Words – Components, Efficiency, Metrics, Objects, Reuse, Specification
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CS321 Spring 2021
CS321 Spring 2021 Lecture 2 Jan 13 2021 Admin • A1 Due next Saturday Jan 23rd – 11:59PM Course in 4 Sections • Section I: Basics and Sorting • Section II: Hash Tables and Basic Data Structs • Section III: Binary Search Trees • Section IV: Graphs Section I • Sorting methods and Data Structures • Introduction to Heaps and Heap Sort What is Big O notation? • A way to approximately count algorithm operations. • A way to describe the worst case running time of algorithms. • A tool to help improve algorithm performance. • Can be used to measure complexity and memory usage. Bounds on Operations • An algorithm takes some number of ops to complete: • a + b is a single operation, takes 1 op. • Adding up N numbers takes N-1 ops. • O(1) means ‘on order of 1’ operation. • O( c ) means ‘on order of constant’. • O( n) means ‘ on order of N steps’. • O( n2) means ‘ on order of N*N steps’. How Does O(k) = O(1) O(n) = c * n for some c where c*n is always greater than n for some c. O( k ) = c*k O( 1 ) = cc * 1 let ccc = c*k c*k = c*k* 1 therefore O( k ) = c * k * 1 = ccc *1 = O(1) O(n) times for sorting algorithms. Technique O(n) operations O(n) memory use Insertion Sort O(N2) O( 1 ) Bubble Sort O(N2) O(1) Merge Sort N * log(N) O(1) Heap Sort N * log(N) O(1) Quicksort O(N2) O(logN) Memory is in terms of EXTRA memory Primary Notation Types • O(n) = Asymptotic upper bound. -
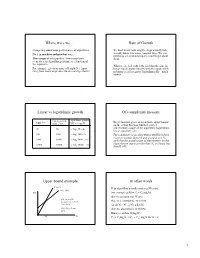
Rate of Growth Linear Vs Logarithmic Growth O() Complexity Measure
Where were we…. Rate of Growth • Comparing worst case performance of algorithms. We don't know how long the steps actually take; we only know it is some constant time. We can • Do it in machine-independent way. just lump all constants together and forget about • Time usage of an algorithm: how many basic them. steps does an algorithm perform, as a function of the input size. What we are left with is the fact that the time in • For example: given an array of length N (=input linear search grows linearly with the input, while size), how many steps does linear search perform? in binary search it grows logarithmically - much slower. Linear vs logarithmic growth O() complexity measure Linear growth: Logarithmic growth: Input size T(N) = c log N Big O notation gives an asymptotic upper bound T(N) = N* c 2 on the actual function which describes 10 10c c log 10 = 4c time/memory usage of the algorithm: logarithmic, 2 linear, quadratic, etc. 100 100c c log2 100 = 7c The complexity of an algorithm is O(f(N)) if there exists a constant factor K and an input size N0 1000 1000c c log2 1000 = 10c such that the actual usage of time/memory by the 10000 10000c c log 10000 = 16c algorithm on inputs greater than N0 is always less 2 than K f(N). Upper bound example In other words f(N)=2N If an algorithm actually makes g(N) steps, t(N)=3+N time (for example g(N) = C1 + C2log2N) there is an input size N' and t(N) is in O(N) because for all N>3, there is a constant K, such that 2N > 3+N for all N > N' , g(N) ≤ K f(N) Here, N0 = 3 and then the algorithm is in O(f(N). -

Comparing the Heuristic Running Times And
Comparing the heuristic running times and time complexities of integer factorization algorithms Computational Number Theory ! ! ! New Mexico Supercomputing Challenge April 1, 2015 Final Report ! Team 14 Centennial High School ! ! Team Members ! Devon Miller Vincent Huber ! Teacher ! Melody Hagaman ! Mentor ! Christopher Morrison ! ! ! ! ! ! ! ! ! "1 !1 Executive Summary....................................................................................................................3 2 Introduction.................................................................................................................................3 2.1 Motivation......................................................................................................................3 2.2 Public Key Cryptography and RSA Encryption............................................................4 2.3 Integer Factorization......................................................................................................5 ! 2.4 Big-O and L Notation....................................................................................................6 3 Mathematical Procedure............................................................................................................6 3.1 Mathematical Description..............................................................................................6 3.1.1 Dixon’s Algorithm..........................................................................................7 3.1.2 Fermat’s Factorization Method.......................................................................7 -

Big-O Notation
The Growth of Functions and Big-O Notation Introduction Note: \big-O" notation is a generic term that includes the symbols O, Ω, Θ, o, !. Big-O notation allows us to describe the aymptotic growth of a function f(n) without concern for i) constant multiplicative factors, and ii) lower-order additive terms. By asymptotic growth we mean the growth of the function as input variable n gets arbitrarily large. As an example, consider the following code. int sum = 0; for(i=0; i < n; i++) for(j=0; j < n; j++) sum += (i+j)/6; How much CPU time T (n) is required to execute this code as a function of program variable n? Of course, the answer will depend on factors that may be beyond our control and understanding, including the language compiler being used, the hardware of the computer executing the program, the computer's operating system, and the nature and quantity of other programs being run on the computer. However, we can say that the outer for loop iterates n times and, for each of those iterations, the inner loop will also iterate n times for a total of n2 iterations. Moreover, for each iteration will require approximately a constant number c of clock cycles to execture, where the number of clock cycles varies with each system. So rather than say \T (n) is approximately cn2 nanoseconds, for some constant c that will vary from person to person", we instead use big-O notation and write T (n) = Θ(n2) nanoseconds. This conveys that the elapsed CPU time will grow quadratically with respect to the program variable n. -

13.7 Asymptotic Notation
“mcs” — 2015/5/18 — 1:43 — page 528 — #536 13.7 Asymptotic Notation Asymptotic notation is a shorthand used to give a quick measure of the behavior of a function f .n/ as n grows large. For example, the asymptotic notation of ⇠ Definition 13.4.2 is a binary relation indicating that two functions grow at the same rate. There is also a binary relation “little oh” indicating that one function grows at a significantly slower rate than another and “Big Oh” indicating that one function grows not much more rapidly than another. 13.7.1 Little O Definition 13.7.1. For functions f; g R R, with g nonnegative, we say f is W ! asymptotically smaller than g, in symbols, f .x/ o.g.x//; D iff lim f .x/=g.x/ 0: x D !1 For example, 1000x1:9 o.x2/, because 1000x1:9=x2 1000=x0:1 and since 0:1 D D 1:9 2 x goes to infinity with x and 1000 is constant, we have limx 1000x =x !1 D 0. This argument generalizes directly to yield Lemma 13.7.2. xa o.xb/ for all nonnegative constants a<b. D Using the familiar fact that log x<xfor all x>1, we can prove Lemma 13.7.3. log x o.x✏/ for all ✏ >0. D Proof. Choose ✏ >ı>0and let x zı in the inequality log x<x. This implies D log z<zı =ı o.z ✏/ by Lemma 13.7.2: (13.28) D ⌅ b x Corollary 13.7.4. -

Binary Search
UNIT 5B Binary Search 15110 Principles of Computing, 1 Carnegie Mellon University - CORTINA Course Announcements • Sunday’s review sessions at 5‐7pm and 7‐9 pm moved to GHC 4307 • Sample exam available at the SCHEDULE & EXAMS page http://www.cs.cmu.edu/~15110‐f12/schedule.html 15110 Principles of Computing, 2 Carnegie Mellon University - CORTINA 1 This Lecture • A new search technique for arrays called binary search • Application of recursion to binary search • Logarithmic worst‐case complexity 15110 Principles of Computing, 3 Carnegie Mellon University - CORTINA Binary Search • Input: Array A of n unique elements. – The elements are sorted in increasing order. • Result: The index of a specific element called the key or nil if the key is not found. • Algorithm uses two variables lower and upper to indicate the range in the array where the search is being performed. – lower is always one less than the start of the range – upper is always one more than the end of the range 15110 Principles of Computing, 4 Carnegie Mellon University - CORTINA 2 Algorithm 1. Set lower = ‐1. 2. Set upper = the length of the array a 3. Return BinarySearch(list, key, lower, upper). BinSearch(list, key, lower, upper): 1. Return nil if the range is empty. 2. Set mid = the midpoint between lower and upper 3. Return mid if a[mid] is the key you’re looking for. 4. If the key is less than a[mid], return BinarySearch(list,key,lower,mid) Otherwise, return BinarySearch(list,key,mid,upper). 15110 Principles of Computing, 5 Carnegie Mellon University - CORTINA Example -

