MTAT.07.017 Applied Cryptography
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

GPU-Based Password Cracking on the Security of Password Hashing Schemes Regarding Advances in Graphics Processing Units
Radboud University Nijmegen Faculty of Science Kerckhoffs Institute Master of Science Thesis GPU-based Password Cracking On the Security of Password Hashing Schemes regarding Advances in Graphics Processing Units by Martijn Sprengers [email protected] Supervisors: Dr. L. Batina (Radboud University Nijmegen) Ir. S. Hegt (KPMG IT Advisory) Ir. P. Ceelen (KPMG IT Advisory) Thesis number: 646 Final Version Abstract Since users rely on passwords to authenticate themselves to computer systems, ad- versaries attempt to recover those passwords. To prevent such a recovery, various password hashing schemes can be used to store passwords securely. However, recent advances in the graphics processing unit (GPU) hardware challenge the way we have to look at secure password storage. GPU's have proven to be suitable for crypto- graphic operations and provide a significant speedup in performance compared to traditional central processing units (CPU's). This research focuses on the security requirements and properties of prevalent pass- word hashing schemes. Moreover, we present a proof of concept that launches an exhaustive search attack on the MD5-crypt password hashing scheme using modern GPU's. We show that it is possible to achieve a performance of 880 000 hashes per second, using different optimization techniques. Therefore our implementation, executed on a typical GPU, is more than 30 times faster than equally priced CPU hardware. With this performance increase, `complex' passwords with a length of 8 characters are now becoming feasible to crack. In addition, we show that between 50% and 80% of the passwords in a leaked database could be recovered within 2 months of computation time on one Nvidia GeForce 295 GTX. -

Increasing Cryptography Security Using Hash-Based Message
ISSN (Print) : 2319-8613 ISSN (Online) : 0975-4024 Seyyed Mehdi Mousavi et al. / International Journal of Engineering and Technology (IJET) Increasing Cryptography Security using Hash-based Message Authentication Code Seyyed Mehdi Mousavi*1, Dr.Mohammad Hossein Shakour 2 1-Department of Computer Engineering, Shiraz Branch, Islamic AzadUniversity, Shiraz, Iran . Email : [email protected] 2-Assistant Professor, Department of Computer Engineering, Shiraz Branch, Islamic Azad University ,Shiraz ,Iran Abstract Nowadays, with the fast growth of information and communication technologies (ICTs) and the vulnerabilities threatening human societies, protecting and maintaining information is critical, and much attention should be paid to it. In the cryptography using hash-based message authentication code (HMAC), one can ensure the authenticity of a message. Using a cryptography key and a hash function, HMAC creates the message authentication code and adds it to the end of the message supposed to be sent to the recipient. If the recipient of the message code is the same as message authentication code, the packet will be confirmed. The study introduced a complementary function called X-HMAC by examining HMAC structure. This function uses two cryptography keys derived from the dedicated cryptography key of each packet and the dedicated cryptography key of each packet derived from the main X-HMAC cryptography key. In two phases, it hashes message bits and HMAC using bit Swapp and rotation to left. The results show that X-HMAC function can be a strong barrier against data identification and HMAC against the attacker, so that it cannot attack it easily by identifying the blocks and using HMAC weakness. -

Second Preimage Attacks on Dithered Hash Functions
Second Preimage Attacks on Dithered Hash Functions Elena Andreeva1, Charles Bouillaguet2, Pierre-Alain Fouque2, Jonathan J. Hoch3, John Kelsey4, Adi Shamir2,3, and Sebastien Zimmer2 1 SCD-COSIC, Dept. of Electrical Engineering, Katholieke Universiteit Leuven, [email protected] 2 École normale supérieure (Département d’Informatique), CNRS, INRIA, {Charles.Bouillaguet,Pierre-Alain.Fouque,Sebastien.Zimmer}@ens.fr 3 Weizmann Institute of Science, {Adi.Shamir,Yaakov.Hoch}@weizmann.ac.il 4 National Institute of Standards and Technology, [email protected] Abstract. We develop a new generic long-message second preimage at- tack, based on combining the techniques in the second preimage attacks of Dean [8] and Kelsey and Schneier [16] with the herding attack of Kelsey and Kohno [15]. We show that these generic attacks apply to hash func- tions using the Merkle-Damgård construction with only slightly more work than the previously known attack, but allow enormously more con- trol of the contents of the second preimage found. Additionally, we show that our new attack applies to several hash function constructions which are not vulnerable to the previously known attack, including the dithered hash proposal of Rivest [25], Shoup’s UOWHF[26] and the ROX hash construction [2]. We analyze the properties of the dithering sequence used in [25], and develop a time-memory tradeoff which allows us to apply our second preimage attack to a wide range of dithering sequences, including sequences which are much stronger than those in Rivest’s proposals. Fi- nally, we show that both the existing second preimage attacks [8, 16] and our new attack can be applied even more efficiently to multiple target messages; in general, given a set of many target messages with a total of 2R message blocks, these second preimage attacks can find a second preimage for one of those target messages with no more work than would be necessary to find a second preimage for a single target message of 2R message blocks. -

