Young,Gifted–Anddigitallysavvy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Symantec™ Encryption Desktop for Windows User's Guide
Symantec™ Encryption Desktop for Windows User's Guide 10.3 The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Version 10.3.2. Last updated: January 2014. Legal Notice Copyright (c) 2014 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Norton Zone, PGP, Pretty Good Privacy, and the PGP logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Java is a registered trademark of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. This Symantec product may contain third party software for which Symantec is required to provide attribution to the third party ("Third Party Programs"). Some of the Third Party Programs are available under open source or free software licenses. The License Agreement accompanying the Licensed Software does not alter any rights or obligations you may have under those open source or free software licenses. For more information on the Third Party Programs, please see the Third Party Notice document for this Symantec product that may be available at http://www.symantec.com/about/profile/policies/eulas/, the Third Party Legal Notice Appendix that may be included with this Documentation and/or Third Party Legal Notice ReadMe File that may accompany this Symantec product. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. -

Norton Antivirus™ Producthandleiding
NortonTM AntiVirus Producthandleiding Zorg voor het milieu: een vanzelfsprekende zaak. Symantec heeft de kaft van deze handleiding verwijderd om de ecologische voetafdruk van onze producten te verkleinen. Deze handleiding is gemaakt van gerecyclede materialen. Norton AntiVirus™ Producthandleiding De software die in deze handleiding wordt beschreven, wordt geleverd met een licentieovereenkomst en mag alleen worden gebruikt in overeenstemming met de voorwaarden in deze overeenkomst. Documentatieversie 21.0 Copyright © 2013 Symantec Corporation. Alle rechten voorbehouden. Symantec, het Symantec-logo, LiveUpdate, Norton 360 en Norton zijn handelsmerken of gedeponeerde handelsmerken van Symantec Corporation of haar aangesloten ondernemingen in de Verenigde Staten en andere landen. Delen van dit product Copyright 1996-2011 Glyph & Cog, LLC. Andere namen kunnen handelsmerken zijn van hun respectieve eigenaars. Het product dat in dit document wordt beschreven, wordt gedistribueerd onder licenties waarmee het gebruik, het kopiëren, het distribueren en het decompileren/toepassen van reverse-engineering ervan wordt beperkt. Geen enkel deel van dit document mag worden gereproduceerd in enige vorm op enige wijze zonder voorafgaande schriftelijke toestemming van Symantec Corporation en zijn eventuele licentiegevers. DE DOCUMENTATIE WORDT ALS ZODANIG GELEVERD EN ALLE EXPLICIETE OF IMPLICIETE VOORWAARDEN, REPRESENTATIES EN GARANTIES, WAARONDER IMPLICIETE GARANTIES VAN VERHANDELBAARHEID, GESCHIKTHEID VOOR EEN BEPAALD DOEL OF NIET-INBREUKMAKENDHEID, WORDEN -

Numbers Are Footnotes for Positions Referenced Below
Gary L. Wade 320 Crescent Village Circle Unit 1396 San Jose, CA 95134 [email protected] 949-505-3223 KEY EXPERIENCES • Passion for developing solutions for Apple Inc.’s platforms (macOS, iOS, tvOS, watchOS) • Innovative in usability design and testing, and refactoring for performance • Design and development of multi-platform client/server/cloud software solutions • Facilitate instruction for technical and non-technical staff including one-on-one mentoring CURRENT TALENT SUMMARY (numbers are footnotes for positions referenced below) • Adobe Photoshop (24,17,10,9,8,1) • Macintosh (Mac OS X) SDK (28,27,26,21,20, • AppKit/macOS (28,27,26,21,20,19,18,17,1) 19,18,17,16,15,14,13,12,11,8,7,6,5,4,2,1) • C (28,27,26,24,23,22,21,20,19,18,17,16,15,14, • Objective-C (28,27,26,24,23,22,21,20,19,18, 13,12,11,8,7,6,5,4,1) 17,1) • C++ (21,20,18,17,16,15,14,13,12,11,8,7,6,5,1) • Perforce (21,20,15) • Client/Server/Cloud (28,27,26,25,24,22,21,20, • Quality Assurance (25,24,17,3,1) 19,18,17,16,13,7,6,4) • QuickTime/AVKit (25,24,22,17,13,10,9,6,5) • Cocoa (28,27,26,25,24,23,22,21,20,19,18,17,1) • REST (28,27,26,25,24,22,21) • CoreFoundation (28,27,26,22,21,20,18,17,16, • Sales support (21,10,9,6,1) 15,14,13,12,1) • sqlite (23) • Cross-platform (28,27,21,20,17,15,14,13,12,8, • Subversion (27,22,19,18,1) 7,6,5,4,2) • Swift (28,27,26,25,24) • git (28,27,26,25,24,23,22) • UIKit/iOS (28,27,26,24,23,22,1) • HTML (28,27,26,25,17,14,12,10,9,1) • UIKit/tvOS (25) • Int. -

