J2EE Patterns and J2EE Platform Summary
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ioc Containers in Spring
301AA - Advanced Programming Lecturer: Andrea Corradini [email protected] http://pages.di.unipi.it/corradini/ AP-2018-11: Frameworks and Inversion of Control Frameworks and Inversion of Control • Recap: JavaBeans as Components • Frameworks, Component Frameworks and their features • Frameworks vs IDEs • Inversion of Control and Containers • Frameworks vs Libraries • Decoupling Components • Dependency Injection • IoC Containers in Spring 2 Components: a recap A software component is a unit of composition with contractually specified interfaces and explicit context dependencies only. A software component can be deployed independently and is subject to composition by third party. Clemens Szyperski, ECOOP 1996 • Examples: Java Beans, CLR Assemblies • Contractually specified interfaces: events, methods and properties • Explicit context dependencies: serializable, constructor with no argument • Subject to composition: connection to other beans – Using connection oriented programming (event source and listeners/delegates) 3 Towards Component Frameworks • Software Framework: A collection of common code providing generic functionality that can be selectively overridden or specialized by user code providing specific functionality • Application Framework: A software framework used to implement the standard structure of an application for a specific development environment. • Examples: – GUI Frameworks – Web Frameworks – Concurrency Frameworks 4 Examples of Frameworks Web Application Frameworks GUI Toolkits 5 Examples: General Software Frameworks – .NET – Windows platform. Provides language interoperability – Android SDK – Supports development of apps in Java (but does not use a JVM!) – Cocoa – Apple’s native OO API for macOS. Includes C standard library and the Objective-C runtime. – Eclipse – Cross-platform, easily extensible IDE with plugins 6 Examples: GUI Frameworks • Frameworks for Application with GUI – MFC - Microsoft Foundation Class Library. -

Design Pattern Interview Questions
DDEESSIIGGNN PPAATTTTEERRNN -- IINNTTEERRVVIIEEWW QQUUEESSTTIIOONNSS http://www.tutorialspoint.com/design_pattern/design_pattern_interview_questions.htm Copyright © tutorialspoint.com Dear readers, these Design Pattern Interview Questions have been designed specially to get you acquainted with the nature of questions you may encounter during your interview for the subject of Design Pattern. As per my experience good interviewers hardly plan to ask any particular question during your interview, normally questions start with some basic concept of the subject and later they continue based on further discussion and what you answer: What are Design Patterns? Design patterns represent the best practices used by experienced object-oriented software developers. Design patterns are solutions to general problems that software developers faced during software development. These solutions were obtained by trial and error by numerous software developers over quite a substantial period of time. What is Gang of Four GOF? In 1994, four authors Erich Gamma, Richard Helm, Ralph Johnson and John Vlissides published a book titled Design Patterns - Elements of Reusable Object-Oriented Software which initiated the concept of Design Pattern in Software development. These authors are collectively known as Gang of Four GOF. Name types of Design Patterns? Design patterns can be classified in three categories: Creational, Structural and Behavioral patterns. Creational Patterns - These design patterns provide a way to create objects while hiding the creation logic, rather than instantiating objects directly using new opreator. This gives program more flexibility in deciding which objects need to be created for a given use case. Structural Patterns - These design patterns concern class and object composition. Concept of inheritance is used to compose interfaces and define ways to compose objects to obtain new functionalities. -

A Survey of Architectural Styles.V4
Survey of Architectural Styles Alexander Bird, Bianca Esguerra, Jack Li Liu, Vergil Marana, Jack Kha Nguyen, Neil Oluwagbeminiyi Okikiolu, Navid Pourmantaz Department of Software Engineering University of Calgary Calgary, Canada Abstract— In software engineering, an architectural style is a and implementation; the capabilities and experience of highest-level description of an accepted solution to a common developers; and the infrastructure and organizational software problem. This paper describes and compares a selection constraints [30]. These styles are not presented as out-of-the- of nine accepted architectural styles selected by the authors and box solutions, but rather a framework within which a specific applicable in various domains. Each pattern is presented in a software design may be made. If one were to say “that cannot general sense and with a domain example, and then evaluated in be called a layered architecture because the such and such a terms of benefits and drawbacks. Then, the styles are compared layer must communicate with an object other than the layer in a condensed table of advantages and disadvantages which is above and below it” then one would have missed the point of useful both as a summary of the architectural styles as well as a architectural styles and design patterns. They are not intended tool for selecting a style to apply to a particular project. The to be definitive and final, but rather suggestive and a starting paper is written to accomplish the following purposes: (1) to give readers a general sense of several architectural styles and when point, not to be used as a rule book but rather a source of and when not to apply them, (2) to facilitate software system inspiration. -