Intro to Cryptography 1 Introduction 2 Secure Password Manager
Programming Assignment 1 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, Feb. 8, 11:59pm 1 Introduction In many software systems today, the primary weakness often lies in the user’s password. This is especially apparent in light of recent security breaches that have highlighted some of the weak passwords people commonly use (e.g., 123456 or password). It is very important, then, that users choose strong passwords (or “passphrases”) to secure their accounts, but strong passwords can be long and unwieldy. Even more problematic, the user generally has many different services that use password authentication, and as a result, the user has to recall many different passwords. One way for users to address this problem is to use a password manager, such as LastPass and KeePass. Password managers make it very convenient for users to use a unique, strong password for each service that requires password authentication. However, given the sensitivity of the data contained in the password manager, it takes considerable care to store the information securely. In this assignment, you will be writing a secure and efficient password manager. In your implemen- tation, you will make use of various cryptographic primitives we have discussed in class—notably, authenticated encryption and collision-resistant hash functions. Because it is ill-advised to imple- ment your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic tem- plate, which you will be able to fill in to satisfy the functionality and security properties described below. -

User Authentication and Cryptographic Primitives
User Authentication and Cryptographic Primitives Brad Karp UCL Computer Science CS GZ03 / M030 16th November 2016 Outline • Authenticating users – Local users: hashed passwords – Remote users: s/key – Unexpected covert channel: the Tenex password- guessing attack • Symmetric-key-cryptography • Public-key cryptography usage model • RSA algorithm for public-key cryptography – Number theory background – Algorithm definition 2 Dictionary Attack on Hashed Password Databases • Suppose hacker obtains copy of password file (until recently, world-readable on UNIX) • Compute H(x) for 50K common words • String compare resulting hashed words against passwords in file • Learn all users’ passwords that are common English words after only 50K computations of H(x)! • Same hashed dictionary works on all password files in world! 3 Salted Password Hashes • Generate a random string of bytes, r • For user password x, store [H(r,x), r] in password file • Result: same password produces different result on every machine – So must see password file before can hash dictionary – …and single hashed dictionary won’t work for multiple hosts • Modern UNIX: password hashes salted; hashed password database readable only by root 4 Salted Password Hashes • Generate a random string of bytes, r Dictionary• For user password attack still x, store possible [H(r,x after), r] in attacker seespassword password file file! Users• Result: should same pick password passwords produces that different aren’t result close to ondictionary every machine words. – So must see password file -

A Full Key Recovery Attack on HMAC-AURORA-512
A Full Key Recovery Attack on HMAC-AURORA-512 Yu Sasaki NTT Information Sharing Platform Laboratories, NTT Corporation 3-9-11 Midori-cho, Musashino-shi, Tokyo, 180-8585 Japan [email protected] Abstract. In this note, we present a full key recovery attack on HMAC- AURORA-512 when 512-bit secret keys are used and the MAC length is 512-bit long. Our attack requires 2257 queries and the off-line com- plexity is 2259 AURORA-512 operations, which is significantly less than the complexity of the exhaustive search for a 512-bit key. The attack can be carried out with a negligible amount of memory. Our attack can also recover the inner-key of HMAC-AURORA-384 with almost the same complexity as in HMAC-AURORA-512. This attack does not recover the outer-key of HMAC-AURORA-384, but universal forgery is possible by combining the inner-key recovery and 2nd-preimage attacks. Our attack exploits some weaknesses in the mode of operation. keywords: AURORA, DMMD, HMAC, Key recovery attack 1 Description 1.1 Mode of operation for AURORA-512 We briefly describe the specification of AURORA-512. Please refer to Ref. [2] for details. An input message is padded to be a multiple of 512 bits by the standard MD message padding, then, the padded message is divided into 512-bit message blocks (M0;M1;:::;MN¡1). 256 512 256 In AURORA-512, compression functions Fk : f0; 1g £f0; 1g ! f0; 1g 256 512 256 512 and Gk : f0; 1g £ f0; 1g ! f0; 1g , two functions MF : f0; 1g ! f0; 1g512 and MFF : f0; 1g512 ! f0; 1g512, and two initial 256-bit chaining U D 1 values H0 and H0 are defined . -

