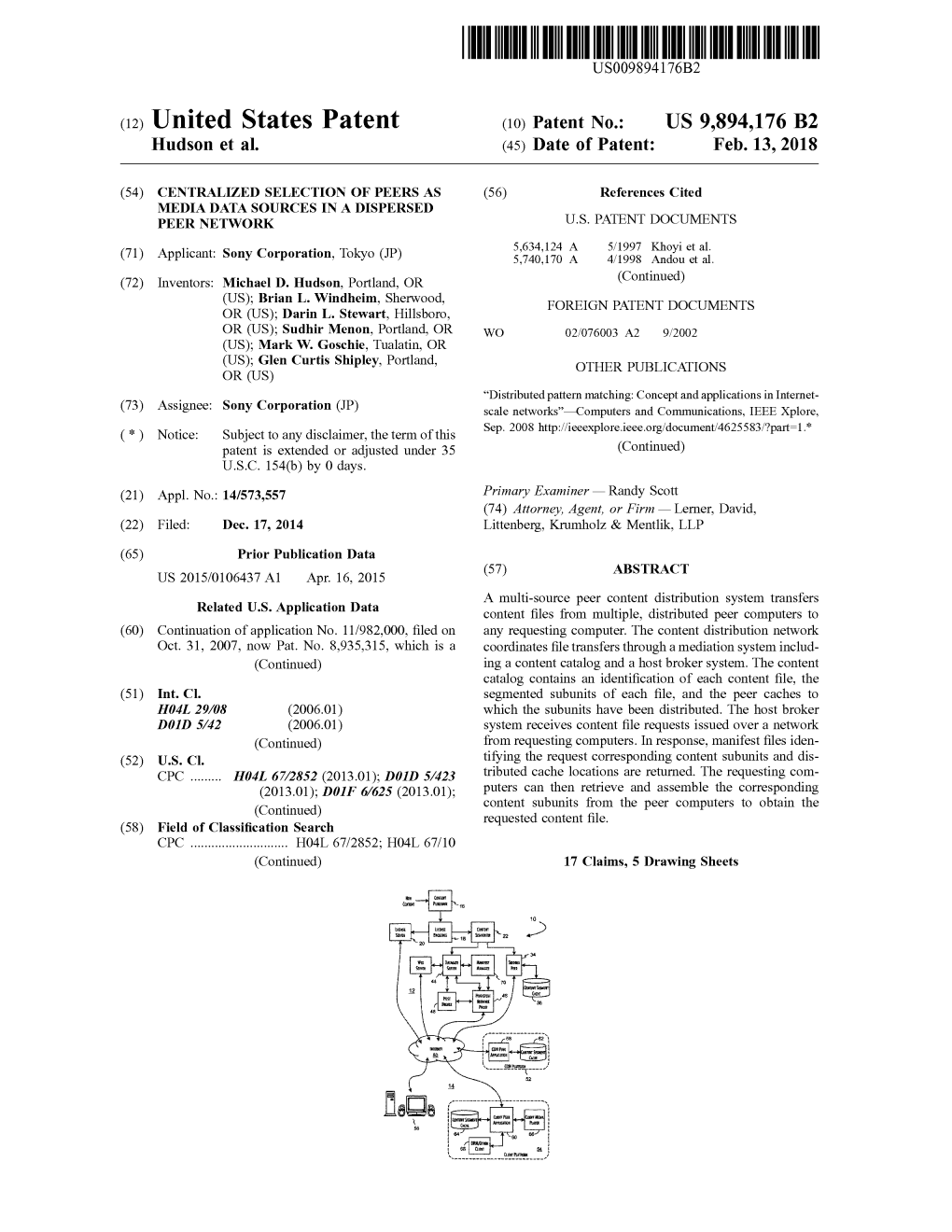
THAT ARE NOT ALLUMINIOUS009894176B2 (12 ) United States Patent ( 10 ) Patent No
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Book of Abstracts Ii Contents
CHEP 2016 Conference, San Francisco, October 8-14, 2016 Monday, 10 October 2016 - Friday, 14 October 2016 San Francisco Marriott Marquis Book of Abstracts ii Contents Experiment Management System for the SND Detector 0 .................. 1 Reconstruction software of the silicon tracker of DAMPE mission 2 ............ 1 HEPData - a repository for high energy physics data exploration 3 ............. 2 Reconstruction of Micropattern Detector Signals using Convolutional Neural Networks 4 3 Federated data storage system prototype for LHC experiments and data intensive science 6 ................................................ 3 BelleII@home: Integrate volunteer computing resources into DIRAC in a secure way 7 . 4 Reconstruction and calibration of MRPC endcap TOF of BESIII 8 .............. 5 RootJS: Node.js Bindings for ROOT 6 9 ............................ 6 C++ Software Quality in the ATLAS experiment: Tools and Experience 10 . 6 An automated meta-monitoring mobile application and frontend interface for the WLCG computing model 11 ..................................... 7 Experience of Google’s latest Deep Learning library, TensorFlow, with Docker in a WLCG cluster 12 ........................................... 8 Flexible online monitoring for high-energy physics with Pyrame 13 ............ 8 Simulation of orientational coherent effects via Geant4 14 .................. 9 Detector control system for the AFP detector in ATLAS experiment at CERN 15 . 10 The InfiniBand based Event Builder implementation for the LHCb upgrade16 . 11 JavaScript ROOT v4 17 ..................................... 12 The evolution of monitoring system: the INFN-CNAF case study18 . 13 Statistical and Data Analysis Package in SWIFT 19 ...................... 13 Analysis Tools in Geant4 10.2 20 ................................ 14 Online & Offline Storage and Processing for the upcoming European XFEL Experiments 21 15 Future approach to tier-0 extension 22 ............................. 15 iii Internal security consulting, reviews and penetration testing at CERN 23 . -

The Linux Command Line
The Linux Command Line Fifth Internet Edition William Shotts A LinuxCommand.org Book Copyright ©2008-2019, William E. Shotts, Jr. This work is licensed under the Creative Commons Attribution-Noncommercial-No De- rivative Works 3.0 United States License. To view a copy of this license, visit the link above or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042. A version of this book is also available in printed form, published by No Starch Press. Copies may be purchased wherever fine books are sold. No Starch Press also offers elec- tronic formats for popular e-readers. They can be reached at: https://www.nostarch.com. Linux® is the registered trademark of Linus Torvalds. All other trademarks belong to their respective owners. This book is part of the LinuxCommand.org project, a site for Linux education and advo- cacy devoted to helping users of legacy operating systems migrate into the future. You may contact the LinuxCommand.org project at http://linuxcommand.org. Release History Version Date Description 19.01A January 28, 2019 Fifth Internet Edition (Corrected TOC) 19.01 January 17, 2019 Fifth Internet Edition. 17.10 October 19, 2017 Fourth Internet Edition. 16.07 July 28, 2016 Third Internet Edition. 13.07 July 6, 2013 Second Internet Edition. 09.12 December 14, 2009 First Internet Edition. Table of Contents Introduction....................................................................................................xvi Why Use the Command Line?......................................................................................xvi -