Cyber Risk Mitigation 57 • Mitigation for Small-Sized Organizations 60 • Mitigation for Medium-Sized Organizations 67 • Mitigation for Large-Sized Organizations 72
Media Impact International CYBER SECURITY REPORT Media Impact International Revised February 14, 2017 Media Impact International TABLE OF CONTENTS 1. Executive Summary 2 2. Introduction: Cyber Security in the Missional Context 5 3. Cyber Threats 8 4. Cyber Security Survey 28 5. Cyber Risk Assessment 50 6. Cyber Risk Mitigation 57 • Mitigation for Small-sized Organizations 60 • Mitigation for Medium-sized Organizations 67 • Mitigation for Large-sized Organizations 72 7. Appendix 75 • A – Small Business Implementation of the CSCS Part 1 • B – Small Business Implementation of the CSCS Part 2 • C – Critical Controls Poster 2016 • D – IBM MaaS360 Bundles • E – Vetted Service Providers • F – Models of Social Media / Communication Policies • G – Model of Password Policy • H – Phishing Training Model • I – Sensitive Information Reduction • J – Survey Questions • K – C3 Guidelines for Email • L – C3 Guidelines for VPN • M – C3 Guidelines for Messaging • N – Additional Country Profiles Copyright © 2017 Media Impact International MII would like to acknowledge and thank 100fold and its Director for serving as the lead researcher for this report, and the countless hours committed to this important project. MII also appreciates the many cyber professionals – inside and outside of the missional world – that provided counsel and expertise for this report. Revised February 14, 2017 1 Media Impact International EXECUTIVE SUMMARY Overview While Cyber Security breaches are often in the news, the impact of cyber security breaches on field ministry is often kept secret. In our su - vey of 30 key MENA ministries, we found that mission organizations were not only experi- encing financial loss (perhaps in the millions of dollars), but more than 50% had staff or seek- ers that experienced arrest or harassment, prison, expulsion – and even death – due to cyber security breaches. -

OSINT Handbook September 2020
OPEN SOURCE INTELLIGENCE TOOLS AND RESOURCES HANDBOOK 2020 OPEN SOURCE INTELLIGENCE TOOLS AND RESOURCES HANDBOOK 2020 Aleksandra Bielska Noa Rebecca Kurz, Yves Baumgartner, Vytenis Benetis 2 Foreword I am delighted to share with you the 2020 edition of the OSINT Tools and Resources Handbook. Once again, the Handbook has been revised and updated to reflect the evolution of this discipline, and the many strategic, operational and technical challenges OSINT practitioners have to grapple with. Given the speed of change on the web, some might question the wisdom of pulling together such a resource. What’s wrong with the Top 10 tools, or the Top 100? There are only so many resources one can bookmark after all. Such arguments are not without merit. My fear, however, is that they are also shortsighted. I offer four reasons why. To begin, a shortlist betrays the widening spectrum of OSINT practice. Whereas OSINT was once the preserve of analysts working in national security, it now embraces a growing class of professionals in fields as diverse as journalism, cybersecurity, investment research, crisis management and human rights. A limited toolkit can never satisfy all of these constituencies. Second, a good OSINT practitioner is someone who is comfortable working with different tools, sources and collection strategies. The temptation toward narrow specialisation in OSINT is one that has to be resisted. Why? Because no research task is ever as tidy as the customer’s requirements are likely to suggest. Third, is the inevitable realisation that good tool awareness is equivalent to good source awareness. Indeed, the right tool can determine whether you harvest the right information. -

Norton 360TM
Norton 360TM Manuel du produit Prenons soin de notre environnement. Nous avons décidé de supprimer la couverture de ce manuel afin de réduire l'empreinte écologique de nos produits. Ce manuel est constitué à partir de matériaux recyclés. Manuel du produit Norton 360™ Le logiciel décrit dans ce manuel est fourni dans le cadre d'un contrat de licence et ne peut être utilisé qu'en accord avec les conditions de ce contrat. Documentation version 21.0 Copyright © 2013 Symantec Corporation. Tous droits réservés. Symantec, le logo Symantec, LiveUpdate, Norton 360 et Norton sont des marques commerciales ou déposées de Symantec Corporation ou de ses sociétés affiliées aux Etats-Unis et dans d'autres pays. Copyright sur les parties de ce produit 1996-2011 Glyph & Cog, LLC. Les autres noms peuvent être des marques de leurs détenteurs respectifs. Le produit décrit dans ce document est distribué aux termes d'une licence limitant son utilisation, sa copie, sa distribution et sa décompilation/ingénierie inverse. Ce document ne peut, en tout ou partie, être reproduit sous aucune forme et par aucun moyen sans l'autorisation préalable écrite de Symantec Corporation et de ses concédants éventuels. LA DOCUMENTATION EST FOURNIE "EN L'ETAT" ET TOUTE GARANTIE OU CONDITION D'AUCUNE SORTE, EXPRESSE OU IMPLICITE, Y COMPRIS, SANS QUE CELA SOIT LIMITATIF, LES GARANTIES OU CONDITIONS IMPLICITES DE QUALITE MARCHANDE, D'ADEQUATION A UN USAGE PARTICULIER OU DE RESPECT DES DROITS DE PROPRIETE INTELLECTUELLE EST REFUTEE, EXCEPTÉ DANS LA MESURE OÙ DE TELLES EXCLUSIONS SERAIENT TENUES POUR LEGALEMENT NON VALIDES. SYMANTEC CORPORATION NE PEUT ETRE TENUE POUR RESPONSABLE DES DOMMAGES DIRECTS OU INDIRECTS RELATIFS AU CONTENU OU A L'UTILISATION DE LA PRESENTE DOCUMENTATION. -
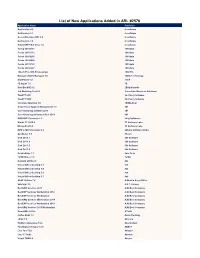
List of New Applications Added in ARL #2576
List of New Applications Added in ARL #2576 Application Name Publisher NetCmdlets 4.0 /n software NetCmdlets 3.1 /n software SecureBlackbox.NET 8.0 /n software NetCmdlets 3.0 /n software EldoS SFTP Net Drive 1.0 /n software Tenup 20190117 1010data Tendo 20151112 1010data Tendo 20160205 1010data Tendo 20190905 1010data Tendo 20170723 1010data Tendo 20161207 1010data 1042-S Pro 2016 Professional 1099 Pro Manager (10ZiG Manager) 3.0 10ZIG Technology DataParser 7.5 17a-4 1E Agent 7.2 1E SyncBackSE 8.2 2BrightSparks 2c8 Modeling Tool 4.2 2conciliate Business Solutions TaxACT 2017 2nd Story Software TaxACT 2018 2nd Story Software Complete Anatomy 5.0 3D4Medical Clean-Trace Hygiene Management 1.3 3M Core Grouping Software 2019 3M Core Grouping Software Client 2019 3M DWG DXF Converter 1.1 3nity Softwares Studio 3T 2020.9 3T Software Labs MongoChef 4.5 3T Software Labs MP4 to MP3 Converter 6.8 4Media Software Studio SendLater 3.4 4Team Disk Dril 3.7 508 Software Disk Dril 1.0 508 Software Disk Dril 3.5 508 Software Disk Dril 3.6 508 Software DoublePane 1.7 5am Code 7-PDF Maker 1.5 7-PDF Network Utility 2.2 8x8 Virtual Office Desktop 6.1 8x8 Virtual Office Desktop 6.4 8x8 Virtual Office Desktop 5.6 8x8 Virtual Office Desktop 6.7 8x8 ASAP Utilities 7.8 A Must in Every Office SafeSign 3.5 A.E.T. Europe BestSRQ Services 2015 A.M. Best Company BestESP Services Workstation 2012 A.M. Best Company BestESP Services Workstation A.M. -

Report on Digital and Physical Security Trainings Held from 16Th to 19Th October, 2019 at Kilifi Bay Hotel
REPORT ON DIGITAL AND PHYSICAL SECURITY TRAININGS HELD FROM 16TH TO 19TH OCTOBER, 2019 AT KILIFI BAY HOTEL OCTOBER, 2019. Prepared by: Tom Bicko Ooko, Project Officer, CJGEA Contents 1.0 DIGITAL SECURITY TRAINING NARRATIVE REPORT ...................................... 1 Wednesday October 16th. ........................................................................................................ 1 Introduction .............................................................................................................................. 1 Objectives of the training ........................................................................................................ 1 Commencement of the training .............................................................................................. 2 Introduction ............................................................................................................................ 2 Threat modelling ...................................................................................................................... 3 Threat assessment .................................................................................................................... 4 Threat actors ............................................................................................................................ 5 Forms of threats ....................................................................................................................... 5 Threat Analysis ....................................................................................................................... -

Norton 360TM
Norton 360TM Produkthandbuch Umweltschutz ist wichtig. Symantec hat dieses Handbuch ohne Umschlag gestaltet, um die Einwirkung auf die Umwelt durch unsere Produkte zu reduzieren. Dieses Handbuch wurde aus recycelten Stoffen hergestellt. Norton 360™ Produkthandbuch Die in diesem Handbuch beschriebene Software wird unter einer Lizenzvereinbarung bereitgestellt und darf nur gemäß den Bedingungen der Lizenzvereinbarung verwendet werden. Dokumentationsversion 21.0 Copyright © 2013 Symantec Corporation. Alle Rechte vorbehalten. Symantec, das Symantec-Logo, LiveUpdate und Norton 360 sind Marken oder eingetragene Marken der Symantec Corporation oder ihrer Tochtergesellschaften in den USA und anderen Ländern. Das Copyright für Teile dieses Produkts liegt bei Glyph & Cog, LLC. 1996–2011. Andere Bezeichnungen können Marken anderer Rechteinhaber sein. Die in diesem Handbuch beschriebene Software wird Ihnen im Rahmen einer Lizenzvereinbarung zur Verfügung gestellt und darf nur unter den darin beschriebenen Bedingungen eingesetzt, kopiert, verteilt, dekompiliert und zurückentwickelt werden. Kein Teil dieser Veröffentlichung darf ohne ausdrückliche schriftliche Genehmigung der Symantec Corporation und ihrer Lizenzgeber vervielfältigt werden. DIE DOKUMENTATION WIRD "OHNE MÄNGELGEWÄHR" GELIEFERT. ALLE AUSDRÜCKLICHEN ODER STILLSCHWEIGENDEN BEDINGUNGEN, DARSTELLUNGEN UND GEWÄHRLEISTUNGEN EINSCHLIESSLICH DER STILLSCHWEIGENDEN GEWÄHRLEISTUNG DER MARKTGÄNGIGKEIT, EIGNUNG FÜR EINEN BESTIMMTEN ZWECK ODER NICHTÜBERTRETUNG SIND UNGÜLTIG, SOFERN DIESER HAFTUNGSAUSSCHLUSS -

Podręcznik Użytkownika
Podręcznik użytkownika Troska o środowisko to słuszna sprawa. Firma Symantec usunęła okładkę z tego podręcznika, aby zmniejszyć niekorzystny wpływ swych produktów na środowisko. Do produkcji tego podręcznika użyto surowców wtórnych. Podręcznik użytkownika programu Norton™ Internet Security Oprogramowanie opisane w niniejszym podręczniku jest dostarczane w ramach umowy licencyjnej i może być używane jedynie zgodnie z postanowieniami tej umowy. Wersja dokumentacji 21.0 Copyright © 2013 Symantec Corporation. Wszystkie prawa zastrzeżone. Nazwa Symantec i logo Symantec, nazwy LiveUpdate, Norton 360 oraz Norton to znaki towarowe lub zastrzeżone znaki towarowe firmy Symantec Corporation lub jej oddziałów, zarejestrowane w USA i innych krajach. Prawa autorskie do części tego produktu: Copyright 1996-2011 Glyph & Cog, LLC. Inne nazwy mogą być znakami towarowymi należącymi do odpowiednich właścicieli. Produkt opisany w tym dokumencie jest dystrybuowany na licencji ograniczającej jego używanie, kopiowanie, dystrybucję i dekompilację/inżynierię odwrotną. Żadnej części tego dokumentu nie wolno powielać w jakiejkolwiek postaci za pomocą jakichkolwiek środków bez wcześniejszej pisemnej zgody firmy Symantec Corporation i jej oddziałów. TA DOKUMENTACJA JEST DOSTARCZANA W STANIE, „W JAKIM JEST” I WSZELKIE JAWNE LUB DOROZUMIANE WARUNKI, ZOBOWIĄZANIA I GWARANCJE, WŁĄCZNIE Z DOROZUMIANYMI GWARANCJAMI PRZYDATNOŚCI HANDLOWEJ, PRZYDATNOŚCI DO JAKIEGOKOLWIEK OKREŚLONEGO CELU I GWARANCJAMI NIENARUSZANIA PRAW WŁASNOŚCI INTELEKTUALNEJ SĄ WYKLUCZONE W STOPNIU DOPUSZCZALNYM -
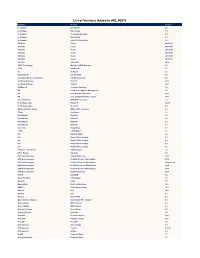
List of Versions Added in ARL #2576
List of Versions Added in ARL #2576 Publisher Product Version /n software NetCmdlets 4.0 /n software NetCmdlets 3.1 /n software SecureBlackbox.NET 8.0 /n software NetCmdlets 3.0 /n software EldoS SFTP Net Drive 1.0 1010data Tendo 20151112 1010data Tendo 20160205 1010data Tendo 20190905 1010data Tendo 20170723 1010data Tendo 20161207 1010data Tenup 20190117 1099 Pro 1042-S Pro 2016 10ZIG Technology Manager (10ZiG Manager) 3.0 17a-4 DataParser 7.5 1E 1E Agent 7.2 2BrightSparks SyncBackSE 8.2 2conciliate Business Solutions 2c8 Modeling Tool 4.2 2nd Story Software TaxACT 2018 2nd Story Software TaxACT 2017 3D4Medical Complete Anatomy 5.0 3M Clean-Trace Hygiene Management 1.3 3M Core Grouping Software 2019 3M Core Grouping Software Client 2019 3nity Softwares DWG DXF Converter 1.1 3T Software Labs Studio 3T 2020.9 3T Software Labs Studio 3T 4.5 4Media Software Studio MP4 to MP3 Converter 6.8 4Team SendLater 3.4 508 Software Disk Dril 3.6 508 Software Disk Dril 1.0 508 Software Disk Dril 3.5 508 Software Disk Dril 3.7 5am Code DoublePane 1.7 7-PDF 7-PDF Maker 1.5 8x8 Network Utility 2.2 8x8 Virtual Office Desktop 6.1 8x8 Virtual Office Desktop 6.4 8x8 Virtual Office Desktop 5.6 8x8 Virtual Office Desktop 6.7 A Must in Every Office ASAP Utilities 7.8 A.E.T. Europe SafeSign 3.5 A.M. Best Company BestSRQ Services 2015 A.M. Best Company BestESP Services Workstation 2012 A.M. Best Company BestESP Services Workstation Unspecified A.M. -

Norton Zone: Symantec's Secure Cloud Storage System
Norton Zone: Symantec’s Secure Cloud Storage System Walter Bogorad Scott Schneider Haibin Zhang Symantec Inc Symantec Research Labs University of North Carolina at Chapel Hill walter [email protected] [email protected] [email protected] Abstract—Cloud storage services are the way of the future, if Some less popular file hosting and sharing services, such not the present, but broad adoption is limited by a stark trade-off as Mega [31], SpiderOak [40], and Wuala [44], provide on- between privacy and functionality. Many popular cloud services premise security. These systems guarantee much better user provide search capabilities, but make only nominal efforts to keep user data fully private. Alternatives that search private user data privacy. They simply allow clients to encrypt their own data on an untrusted server sacrifice functionality and/or scalability. and then upload the ciphertext. These services have no access We describe Norton Zone, Symantec’s secure and scalable to user plaintext, so they cannot search user data with a public storage system based on our valet security model. Whereas strictly server-side implementation. None support encrypted most commercial cloud storage systems secure user data with search, perhaps because of its complexity or perhaps because access control and legal mechanisms, Zone’s cryptographic techniques provide proven privacy guarantees. This gives users of the computational requirements it puts on the client. This an extra layer of security without compromising functionality. requirement is particularly prohibitive for devices such as Zone’s performance is comparable to unencrypted cloud storage tablets and mobile phones. systems that support search and sharing.