The History of Algorithmic Complexity
City University of New York (CUNY) CUNY Academic Works Publications and Research Borough of Manhattan Community College 2016 The history of Algorithmic complexity Audrey A. Nasar CUNY Borough of Manhattan Community College How does access to this work benefit ou?y Let us know! More information about this work at: https://academicworks.cuny.edu/bm_pubs/72 Discover additional works at: https://academicworks.cuny.edu This work is made publicly available by the City University of New York (CUNY). Contact: [email protected] The Mathematics Enthusiast Volume 13 Article 4 Number 3 Number 3 8-2016 The history of Algorithmic complexity Audrey A. Nasar Follow this and additional works at: http://scholarworks.umt.edu/tme Part of the Mathematics Commons Recommended Citation Nasar, Audrey A. (2016) "The history of Algorithmic complexity," The Mathematics Enthusiast: Vol. 13: No. 3, Article 4. Available at: http://scholarworks.umt.edu/tme/vol13/iss3/4 This Article is brought to you for free and open access by ScholarWorks at University of Montana. It has been accepted for inclusion in The Mathematics Enthusiast by an authorized administrator of ScholarWorks at University of Montana. For more information, please contact [email protected]. TME, vol. 13, no.3, p.217 The history of Algorithmic complexity Audrey A. Nasar1 Borough of Manhattan Community College at the City University of New York ABSTRACT: This paper provides a historical account of the development of algorithmic complexity in a form that is suitable to instructors of mathematics at the high school or undergraduate level. The study of algorithmic complexity, despite being deeply rooted in mathematics, is usually restricted to the computer science curriculum. -

1 Computational Complexity and Big-O Notation
1 Computational complexity and big-O notation References: [Ros11] The time that algorithms take to solve problems depends on the implementation, the software, the hardware, and a whole host of factors. We use big-O notation as a way of simplifying the running time of an algorithm based on the size of its input. The notation allows us to talk about algorithms at a higher level and estimate how implementations of algorithms will behave. We will use big-O notation extensively in this refresher course. We use big O notation as a way of expressing an asymptotic upper bound on a function. We say that a function f is O(g) if the rate of growth of f is less than or equal to the rate of growth of g (up to a constant). More formally: Definition 1.1. Let f, g: R ! R. We say that f is O(g) if there are positive constants c and N such that for x > N, jf(x)j ≤ cjg(x)j. Example 1.2. The number of multiplications and additions needed to multiply two n × n matrices together is n2(2n − 1), which is O(n3). To see Example 1.2, let f(n) = n2(2n − 1) and g(n) = n3. Choose N = 1 and c = 2. For n > N, f(n) = 2n3 − n2 < 2n3 = cg(n). A general advantage of big-O notation is that we can ignore the \lower order terms": k k Example 1.3. Let a0, a1, : : : ; ak be real numbers. Then f(x) = a0 + a1x + : : : akx is O(x ). -

Binary Search Algorithm Anthony Lin¹* Et Al
WikiJournal of Science, 2019, 2(1):5 doi: 10.15347/wjs/2019.005 Encyclopedic Review Article Binary search algorithm Anthony Lin¹* et al. Abstract In In computer science, binary search, also known as half-interval search,[1] logarithmic search,[2] or binary chop,[3] is a search algorithm that finds a position of a target value within a sorted array.[4] Binary search compares the target value to an element in the middle of the array. If they are not equal, the half in which the target cannot lie is eliminated and the search continues on the remaining half, again taking the middle element to compare to the target value, and repeating this until the target value is found. If the search ends with the remaining half being empty, the target is not in the array. Binary search runs in logarithmic time in the worst case, making 푂(log 푛) comparisons, where 푛 is the number of elements in the array, the 푂 is ‘Big O’ notation, and 푙표푔 is the logarithm.[5] Binary search is faster than linear search except for small arrays. However, the array must be sorted first to be able to apply binary search. There are spe- cialized data structures designed for fast searching, such as hash tables, that can be searched more efficiently than binary search. However, binary search can be used to solve a wider range of problems, such as finding the next- smallest or next-largest element in the array relative to the target even if it is absent from the array. There are numerous variations of binary search. -

Algorithm Efficiency and Sorting
Measuring the Efficiency of Chapter 10 Algorithms • Analysis of algorithms – contrasts the efficiency of different methods of solution Algorithm Efficiency and • A comparison of algorithms Sorting – Should focus of significant differences in efficiency – Should not consider reductions in computing costs due to clever coding tricks © 2006 Pearson Addison-Wesley. All rights reserved 10 A-1 © 2006 Pearson Addison-Wesley. All rights reserved 10 A-2 The Execution Time of Algorithm Growth Rates Algorithms • Counting an algorithm's operations is a way to • An algorithm’s time requirements can be access its efficiency measured as a function of the input size – An algorithm’s execution time is related to the number of operations it requires • Algorithm efficiency is typically a concern for large data sets only © 2006 Pearson Addison-Wesley. All rights reserved 10 A-3 © 2006 Pearson Addison-Wesley. All rights reserved 10 A-4 Order-of-Magnitude Analysis and Algorithm Growth Rates Big O Notation • Definition of the order of an algorithm Algorithm A is order f(n) – denoted O(f(n)) – if constants k and n0 exist such that A requires no more than k * f(n) time units to solve a problem of size n ! n0 • Big O notation – A notation that uses the capital letter O to specify an algorithm’s order Figure 10-1 – Example: O(f(n)) Time requirements as a function of the problem size n © 2006 Pearson Addison-Wesley. All rights reserved 10 A-5 © 2006 Pearson Addison-Wesley. All rights reserved 10 A-6 Order-of-Magnitude Analysis and Order-of-Magnitude Analysis and Big O Notation Big O Notation • Order of growth of some common functions 2 3 n O(1) < O(log2n) < O(n) < O(nlog2n) < O(n ) < O(n ) < O(2 ) • Properties of growth-rate functions – You can ignore low-order terms – You can ignore a multiplicative constant in the high- order term – O(f(n)) + O(g(n)) = O(f(n) + g(n)) Figure 10-3b A comparison of growth-rate functions: b) in graphical form © 2006 Pearson Addison-Wesley. -

Sorting Algorithm 1 Sorting Algorithm
Sorting algorithm 1 Sorting algorithm A sorting algorithm is an algorithm that puts elements of a list in a certain order. The most-used orders are numerical order and lexicographical order. Efficient sorting is important for optimizing the use of other algorithms (such as search and merge algorithms) which require input data to be in sorted lists; it is also often useful for canonicalizing data and for producing human-readable output. More formally, the output must satisfy two conditions: 1. The output is in nondecreasing order (each element is no smaller than the previous element according to the desired total order); 2. The output is a permutation (reordering) of the input. Since the dawn of computing, the sorting problem has attracted a great deal of research, perhaps due to the complexity of solving it efficiently despite its simple, familiar statement. For example, bubble sort was analyzed as early as 1956.[1] Although many consider it a solved problem, useful new sorting algorithms are still being invented (for example, library sort was first published in 2006). Sorting algorithms are prevalent in introductory computer science classes, where the abundance of algorithms for the problem provides a gentle introduction to a variety of core algorithm concepts, such as big O notation, divide and conquer algorithms, data structures, randomized algorithms, best, worst and average case analysis, time-space tradeoffs, and upper and lower bounds. Classification Sorting algorithms are often classified by: • Computational complexity (worst, average and best behavior) of element comparisons in terms of the size of the list (n). For typical serial sorting algorithms good behavior is O(n log n), with parallel sort in O(log2 n), and bad behavior is O(n2). -

Big O Complexity
CS106B Handout Big O Complexity As we discussed in class, computer scientists use a special shorthand called big-O notation to denote the computational complexity of algorithms. When using big-O notation, the goal is to provide a qualitative insight as to how changes in N affect how many units of computation are performed for large amounts of data. Therefore, when computing big-O, we can make the following simplifications: 1. Eliminate any term whose contribution to the total is insignificant as N becomes large �(�! + �) = �(�!) for large n 2. Eliminate any constant factors �(3�) = � � for large n To compute big-O, it we think about the number of executions that the code will perform in the worst case scenario. The stragegy for computing Big-O depends on whether or not your program is recursive. For the case of iterative solutions, we try and count the number of executions that are performed. For the case of recursive solutions, we first try and compute the number of recursive calls that are performed. Basic Examples Code Complexity for (int x = n; x >= 0; x--) { �(�) cout << x << endl; } The loop executes n times for (int i = 0; i < 5; i++) { �(1) for (int j = 0; j < 10; j++) { cout << j << endl; Neither loop depends on the value n } } for (int i = 0; i < n; i++) { �(�!) for (int j = 0; j < n; j++) { cout << j << endl; The outer loop executes n times and each iteration, the inner loop executes } n times, totaling in �! loops } for (int i = 0; i < 5n; i++) { �(�) cout << “hello!” << endl; } The loop executes 5n times and the constant 5 is insignificant as n grows for (int i = 0; i < n; i++) { �(�!) for (int j = 0; j < n*n; j++) { cout << “tricky!” << endl; The outer loop executes n times and each iteration, the inner loop executes } �! times, totaling in �!executions } Gauss Summation In many situations you have a case where you have a code block which executes 1 time, then 2 times, then 3 times until n times.