38 Bittorrent Software and Usage Justin Mckinney
ARTICLE BITTORRENT SOFTwaRE AND USAGE Justin McKinney Mark Simon Haydn 1. Abstract: While the circulation of cultural material outside of official channels is not new, the scale and infrastructure afforded by digital networks and peer-to-peer protocols has drastically changed its dynamics. Focusing on private trackers and online, members-only communities dedicated to sharing difficult to find and “gray-area” cinema content, our paper discusses new digital re- positories and their connection to the traditional film archive. With discussion of the types of materials held, user participation, and custodial efforts to restore or improve cultural material, we will discuss the activities of a contemporary private tracker community. Additionally, the paper will interrogate the legality and copyright issues surrounding these activities and ex- plore recent, licit adoption of the infrastructure that has been developed for online circulation. Discussion will conclude with attention to cases in which pirated material has resurfaced in a rights-holding context, and an assessment of what these developments mean for custodians of film material working in a traditional film archive context. As a combination of discussion, case study, and argument, the paper will serve as a topical primer on a pressing and under- researched area of interest in this field, building on a panel presented at last year’s Association of Moving Image Archivists conference in Georgia. 2. BitTorrent Software and Usage BitTorrent is a software protocol developed in 2001 and designed to aid the practice of peer- to-peer file sharing on the Internet. The primary advantage of BitTorrent is that it allows for segmented downloading, which is the coordinated transmission of a file sourced from multiple servers to a single destination.81 This protocol allows for the rapid sharing of large amounts of data by allowing a user to download a file from multiple sources that are uploading the file at the same time.82 This allows for more efficient and faster downloading than the traditional client-server model. -

A Review on Torrent & Torrent Poisoning Over Internet
IJCSMS (International Journal of Computer Science & Management Studies) Vol. 22, Issue 01 Publishing Month: January 2016 An Indexed and Referred Journal with ISSN (Online): 2231-5268 www.ijcsms.com A Review on Torrent & Torrent Poisoning over Internet Pooja Balhara Lecturer, All India Jat Heroes Memorial College, Rohtak, Haryana (India) [email protected] Publishing Date: January 22, 2016 Abstract A torrent file is a encoded dictionary with the Now a days, Torrents are widely used for downloading following keys: heavy files over internet the reason is being unlike other download methods, Torrent maximizes transfer speed by downloading the pieces of the files you want ∑ Announce the URL of the tracker simultaneously from people who already have them. This ∑ Info this maps to a dictionary whose keys are process makes very large files, such as videos and dependent on whether one or more files are television programs; games download much faster than is being shared: possible with other methods. In this paper, I am ∑ Name suggested filename where the file is to representing the basic and some popular details and be saved (if one file)/suggested directory name activities after a deep review of torrent and torrent poisoning. where the files are to be saved (if multiple files) Keywords: Torrent, bit torrent, torrent poisoning. ∑ Piece length number of bytes per piece. ∑ Pieces a hash list, i.e., a concatenation of each 1. Introduction to Torrent piece's SHA-1 hash. As SHA-1 returns a 160-bit hash, pieces will be a string whose length is a A Torrent file is a computer file that multiple of 160-bits. -

