Programming Manual for SQUIX, MACH
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Interaction Between Web Browsers and Script Engines
IT 12 058 Examensarbete 45 hp November 2012 Interaction between web browsers and script engines Xiaoyu Zhuang Institutionen för informationsteknologi Department of Information Technology Abstract Interaction between web browser and the script engine Xiaoyu Zhuang Teknisk- naturvetenskaplig fakultet UTH-enheten Web browser plays an important part of internet experience and JavaScript is the most popular programming language as a client side script to build an active and Besöksadress: advance end user experience. The script engine which executes JavaScript needs to Ångströmlaboratoriet Lägerhyddsvägen 1 interact with web browser to get access to its DOM elements and other host objects. Hus 4, Plan 0 Browser from host side needs to initialize the script engine and dispatch script source code to the engine side. Postadress: This thesis studies the interaction between the script engine and its host browser. Box 536 751 21 Uppsala The shell where the engine address to make calls towards outside is called hosting layer. This report mainly discussed what operations could appear in this layer and Telefon: designed testing cases to validate if the browser is robust and reliable regarding 018 – 471 30 03 hosting operations. Telefax: 018 – 471 30 00 Hemsida: http://www.teknat.uu.se/student Handledare: Elena Boris Ämnesgranskare: Justin Pearson Examinator: Lisa Kaati IT 12 058 Tryckt av: Reprocentralen ITC Contents 1. Introduction................................................................................................................................ -

Disk Clone Industrial
Disk Clone Industrial USER MANUAL Ver. 1.0.0 Updated: 9 June 2020 | Contents | ii Contents Legal Statement............................................................................... 4 Introduction......................................................................................4 Cloning Data.................................................................................................................................... 4 Erasing Confidential Data..................................................................................................................5 Disk Clone Overview.......................................................................6 System Requirements....................................................................................................................... 7 Software Licensing........................................................................................................................... 7 Software Updates............................................................................................................................. 8 Getting Started.................................................................................9 Disk Clone Installation and Distribution.......................................................................................... 12 Launching and initial Configuration..................................................................................................12 Navigating Disk Clone.....................................................................................................................14 -

Readerware Cuecat Manual
Readerware CueCat Manual This manual will help you install your CueCat(R) barcode reader and get you started scanning your books, music and videos. Important: If you purchased your CueCat from another source, you may have received software with it, do not install this software. You do not need any additional software when using your CueCat with Readerware, and following the demise of Digital Convergence, the CueCat software will no longer work. Table of Contents Installing a PS/2 CueCat on a desktop machine (Windows and Linux)..............................2 Installing a PS/2 CueCat on a laptop (Windows and Linux)..............................................4 Installing a USB CueCat (Windows, Mac OS X and Linux)..............................................5 How to Swipe a Barcode..................................................................................................6 Troubleshooting................................................................................................................7 Readerware CueCat Manual v1.04 Page: 1 Installing a PS/2 CueCat on a desktop machine (Windows and Linux) Note: Before you begin, shut down all programs and turn off your computer. If you are installing the CueCat reader on a laptop computer, proceed to the next section. Disconnect the keyboard cable from your computer. The CueCat reader operates through the keyboard port. Make sure you do not use the mouse port. If the keyboard port on your computer doesn©t match the male connector on the CueCat reader, you can get adapters at any computer store or Radio Shack. Readerware CueCat Manual v1.04 Page: 2 Connect the male connector on the CueCat reader into the computer©s keyboard port. Match up the "notch key" for easy insertion. (Note: the male connector is the one with the protruding pins.) Connect the keyboard cable to the female connector on the CueCat reader. -

