Pseudonymity in Social Machines
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UC Santa Barbara UC Santa Barbara Electronic Theses and Dissertations
UC Santa Barbara UC Santa Barbara Electronic Theses and Dissertations Title A Web of Extended Metaphors in the Guerilla Open Access Manifesto of Aaron Swartz Permalink https://escholarship.org/uc/item/6w76f8x7 Author Swift, Kathy Publication Date 2017 Peer reviewed|Thesis/dissertation eScholarship.org Powered by the California Digital Library University of California UNIVERSITY OF CALIFORNIA Santa Barbara A Web of Extended Metaphors in the Guerilla Open Access Manifesto of Aaron Swartz A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Education by Kathleen Anne Swift Committee in charge: Professor Richard Duran, Chair Professor Diana Arya Professor William Robinson September 2017 The dissertation of Kathleen Anne Swift is approved. ................................................................................................................................ Diana Arya ................................................................................................................................ William Robinson ................................................................................................................................ Richard Duran, Committee Chair June 2017 A Web of Extended Metaphors in the Guerilla Open Access Manifesto of Aaron Swartz Copyright © 2017 by Kathleen Anne Swift iii ACKNOWLEDGEMENTS I would like to thank the members of my committee for their advice and patience as I worked on gathering and analyzing the copious amounts of research necessary to -

Negotiating Ludic Normativity in Facebook Meme Pages
in ilburg apers ulture tudies 247 T P C S Negotiating Ludic Normativity in Facebook Meme Pages by Ondřej Procházka Tilburg University [email protected] December 2020 This work is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nd/4.0/ Negotiating ludic normativity in Facebook meme pages Negotiating ludic normativity in Facebook meme pages PROEFSCHRIFT ter verkrijging van de graad van doctor aan Tilburg University, op gezag van de rector magnificus, prof. dr. W.B.H.J. van de Donk, in het openbaar te verdedigen ten overstaan van een door het college voor promoties aangewezen commissie in de Portrettenzaal van de Universiteit op maandag 7 december 2020 om 16.00 uur door Ondřej Procházka geboren te Kyjov, Tsjechië Promotores: prof. J.M.E. Blommaert prof. A.M. Backus Copromotor: dr. P.K. Varis Overige leden van de promotiecommissie: prof. A. Georgakopoulou prof. A. Jaworski prof. A.P.C. Swanenberg dr. R. Moore dr. T. Van Hout ISBN 978-94-6416-307-0 Cover design by Veronika Voglová Layout and editing by Karin Berkhout, Department of Culture Studies, Tilburg University Printed by Ridderprint BV, the Netherlands © Ondřej Procházka, 2020 The back cover contains a graphic reinterpretation of the material from the ‘Faceblock’ article posted by user ‘Taha Banoglu’ on the Polandball wiki and is licensed under the Creative Commons Attribution- Share Alike License. All rights reserved. No other parts of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any other means, electronic, mechanical, photocopying, recording, or otherwise, without permission of the author. -

Thesis (844.6Kb)
ABSTRACT You Should Have Expected Us – An Explanation of Anonymous Alex Gray Director: Linda Adams; PhD Anonymous is a decentralized activist collective that has evolved using the technology of the information age. This paper traces its origins as a way of contextualizing and better understanding its actions. The groups composition is examined using its self‐ascribed imagery to illustrate its’ unique culture and relational norms. Its structure and motivation are analyzed using the framework developed for social movements and terrorist networks. Finally a discussion of a splinter cell and official reaction delineate both strengths and weaknesses of the movement while suggesting its future development. The conclusion serves to expound on the ideal end for the online anonymous community as a new frontier in meritocratic activism. APPROVED BY DIRECTOR OF HONORS THESIS: ‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐ Dr. Linda Adams, Department of Political Science APPROVED BY THE HONORS PROGRAM: ‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐‐ Dr. Andrew Wisely, Director. DATE: ________________________ YOU SHOULD HAVE EXPECTED US AN EXPLANATION OF ANONYMOUS A Thesis Submitted to the Faculty of Baylor University In Partial Fulfillment of the Requirements for the Honors Program By Alex Gray Waco, Texas May 2012 TABLE OF CONTENTS Preface iii Acknowledgements iv Dedication v CHAPTER ONE 1 Introduction CHAPTER TWO 4 The Story of Anonymous CHAPTER THREE 20 A Group with No Head and No Members CHAPTER FOUR 39 Activists or Terrorists CHAPTER FIVE 56 Distraction, Diversion, Division CHAPTER SIX 67 Conclusion Bibliography 71 ii PREFACE Writing a paper about a decentralized, online collective of similarly minded individuals presents a unique set of challenges. In spending so much time with this subject, it is my goal to be both intellectually honest and as thorough as I can be. -