Diplomarbeit Im Fachbereich Elektrotechnik & Informatik an Der
Bachelor Thesis Prannoy Mulmi Design and Implementation of an Archive Microservice solution for the Multi-Agent Research and Simulation Distributed System Fakultät Technik und Informatik Faculty of Engineering and Computer Science Department Informations- und Department of Information and Elektrotechnik Electrical Engineering Prannoy Mulmi Design and Implementation of an Archive Microservice solution for the Multi-Agent Research and Simulation Distributed System Bachelor Thesis based on the study regulations for the Bachelor of Engineering degree programme Information Engineering at the Department of Information and Electrical Engineering of the Faculty of Engineering and Computer Science of the Hamburg University of Applied Sciences Supervising examiner : Prof. Dr. rer. nat. Henning Dierks Second Examiner : Prof. Dr. rer. nat. Thomas Clemen Day of delivery 23. Juli 2018 Prannoy Mulmi Title of the Bachelor Thesis Design and Implementation of an Archive Microservice solution for the Multi-Agent Research and Simulation Distributed System Keywords Distributed System, Microservice, Two-Phase commit protocol, Archive, Decentrali- zed data, Multi-Agent Research and Simulation (MARS) Abstract This thesis introduces the design and implementation of an Archive Microservice in the Multi-Agent Research and Simulation (MARS) framework. Due to the distributed architecture of the system, the process of the archive and restore is complex to imple- ment and maintain as there multiple possibilities of failure. This thesis uses different strategies to -

Methods & Tools
METHODS & TOOLS Practical knowledge for the software developer, tester and project manager ISSN 1661-402X Spring 2011 (Volume 19 - number 1) www.methodsandtools.com The Salesmen/Developers Ratio at Software Vendors Many of us might think that software is a technological industry. Maybe. But maybe not. If you consider Oracle or Microsoft, I suppose that few of us would consider them as technology leaders, but we will all recognize their financial strength and marketing power. Long lasting organizations in the software industry might have more financial strength than technological capabilities. The recent conflict between Oracle and the creator of Hudson, an open source continuous integration server, is just another episode in the opposition between developers- and salesmen-driven software companies. On one side you have Oracle, for which Hudson is just small project inherited from the Sun buyout and that owns the "Hudson" brand. On the other side, you find Kohsuke Kawaguchi, who created Hudson and wants keep some control on its development. Hudson has been "forked", the open source code being used to start another project. You now have a Jenkins CI project that includes most of the active Hudson contributors and a Hudson CI project backed by Oracle and Sonatype, the commercial company behind the Maven project. Everything is however not black and white. Kohsuke Kawaguchi has joined Cloudbees, a company that has some management and financing coming from ex-JBoss managers, people that know how to make money with open source software. These people are not working hard for the only sake of technology evolution. You can judge the main orientation of a company looking at its salesmen/developers ratios. -

Dependency Injection with Unity
D EPEN DEPENDENCY INJECTION WITH UNITY Over the years software systems have evolutionarily become more and more patterns & practices D ENCY complex. One of the techniques for dealing with this inherent complexity Proven practices for predictable results of software systems is dependency injection – a design pattern that I allows the removal of hard-coded dependencies and makes it possible to Save time and reduce risk on your NJECT assemble a service by changing dependencies easily, whether at run-time software development projects by or compile-time. It promotes code reuse and loosely-coupled design which incorporating patterns & practices, I leads to more easily maintainable and flexible code. Microsoft’s applied engineering ON guidance that includes both production The guide you are holding in your hands is a primer on using dependency quality source code and documentation. W I injection with Unity – a lightweight extensible dependency injection TH DEPENDENCY INJECTION container built by the Microsoft patterns & practices team. It covers The guidance is designed to help U software development teams: various styles of dependency injection and also additional capabilities N I of Unity container, such as object lifetime management, interception, Make critical design and technology TY and registration by convention. It also discusses the advanced topics of selection decisions by highlighting WITH UNITY enhancing Unity with your custom extensions. the appropriate solution architectures, technologies, and Microsoft products The guide contains plenty of trade-off discussions and tips and tricks for for common scenarios managing your application cross-cutting concerns and making the most out of both dependency injection and Unity. These are accompanied by a Understand the most important Dominic Betts real world example that will help you master the techniques. -

