 276Cx Google Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Nexus 7 Google Nexus 6 HTC HTC One (M7) HTC One (M9) HTC One (M10) HTC One (M8) HTC One (A9) HTC Butterfly S LG LG V10 H962 LG G3 Titan LG G5 H860 LG E988 Gpro LG G4 H815 Motorola Motorola RAZR M Motorola DROID Turbo Motorola Moto G (2st Gen) Motorola Droid MAXX Motorola Moto G (1st Gen) Samsung Samsung Galaxy Note 2 Samsung Galaxy S4 Active Samsung Galaxy S6 edge + (SM-G9287) Samsung Galaxy Note 3 Samsung Galaxy S5 Samsung Galaxy S7 edge (SM- G935FD) Samsung Galaxy Note 4 Samsung Galaxy S5 Active Samsung GALAXY J Samsung Galaxy Note 5 (SM- Samsung Galaxy S5 Mini Samsung Galaxy A5 Duos N9208) Samsung Galaxy S3 Samsung Galaxy S6 Samsung Galaxy A9 (SM- A9000) Samsung Galaxy S4 Sony Sony Ericsson Xperia Z Sony Xperia Z3 Sony Xperia X Sony Ericsson Xperia Z Ultra Sony Xperia Z3 Compact Sony XPERIA Z5 Sony Xperia Z2 Sony XPERIA E1 Asus ASUS Zenfone 2 ASUS Zenfone 5 ASUS Zenfone 6 Huawei HUAWEI P8 HUAWEI M100 HUAWEI P9 HUAWEI CRR_L09 XIAOMI XIAOMI 2S XIAOMI 3 XIAOMI 5 XIAOMI Note GPSMAP 64s Google Google Nexus 4 Google Nexus 6P (H1512) Google Pixel Google Nexus 6 Google Nexus 7 HTC HTC One (M7) HTC One (A9) HTC Butterfly S HTC One (M8) HTC One (M10) HTC U11 HTC One (M9) LG LG Flex LG E988 Gpro LG G5 H860 LG V10 H962 LG G4 H815 LG G6 H870 Motorola Motorola RAZR M Motorola DROID Turbo Motorola Moto G (2st Gen) Motorola Droid MAXX Motorola Moto G (1st Gen) Motorola Moto Z Samsung Samsung Galaxy Note 2 Samsung Galaxy S5 Samsung Galaxy J5 Samsung Galaxy Note 3 Samsung Galaxy -

Mobile Phones the Latest Handsets Tested
Kondinin Group ResearchMAY 2018 No. 100 www.farmingahead.com.au ReportPrice: $95 MOBILE PHONES THE LATEST HANDSETS TESTED Independent information for agriculture H RE RC PO A R E T S • E RESEARCH REPORT MOBILE PHONES K R O • N P D U I N O I R N G NextG phones – the good, the bad and the ugly In their annual outback pilgrimage, Kondinin Group engineers Josh Giumelli and Ben White head to remote NSW to test the latest crop of handsets. Of the 13 units tested, there were several surprises; some star performers, some lacklustre results, and several that just made up the numbers. If you want a phone with good reception or features that matter, read on. hese days, the mobile phone is source in the paddock, rather than at home just about as crucial to the farm on the computer. business as any other piece of But we face a growing dilemma in that machinery. connectivity continues to limit the usefulness TThe sum total of tasks performed using a of much of what we want to do with our phone handset only increases as each year smartphones. While mobile networks goes by. More manufacturers supply apps continue to grow, they are not always rolled Retro rocket? The new Nokia 3310 harkens back to to operate or calibrate machinery, more out in rural areas where we need them the days of the CDMA network and the simple Nokia information is needed at your fingertips most. Compounding the problem is that the handsets with awesome battery life and excellent in an instant, and record keeping becomes smartphones' reception performance seems reception. -

Get a Samsung Galaxy S8 for FREE *
Get a Samsung Galaxy S8 for FREE * Buy a Samsung Galaxy S8, and get one free when you buy both on AT&T Next® with monthly eligible wireless (min. 1st line $50; 2nd line $20) and DIRECTV service (min. $29.99/mo.). *Each req’s $750 on installment agmt & elig. svc. Req’s a new line. Free after $750 in credits over 30 months. Credits start in 2 to 3 bills. If svc cancelled, device balance due. Taxes & fees apply. See details below. PLUS As a employee of JPMorgan Chase, you could qualify for benefits with the AT&T Signature Program.° °AT&T Signature Program provides various wireless service related benefits to qualified employees, students, military, and organization members of qualified AT&T enterprise or business customers. Go to att.com/bogosamsung for more details. To find the AT&T store^ closest to you, visit: att.com/find-a- store ^If you visit a local AT&T store, please have proof of eligibility. Mention Signature Code: FAN2476175 SAMSUNG GALAXY S8 INTEGRATED BOGO: Limited Time Offer (ends 4/30/17 in Puerto Rico). Select locations. Elig. Devices: Samsung Galaxy ,S S8 8+, Galaxy ,S G7 alaxy S7 Active, and Galaxy S7 Edge on 0% APR AT&T Next (30-mo. at $25) or AT&T Next Every Year (24-mo. at $31.25) installment agmts. $0 down for well-qualified credit or down payment may be req’d. Retail price is divided into monthly installments. Tax on full retail price due at sale. After all credits, get S8 up to $750 (credits are $25/mo. -
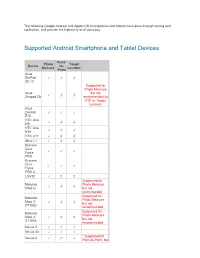
Supported Android Smartphone and Tablet Devices
The following Google Android and Apple iOS smartphones and tablets have gone through testing and calibration, and provide the highest level of accuracy: Supported Android Smartphone and Tablet Devices Point- Photo Target Device to- Measure Location Point Asus ZenPad ✓ ✗ ✗ 3S 10 Supported for Photo Measure Asus but not ✓ ✗ ✗ Zenpad Z8 recommended for P2P or Target Location Asus Zenpad ✓ ✓ ✓ Z10 HTC One ✓ ✗ ✗ M8 HTC One ✓ ✗ ✗ Mini HTC U11 ✓ ✗ ✗ iNew L1 ✓ ✗ ✗ Kyocera Dura ✓ ✓ ✓ Force PRO Kyocera Dura ✓ ✓ ✓ Force PRO 2 LGV20 ✓ ✗ ✗ Supported for Motorola Photo Measure ✓ ✗ ✗ Moto G but not recommended Supported for Motorola Photo Measure Moto X ✓ ✗ ✗ but not XT1052 recommended Supported for Motorola Photo Measure Moto X ✓ ✗ ✗ but not XT1053 recommended Nexus 5 ✓ ✓ ✓ Nexus 5X ✓ ✓ ✓ * Supported for Nexus 6 ✓ ✓* ✓ Point-to-Point, but cannot guarantee +/-3% accuracy * Supported for Point-to-Point, but Nexus 6P ✓ ✓* ✓ cannot guarantee +/-3% accuracy * Supported for Point-to-Point, but Nexus 7 ✓ ✓* ✓ cannot guarantee +/-3% accuracy Samsung Galaxy ✓ ✓ ✓ A20 Samsung Galaxy J7 ✓ ✗ ✓ Prime * Supported for Samsung Point-to-Point, but GALAXY ✓ ✓* ✓ cannot guarantee Note3 +/-3% accuracy Samsung GALAXY ✓ ✓ ✓ Note 4 * Supported for Samsung Point-to-Point, but GALAXY ✓ ✓* ✓ cannot guarantee Note 5 +/-3% accuracy Samsung GALAXY ✓ ✓ ✓ Note 8 Samsung GALAXY ✓ ✓ ✓ Note 9 Samsung GALAXY ✓ ✓ ✓ Note 10 Samsung GALAXY ✓ ✓ ✓ Note 10+ Samsung GALAXY ✓ ✓ ✓ Note 10+ 5G Supported for Samsung Photo Measure GALAXY ✓ ✗ ✗ but not Tab 4 (old) recommended Samsung Supported for -

Barometer of Mobile Internet Connections in Indonesia Publication of March 14Th 2018
Barometer of mobile Internet connections in Indonesia Publication of March 14th 2018 Year 2017 nPerf is a trademark owned by nPerf SAS, 87 rue de Sèze 69006 LYON – France. Contents 1 Methodology ................................................................................................................................. 2 1.1 The panel ............................................................................................................................... 