Cognitive Programming Language (CPL) Programmer's Guide
Cognitive Programming Language (CPL) Programmer's Guide 105-008-02 Revision C2 – 3/17/2006 *105-008-02* Copyright © 2006, Cognitive. Cognitive™, Cxi™, and Ci™ are trademarks of Cognitive. Microsoft® and Windows™ are trademarks of Microsoft Corporation. Other product and corporate names used in this document may be trademarks or registered trademarks of other companies, and are used only for explanation and to their owner’s benefit, without intent to infringe. All information in this document is subject to change without notice, and does not represent a commitment on the part of Cognitive. No part of this document may be reproduced for any reason or in any form, including electronic storage and retrieval, without the express permission of Cognitive. All program listings in this document are copyrighted and are the property of Cognitive and are provided without warranty. To contact Cognitive: Cognitive Solutions, Inc. 4403 Table Mountain Drive Suite A Golden, CO 80403 E-Mail: [email protected] Telephone: +1.800.525.2785 Fax: +1.303.273.1414 Table of Contents Introduction.............................................................................................. 1 Label Format Organization .................................................................. 2 Command Syntax................................................................................ 2 Important Programming Rules............................................................. 3 Related Publications........................................................................... -
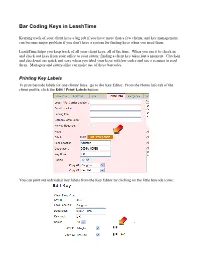
Bar Coding Keys in Leashtime
Bar Coding Keys in LeashTime Keeping track of your client keys a big job if you have more than a few clients, and key management can become major problem if you don't have a system for finding keys when you need them. LeashTime helps you keep track of all your client keys, all of the time. When you use it to check in and check out keys from your office to your sitters, finding a client key takes just a moment. Check-in and check-out are quick and easy when you label your keys with bar codes and use a scanner to read them. Managers and sitters alike can make use of these barcodes. Printing Key Labels To print barcode labels for one clients' keys, go to the Key Editor. From the Home Info tab of the client profile, click the Edit / Print Labels button: You can print out individual key labels from the Key Editor by clicking on the little barcode icons: You can save paper and time by printing out lots of key labels at once from the Key Location Report (KEYS > Key Location Report). Key Tags If you're going to print key labels, you will need key tags to slip the labels into. Search eBay for “key label tags” and you will find plenty of them. A tag that encases the label or protects the label from the elements with a window of plastic is a good idea. The largest size label tag that LeashTime currently prints labels for is sold under the Clik-It brand. -

A Compiler for a Simple Language. V0.16
Project step 1 – a compiler for a simple language. v0.16 Change log: v0.16, changes from 0.15 Make all push types in compiler actions explicit. Simplified and better documentation of call and callr instruction compiler actions. Let the print statement print characters and numbers. Added a printv statement to print variables. Changed compiler actions for retr to push a variable value, not a literal value. Changes are shown in orange. v0.15, changes from 0.14 Change compiler actions for ret, retr, jmp. Change the description and compiler actions for poke. Change the description for swp. Change the compiler actions for call and callr. Changes shown in green. v0.14, changes from 0.13 Add peek, poke and swp instructions. Change popm compiler actions. Change callr compiler actions. Other small changes to wording. Changes are shown in blue. v0.13, changes from 0.12 Add a count field to subr, call and callr to simplify code generation. Changes are shown in red. v0.12 Changes from 0.11. Added a callr statement that takes a return type. Fix the generated code for this and for call to allow arguments to be pushed by the call. Add a retr that returns a value and update the reg. v0.11: changes from 0.10. Put typing into push operators. Put opcodes for compare operators. fix actions for call. Make declarations reserve a stack location. Remove redundant store instruction (popv does the same thing.) v0.10: changes from 0.0. Comparison operators (cmpe, cmplt, cmpgt) added. jump conditional (jmpc) added. bytecode values added. -

Forest Quickstart Guide for Linguists
Forest Quickstart Guide for Linguists Guido Vanden Wyngaerd [email protected] June 28, 2020 Contents 1 Introduction 1 2 Loading Forest 2 3 Basic Usage 2 4 Adjusting node spacing 4 5 Triangles 7 6 Unlabelled nodes 9 7 Horizontal alignment of terminals 10 8 Arrows 11 9 Highlighting 14 1 Introduction Forest is a package for drawing linguistic (and other) tree diagrams de- veloped by Sašo Živanović. This manual provides a quickstart guide for linguists with just the essential things that you need to get started. More 1 extensive documentation is available from the CTAN-archive. Forest is based on the TikZ package; more information about its commands, in par- ticular those controlling the appearance of the nodes, the arrows, and the highlighting can be found in the TikZ documentation. 2 Loading Forest In your preamble, put \usepackage[linguistics]{forest} The linguistics option makes for nice trees, in which the branches meet above the two nodes that they join; it will also align the example number (provided by linguex) with the top of the tree: (1) CP C IP I VP V NP 3 Basic Usage Forest uses a familiar labelled brackets syntax. The code below will out- put the tree in (1) above (\ex. requires the linguex package and provides the example number): \ex. \begin{forest} [CP[C][IP[I][VP[V][NP]]]] \end{forest} Forest will parse the above code without problem, but you are likely to soon get lost in your labelled brackets with more complicated trees if you write the code this way. The better alternative is to arrange the nodes over multiple lines: 2 \ex. -

Metadata for Everyone a Simple, Low-Cost Methodology Timothy D
SAS Global Forum 2008 Data Integration Paper 138-2008 Metadata for Everyone A Simple, Low-Cost Methodology Timothy D. Brown, Altoona, IA ABSTRACT In the context of Base SAS® programming, this paper uses “hardcoded” values as an introduction to “metadata” and the reasons for using it. It then describes a low cost and simple methodology for maintaining any kind of metadata. INTRODUCTION This discussion will take an indirect approach to defining metadata. It’ll describe the metadata which might be included, or hard-coded, in a Base SAS program and propose alternatives to storing and using the metadata. Outside of programs “data” and “code” are distinct. However within programs, the distinction gets blurred when data values, called “hardcoded” data, are included within the code. Hardcoded values include, but are not limited to: • Text constants, literals • Names of companies, people, organizations and places • Directory paths and file names • Parameters on SAS procedures such as WHERE, KEEP, DROP, RENAME, VARS, BY etc • Numeric constants including dates* • Statistical constants • Period begin and end dates • Mixed text and numeric values • Expressions in IF and WHERE clauses • What-if scenarios (* excluding dates which are derived logically using a SAS functions such as TODAY(), DATETIME(), INTNX and NXTPD) In addition, many small conversion, cross-reference and look-up tables, which might be hardcoded as SAS formats or read into a program from many different sources, work well as metadata and fit into this framework. Obviously, some hardcoded values might never change in the life of a program. So it might be prudent to leave some hardcoded values in the code. -

Kiosk Barcode Reader
KBR2D Kiosk Barcode Reader KBR2D is the family of barcode scanners designed for self-service kiosks, ATMs, price checkers, healthcare and for any OEM application, also available in a plastic case version (KBR2D-C). KBR2D is a high-performance, high-volume omnidirectional scanner, capable of quickly and accurately reading any 1D and 2D barcodes, whether printed on paper (badges, receipts, health bracelets) or displayed on the screen of a smartphone or of a tablet. KBR2D scanners are based on CMOS technology for optimal image sensitivity and dynamic range. KBR2D integration is quick and easy thanks to several mounting options. www.custom.biz - [email protected] Follow us CHARACTERISTICS Easily integrated with various OEM applications 1D and 2D barcode scanning Omnidirectional scanning: no need to align barcode and scanner, ensuring user comfort and protecting productivity Long distance reading from 3 to 28 cm without problems even in direct sunlight (100,000 lux) Reading barcodes on screens of smartphones or tablets even with brightness reduced to 25/30% Red colored pointer for precise aiming and optimal barcode acquisition Flexibility: various external mounting options or internal screw holes Integrated decoder Custom ScannerSet configuration software DIMENSION: www.custom.biz - [email protected] Follow us www.custom.biz - [email protected] Follow us TECHNICAL SHEET KBR2D-C KBR2D GENERAL Interface USB-HID(or Virtual COM port) RS232/USB-HID(or Virtual COM port) UPC-A, UPC-E, EAN-8/JAN-8, EAN-13/JAN-13, Code 39, Code 128, Interleaved 25, Industrial -