Designpatternsphp Documentation Release 1.0
DesignPatternsPHP Documentation Release 1.0 Dominik Liebler and contributors Jul 18, 2021 Contents 1 Patterns 3 1.1 Creational................................................3 1.1.1 Abstract Factory........................................3 1.1.2 Builder.............................................8 1.1.3 Factory Method......................................... 13 1.1.4 Pool............................................... 18 1.1.5 Prototype............................................ 21 1.1.6 Simple Factory......................................... 24 1.1.7 Singleton............................................ 26 1.1.8 Static Factory.......................................... 28 1.2 Structural................................................. 30 1.2.1 Adapter / Wrapper....................................... 31 1.2.2 Bridge.............................................. 35 1.2.3 Composite............................................ 39 1.2.4 Data Mapper.......................................... 42 1.2.5 Decorator............................................ 46 1.2.6 Dependency Injection...................................... 50 1.2.7 Facade.............................................. 53 1.2.8 Fluent Interface......................................... 56 1.2.9 Flyweight............................................ 59 1.2.10 Proxy.............................................. 62 1.2.11 Registry............................................. 66 1.3 Behavioral................................................ 69 1.3.1 Chain Of Responsibilities................................... -
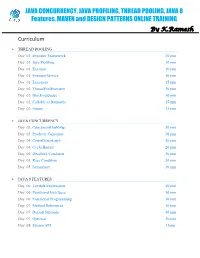
JAVA CONCURRENCY ONLINE TRAINING – Java2aspire
JAVA CONCURRENCY, JAVA PROFILING, THREAD POOLING, JAVA 8 Features, MAVEN and DESIGN PATTERNS ONLINE TRAINING By K.Ramesh Curriculum THREAD POOLING Day 01: Executor Framework 20 min Day 01: Java Profiling 10 min Day 01: Executor 10 min Day 01: ExecutorService 10 min Day 01: Executors 15 min Day 02: ThreadPoolExecutor 20 min Day 02: BlockingQueue 10 min Day 02: Callable vs Runnable 15 min Day 02: Future 15 min JAVA CONCURRENCY Day 03: ConcurrentHashMap 30 min Day 03: Producer Consumer 30 min Day 04: CountDownLatch 20 min Day 04: CyclicBarrier 20 min Day 04: Deadlock Condition 20 min Day 05: Race Condition 30 min Day 05: Semaphore 30 min JAVA 8 FEATURES Day 06: Lambda Expressions 40 min Day 06: Functional Interfaces 10 min Day 06: Functional Programming 10 min Day 07: Method References 10 min Day 07: Default Methods 40 min Day 07: Optional 10 min Day 08: Stream API 1 hour MAVEN Day 09: Project Object Model (POM) 20 min Day 09: Project Description 10 min Day 09: Public Repository 10 min Day 09: Dependency Management 10 min Day 09: Build Configuration 10 min Day 10: Installation 15 min Day 10: Dependency Scope 15 min Day 10: Proprietary Dependencies 15 min Day 10: Project Inheritance 15 min Day 11: Maven life cycle 20 min Day 11: Maven Directory Structure 20 min Day 11: Archetypes 20 min Day 12: Applications 1 hour DESIGN PATTERNS Day 13: Factory Pattern 20 min Day 13: Abstract Factory Pattern 10 min Day 13: Single Pattern 20 min Day 13: Prototype Pattern 10 min Day 14: Composite Pattern 10 min Day 14: Facade Pattern 15 min Day 14: DAO -

A Design Pattern Approach
Wright State University CORE Scholar Browse all Theses and Dissertations Theses and Dissertations 2009 Automated Transforms of Software Models: A Design Pattern Approach Brandon Adam Gump Wright State University Follow this and additional works at: https://corescholar.libraries.wright.edu/etd_all Part of the Computer Sciences Commons Repository Citation Gump, Brandon Adam, "Automated Transforms of Software Models: A Design Pattern Approach" (2009). Browse all Theses and Dissertations. 969. https://corescholar.libraries.wright.edu/etd_all/969 This Thesis is brought to you for free and open access by the Theses and Dissertations at CORE Scholar. It has been accepted for inclusion in Browse all Theses and Dissertations by an authorized administrator of CORE Scholar. For more information, please contact [email protected]. AUTOMATED TRANSFORMS OF SOFTWARE MODELS: A DESIGN PATTERN APPROACH A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science By BRANDON ADAM GUMP B.S., Wright State University, 2008 2009 Wright State University WRIGHT STATE UNIVERSITY SCHOOL OF GRADUATE STUDIES November 23, 2009 I HEREBY RECOMMEND THAT THE THESIS PREPARED UNDER MY SUPERVISION BY Brandon Adam Gump ENTITLED Automated Transforms of Software Models: A Design Pattern Approach BE ACCEPTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF Master of Science . Thomas C. Hartrum, Ph.D. Thesis Co-Director Mateen M. Rizki, Ph.D. Thesis Co-Director Thomas A. Sudkamp, Ph.D. Department Chair Committee on Final Examination Thomas C. Hartrum, Ph.D. Mateen M. Rizki, Ph.D. Travis E. Doom, Ph.D. Joseph F. Thomas, Jr., Ph.D. Dean, School of Graduate Studies ABSTRACT Gump, Brandon Adam. -