Internet Memes and Their Significance for Myth Studies
PALACKÝ UNIVERSITY, OLOMOUC FACULTY OF ARTS DEPARTMENT OF ENGLISH AND AMERICAN STUDIES INTERNET MEMES AND THEIR SIGNIFICANCE FOR MYTH STUDIES DOCTORAL DISSERTATION Author: Mgr. Pavel Gončarov Supervisor: Prof. PhDr. Marcel Arbeit, Dr. 2016 UNIVERZITA PALACKÉHO V OLOMOUCI FILOZOFICKÁ FAKULTA KATEDRA ANGLISTIKY A AMERIKANISTIKY INTERNETOVÉ MEMY A JEJICH VÝZNAM PRO VÝZKUM MYTOLOGIÍ DIZERTAČNÍ PRÁCE Autor práce: Mgr. Pavel Gončarov Vedoucí práce: Prof. PhDr. Marcel Arbeit, Dr. 2016 ANNOTATION Pavel Gončarov Department of English and American Studies, Faculty of Arts, Palacký University, Olomouc Title: Internet Memes and their Significance for Myth Studies Supervisor: Prof. PhDr. Marcel Arbeit, Dr. Language: English Character count: 347, 052 Number of appendices: 65 Entries in bibliography: 134 KEY WORDS myth, mythology, archaic revival, poetry, concrete poetry, semiotics, participatory media, digital culture, meme, memetics, internet memes, rage comics, Chinese rage comics, baozou manhua, baoman ABSTRACT This dissertation posits that the heart of myth rests with the novelizing and complexifying ritual of post-totemic sacrifice. As it makes an example of its delivery through poetry it tries to show the changing nature of poetry and art through history towards a designated act of whichever content. Transhumanism is seen as a tendency and so the dissertation imagines a poet whose practical exercise in the workings of typewriter produced concrete poetry are then tied to the coded ASCII table, emoticons and polychromatic glyphs which are subject to default visual modifications by manufacturers of technology. The dissertation then offers a view at memetic information transmission which is worked into a model that draws on Jacque Derrida’s différance. From a construction of a tree of hypothetical changes in the evolution of a state of culture of the primitive Waorani tribe, the dissertation moves to a logical exercise about hypernyms and hyponyms. -

Lols, Lulz, and ROFL: the Culture, Fun, and Serious Business of Internet Memes
LOLs, Lulz, and ROFL: The Culture, Fun, and Serious Business of Internet Memes by Noah David Levinson Bachelor of Philosophy, University of Pittsburgh, 2012 Submitted to the Faculty of The University of Pittsburgh Honors College in partial fulfillment of the requirements for the degree of Bachelor of Philosophy University of Pittsburgh 2012 UNIVERSITY OF PITTSBURGH University Honors College This thesis was presented by Noah David Levinson It was defended on July 30, 2012 and approved by Gabriella Coleman, PhD, Department of Art History & Communications, McGill University Dana Och, PhD, Film Studies Program Annette Vee, PhD, English Department Thesis Advisor: Daniel Morgan, PhD, Film Studies Program ii Copyright © by Noah David Levinson 2012 iii LOLs, Lulz, and ROFL: The Culture, Fun, and Serious Business of Internet Memes Noah David Levinson, BPhil University of Pittsburgh, 2012 This thesis takes an analytical look into the workings of Internet Memes and the culture that surrounds and nourishes them. Through a selection of Internet Meme case studies, a list of cultural qualities are compiled and then used to identify the attitudes of Internet Meme Culture. Then by comparing the relationship between Internet Memes and advertising, film, and television, a contrast between Old and New Media is established. Alongside using political Memes to find connections between Internet Memes and general expression and communication, the final hope is to understand Internet Meme Culture and where it might take Mass and Popular Culture as the digital millennial becomes the new digital citizens. iv TABLE OF CONTENTS 1.0 INTRODUCTION: WHY STUDY INTERNET MEMES? ............................................. 1 1.1 WEB 3.33333333… AND BRONIES ...................................................................... -

Lols, Lulz, and ROFL: the Culture, Fun, and Serious Business of Internet Memes
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by D-Scholarship@Pitt LOLs, Lulz, and ROFL: The Culture, Fun, and Serious Business of Internet Memes by Noah David Levinson Bachelor of Philosophy, University of Pittsburgh, 2012 Submitted to the Faculty of The Univresity of Pittsburgh Honors College in partial fulfillment of the requirements for the degree of Bachelor of Philosophy University of Pittsburgh 2012 UNIVERSITY OF PITTSBURGH University Honors College This thesis was presented by Noah David Levinson It was defended on July 30, 2012 and approved by Gabriella Coleman, PhD, Department of Art History & Communications, McGill University Dana Och, PhD, Film Studies Program Annette Vee, PhD, English Department Thesis Advisor: Daniel Morgan, PhD, Film Studies Program ii Copyright © by Noah David Levinson 2012 iii LOLs, Lulz, and ROFL: The Culture, Fun, and Serious Business of Internet Memes Noah David Levinson, BPhil University of Pittsburgh, 2012 This thesis takes an analytical look into the workings of Internet Memes and the culture that surrounds and nourishes them. Through a selection of Internet Meme case studies, a list of cultural qualities are compiled and then used to identify the attitudes of Internet Meme Culture. Then by comparing the relationship between Internet Memes and advertising, film, and television, a contrast between Old and New Media is established. Alongside using political Memes to find connections between Internet Memes and general expression and communication, the final hope is to understand Internet Meme Culture and where it might take Mass and Popular Culture as the digital millennial becomes the new digital citizens. -

Who Is Pedobear
Who Is Pedobear 1 / 3 Who Is Pedobear 2 / 3 Of course, this ignores what the Pedobear meme is really about -- which is more of a 4chan /b/ "you're being creepy" sorta of thing, which .... WHO PEDOBEAR IS | Just clearing up a few misconceptions and providing an avenue to help the pedobear meme reclaim his "good" name in .... Police in San Luis Obispo in California have entirely missed the joke and seem to believe that Pedobear has been adopted as a 'mascot' by .... This group has over 335 pages that promote pedophila, child molestation, exsposes child porn, has graphic content, posts, pictures. It is affillated with the .... If you're not familiar with Pedobear, it's an internet meme of a pedophilic bear used to mock pedophiles. Nestle Australia & New Zealand .... Pedobear is an Internet meme that became popular through the imageboard 4chan. As the name suggests it is portrayed as a pedophilic cartoon bear. It is a .... Jul 12, 2014 - Explore calliecastellan's board "pedobear" on Pinterest. See more ideas about Funny, Memes and Funny pictures.. The alert links Pedobear's image to people, who have "a predilection to sexually inappropriate, or even, sexually assaultive behavior." "His cute .... UPDATE--September 15th, 2010. Tulsa Police originially told FOX23 News the man in Pedobear costume at San Diego's Comic Con .... Re: http://knowyourmeme.com/memes/pedobear oin us as we take a look at the Internet's most beloved and offensive bear.. Police in California have issued a warning about the “Pedo bear”, a computer character created as an internet joke. -

Troll Feminism: the Rise of Popular Feminism in South Korea
Troll Feminism: The Rise of Popular Feminism in South Korea Euisol Jeong PhD University of York Women’s Studies September 2020 Abstract This dissertation explores a new form of feminist movement in South Korea that has emerged online. The movement, which I refer to as the ‘Megalia phenomenon’, was catalysed by ‘man-hating trolling’ in 2015, which distinguishes this new digital feminism from extant feminist movements. The dissertation interrogates how South Korean digital practices have shaped a specific form of popular feminism – which I term ‘troll feminism’. In this dissertation, I ask: how the digital venues on the South Korean web have interacted and intertwined with the Megalia phenomenon; how Megalian trolls devised their activist practices based on the digital habits; and how Megalians’ digital discourses were materialised through forms of practical activism. I trace how the participants in the Megalian movement appropriated the practices of online misogynists (such as aggressive and offensive trolling acts) in order to respond to prevalent online misogyny, which led them to develop a feminist movement. The fun entailed in trolling altered how people ‘do’ feminism in this movement, making participants experience it as game playing, hence ‘gamifying’ the activism. As the activism of ‘chasing fun’ through ‘man-hating’ enabled many women to question the gendered reality of their world, the politics of trolling provided a feminist critique of South Korean society that made women’s lives intelligible and made social oppression recognisable, resulting in their involvement in political resistance. I analyse the materialist orientation of feminist politics in the Megalian movement, arguing that its inclination to prioritise what is actual and material, practical and pragmatic derives from Megalians’ nature as digital users, and as gamers, who seek out direct and immediate reactions to their actions – which they experience as ‘triumphs’ in the gender war they are involved in. -

First-Monday-Paper.Pdf
Volume 24, Number 8 - 5 August 2019 > Lamont The paper consists of an interdisciplinary close reading analysis of the 4chan character of Pedobear as an example of transgressive humour surrounding traumatic subjects in interactive online media. The character and its various applications, from simple knock-knock style jokes, pranks against an ignorant outsider public, countercultural consumption and even as an accusation of real-world abuse, are examined here. The close reading study locates the subject within a broader context of the insider currency of the shocking and taboo subject for masculinist youth culture communities both online and off. Contents Introduction Insider abusers: A close reading of Pedobear as anexample of CSA-themed online comic capital Conclusion Introduction The paper consists of a close reading analysis of the character of Pedobear as an example of digital humour and transgressive media surrounding representations of CSA (childhood sexual abuse) in interactive online media. This is a comic cartoon teddy bear created on 4chan in the mid-2000s, described as “the characterization of paedophilia on the Web” (‘Know Your Meme: Pedo Bear,’ 2011), with the study itself located within what digital media theorist Whitney Phillips (2018) described as the “subcultural golden age” of online humour and trolling culture, a time period she estimates as between “2007–2011, which was followed by a slow strange integration into mainstream culture between 2011– 2013” [1]. The character and its various applications, from simple knock-knock style jokes, pranks against an ignorant outsider public, and even as an accusation of real-world abuse, are examined here. The responsive and reactive function of this character is reflected in the paper’s selection of sources, which range from online comments to panic-ed newspaper write ups around this contentious creation. -

Focus-2009-10 Focus 2009
FOCUS media joUrNal volUme XXX 2009-2010 the FocUs staFF Editor-in-Chief Jorge Cuellar Chief Copy Editors Virginia Yapp and Danielle Laudon Copy Editors Se Young Kang, Justin Kruszona, Luis Moreno, Melissa Perez Cover Design Dan Polaske Se Young Kang Layout Design Jorge Cuellar, Virginia Yapp Staff Advisor Joe Palladino aBoUt Us Jorge Cuellar: Editor-in-Chief Jorge is a graduating senior double majoring in Film & Media Studies and Latin American & Iberian Studies. He is Salvadoran-born and LA raised. He really enjoys critical and cultur- al theory. Someday he may write it. Jorge will be attending graduate school in the School of Cinematic Arts at USC in Fall 2010. Virginia Yapp: Chief Copy Editor Virginia is a Film & Media Studies major who will be sent out into the “real” world, kicking and screaming, this June. As far as film goes, she’s rather fond of New Queer Cinema, ad- mittedly awful horror films and Sunset Boule- vard, but she’d really rather be rollerskating. Danielle Laudon: Chief Copy Editor Danielle Laudon is a graduating Film & Me- dia Studies major. She has done research for the production company FilmEngine and ex- celled as a story analyst for the 4th STAGE International Script Competition. Being an un- abashed, nondiscriminatory cinephile, she has thoroughly enjoyed every minute of study at UCSB. Se Young Kang: Copy Editor Se Young is a third year Film & Media Stud- ies major. She wrote, directed, and narrated Ripped Off, a doc about the UC budget cri- sis. Currently she works as the Digital Media Coordinator for Associated Students Program Board and is interning at Original Productions (the creators of Deadliest Catch). -

