Bid Number: GEM/2020/B/559311 Dated: 20-02-2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Final Book Completed to Print in PRESS.Cdr
S.Alagiavanan 3rd CSE GRAPHIC CARDS: V.Narendran 3rd CSE HOW THEY WORK voultion of computing over the last decade EVER Yet very few of you know exactly how these has seen a distinct differentiation based on marvels work. Today's graphic cards are the nature of the workload. On the one WONDERED marvels of engineering, with over 50 times the E raw computational power of current CPUs, but hand you have the computing heavy tasks while on the other, there are graphics intensive tasks. Rewind WHAT GOES they have far more specific and streamlined a back a decade, and you will remember almost every ON BEHIND task. There are two aspects to understanding other motherboard having a dedicated display port how a graphics card works. The first is to as the graphics processor was onboard. Also some THE SCENES understand how it works with the rest of the present day processors which sport integrated WHEN YOU components in a personal computer to generate graphics also have IGP ports on the board. But with an image. The second part would be to the graphical workloads getting more advanced and POWER UP understand the role of major components on outputs more realistic, you would need to invest in a video card. dedicated graphics processing unit to divide tasks YOUR between the CPU and the GPU. Another advantage GAME? of having a dedicated graphics processing unit is the fact that it lets your CPU be free to perform READ ON. other tasks. For instance you can rip a movie in the background while playing a game. -

Scanned by Camscanner Annexure - 1 Broad Based Specifications for Forensic Platformfor National Cyber Forensic Laboratory
Scanned by CamScanner Annexure - 1 Broad Based Specifications for Forensic Platformfor National Cyber Forensic Laboratory S. No. Name of the Tool Specifications 1. The integrated Integrated platform that enables centralized case management and web-based access to various digital forensic tools. Forensic Platform Interface to distributed processing support, Role Assignment, Password Cracking and Recovery, Wizard-Driven Multi-Machine, for sharing Customizable Processing. theDigital Forensic Integrated Simultaneous access to Forensic Lab, Attorneys and Investigators through centralised management console via web interface. tools with suitable Automate email notifications regarding case state. Should include the following with APIs APIs. o FTK Standalone Perpetual Licences – 10 Nos. o AccessData Lab - FTK Connection – 10 Nos. o AccessData Lab - Web User Account – 10 Nos. o Magnet AXIOM Complete Perpetual Licences – 10 Nos. o Comprehensive Mac and iOS forensic analysis and reporting software – 10 Nos. o Belkasoft Evidence Centre Perpetual Licences with integration – 10 Nos. o SPEKTOR Drive with 64GB USB drive running SPEKTOR software Black fabric case 1 x 1 TB collector 1 x 8GB USB Drive for exporting FIVE years' support and updates – 10 Nos. The solution should be deployed/operated on the inhouse Data Centre at CFSL, Hyderabad. The required server hardware and software components for the Integrated API is the responsibility of the solution provider. The platform should be flexible enough to accommodate more number of licences as per the need in future. Perpetual Licencing with 03 years warranty with support for updates up to 05 years. Solution should include certified training for 10 Experts from OEM with in India or at OEM location. -

Title Smart Cites Forensics-Evaluating the Challenges of MK Smart City Forensics Name Ebenezer Okai
Title Smart Cites Forensics-Evaluating the Challenges of MK Smart City Forensics Name Ebenezer Okai This is a digitised version of a dissertation submitted to the University of Bedfordshire. It is available to view only. This item is subject to copyright. INSTITUTE FOR RESEARCH IN APPLICABLE COMPUTING (IRAC) MASTERS BY RESEARCH MODE OF STUDY: FULL TIME Ebenezer Okai ID: 0708426 Smart Cites Forensics-Evaluating the Challenges of MK Smart City Forensics June 2019 I | P a g e Declaration “I, Ebenezer Okai declare that this thesis and the work presented in it are my own and has been generated by me as the result of my own original research. I confirm that: • This work was done wholly or mainly while in candidature for a research degree at this University; • Where any part of this thesis has previously been submitted for a degree or any other qualification at this University or any other institution, this has been clearly stated; • Where I have drawn on or cited the published work of others, this is always clearly attributed; • Where I have quoted from the work of others, the source is always given. With the exception of such quotations, this thesis is entirely my own work; • I have acknowledged all main sources of help; • Where the thesis or any part of it is based on work done by myself jointly with others, I have made clear exactly what was done by others and what I have contributed myself; • Either none of this work has been published before submission, or parts of this work have been published. -

Scanned by Camscanner
Page 1 of 65. Scanned by CamScanner Broad Based Specifications of Vehicle for Scene of Crime Unit of National Cyber Forensic Laboratory for Evidentiary purpose S. No. Name of the Tool Specifications 2. Digital Forensic 1. Support collection of data from file systems including NTFS, FAT (12, 16 & 32 bit), EXFAT, HFS+, XFS, APFS, EXT2, EXT3 & Triage Tool Kit EXT4. 2. Support collection of data from both UEFI and BIOS based systems. 3. Support Profile configuration based on case. 4. Support digital forensic triage from powered off computers (Desktops, Laptops, Servers aka windows/linux/iOS)and running Windows computers(NTFS/FAT). 5. Support capture of volatile data/memory (RAM capture) 6. Support collection of Files from Removable Media (e.g. USB Drives) 7. Support collection of Files from Forensic Images (E01, DD etc.) 8. Support collection of files from Devices with Internal Memory Storage E.g. Digital Cameras. 9. Support physical backup to be supported by popular digital forensic tools. 10. Support extraction of data from Customised Locations. 11. Support data collection from mounted encrypted partitions. 12. Support automated analysis and report generation in PDF/HTML/DOCX of files collected from a target device. 13. Support automatic Logging (Device, Processing & User Interaction) of activities. 14. Support filter of data by Criteria to Target Specific Results. 15. Support Identify, Process and Display Browser History, Display Contents of E-Mail, Chat, Social Media Artefacts. 16. Support automatic indexing and tagging of hash and keyword matches. 17. Support time lining. 18. Solution in a ruggedized portable system with suitable processing and configuration as below: a. -

All-In-One Cloud Storage Gateways with Integrated Data Protection And
CTERA C400 / C800 Cloud Attached Storage® Appliances All-in-One Cloud Storage Gateways with Integrated Data Protection and Network Attached Storage Integrated On-Site & Off-Site Data Backup and Disaster Recovery Robust Enterprise-Grade NAS Features Cloud File Sharing and Synchronization Hybrid Storage Appliances with Integrated Cloud Services for SMBs and Branch Offices The C400 and C800 appliances from CTERA Networks combine network attached storage (NAS) functionality with comprehensive data protection, providing fast local backup & recovery integrated with cloud storage for disaster recovery, remote access and file sharing. With the included CTERA backup software, managed agents, remote management capabilities and end-to-end data protection, the C400 and C800 provide a highly cost-effective, easy-to-manage alternative to more expensive, disparate solutions. Lightning-fast on-site backup and restore, with integrated, globally de-duplicated, Hybrid Cloud & On-Premises efficient cloud backup that provides an off-site copy for disaster recovery. Protect the business against data loss and minimize disaster recovery time using a Complete Data Protection single solution – including roaming laptops, remote users, servers and workstations. Full-fledged NAS appliances supporting RAID 5/6 for redundancy, inline volume Robust Network Storage encryption, thin-provisioned snapshots, iSCSI and Active Directory integration. Using the CTERA Portal, service providers and enterprise IT can manage and Central Management monitor any number of CTERA appliances from a unified Web console. Access local and cloud-stored files from anywhere, on locally or over the Web. File-Based Collaboration Share files with project groups and occasional users with email invitations. Synchronize files to and from the cloud between multiple users. -

Latest
stfc-cloud-docs Documentation Release 1.0 CloudTeam Aug 19, 2021 Getting Started: 1 Common Commands 1 2 How-To Articles 3 3 Policies 37 4 Contact Details 41 5 FAQS 43 6 Fault Fixes 51 7 Flavors 53 8 Image Types 55 9 Reference Documents 57 10 Aodh and Gnocchi 73 11 Improving this Documentation 93 12 Heat 95 13 Magnum 117 14 Octavia 147 15 Legacy Documentation 173 16 Indices and tables 179 i ii CHAPTER 1 Common Commands On Queens, Hypervisors often disable themselves and remove their services from the pool of resources if there are 10 build failures in a row on a hypervisor. 1.1 List available images To list available images do: openstack image list 1.2 List available flavors To list available flavors run: openstack flavor list 1.3 List available networks To list available networks run: openstack network list 1.4 List running servers Showing all hosts in your current projects: 1 stfc-cloud-docs Documentation, Release 1.0 openstack server list 1.5 Show a specific server Looking at a specific server:- openstack server show <server ID> 2 Chapter 1. Common Commands CHAPTER 2 How-To Articles 2.1 Adding Your SSH Key into the OpenStack Web Interface 2.1.1 Overview This document describes how to add your public ssh key into the openstack ssh web user interface (https://openstack. stfc.ac.uk). It assumes you have already contacted [email protected] to either initiate a project, or to add user accounts to an existing project. It also assumes you already have an SSH key pair generated, and you just wish to add your existing public ssh key. -

X-Ways Forensics & Winhex Manual
X-Ways Software Technology AG X-Ways Forensics/ WinHex Integrated Computer Forensics Environment. Data Recovery & IT Security Tool. Hexadecimal Editor for Files, Disks & RAM. Manual Copyright © 1995-2021 Stefan Fleischmann, X-Ways Software Technology AG. All rights reserved. Contents 1 Preface ..................................................................................................................................................1 1.1 About WinHex and X-Ways Forensics.........................................................................................1 1.2 Legalities.......................................................................................................................................2 1.3 License Types ...............................................................................................................................4 1.4 More differences between WinHex & X-Ways Forensics............................................................5 1.5 Getting Started with X-Ways Forensics........................................................................................6 2 Technical Background ........................................................................................................................7 2.1 Using a Hex Editor........................................................................................................................7 2.2 Endian-ness...................................................................................................................................8 2.3 Integer -

Generating Computer Forensic Supertimelines Under Linux
Generating computer forensic super- timelines under Linux A comprehensive guide for Windows-based disk images R. Carbone Certified Hacking Forensic Investigator (EC-Council) DRDC Valcartier C. Bean Certified Hacking Forensic Investigator (EC Council) Defence R&D Canada – Valcartier Technical Memorandum DRDC Valcartier TM 2011-216 October 2011 Generating computer forensic super- timelines under Linux A comprehensive guide for Windows-based disk images R. Carbone Certified Hacking Forensic Investigator (EC Council) DRDC Valcartier C. Bean Certified Hacking Forensic Investigator (EC Council) Defence R&D Canada – Valcartier Technical Memorandum DRDC Valcartier TM 2011-216 October 2011 Principal Author Richard Carbone Programmer/Analyst Approved by Guy Turcotte Head/System of Systems Approved for release by Christian Carrier Chief Scientist © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2011 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2011 Abstract …….. This technical memorandum examines the basics surrounding computer forensic filesystem timelines and provides an enhanced approach to generating superior timelines for improved filesystem analysis and contextual awareness. Timelines are improved by polling multiple sources of information across the filesystem resulting in an approach that is surprisingly flexible and customizable. The timeline is further enhanced by incorporating key time-based metadata found across a disk image which, when taken as a whole, increases the forensic investigator’s understanding. Résumé …..... Ce mémorandum technique examine les bases entourant la création d’un calendrier des événements inforensiques des systèmes de fichier et fournit une approche améliorée pour générer des calendriers supérieurs pour une analyse améliorée des systèmes de fichiers et un meilleur éveil contextuel. -