2 1.2 Speed and latency tests ....................................................................................................... 2 1.2.1 Objectives and operation of the speed and latency tests ............................................ 2 1.2.2 nPerf servers .................................................................................................................. 2 1.3 Tests Quality of Service (QoS) .............................................................................................. 2 1.3.1 The browsing test .......................................................................................................... 2 1.3.2 YouTube streaming test ................................................................................................ 3 1.4 Filtering of test results .......................................................................................................... 3 1.4.1 Filtering of devices ........................................................................................................ 3 2 Overall results 2G/3G/4G ............................................................................................................ -
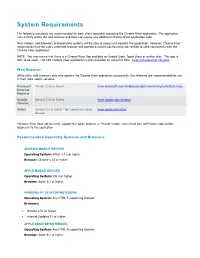
System Requirements
System Requirements The following standards are recommended for each client computer accessing the Chrome River application. The application runs entirely within the web browser and does not require any additional Chrome River application code. Most modern web browsers and operating systems will be able to access and operate the application. However, Chrome River recommends that the user’s preferred browser and operating system configuration be verified to work consistently with the Chrome River application. NOTE: You may notice that there is a Chrome River App available on Google Store, Apple Store or similar sites. This app is NOT to be used. The CBS Chrome River application is only available by using this URL: https://chromeriver.cbs.com. Web Browser While other web browsers may also operate the Chrome River application successfully, the following are recommended for use in their most recent versions: Microsoft Version 11.0 or higher www.microsoft.com/windows/products/winfamily/ie/default.mspx Internet Explorer Google Version 51.0 or higher www.google.com/chrome Chrome Safari Version 9.1 or higher* for supported mobile www.apple.com/safari devices *Chrome River does not currently support the Safari browser in “Private” mode. Users must turn off Private mode before logging in to the application. Recommended Operating Systems and Browsers ANDROID MOBILE DEVICES Operating System: Kitkat 4.4.2 or higher Browser: Chrome v.51 or higher APPLE MOBILE DEVICES Operating System: iOS 9 or higher Browser: Safari 9.1 or higher WINDOWS PC DESKTOP/NOTEBOOK Operating System: Any HTML 5-supporting browser Browsers: • Chrome v.51 or higher • Internet Explorer 11 or higher APPLE DESKTOP/NOTEBOOK: Operating System: Any HTML 5-supporting browser Browser: Safari 9.1 or higher CERTIFIED VS SUPPORTED DEVICES Devices listed as certified are those on which Chrome River has tested and fixed any bugs. -

A Guide to Smartphone Astrophotography National Aeronautics and Space Administration