To Change Your Ud Password(S)
TO CHANGE YOUR UD PASSWORD(S) The MyCampus portal allows the user a single-signon for campus applications. IMPORTANT NOTICE AT BOTTOM OF THESE INSTRUCTIONS !! INITIAL PROCEDURE TO ALLOW YOU TO CHANGE YOUR PASSWORD ON THE UD NETWORK : 1. In your web browser, enter http://mycampus.dbq.edu . If you are logging in for the first time, you will be directed to answer (3) security questions. Also, be sure to answer one of the recovery methods. 2. Once the questions are answered, you will click on SUBMIT and then CONTINUE and then YES. 3. In one location, you will now find MyUD, Campus Portal, Email and UDOnline (Moodle). 4. You can now click on any of these apps and you will be logged in already. The email link will prompt you for the password a second time until we get all accounts set up properly. YOU MUST BE SURE TO LOGOUT OF EACH APPLICATION AFTER YOU’RE DONE USING IT !! TO CHANGE YOUR PASSWORD: 1. After you have logged into the MyCampus.dbq.edu website, you will see your username in the upper- right corner of the screen. 2. Click on your name and then go into My Account. 3. At the bottom, you will click on Change Password and then proceed as directed. 4. You can now logout. You will need to use your new password on your next login. Password must be a minimum of 6 characters and contain 3 of the following 4 categories: - Uppercase character - Lowercase character - Number - Special character You cannot use the previous password You’ll be required to change your password every 180 days. -

Security + Encryption Standards
Security + Encryption Standards Author: Joseph Lee Email: joseph@ ripplesoftware.ca Mobile: 778-725-3206 General Concepts Forward secrecy / perfect forward secrecy • Using a key exchange to provide a new key for each session provides improved forward secrecy because if keys are found out by an attacker, past data cannot be compromised with the keys Confusion • Cipher-text is significantly different than the original plaintext data • The property of confusion hides the relationship between the cipher-text and the key Diffusion • Is the principle that small changes in message plaintext results in large changes in the cipher-text • The idea of diffusion is to hide the relationship between the cipher-text and the plaintext Secret-algorithm • A proprietary algorithm that is not publicly disclosed • This is discouraged because it cannot be reviewed Weak / depreciated algorithms • An algorithm that can be easily "cracked" or defeated by an attacker High-resiliency • Refers to the strength of the encryption key if an attacker discovers part of the key Data-in-transit • Data sent over a network Data-at-rest • Data stored on a medium Data-in-use • Data being used by an application / computer system Out-of-band KEX • Using a medium / channel for key-exchange other than the medium the data transfer is taking place (phone, email, snail mail) In-band KEX • Using the same medium / channel for key-exchange that the data transfer is taking place Integrity • Ability to determine the message has not been altered • Hashing algorithms manage Authenticity -
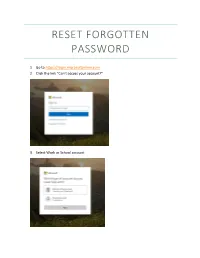
Reset Forgotten Password with Office365
RESET FORGOTTEN PASSWORD 1. Go to https://login.microsoftonline.com 2. Click the link “Can’t access your account?” 3. Select Work or School account 4. Enter in your User ID with the @uamont.edu at the end and then enter the characters as seen in the picture. You can click the refresh button for a different set of letters. 5. You will have 3 options to verify your account and reset your password. This information was set up when you registered with self-service password reset. If you have not registered, please go to https://aka.ms/ssprsetup and enter in your information. A step by step guide on how to do this can be found here. a. Text your mobile phone b. Call your mobile phone c. Answer Security Questions 6. Choose one option and enter the information requested 7. Click Text for text my mobile phone, Call for call my mobile phone, or click Next when you’ve answered all security questions. a. If you have selected Text my mobile phone you will be required to enter in a verification code and click Next b. If you have select Call my mobile phone you will receive a call and will need to enter # to verify. 8. Enter in your new password and click Finish a. Note: If you receive the message, “Unfortunately, your password contains a word, phrase, or pattern that makes it easily guessable. Please try again with a different password.” Please try to create a password that does not use any dictionary words. b. Passwords must meet 3 of the 4 following requirements i. -

The First Collision for Full SHA-1
The first collision for full SHA-1 Marc Stevens1, Elie Bursztein2, Pierre Karpman1, Ange Albertini2, Yarik Markov2 1 CWI Amsterdam 2 Google Research [email protected] https://shattered.io Abstract. SHA-1 is a widely used 1995 NIST cryptographic hash function standard that was officially deprecated by NIST in 2011 due to fundamental security weaknesses demonstrated in various analyses and theoretical attacks. Despite its deprecation, SHA-1 remains widely used in 2017 for document and TLS certificate signatures, and also in many software such as the GIT versioning system for integrity and backup purposes. A key reason behind the reluctance of many industry players to replace SHA-1 with a safer alternative is the fact that finding an actual collision has seemed to be impractical for the past eleven years due to the high complexity and computational cost of the attack. In this paper, we demonstrate that SHA-1 collision attacks have finally become practical by providing the first known instance of a collision. Furthermore, the prefix of the colliding messages was carefully chosen so that they allow an attacker to forge two PDF documents with the same SHA-1 hash yet that display arbitrarily-chosen distinct visual contents. We were able to find this collision by combining many special cryptanalytic techniques in complex ways and improving upon previous work. In total the computational effort spent is equivalent to 263:1 SHA-1 compressions and took approximately 6 500 CPU years and 100 GPU years. As a result while the computational power spent on this collision is larger than other public cryptanalytic computations, it is still more than 100 000 times faster than a brute force search. -

Related-Key and Key-Collision Attacks Against RMAC
Related-Key and Key-Collision Attacks Against RMAC Tadayoshi Kohno CSE Department, UC San Diego 9500 Gilman Drive, MC-0114 La Jolla, California 92093-0114, USA IACR ePrint archive 2002/159, 21 October 2002, revised 2 December 2002. Abstract. In [JJV02] Jaulmes, Joux, and Valette propose a new ran- domized message authentication scheme, called RMAC, which NIST is currently in the process of standardizing [NIS02]. In this work we present several attacks against RMAC. The attacks are based on a new protocol- level related-key attack against RMAC and can be considered variants of Biham’s key-collision attack [Bih02]. These attacks provide insights into the RMAC design. We believe that the protocol-level related-key attack is of independent interest. Keywords: RMAC, key-collision attacks, related-key attacks. 1 Introduction Jaulmes, Joux, and Valette’s RMAC construction [JJV02] is a new ran- domized message authentication scheme. Similar to Petrank and Rackoff’s DMAC construction [PR97] and Black and Rogaway’s ECBC construc- tion [BR00], the RMAC construction is a CBC-MAC variant in which an input message is first MACed with standard CBC-MAC and then the resulting intermediate value is enciphered with one additional block ci- pher application. Rather than using a fixed key for the last block cipher application (as DMAC and ECBC do), RMAC enciphers the last block with a randomly chosen (but related) key. One immediate observation is that RMAC directly exposes the underlying block cipher to a weak form of related-key attacks [Bih93]. We are interested in attacks that do not exploit some related-key weakness of the underlying block cipher, but rather some property of the RMAC mode itself. -

Implementation and Performance Analysis of PBKDF2, Bcrypt, Scrypt Algorithms
Implementation and Performance Analysis of PBKDF2, Bcrypt, Scrypt Algorithms Levent Ertaul, Manpreet Kaur, Venkata Arun Kumar R Gudise CSU East Bay, Hayward, CA, USA. [email protected], [email protected], [email protected] Abstract- With the increase in mobile wireless or data lookup. Whereas, Cryptographic hash functions are technologies, security breaches are also increasing. It has used for building blocks for HMACs which provides become critical to safeguard our sensitive information message authentication. They ensure integrity of the data from the wrongdoers. So, having strong password is that is transmitted. Collision free hash function is the one pivotal. As almost every website needs you to login and which can never have same hashes of different output. If a create a password, it’s tempting to use same password and b are inputs such that H (a) =H (b), and a ≠ b. for numerous websites like banks, shopping and social User chosen passwords shall not be used directly as networking websites. This way we are making our cryptographic keys as they have low entropy and information easily accessible to hackers. Hence, we need randomness properties [2].Password is the secret value from a strong application for password security and which the cryptographic key can be generated. Figure 1 management. In this paper, we are going to compare the shows the statics of increasing cybercrime every year. Hence performance of 3 key derivation algorithms, namely, there is a need for strong key generation algorithms which PBKDF2 (Password Based Key Derivation Function), can generate the keys which are nearly impossible for the Bcrypt and Scrypt.