How Does Digital Piracy Influence the Subscription of Online Video Bundling Services?
How does Digital Piracy influence the subscription of online video bundling services? Bernardo Filipe Geadas Joaquim Dissertation presented as partial requirement for obtaining the Double Degree Master’s in Information Management and Business Informatics i How does Digital Piracy influence the subscription of online video bundling services? Bernardo Filipe Geadas Joaquim Dissertation presented as partial requirement for obtaining the Double Degree Master’s in Information Management and Business Informatics ii 201 Title: Student 6 full name MEGI Subtitle: 201 Title: Student 6 full name MGI Subtitle: i i NOVA Information Management School Instituto Superior de Estatística e Gestão de Informação Universidade Nova de Lisboa HOW DOES DIGITAL PIRACY INFLUENCE THE SUBSCRIPTION OF ONLINE VIDEO BUNDLING SERVICES? By Bernardo Filipe Geadas Joaquim Dissertation presented as partial requirement for obtaining the Double degree Master in Information Systems Management Co Advisor: Professor Aleš Popovič Co Advisor: Professor Vitor Santos ii October 2016 SUBMISSION RESULTING FROM THIS MASTER THESIS Joaquim, B., Santos, V., Popovič, A. How does Digital Piracy influence the subscription of Online Video Bundling Services? (Submission to WorldCist’17 – 5th World Conference on Information Systems and Technologies) iii ACKNOWLEDGEMENTS I would like to thanks my parents for providing me the opportunity to be a part of this Master’s, my mentors: Professor Aleš Popovič and Professor Vitor Santos for all the help and advices given during the progression of the thesis and the country of Slovenia for hosting me during the execution of this master thesis. iv ABSTRACT The availability of digital channels that allow the distribution of copyrighted material has raised several questions over the last few years. -
![CS555: Distributed Systems [Fall 2019] Dept](https://docslib.b-cdn.net/cover/7014/cs555-distributed-systems-fall-2019-dept-5497014.webp)
CS555: Distributed Systems [Fall 2019] Dept
CS555: Distributed Systems [Fall 2019] Dept. Of Computer Science, Colorado State University Frequently asked questions from the previous class survey CS 555: DISTRIBUTED SYSTEMS ¨ Difference in routing in the network space vs ID space [ BITTORRENT & DISTRIBUTED COMPUTING ECONOMICS] ¨ Can Gnutella be viewed as a semi-structured P2P system? Shrideep Pallickara Computer Science Colorado State University CS555: Distributed Systems [Fall 2019] L9.1 September 24, 2019 September 24, 2019 CS555: Distributed Systems [Fall 2019] L9.2 Dept. Of Computer Science, Colorado State University Professor: SHRIDEEP PALLICKARA Dept. Of Computer Science, Colorado State University Topics covered in this lecture ¨ BitTorrent ¨ Distributed Computing Economics BITTORRENT CS555: Distributed Systems [Fall 2019] September 24, 2019 CS555: Distributed Systems [Fall 2019] L9.3 September 24, 2019 L9.4 Professor: SHRIDEEP PALLICKARA Dept. Of Computer Science, Colorado State University Dept. Of Computer Science, Colorado State University Bit Torrent: Traffic statistics BitTorrent ¨ In November 2004 ¨ Designed for downloading large files ¤ Responsible for 25% of all Internet traffic ¨ Not intended for real-time routing of content ¨ February 2013 ¨ Relies on capabilities of ordinary user machines ¤ 3.35% of all worldwide bandwidth ¤ > 50% of the 6% total bandwidth dedicated to file sharing September 24, 2019 CS555: Distributed Systems [Fall 2019] L9.5 September 24, 2019 CS555: Distributed Systems [Fall 2019] L9.6 Professor: SHRIDEEP PALLICKARA Dept. Of Computer Science, Colorado -
Efficient Data Communication and Storage Using Synchronized Servers with Load Distribution Facility
ISSN (Online) 2278-1021 IJARCCE ISSN (Print) 2319-5940 International Journal of Advanced Research in Computer and Communication Engineering Vol. 10, Issue 4, April 2021 DOI 10.17148/IJARCCE.2021.10470 Efficient Data Communication and Storage using Synchronized Servers with Load Distribution Facility Prof. Aparna Kalaskar1, Mohit Patil2, Smit Mahajan3, Neha Goundadkar4, Amit Raj5 Assistant Professor, Department of Computer Engineering, Sinhgad College of Engineering, Pune, India 1 Student, Department of Computer Engineering, Sinhgad College of Engineering, Pune, India 2,3,4,5 Abstract: In the early 2000’s, when data used to be of simple structure and small size, the client- server architecture handled the sharing and storage of data pretty efficiently. But as the technology progressed, the data became more and more complex and huge in size which led to load on servers for storing and sharing the data. Here, the P2P network architecture comes into picture where the peers could communicate and share the data without any centralized server. The basic idea behind the proposal of this system is the combined use of segmented file transfer on P2P network. This makes it possible to download a single file from multiple peers at the same time. Moreover, it also includes a synchronized server module for efficient storage and updating data more efficiently on the servers. This paper presents a system in which data transfer and storage system uses file downloading based on peer-to-peer network architecture. It’s the software developed for sharing/downloading huge data files and storing important data efficiently. It’s very convenient to share data using this system as the data is spread across the peer-to-peer network. -
Peer to Peer Archiectures
Lesson 8: Peer-to-Peer Architectures Phillip J. Windley, Ph.D. CS462 – Large-Scale Distributed Systems Lesson 08: Peer to Peer Architectures Contents Fallacies of Distributed Distributed Discovery 00 Computing 03 01 The CAP Theorem 04 Conclusion 02 Swarm File Sharing Lesson 08: Peer-to-Peer Architectures Introduction Peer-to-peer (P2P) architectures are networked Special purpose P2P systems are frequently systems where each node in the network is on built on top of the Internet. Such a network is equal footing with every other node. called an overlay network. The largest and most successful P2P network is Designing a functional P2P system can be the Internet itself. Every machine connected to difficult because humans think in stories— the network gets an IP address and can interact linearly. And we love centralized systems with any other machine on the Internet so long because they’re easy to understand. as it knows that machine’s IP address. This lesson introduces concepts and algorithms The Web is not a P2P architecture because it for building practical decentralized peer-to-peer sees some machines as clients and some as systems. servers. They are not peers. CS462 – Large-Scale Distributed Systems © PJW LC (CC BY-NC 4.0) 3 Lesson 08: Peer-to-Peer Architectures Lesson Objectives After completing this lesson, you should be able to: 1. Explain the eight fallacies of distributed computing 2. Give examples of the CAP theorem and explain tradeoffs 3. Show how distributed file sharing works and relate it to consensus 4. Describe distributed discovery and show how a distributed hash table works CS462 – Large-Scale Distributed Systems © PJW LC (CC BY-NC 4.0) 4 Lesson 08: Peer-to-Peer Architectures Reading Read the following: Ø Fallacies of Distributed Computing Explained (PDF) by Arnon Rotem-Gal-Oz (http://www.rgoarchitects.com/Files/fallacies.pdf) Ø A plain English introduction to CAP Theorem by Kaushik Sathupadi (http://ksat.me/a-plain-english- introduction-to-cap-theorem/ ) Ø Perspectives on the CAP Theorem (PDF) by Seth Gilbert and Nancy A. -
Best Torrent Download Client Best Torrent Client to Download Torrent Files
best torrent download client Best torrent client to download torrent files. There will be a time that you need to download a file through torrent. There are quite a lot of applications that you can use to download torrent files. But, most of them are not that great. Are you looking for a torrent client which is clean by design, with no advertisements, open-source, and kept up to date? You’re on the right page. Let’s dive into it. Table of contents. Introduction. I need to download a file, and I see that the provider asks us to download from the torrent link. So it’s an excellent way for me to introduce the best torrent client, which I always use. Is torrenting legal or illegal. Before we move on, let’s answer a question that is always asked: Is torrenting legal or illegal? Torrenting itself isn’t illegal , but downloading unsanctioned copyrighted material is. It’s not always immediately apparent which content is legal to torrent and which isn’t. Some fall in a gray area, so you may find yourself unwittingly on the wrong side of the law. Download qBittorrent client. Go to the qBittorrent download page and download the version that suits your operating system. At the moment of writing, qBittorrent v4.3.6 is the current stable version for Windows 7/8/10. There are 32 and 64-bit versions. Make sure you select the version that is compatible with your operating system. In this example, I will download qBittorrent for Windows 10 64-bit. -

The Linux Command Line the Linux
BANISHBANISH YOURYOUR MOUSEMOUSE THE LINUX COMMAND LINE THE LINUX COMMAND LINE THETHE LINUXLINUX You’ve experienced the shiny, point-and-click surface • Use standard input and output, redirection, and COMMANDCOMMAND LINELINE of your Linux computer—now dive below and explore pipelines its depths with the power of the command line. • Edit files with Vi, the world’s most popular text editor A COMPLETE INTRODUCTION The Linux Command Line takes you from your very first • Write shell scripts to automate common or boring tasks terminal keystrokes to writing full programs in Bash, the most popular Linux shell. Along the way you’ll learn • Slice and dice text files with cut, paste, grep, patch, the timeless skills handed down by generations of and sed WILLIAM E. SHOTTS, JR. gray-bearded, mouse-shunning gurus: file navigation, Once you overcome your initial “shell shock,” you’ll environment configuration, command chaining, pattern find that the command line is a natural and expressive matching with regular expressions, and more. way to communicate with your computer. Just don’t be In addition to that practical knowledge, author William surprised if your mouse starts to gather dust. Shotts reveals the philosophy behind these tools and ABOUT THE AUTHOR the rich heritage that your desktop Linux machine has inherited from Unix supercomputers of yore. William E. Shotts, Jr., has been a software professional and avid Linux user for more than 15 years. He has an As you make your way through the book’s short, easily extensive background in software development, including digestible chapters, you’ll learn how to: technical support, quality assurance, and documentation. -
![Arxiv:1711.08060V1 [Cs.DC] 21 Nov 2017 When Embracing the Cloud](https://docslib.b-cdn.net/cover/5456/arxiv-1711-08060v1-cs-dc-21-nov-2017-when-embracing-the-cloud-8265456.webp)
Arxiv:1711.08060V1 [Cs.DC] 21 Nov 2017 When Embracing the Cloud
Efficient image deployment in Cloud environments Alvaro´ L´opez Garc´ıa∗, Enol Fern´andezdel Castillo Instituto de F´ısica de Cantabria | IFCA (CSIC|UC). Avda. los Castros s/n. 39005 Santander, Spain Abstract The biggest overhead for the instantiation of a virtual machine in a cloud in- frastructure is the time spent in transferring the image of the virtual machine into the physical node that executes it. This overhead becomes larger for re- quests composed of several virtual machines to be started concurrently, and the illusion of flexibility and elasticity usually associated with the cloud computing model may vanish. This poses a problem for both the resource providers and the software developers, since tackling those overheads is not a trivial issue. In this work we implement and evaluate several improvements for virtual machine image distribution problem in a cloud infrastructure and propose a method based on BitTorrent and local caching of the virtual machine images that reduces the transfer time when large requests are made. Keywords: Cloud Computing, Image Deployment, OpenStack, Scheduling 1. Introduction As it is widely known, the Cloud Computing model is aimed on deliver- ing resources (such as virtual machines, storage and network capacity) as an on demand service. The most accepted publication defining the Cloud from the United States National Institute of Standards and Technology (NIST), em- phasizes the rapid elasticity as one of the essential characteristics of the Cloud Computing model: \capabilities can be elastically provisioned and released, (...), to scale rapidly outward and inward (...)" [1]. Moreover, users and con- sumers consider them as the new key features that are more attractive [2, 3] arXiv:1711.08060v1 [cs.DC] 21 Nov 2017 when embracing the cloud. -

(12) United States Patent (10) Patent No.: US 7,984,116 B2 Hudson Et Al
USOO79841 16B2 (12) United States Patent (10) Patent No.: US 7,984,116 B2 Hudson et al. (45) Date of Patent: *Jul. 19, 2011 (54) CENTRALIZED SELECTION OF PEERS AS (56) References Cited MEDIA DATASOURCES IN A DSPERSED PEER NETWORK U.S. PATENT DOCUMENTS 5,740,170 A 4/1998 Andou et al. (75) Inventors: Michael D. Hudson, Portland, OR (US); 5,778,187 A 7/1998 Monteiro et al. Brian L. Windheim, Sherwood, OR 5,850,396 A 12, 1998 Gilbert (US); Darin Stewart, Hillsboro, OR 5,864,854 A 1/1999 Boyle (US); Sudhir Menon, Portland, OR 5,884,031 A 3, 1999 Ice (US); Mark W. Goschie, Tualatin, OR 5,944,780 A 8, 1999 Chase et al. (US); Glen Curtis Shipley, Portland, (Continued) OR (US) FOREIGN PATENT DOCUMENTS (73) Assignee: Sony Corporation (JP) WO WO-O2/O76003 A2 9, 2002 (*) Notice: Subject to any disclaimer, the term of this OTHER PUBLICATIONS patent is extended or adjusted under 35 U.S. Appl. No. 10/033,305, filed Oct. 1, 2007, Chapweske. U.S.C. 154(b) by 0 days. This patent is Subject to a terminal dis (Continued) claimer. Primary Examiner — Larry Donaghue Assistant Examiner — Nicholas Taylor (21) Appl. No.: 12/533,434 (74) Attorney, Agent, or Firm — Lerner, David, Littenberg, (22) Filed: Jul. 31, 2009 Krumholz & Mentlik, LLP (65) Prior Publication Data (57) ABSTRACT A multi-source peer content distribution system transfers US 201O/OO11061 A1 Jan. 14, 2010 content files from multiple, distributed peer computers to any Related U.S. Application Data requesting computer. The content distribution network coor dinates file transfers through a mediation system includings (63) Continuation of application No.