Semantic Description of Services and Service Factories for Ambient Intelligence Rémi Emonet
Semantic Description of Services and Service Factories for Ambient Intelligence Rémi Emonet To cite this version: Rémi Emonet. Semantic Description of Services and Service Factories for Ambient Intelligence. Soft- ware Engineering [cs.SE]. Institut National Polytechnique de Grenoble - INPG, 2009. English. tel- 00450479 HAL Id: tel-00450479 https://tel.archives-ouvertes.fr/tel-00450479 Submitted on 26 Jan 2010 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. GRENOBLE INP n◦ attribu´epar la biblioth`eque THESE` pour obtenir le grade de ❉♦❝❡✉ ❉✉ ●♦✉♣❡ ●❡♥♦❜❧❡ ■◆ Sp´ecialit´e: Informatique pr´epar´eeau Laboratoire d’Informatique de Grenoble dans le cadre de l’Ecole´ Doctorale Math´ematiques, Sciences et Technologies de l’Information, Informatique pr´esent´eeet soutenue publiquement par R´emi ❊♠♦♥❡ le 23 septembre 2009 ❉❡❝✐♣✐♦♥ ❙♠❛♥✐✉❡ ❞❡ ❙❡✈✐❝❡ ❡ ❞✬❯✐♥❡ à ❙❡✈✐❝❡ ♣♦✉ ❧✬■♥❡❧❧✐❣❡♥❝❡ ❆♠❜✐❛♥❡ ❙❡♠❛♥✐❝ ❉❡❝✐♣✐♦♥ ♦❢ ❙❡✈✐❝❡ ❛♥❞ ❙❡✈✐❝❡ ❋❛❝♦✐❡ ❢♦ ❆♠❜✐❡♥ ■♥❡❧❧✐❣❡♥❝❡ Directeur de th`ese : James L. ❈♦✇❧❡② Co-directeur de th`ese : Dominique ❱❛✉❢❡②❞❛③ JURY Pr. Marie-Christine Rousset Pr´esident Pr. James L. Crowley Directeur de th`ese Dr. Dominique Vaufreydaz Co-directeur de th`ese Pr. Gregory D. Abowd Rapporteur Pr. David Simplot-Ryl Rapporteur Pr. Michel Riveill Examinateur 2 R´esum´e Ce manuscrit ´etudie l’ad´equation des approches `aservices, ainsi que leur am´elioration, pour l’int´egration dynamique et la r´eutilisation logicielle dans le cadre de l’informatique ambiante. -

Design Optimizations of Enterprise Applications – a Literature Survey
Design Optimizations of Enterprise Applications – A Literature Survey Willie (Phong) Tu Dept. of Computer Science, University of Calgary [email protected] Abstract Another dimension is the performance improvement for the single user versus multiple users, in other words, Software design patterns have been defined as scalability. The design optimization patterns noted here possible solutions to reoccurring problems. One aspect will focus on actual running time of operations for of the problems is performance. This can be arguably single user performance and multi-user scalability true in high volume enterprise applications. This paper improvements. will explore the current discussions and research in The organization of the findings is categorized utilization of software design patterns to optimize through the usage of an architectural pattern, which is enterprise applications. defined as layer [5]. The layers used are the primary three-layer architecture for information systems [10,21], which includes the data access layer, domain layer, and 1. Introduction presentation layer. Design optimization patterns that spans layers will be elaborated first, then a bottom up First, let’s define what is design optimization. In this approach starting with the data access layer, followed by context, design optimization is the improvement of an the domain layer, and finally the presentation layer. We application’s design and performance using software will then continue on with findings from different design patterns. Design improvements can be subjective, enterprise applications. After which, we will summarize thus the main qualifier is the utilization of software the current state in design optimizations of enterprise design patterns to improve the performance of an applications based on the findings. -

Sun Certified Enterprise Architect for Java EE Study Guide / Mark Cade, Humphrey Sheil
Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. Sun Microsystems, Inc. has intellectual property rights relating to implementations of the technology described in this publication. In particular, and without limitation, these intellectual property rights may include one or more U.S. patents, foreign patents, or pending applications. Sun, Sun Microsystems, the Sun logo, J2ME, J2EE, Java Card, and all Sun and Java based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc., in the United States and other countries. UNIX is a registered trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. This publication is provided “as is” without warranty of any kind, either express or implied, including, but not limited to, the implied warranties of merchantability, fitness for a particular purpose, or non-infringement. This publication could include technical inaccuracies or typographical errors. Changes are periodically added to the information herein; these changes will be incorporated in new editions of the publication. Sun Microsystems, Inc. may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time. The authors and publisher have taken care in the preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein.