Andrea M. Matwyshyn* & Stephanie K. Pell
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Internet Security THREAT REPORT GOVERNMENT 2013 P
2012 Trends, Volume 18, Published April 2013 INTERNET SECURITY THREAT REPORT GOVERNMENT 2013 p. 2 Symantec Corporation Internet Security Threat Report 2013 :: Volume 18 CONTENTS 03 Introduction 31 Social Networking, Mobile, and the Cloud 04 Executive Summary 32 Introduction 32 Data 06 2012 Security Timeline 35 Analysis 09 2012 in Numbers 35 Spam and Phishing Move to Social Media 37 Mobile Threats 13 Targeted Attacks, Hacktivism, and Data Breaches 38 Cloud Computing Risks 14 Introduction 14 Data 40 Malware, Spam, and Phishing 17 DDoS Used as a Diversion 41 Introduction 17 Data Breaches 42 Data 19 Analysis 42 Spam 19 Cyberwarfare, Cybersabotage, and Industrial Espionage 45 Phishing 20 Advanced Persistent Threats and Targeted Attacks 46 Malware 20 Social Engineering and Indirect Attacks 48 Website Exploits by Type of Website 21 Watering Hole Attacks 49 Analysis 49 Macs Under Attack 23 Vulnerabilities, Exploits, and Toolkits 50 Rise of Ransomware 24 Introduction 51 Long-term Stealthy Malware 24 Data 51 Email Spam Volume Down 26 Analysis 51 Advanced Phishing 26 Web-based Attacks on the Rise 27 The Arms Race to Exploit New Vulnerabilities 53 Looking ahead 27 Malvertising and Website Hacking 56 Endnotes 28 Web Attack Toolkits 57 Appendix 29 Website Malware Scanning and Website Vulnerability Assessment 29 The Growth of Secured Connections 29 Norton Secured Seal and Trust Marks 29 Stolen Key-signing Certificates p. 3 Symantec Corporation Internet Security Threat Report 2013 :: Volume 18 Introduction Symantec has established some of the most In addition, Symantec maintains one of the world’s most comprehensive vulnerability databases, currently consisting of comprehensive sources of Internet threat more than 51,644 recorded vulnerabilities (spanning more than data in the world through the Symantec™ two decades) from over 16,687 vendors representing over 43,391 Global Intelligence Network, which is made products. -

Digital Transformation: Cure-All, Placebo Or Poison Pill? Leonidas Tougiannidis Country Manager, Greece & Cyprus
Digital Transformation: Cure-all, Placebo or Poison Pill? Leonidas Tougiannidis Country Manager, Greece & Cyprus © Copyright Fortinet Inc. All rights reserved. IT Trends increase the ATTACK SURFACE & LIABILITIES ▪ Digital Transformation entails sharing data ▪ IoT brings 20 Billion new Devices Online ▪ Cloud breaks the Borders ▪ Mobility Disperses Users and Data ▪ SD-WAN stretchers enterprise networks ▪ Regulations (ie GDPR, PCI-DSS, PSD2) 2 [Digital Transformation] is the integration of digital technology into all areas of a business, resulting in fundamental changes to how businesses operate and how they deliver value to customers 3 Digital Transformation Digital Transformation Engage Your Empower Your Optimize Your Transform Your Customers Employees Business Products Digital Technology 4 Real Life Digital Transformation From 140-year old manufacturing company: Digital Transformation Goals – 2020: Top 10 Global Energy, Transportation, Healthcare Software Company – $15B Digital Revenue 5 Obstacles to Digital Transformation Security is the largest factor standing in the way of enterprise digital transformation efforts. More than half (55%) of companies said that security was the No. 1 challenge they face when implementing digital enablement technologies Source: SoftServe 2017 Cybersecurity one of Top 10 “Security nearly always tops the list of obstacles to Digital Transformation digital transformation obstacles”. Source:Harvard Business Review 2017 Marc Cecere, Forrester, ZD Net, 2017 The biggest disruptive technologies Some 57% of businesses reported cited by global respondents are the major issues finding and recruiting cloud (58%), mobility and talented IT security staff—a problem collaboration (54%), big data as digital transformation efforts (52%)...IoT (43%) move more data and systems to the cloud, and cyber attacks grow more Source: BT CIO Report 2016 sophisticated. -

BEGIN README.TXT-- PC Media Antivirus (PCMAV)
--BEGIN README.TXT-- PC Media Antivirus (PCMAV) 9.9.1 Copyright (c) 2006-2014 Majalah PC Media Pinpoint Publications Group ************************************************************************ MEMANFAATKAN/MENGGUNAKAN PCMAV BERARTI ANDA MENGERTI DAN SETUJU DENGAN SELURUH KETENTUAN YANG ADA DI BAGIAN "KETENTUAN PENGGUNAAN (END-USER LICENSE)" YANG TERDAPAT PADA FILE README.TXT INI. PCMAV INI DIBUAT KHUSUS DAN DIPERSEMBAHKAN BAGI "PEMBACA SETIA" PC MEDIA DAN YANG KAMI CINTAI. MAKA DARI ITU, JIKA ANDA ADALAH PENGGUNA PEMULA DAN ATAU MERASA KESULITAN MEMAHAMI ISI README.TXT INI, BAIK SEBAGIAN MAUPUN SECARA KESELURUHAN, MAKA KAMI SANGAT MENYARANKAN ANDA UNTUK BERKONSULTASI TERLEBIH DULU DENGAN REKAN ANDA YANG LEBIH BERPENGALAMAN DALAM BERKOMPUTER. ATAU DEMI KENYAMANAN ANDA, MAKA KAMI SARANKAN UNTUK TIDAK MENGGUNAKAN PCMAV SAMA SEKALI. ************************************************************************ ------------------------------ ANTIVIRUS KEBANGGAAN INDONESIA ------------------------------ Tidak ada antivirus lain yang mampu mengatasi secara tuntas virus komputer, baik lokal maupun asing, yang banyak menyebar di Indonesia sebaik dan seaman PCMAV. Umumnya antivirus yang ada hanya mampu mengenali dan menghapus file yang dideteksi bervirus. PCMAV menyempurnakannya dengan tingkat akurasi pendeteksian yang lebih tinggi, sehingga lebih handal dalam mengembalikan file, dokumen dan sistem yang menjadi sasaran serangan virus hingga pulih 100%. Dengan PCMAV, Anda akan mendapatkan antivirus yang bukan hanya sekadar mendeteksi namun daya basminya -

Coordinating Across Chaos: the Practice of Transnational Internet Security Collaboration
COORDINATING ACROSS CHAOS: THE PRACTICE OF TRANSNATIONAL INTERNET SECURITY COLLABORATION A Dissertation Presented to The Academic Faculty by Tarun Chaudhary In Partial Fulfillment of the Requirements for the Degree International Affairs, Science, and Technology in the Sam Nunn School of International Affairs Georgia Institute of Technology May 2019 COPYRIGHT © 2019 BY TARUN CHAUDHARY COORDINATING ACROSS CHAOS: THE PRACTICE OF TRANSNATIONAL INTERNET SECURITY COLLABORATION Approved by: Dr. Adam N. Stulberg Dr. Peter K. Brecke School of International Affairs School of International Affairs Georgia Institute of Technology Georgia Institute of Technology Dr. Michael D. Salomone Dr. Milton L. Mueller School of International Affairs School of Public Policy Georgia Institute of Technology Georgia Institute of Technology Dr. Jennifer Jordan School of International Affairs Georgia Institute of Technology Date Approved: March 11, 2019 ACKNOWLEDGEMENTS I was once told that writing a dissertation is lonely experience. This is only partially true. The experience of researching and writing this work has been supported and encouraged by a small army of individuals I am forever grateful toward. My wife Jamie, who has been a truly patient soul and encouraging beyond measure while also being my intellectual sounding board always helping guide me to deeper insight. I have benefited from an abundance of truly wonderful teachers over the course of my academic life. Dr. Michael Salomone who steered me toward the world of international security studies since I was an undergraduate, I am thankful for his wisdom and the tremendous amount of support he has given me over the past two decades. The rest of my committee has been equally as encouraging and provided me with countless insights as this work has been gestating and evolving. -

APCERT Annual Report 2012
AAPPCCEERRTT AAnnnnuuaall RReeppoorrtt 22001122 APCERT Secretariat E-mail: [email protected] URL: http://www.apcert.org 1 CONTENTS CONTENTS ........................................................................................................................... 2 Chair’s Message 2012 ............................................................................................................ 4 I. About APCERT ................................................................................................................... 6 II. APCERT Activity Report 2012 ...................................................................................... 12 1. International Activities and Engagements 12 2. Approval of New General Members / Full Members 16 3. APCERT SC Meetings 16 4. APCERT Study Calls 16 5. APCERT Information Classification Policy 17 III. Activity Reports from APCERT Members ................................................................... 18 Full Members 18 1. AusCERT Activity Report 18 2. BKIS Activity Report 20 3. BruCERT Activity Report 24 4. CERT Australia Activity Report 30 5. CERT-In Activity Report 35 6. CNCERT/CC Activity Report 47 7. HKCERT Activity Report 55 8. ID-CERT Activity Report 61 9. ID-SIRTII/CC Activity Report 71 10. JPCERT/CC Activity Report 78 11. KrCERT/CC Activity Report 86 12. MyCERT Activity Report 91 13. SingCERT Activity Report 99 14. Sri Lanka CERT|CC Activity Report 102 15. TechCERT Activity Report 113 16. ThaiCERT Activity Report 122 2 17. TWCERT/CC Activity Report 131 18. VNCERT Activity Report 142 General Members 146 19. bdCERT Activity Report 146 20. EC-CERT Activity Report 150 21. mmCERT Activity Report 154 22. MOCERT Activity Report 160 23. MonCIRT Activity Report 168 24. NCSC Activity Report 179 3 Chair’s Message 2012 The history of CERTs began in 1989 as a result of the Morris worm. As Internet expanded globally, CERTs began to form within the Asia Pacific region and quickly it became clear that collaboration to address challenges that went beyond individual national borders would become essential. -

Threatblogger Footsloggers Review 2012
December 2012 Feature Article: ThreatBlogger FootSloggers Review 2012 Table of Contents ThreatBlogger FootSloggers Review 2012 ..................................................................................................................3 ESET Papers and Articles in 2012............................................................................................................................. 10 The Top Ten Threats of 2012 ................................................................................................................................... 12 Top Ten Threats at a Glance (graph) ....................................................................................................................... 15 About ESET .............................................................................................................................................................. 16 Additional resources ................................................................................................................................................ 16 ThreatBlogger FootSloggers Of course, other social media were targeted too, as Stephen Review 2012 pointed out in Tricky Twitter DM hack seeks your credentials, malware infection, and more. David Harley, ESET Senior Research Fellow In fact, scams were a very prominent feature of the January 2012 on the ThreatBlog was far too busy to do justice to in a threatscape: the first blog of the year, with some input from fairly short article: inevitably, I’ll have to leave out some ESET Ireland’s -

Early Warning Factor of Cyber Threats Intelligence Fusion
ISACA Conference – 23rd of October 2013 – Riga - Latvia • Trustworthy Computing @ 10 Years • Security Development Lifecycle • Digital Crimes Unit • Government Security Program • Security Cooperation Program • Cyber Defense – Technology View Infrastructure Impact Global Services Targeted Resources Trustworthy Computing Security • Security Science • Microsoft Security Response Center Microsoft Malware Prevention Center • Malware analysis • Anti-malware capabilities Microsoft Product Development • Product architecture & engineering insight Customer Service & Support - Cybersecurity • Diagnosis and technical investigation • IT ecosystem viewpoint Global view to Global Cyber Threats – Microsoft Intelligence – SIR Report vol. 14 more than 5 times Scenario 1: malware disables real-time Scenario 2: user disables real-time antimalware Scenario 3: subscription lapses antimalware to ‘stay quiet’ because of perceived performance improvements 16.0 14.0 12.0 10.0 8.0 6.0 4.0 2.0 0.0 July August September October November December 32 32 32 64 Windows Vista SP2 Unprotected Windows Vista SP2 Protected • Using up-to-date real-time security software is an important part of a defense in depth strategy • Simply installing and using up-to-date real-time antimalware software can help individuals and organizations reduce the risk they face from malware by more than 80 percent • The statistics presented here are generated by Microsoft security programs and services running on computers in Slovakia in 4Q12 and previous quarters. This data is provided from administrators -
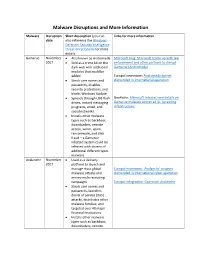
Malware Disruptions and More Information
Malware Disruptions and More Information Malware Disruption Short description (you can Links for more information date also reference the Windows Defender Security Intelligence threat encyclopedia for more details Gamarue November • Also known as Andromeda Microsoft blog: Microsoft teams up with law 2017 • Sold as a crime kit on the enforcement and other partners to disrupt dark web with additional Gamarue (Andromeda) modules that could be added Europol newsroom: Andromeda botnet • Steals user names and dismantled in international operation passwords, disables security protections, and blocks Windows Update • Spreads through USB flash Geekwire: Microsoft releases new details on drives, instant messaging Gamarue malware botnet ad its 'sprawling programs, email, and infrastructure' social networks • Installs other malware types such as backdoor, downloaders, remote access, worm, spam, ransomware, and click fraud – a Gamarue infected system could be infected with dozens of additional different types malware Avalanche November • Used as a delivery 2017 platform to launch and manage mass global Europol newsroom: 'Avalanche' network malware attacks and dismantled in international cyber operation money mule recruiting campaigns Europol infographic: Operation Avalanche • Steals user names and passwords, launches denial of service (DoS) attacks, distributes other malware families, and targeted over 40 major financial institutions • Installs other malware types such as backdoor, downloaders, remote access, worm, spam, and click fraud Barium November -

Civil Cyberconflict: Microsoft, Cybercrime, and Botnets Janine S
Santa Clara High Technology Law Journal Volume 31 | Issue 2 Article 1 January 2014 Civil Cyberconflict: Microsoft, Cybercrime, and Botnets Janine S. Hiller Follow this and additional works at: http://digitalcommons.law.scu.edu/chtlj Part of the Intellectual Property Law Commons, and the Science and Technology Law Commons Recommended Citation Janine S. Hiller, Civil Cyberconflict: Microsoft, yC bercrime, and Botnets, 31 Santa Clara High Tech. L.J. 163 (2015). Available at: http://digitalcommons.law.scu.edu/chtlj/vol31/iss2/1 This Article is brought to you for free and open access by the Journals at Santa Clara Law Digital Commons. It has been accepted for inclusion in Santa Clara High Technology Law Journal by an authorized administrator of Santa Clara Law Digital Commons. For more information, please contact [email protected]. 08_ARTICLE_HILLER (DO NOT DELETE) 5/27/2015 1:51 PM CIVIL CYBERCONFLICT: MICROSOFT, CYBERCRIME, AND BOTNETS Janine S. Hiller† Cyber “warfare” and hackback by private companies is a hot discussion topic for its potential to fight cybercrime and promote cybersecurity. In the shadow of this provocative discussion, Microsoft has led a concerted, sustained fight against cybercriminals by using traditional legal theories and court actions to dismantle criminal networks known as botnets. This article brings focus to the role of the private sector in cybersecurity in light of the aggressive civil actions by Microsoft to address a thorny and seemingly intractable global problem. A botnet is a network of computers infected with unauthorized code that is controlled from a distance by malicious actors. The extent of botnet activity is staggering, and botnets have been called the plague of the Internet. -

Lutte Contre Les Botnets : Analyse Et Stratégie Eric Freyssinet
Lutte contre les botnets : analyse et stratégie Eric Freyssinet To cite this version: Eric Freyssinet. Lutte contre les botnets : analyse et stratégie. Cryptographie et sécurité [cs.CR]. Université Pierre et Marie Curie - Paris VI, 2015. Français. NNT : 2015PA066390. tel-01231974v3 HAL Id: tel-01231974 https://tel.archives-ouvertes.fr/tel-01231974v3 Submitted on 15 Feb 2016 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. THÈSE DE DOCTORAT DE L’UNIVERSITÉ PIERRE ET MARIE CURIE Spécialité Informatique École doctorale Informatique, Télécommunications et Électronique (Paris) Présentée par Éric FREYSSINET Pour obtenir le grade de DOCTEUR DE L’UNIVERSITÉ PIERRE ET MARIE CURIE Sujet de la thèse : Lutte contre les botnets : analyse et stratégie Présentée et soutenue publiquement le 12 novembre 2015 devant le jury composé de : Rapporteurs : M. Jean-Yves Marion Professeur, Université de Lorraine M. Ludovic Mé Enseignant-chercheur, Supélec Rennes Directeurs : M. David Naccache Professeur, École normale supérieure de thèse M. Matthieu Latapy Directeur de recherche, UPMC, LIP6 Examinateurs : Mme Clémence Magnien Directrice de recherche, UPMC, LIP6 Mme Solange Ghernaouti-Hélie Professeure, Université de Lausanne M. Vincent Nicomette Professeur, INSA Toulouse Cette thèse est dédiée à M. -

Beheading Hydras: Performing Effective Botnet Takedowns
Beheading Hydras: Performing Effective Botnet Takedowns Yacin Nadji Manos Antonakakis Roberto Perdisci College of Computing Damballa, Inc. Department of Computer Georgia Institute of Atlanta, GA Science Technology [email protected] University of Georgia Atlanta, GA Athens, GA [email protected] [email protected] David Dagon Wenke Lee College of Computing College of Computing Georgia Institute of Georgia Institute of Technology Technology Atlanta, GA Atlanta, GA [email protected] [email protected] ABSTRACT Categories and Subject Descriptors Devices infected with malicious software typically form bot- K.6.m [Management of Computing and Information net armies under the influence of one or more command and Systems]: Security; K.5.m [Legal Aspects of Comput- control (C&C) servers. The botnet problem reached such ing]: Contracts levels where federal law enforcement agencies have to step in and take actions against botnets by disrupting (or \taking General Terms down") their C&Cs, and thus their illicit operations. Lately, more and more private companies have started to indepen- Botnets dently take action against botnet armies, primarily focusing on their DNS-based C&Cs. While well-intentioned, their Keywords C&C takedown methodology is in most cases ad-hoc, and botnet takedowns; takedown analysis; takedown policy limited by the breadth of knowledge available around the malware that facilitates the botnet. With this paper, we aim to bring order, measure, and 1. INTRODUCTION reason to the botnet takedown problem. We propose a Botnets represent a persistent threat to Internet security. takedown analysis and recommendation system, called rza, To effectively counter botnets, security researchers and law that allows researchers to perform two tasks: 1) a post- enforcement organizations have been recently relying more mortem analysis of past botnet takedowns, and 2) provide and more on botnet takedown operations. -

Éric FREYSSINET Lutte Contre Les Botnets : Analyse Et Stratégie
THÈSE DE DOCTORAT DE L’UNIVERSITÉ PIERRE ET MARIE CURIE Spécialité Informatique École doctorale Informatique, Télécommunications et Électronique (Paris) Présentée par Éric FREYSSINET Pour obtenir le grade de DOCTEUR DE L’UNIVERSITÉ PIERRE ET MARIE CURIE Sujet de la thèse : Lutte contre les botnets : analyse et stratégie Présentée et soutenue publiquement le 12 novembre 2015 devant le jury composé de : Rapporteurs : M. Jean-Yves Marion Professeur, Université de Lorraine M. Ludovic Mé Enseignant-chercheur, CentraleSupélec Directeurs : M. David Naccache Professeur, École normale supérieure de thèse M. Matthieu Latapy Directeur de recherche, UPMC, LIP6 Examinateurs : Mme Clémence Magnien Directrice de recherche, UPMC, LIP6 Mme Solange Ghernaouti-Hélie Professeure, Université de Lausanne M. Vincent Nicomette Professeur, INSA Toulouse Cette thèse est dédiée à M. Celui qui n’empêche pas un crime alors qu’il le pourrait s’en rend complice. — Sénèque Remerciements Je tiens à remercier mes deux directeurs de thèse. David Naccache, officier de réserve de la gendarmerie, contribue au développement de la recherche au sein de notre institution en poussant des personnels jeunes et un peu moins jeunes à poursuivre leur passion dans le cadre académique qui s’impose. Matthieu Latapy, du LIP6, avec qui nous avions pu échanger autour d’une thèse qu’il encadrait dans le domaine difficile des atteintes aux mineurs sur Internet et qui a accepté de m’accueillir dans son équipe. Je voudrais remercier aussi, l’ensemble de l’équipe Réseaux Complexes du LIP6 et sa responsable d’équipe actuelle, Clémence Magnien, qui m’ont accueilli à bras ouverts, accom- pagné à chaque étape et dont j’ai pu découvrir les thématiques et les méthodes de travail au fil des rencontres et des discussions.