All-In-One Network Attached Storage, Backup Appliance and Gateway To
CTERA C200 Cloud Attached Storage® Appliance All-in-One Network Attached Storage, Backup Appliance and Gateway to Cloud Services Integrated On-Site & Cloud Backup and Recovery Remote Access and Central Management File Sharing on The Local Network and in The Cloud Hybrid 2-Bay Storage Appliance with Integrated Cloud Services for Small Business and Offices Ideal for small businesses and branch offices, the CTERA C200 appliance combines network attached storage (NAS) functionality with comprehensive data protection, providing fast local backup & recovery integrated with cloud storage for backup, remote access and file sharing. With the included CTERA backup software, managed agents, remote management capabilities and end-to-end data protection, the C200 provides a cost-effective, easy-to-manage alternative to more expensive, disparate solutions. Lightning-fast on-site backup and restore, with integrated, globally de-duplicated, Hybrid Cloud & On-Premises efficient cloud backup that provides an off-site copy for disaster recovery. Protect the business against data loss and minimize disaster recovery time using a Complete Data Protection single solution – including roaming laptops, remote users, servers and workstations. Using the CTERA Portal, MSPs and enterprise IT administrators can manage and Central Management monitor any number of CTERA appliances from a unified Web console. Access local and cloud-stored files from anywhere, locally or over the Web. Share File-Based Collaboration files with project groups and occasional users with -
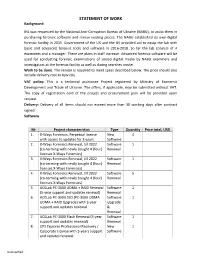
STATEMENT of WORK Background
STATEMENT OF WORK Background: INL was requested by the National Anti-Corruption Bureau of Ukraine (NABU), to assist them in purchasing forensic software and renew existing pieces. The NABU established its own digital forensic facility in 2015. Government of the UK and the US provided aid to equip the lab with basic and advanced forensic tools and software in 2016-2018. So far the lab consists of 4 examiners and a manager. There are plans in staff increase. Advanced forensic software will be used for conducting forensic examinations of seized digital media by NABU examiners and investigators at the forensic facility as well as during searches onsite. Work to be done. The vendor is required to meet specs described below. The price should also include delivery cost to Kyiv city. VAT policy: This is a technical assistance Project registered by Ministry of Economic Development and Trade of Ukraine. The offers, if applicable, may be submitted without VAT. The copy of registration card of the project and procurement plan will be provided upon request. Delivery: Delivery of all items should not exceed more than 30 working days after contract signed. Software № Project characteristics Type Quantity Price total, USD 1. X- Ways Forensics, Perpetual license New 4 with access to updates for 3 years Software 2. X- Ways Forensics Renewal, till 2022 Software 1 (co-terming with newly bought 4 (four) Renewal licenses X-Ways Forensics) 3. X- Ways Forensics Renewal, till 2022 Software 1 (co-terming with newly bought 4 (four) Renewal licenses X-Ways Forensics) 4. X- Ways Forensics Renewal, till 2022 Software 5 (co-terming with newly bought 4 (four) Renewal licenses X-Ways Forensics) 5. -

Gctrees: Garbage Collecting Snapshots
GCTrees: Garbage Collecting Snapshots Chris Dragga and Douglas J. Santry Advanced Technology Group, NetApp Inc. [email protected], [email protected] Abstract—File-system snapshots have been a key component There are many advantages to employing shared storage. of enterprise storage management since their inception. Creating Shared storage offers location transparency, disaster recovery, and managing them efficiently, while maintaining flexibility and and advanced data management features. Snapshots have be- low overhead, has been a constant struggle. Although the cur- come an indispensable tool for data management. Snapshots rent state-of-the-art mechanism, hierarchical reference counting, offer a consistent read-only point-in-time view of a file system. performs reasonably well for traditional small-file workloads, Such views are important when a consistent backup is required. these workloads are increasingly vanishing from the enterprise data center, replaced instead with virtual machine and database Snapshots can also be used to conveniently recover from data workloads. These workloads center around a few very large files, loss, potentially without the need for a system administrator’s violating the assumptions that allow hierarchical reference count- assistance. ing to operate efficiently. To better cope with these workloads, we introduce GCTrees, a novel method of space management A space-efficient implementation of snapshots has to man- that uses concepts of block lineage across snapshots, rather than age block sharing well. As a result, snapshot implementations explicit reference counting. As a proof of concept, we create a must be able to efficiently detect which blocks are shared. prototype file system, gcext4, a modified version of ext4 that uses Consider a new snapshot. -

HP Smartstart Scripting Toolkit Windows Edition User Guide
HP SmartStart Scripting Toolkit Windows Edition User Guide Part Number 415598-006 January 2008 (Sixth Edition) © Copyright 2005, 2008 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein. Confidential computer software. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s standard commercial license. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. Windows Server 2003 and Windows Server 2008 are trademarks of Microsoft Corporation. AMD is a trademark of Advanced Micro Devices, Inc. Audience assumptions The Toolkit is designed for IT experts with experience in scripting operating system installations and configuring HP ProLiant server hardware. Contents Introduction.................................................................................................................................. 5 SmartStart Scripting Toolkit ......................................................................................................................... 5 Microsoft