National Aeronautics and Space Administration A Guide to Smartphone Astrophotography National Aeronautics and Space Administration A Guide to Smartphone Astrophotography A Guide to Smartphone Astrophotography Dr. Sten Odenwald NASA Space Science Education Consortium Goddard Space Flight Center Greenbelt, Maryland Cover designs and editing by Abbey Interrante Cover illustrations Front: Aurora (Elizabeth Macdonald), moon (Spencer Collins), star trails (Donald Noor), Orion nebula (Christian Harris), solar eclipse (Christopher Jones), Milky Way (Shun-Chia Yang), satellite streaks (Stanislav Kaniansky),sunspot (Michael Seeboerger-Weichselbaum),sun dogs (Billy Heather). Back: Milky Way (Gabriel Clark) Two front cover designs are provided with this book. To conserve toner, begin document printing with the second cover. This product is supported by NASA under cooperative agreement number NNH15ZDA004C. [1] Table of Contents Introduction.................................................................................................................................................... 5 How to use this book ..................................................................................................................................... 9 1.0 Light Pollution ....................................................................................................................................... 12 2.0 Cameras ................................................................................................................................................ -

List Compatible Smartphones
Produkt App iOS Android AS80/C iPhone 7 Plus Samsung Galaxy S7 iPhone 7 Samsung Galaxy S6 iPhone 6s Plus Samsung Galaxy S5 iPhone 6s Samsung Galaxy S4 iPhone 6 Plus Samsung Galaxy S4 mini iPhone 6 Samsung Galaxy S3 AS81 iPhone 5s LG Google Nexus 5 iPhone 5c LG L40 iPhone 5 iPhone 4s iPad (4th generation) AW85 iPad (3rd generation) iPad mini iPod touch (5th generation) BC57 BC85 BF700 BF710 BF800 BM57 1/6 Produkt App iOS Android BM75 iPhone 7 Plus Samsung Galaxy S7 iPhone 7 Samsung Galaxy S6 iPhone 6s Plus Samsung Galaxy S5 iPhone 6s Samsung Galaxy S4 iPhone 6 Plus Samsung Galaxy S4 mini iPhone 6 Samsung Galaxy S3 BM77 iPhone 5s LG Google Nexus 5 iPhone 5c LG L40 iPhone 5 iPhone 4s iPad (4th generation) BM 85 iPad (3rd generation) iPad mini iPod touch (5th generation) GL50EVO BLE GL50EVO NFC GS485 PO60 Systemvoraussetzung: Bluetooth® 4.0, iOS ab 8.0 Bluetooth® 4.0, Android™ ab 4.4 Android™ ab Version 4.1 mit NFC-Funktion (Near Field Communication) 2/6 Produkt App iOS Android KS800 iPhone 7 Plus iPhone 7 iPhone 6s Plus iPhone 6s iPhone 6 Plus iPhone 6 iPhone 5s iPhone 5c iPhone 5 iPhone 4s iPad (4th generation) iPad (3rd generation) iPad mini Systemvoraussetzung: Bluetooth® 4.0, iOS ab 8.0 Produkt App iOS Android AS80/C iPhone 7 Plus Samsung Galaxy S7 iPhone 7 Samsung Galaxy S6 iPhone 6s Plus Samsung Galaxy S5 iPhone 6s Samsung Galaxy S4 iPhone 6 Plus Samsung Galaxy S4 mini iPhone 6 Samsung Galaxy S3 AS81 iPhone 5s LG Google Nexus 5 iPhone 5c LG L40 iPhone 5 iPhone 4s iPad (4th generation) BF700 iPad (3rd generation) iPad mini iPod touch -
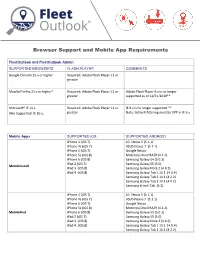
Browser Support and Mobile App Requirements