Programming Basics - FORTRAN 77
CWCS Workshop May 2005 Programming Basics - FORTRAN 77 http://www.physics.nau.edu/~bowman/PHY520/F77tutor/tutorial_77.html Program Organization A FORTRAN program is just a sequence of lines of plain text. This is called the source code. The text has to follow certain rules (syntax) to be a valid FORTRAN program. We start by looking at a simple example: program circle real r, area, pi c This program reads a real number r and prints c the area of a circle with radius r. write (*,*) 'Give radius r:' read (*,*) r pi = atan(1.0e0)*4.0e0 area = pi*r*r write (*,*) 'Area = ', area end A FORTRAN program generally consists of a main program and possibly several subprograms (i.e., functions or subroutines). The structure of a main program is: program name declarations statements end Note: Words that are in italics should not be taken as literal text, but rather as a description of what belongs in their place. FORTRAN is not case-sensitive, so "X" and "x" are the same variable. Blank spaces are ignored in Fortran 77. If you remove all blanks in a Fortran 77 program, the program is still acceptable to a compiler but almost unreadable to humans. Column position rules Fortran 77 is not a free-format language, but has a very strict set of rules for how the source code should be formatted. The most important rules are the column position rules: Col. 1: Blank, or a "c" or "*" for comments Col. 1-5: Blank or statement label Col. 6: Blank or a "+" for continuation of previous line Col. -

NET Framework
Advanced Windows Programming .NET Framework based on: A. Troelsen, Pro C# 2005 and .NET 2.0 Platform, 3rd Ed., 2005, Apress J. Richter, Applied .NET Frameworks Programming, 2002, MS Press D. Watkins et al., Programming in the .NET Environment, 2002, Addison Wesley T. Thai, H. Lam, .NET Framework Essentials, 2001, O’Reilly D. Beyer, C# COM+ Programming, M&T Books, 2001, chapter 1 Krzysztof Mossakowski Faculty of Mathematics and Information Science http://www.mini.pw.edu.pl/~mossakow Advanced Windows Programming .NET Framework - 2 Contents The most important features of .NET Assemblies Metadata Common Type System Common Intermediate Language Common Language Runtime Deploying .NET Runtime Garbage Collection Serialization Krzysztof Mossakowski Faculty of Mathematics and Information Science http://www.mini.pw.edu.pl/~mossakow Advanced Windows Programming .NET Framework - 3 .NET Benefits In comparison with previous Microsoft’s technologies: Consistent programming model – common OO programming model Simplified programming model – no error codes, GUIDs, IUnknown, etc. Run once, run always – no "DLL hell" Simplified deployment – easy to use installation projects Wide platform reach Programming language integration Simplified code reuse Automatic memory management (garbage collection) Type-safe verification Rich debugging support – CLR debugging, language independent Consistent method failure paradigm – exceptions Security – code access security Interoperability – using existing COM components, calling Win32 functions Krzysztof -

Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor Matt Graeber
Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor Matt Graeber Black Hat 2015 Introduction As technology is introduced and subsequently deprecated over time in the Windows operating system, one powerful technology that has remained consistent since Windows NT 4.01 and Windows 952 is Windows Management Instrumentation (WMI). Present on all Windows operating systems, WMI is comprised of a powerful set of tools used to manage Windows systems both locally and remotely. While it has been well known and utilized heavily by system administrators since its inception, WMI was likely introduced to the mainstream security community when it was discovered that it was used maliciously as one component in the suite of exploits and implants used by Stuxnet3. Since then, WMI has been gaining popularity amongst attackers for its ability to perform system reconnaissance, AV and VM detection, code execution, lateral movement, persistence, and data theft. As attackers increasingly utilize WMI, it is important for defenders, incident responders, and forensic analysts to have knowledge of WMI and to know how they can wield it to their advantage. This whitepaper will introduce the reader to WMI, actual and proof-of-concept attacks using WMI, how WMI can be used as a rudimentary intrusion detection system (IDS), and how to perform forensics on the WMI repository file format. WMI Architecture 1 https://web.archive.org/web/20050115045451/http://www.microsoft.com/downloads/details.aspx?FamilyID=c17 4cfb1-ef67-471d-9277-4c2b1014a31e&displaylang=en 2 https://web.archive.org/web/20051106010729/http://www.microsoft.com/downloads/details.aspx?FamilyId=98A 4C5BA-337B-4E92-8C18-A63847760EA5&displaylang=en 3 http://poppopret.blogspot.com/2011/09/playing-with-mof-files-on-windows-for.html WMI is the Microsoft implementation of the Web-Based Enterprise Management (WBEM)4 and Common Information Model (CIM)5 standards published by the Distributed Management Task Force (DMTF)6.