Laugh out Loud in Real Life: Women's Humor and Fan Identity MASSACHUSETTS INSTITUTE by of TECHNOLOGY Madeline Lenore "Flourish" Klink JUN 292010 B.A
Laugh Out Loud In Real Life: Women's Humor and Fan Identity MASSACHUSETTS INSTITUTE by OF TECHNOLOGY Madeline LeNore "Flourish" Klink JUN 292010 B.A. Religion LIBRARIES Reed College, 2008 SUBMITTED TO THE PROGRAM IN COMPARATIVE MEDIA STUDIES IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF SCIENCE IN COMPARATIVE MEDIA STUDIES AT THE MASSACHUSETTS INSTITUTE OF TECHNOLOGY JUNE 2010 ARCHNES @ 2010 Madeline LeNore "Flourish" Klink. All rights reserved. The author hereby grants MIT permission to reproduce and to distribute publicly paper and electronic copies of this thesis document in whole or in part in any medium now known or hereafter created., Signature of author: Program in C6mparative Media Studies May 2010 Certified by: I Henry Jenkins III Comparative Media Studies Affiliate Provost's Professor of Communication, Journalism and Cinematic Arts (USC) Thesis Supervisor Accepted by: William Charles Uricchio Professor of Comparative Media Studies Co-director, Comparative Media Studies Laugh Out Loud In Real Life: Women's Humor and Fan Identity by Madeline LeNore "Flourish" Klink Submitted to the Program in Comparative Media Studies on May 5, 2010, in Partial Fulfillment of the Requirements for the Degree of Master of Science Comparative Media Studies ABSTRACT The emerging field of fan studies has, until recently, been defined only by the research that has taken place within it. Almost universally, this research focuses on self-identified fans. However, scholars are beginning to examine and debate what the limits of the field should be. This study argues that self-identified fans are not the only group that ought to be examined under the heading of fan studies. -
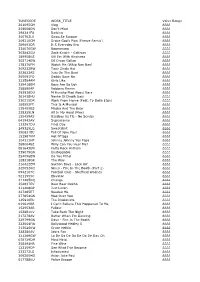
TUNECODE WORK TITLE Value Range 261095CM
TUNECODE WORK_TITLE Value Range 261095CM Vlog ££££ 259008DN Don't Mind ££££ 298241FU Barking ££££ 300703LV Swag Se Swagat ££££ 309210CM Drake God's Plan (Freeze Remix) ££££ 289693DR It S Everyday Bro ££££ 234070GW Boomerang ££££ 302842GU Zack Knight - Galtiyan ££££ 189958KS Kill Em With Kindness ££££ 302714EW Dil Diyan Gallan ££££ 178176FM Watch Me (Whip Nae Nae) ££££ 309232BW Tiger Zinda Hai ££££ 253823AS Juju On The Beat ££££ 265091FQ Daddy Says No ££££ 232584AM Girls Like ££££ 329418BM Boys Are So Ugh ££££ 258890AP Robbery Remix ££££ 292938DU M Huncho Mad About Bars ££££ 261438HU Nashe Si Chadh Gayi ££££ 230215DR Work From Home (Feat. Ty Dolla $Ign) ££££ 188552FT This Is A Musical ££££ 135455BS Masha And The Bear ££££ 238329LN All In My Head (Flex) ££££ 155459AS Bassboy Vs Tlc - No Scrubs ££££ 041942AV Supernanny ££££ 133267DU Final Day ££££ 249325LQ Sweatshirt ££££ 290631EU Fall Of Jake Paul ££££ 153987KM Hot N*Gga ££££ 304111HP Johnny Johnny Yes Papa ££££ 2680048Z Willy Can You Hear Me? ££££ 081643EN Party Rock Anthem ££££ 239079GN Unstoppable ££££ 254096EW Do You Mind ££££ 128318GR The Way ££££ 216422EM Section Boyz - Lock Arf ££££ 325052KQ Nines - Fire In The Booth (Part 2) ££££ 0942107C Football Club - Sheffield Wednes ££££ 5211555C Elevator ££££ 311205DQ Change ££££ 254637EV Baar Baar Dekho ££££ 311408GP Just Listen ££££ 227485ET Needed Me ££££ 277854GN Mad Over You ££££ 125910EU The Illusionists ££££ 019619BR I Can't Believe This Happened To Me ££££ 152953AR Fallout ££££ 153881KV Take Back The Night ££££ 217278AV Better When