Browser Support and Mobile App Requirements FleetOutlook and FleetOutlook Admin SUPPORTED BROWSERS FLASH PLAYER COMMENTS Google Chrome 25.x or higher Required: Adobe Flash Player 11 or greater Mozilla Firefox 21.x or higher* Required: Adobe Flash Player 11 or Adobe Flash Player 9.x is no longer greater supported as of 12/31/2010** Microsoft® IE 11.x Required: Adobe Flash Player 11 or IE 9.x is no longer supported ** Also Supported: IE 10.x, greater Note: ActiveX Filtering must be OFF in IE 9.x Mobile Apps SUPPORTED iOS SUPPORTED ANDROID iPhone 4 (iOS 7) LG Nexus 5 (5.1.1) iPhone 4s (iOS 7) ASUS Nexus 7 (5.1.1) iPhone 5 (iOS 7) Google Nexus iPhone 5s (iOS 8) Motorola Droid RAZR (4.1.2) iPhone 6 (iOS 8) Samsung Galaxy S4 (5.0.1) iPad 2 (iOS 7) Samsung Galaxy S5 (5.0) MobileInstall iPad 3 (iOS 8) Samsung Galaxy Note 2 (4.4.2) iPad 4 (iOS 8) Samsung Galaxy Tab 1 10.1 (4.0.4) Samsung Galaxy Tab 2 10.1 (4.2.2) Samsung Galaxy Tab 3 10.1 (4.4.2) Samsung 8-inch Tab (4.2) iPhone 4 (iOS 7) LG Nexus 5 (5.1.1) iPhone 4s (iOS 7) ASUS Nexus 7 (5.1.1) iPhone 5 (iOS 7) Google Nexus iPhone 5s (iOS 8) Motorola Droid RAZR (4.1.2) MobileFind iPhone 6 (iOS 8) Samsung Galaxy S4 (5.0.1) iPad 2 (iOS 7) Samsung Galaxy S5 (5.0) iPad 3 (iOS 8) Samsung Galaxy Note 2 (4.4.2) iPad 4 (iOS 8) Samsung Galaxy Tab 1 10.1 (4.0.4) Samsung Galaxy Tab 2 10.1 (4.2.2) Samsung Galaxy Tab 3 10.1 (4.4.2) Samsung S3 (4.0.4) Samsung 8-inch Tab (4.2) iPhone 4 (iOS 6) LG Nexus 5 (5.1.1) iPhone 4s (iOS 6) ASUS Nexus 7 (5.1.1) iPhone 5 (iOS 7) Google Nexus iPhone 5s (iOS 8) Motorola Droid RAZR (4.1.2) iPhone 6 (iOS 8) Samsung Galaxy S4 (5.0.1) iPad 2 (iOS 7) Samsung Galaxy S5 (5.0) MobileNav iPad 3 (iOS 8) Samsung Galaxy Note 2 (4.4.2) iPad 4 (iOS 8) Samsung Galaxy Tab 1 10.1 (4.0.4) Samsung Galaxy Tab 2 10.1 (4.2.2) Samsung Galaxy Tab 3 10.1 (4.4.2) Samsung S3 (4.0.4) Samsung 8-inch Tab (4.2) ! Important: For all browsers you must enable JavaScript, cookies and SSL 3.0. -
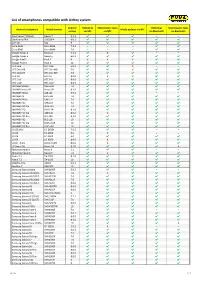
List of Smartphones Compatible with Airkey System
List of smartphones compatible with AirKey system Android Unlocking Maintenance tasks Unlocking Maintenance tasks Android smartphone Model number Media updates via NFC version via NFC via NFC via Bluetooth via Bluetooth Asus Nexus 7 (Tablet) Nexus 7 5.1.1 ✔ ✔ ✔ – – Blackberry PRIV STV100-4 6.0.1 ✔ ✔ ✔ ✔ ✔ CAT S61 S61 9 ✔ ✔ ✔ ✔ ✔ Doro 8035 Doro 8035 7.1.2 – – – ✔ ✔ Doro 8040 Doro 8040 7.0 – – – ✔ ✔ Google Nexus 4 Nexus 4 5.1.1 ✔ X ✔ – – Google Nexus 5 Nexus 5 6.0.1 ✔ ✔ ✔ ✔ ✔ Google Pixel 2 Pixel 2 9 X X X ✔ ✔ Google Pixel 4 Pixel 4 10 ✔ ✔ ✔ ✔ ✔ HTC One HTC One 5.0.2 ✔ ✔ X – – HTC One M8 HTC One M8 6.0 ✔ ✔ X ✔ ✔ HTC One M9 HTC One M9 7.0 ✔ ✔ ✔ ✔ ✔ HTC 10 HTC 10 8.0.0 ✔ X X ✔ ✔ HTC U11 HTC U11 8.0.0 ✔ ✔ ✔ ✔ ✔ HTC U12+ HTC U12+ 8.0.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Mate 9 MHA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Nexus 6P Nexus 6P 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P8 lite ALE-L21 5.0.1 ✔ ✔ ✔ – – HUAWEI P9 EVA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P9 lite VNS-L21 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 VTR-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 lite WAS-LX1 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 EML-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 lite ANE-LX1 8.0.0 ✔ X ✔ ✔ ✔ HUAWEI P20 Pro CLT-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 ELE-L29 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 lite MAR-LX1A 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 Pro VOG-L29 10 ✔ ✔ ✔ ✔ ✔ LG G2 Mini LG-D620r 5.0.2 ✔ ✔ ✔ – – LG G3 LG-D855 5.0 ✔ X ✔ – – LG G4 LG-H815 6.0 ✔ ✔ ✔ ✔ ✔ LG G6 LG-H870 8.0.0 ✔ X ✔ ✔ ✔ LG G7 ThinQ LM-G710EM 8.0.0 ✔ X ✔ ✔ ✔ LG Nexus 5X Nexus 5X 8.1.0 ✔ ✔ ✔ ✔ X Motorola Moto X Moto X 5.1 ✔ ✔ ✔ – – Motorola Nexus 6 Nexus 6 7.0 ✔ X ✔ ✔ ✔ Nokia 7.1 TA-1095 8.1.0 ✔ ✔ X ✔ ✔ Nokia 7.2 TA-1196 10 ✔ ✔ ✔