^`Nrfpfqflk=Oةًة~يإ = Pىهمًهيةا=Oةىهيٍ=ًةيفةً=
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Openscenegraph 3.0 Beginner's Guide
OpenSceneGraph 3.0 Beginner's Guide Create high-performance virtual reality applications with OpenSceneGraph, one of the best 3D graphics engines Rui Wang Xuelei Qian BIRMINGHAM - MUMBAI OpenSceneGraph 3.0 Beginner's Guide Copyright © 2010 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the authors, nor Packt Publishing and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: December 2010 Production Reference: 1081210 Published by Packt Publishing Ltd. 32 Lincoln Road Olton Birmingham, B27 6PA, UK. ISBN 978-1-849512-82-4 www.packtpub.com Cover Image by Ed Maclean ([email protected]) Credits Authors Editorial Team Leader Rui Wang Akshara Aware Xuelei Qian Project Team Leader Reviewers Lata Basantani Jean-Sébastien Guay Project Coordinator Cedric Pinson -

Symantec™ Data Loss Prevention Third-Party License Agreements
Symantec™ Data Loss Prevention Third-Party License Agreements Version 15.1 Symantec Data Loss Prevention Third-Party License Agreements Documentation version: 15.1 Legal Notice Copyright © 2018 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo and the Checkmark Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. This Symantec product may contain third party software for which Symantec is required to provide attribution to the third party (“Third Party Programs”). Some of the Third Party Programs are available under open source or free software licenses. The License Agreement accompanying the Software does not alter any rights or obligations you may have under those open source or free software licenses. Please see the Third Party Legal Notice Appendix to this Documentation or TPIP ReadMe File accompanying this Symantec product for more information on the Third Party Programs. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. -

Crossmark Content Copyright Information
CrossMark Content Copyright Information In addition to BAPCo produced content and source code, BAPCo CrossMark uses licensed libraries listed below in the benchmark programs. OpenCV, Opencv Contrib By downloading, copying, installing or using the software you agree to this license. If you do not agree to this license, do not download, install,copy or use the software. License Agreement For Open Source Computer Vision Library (3-clause BSD License) Copyright (C) 2000-2019, Intel Corporation, all rights reserved. Copyright (C) 2009-2011, Willow Garage Inc., all rights reserved. Copyright (C) 2009-2016, NVIDIA Corporation, all rights reserved. Copyright (C) 2010-2013, Advanced Micro Devices, Inc., all rights reserved. Copyright (C) 2015-2016, OpenCV Foundation, all rights reserved. Copyright (C) 2015-2016, Itseez Inc., all rights reserved. Third party copyrights are property of their respective owners. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: * Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. * Neither the names of the copyright holders nor the names of the contributors may be used to endorse or promote products derived from this software without specific prior written permission. This software is provided by the copyright holders and contributors "as is" and any express or implied warranties, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose are disclaimed. -

Open Source Software License
Open Source Software License Contents Open Source Software License.................................................................................................................. 5 Copyright Attribution ................................................................................................................................ 83 3 Open Source Software License GNU GPL This projector product includes the open source software programs which apply the GNU General Public License Version 2 (June 1991) ("GPL Programs"). We provide the source code of the GPL Programs until five (5) years after the discontinuation of same model of this projector product. If you desire to receive the source code of the GPL Programs, contact Epson. These GPL Programs are WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. The list of GPL Programs is as follows and the names of author are described in the source code of the GPL Programs The list of GPL Programs • busybox-1.21.0 • iptables-1.4.21 • linaro-lsk-v4.4 • patches • kernel driver • udhcp 0.9.8 • wireless_tools 29 • dibbler-1.0.1 • backports v4.14-rc2 • Cypress Wi-Fi Linux FMAC Driver • e2fsprogs 1.44.4 • busybox V1.4 • ION Driver • libaio • OpenMAX 5 • U-Boot V2017.11 • eudev The GNU General Public License Version 2 is as follows. You also can see the GNU General Public License Version 2 at http://www.gnu.org/licenses/. GNU GENERAL PUBLIC LICENSE Version 2, June 1991 Copyright (C) 1989, 1991 Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. -

Why Open Source Software / Free Software (OSS/FS, FLOSS, Or FOSS)? Look at the Numbers!
Translations available: Czech | French | Japanese | Spanish Why Open Source Software / Free Software (OSS/FS, FLOSS, or FOSS)? Look at the Numbers! David A. Wheeler http://www.dwheeler.com/contactme.html Revised as of July 18, 2015 This paper (and its supporting database) provides quantitative data that, in many cases, using open source software / free software (abbreviated as OSS/FS, FLOSS, or FOSS) is a reasonable or even superior approach to using their proprietary competition according to various measures. This paper’s goal is to show that you should consider using OSS/FS when acquiring software. This paper examines popularity, reliability, performance, scalability, security, and total cost of ownership. It also has sections on non-quantitative issues, unnecessary fears, OSS/FS on the desktop, usage reports, governments and OSS/FS, other sites providing related information, and ends with some conclusions. An appendix gives more background information about OSS/FS. You can view this paper at http://www.dwheeler.com/oss_fs_why.html (HTML format). A short presentation (briefing) based on this paper is also available. Palm PDA users may wish to use Plucker to view this longer report. Old archived copies and a list of changes are also available. 1. Introduction Open Source Software / Free Software (aka OSS/FS), also described as Free/Libre and Open Source Software (FLOSS), has risen to great prominence. Briefly, FLOSS programs are programs whose licenses give users the freedom to run the program for any purpose, to study and modify the program, and to redistribute copies of either the original or modified program (without having to pay royalties to previous developers). -

License Compliance
License Compliance Required information as per the licenses of used algorithm and libraries Product: Guiliani Streaming Editor (GSE) Release version: 2.4 Release date: April 6, 2021 Table of contents 1 Introduction .............................................................................................................................. 3 2 Used algorithms........................................................................................................................ 3 2.1 md5 .................................................................................................................................... 3 2.2 AES .................................................................................................................................... 3 3 Used libraries: .......................................................................................................................... 3 3.1 libjpeg ................................................................................................................................ 3 3.2 libgif .................................................................................................................................. 3 3.3 libpng ................................................................................................................................. 3 3.4 zlib ..................................................................................................................................... 3 3.5 freetype ............................................................................................................................. -
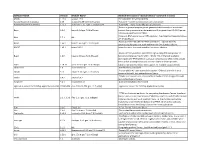
List of Software
Software Name Version Module Name Module Description ("module whatis" command in Linux) ADIOS 1.12.0 adios/1.12.0 The Adaptable IO System (ADIOS). Autoconf (part of autotools) 2.69 autoconf-2.69-gcc-7.2.0-sayraxx Autoconf -- system configuration part of autotools Automake (part of autotools) 1.15.1 automake-1.15.1-gcc-7.2.0-kyu5v74 Automake -- make file builder part of autotools Bison is a general-purpose parser generator that converts an annotated Bison 3.0.4 bison-3.0.4-gcc-7.2.0-nl7vmez context-free grammar into a deterministic LR or generalized LR (GLR) parser employing LALR(1) parser tables. Compares DNA sequences to NCBI database. /opt/ohpc/pub/apps/ncbi-blast- Blast 2.7.1 NA 2.7.1+/bin/blastn Boost provides free peer-reviewed portable C++ source libraries, Boost 1.66.0 boost-1.66.0-gcc-7.2.0-lh7j247 emphasizing libraries that work well with the C++ Standard Library. BOOST 1.65.1 boost/1.65.1 Boost free peer-reviewed portable C++ source libraries. bzip2 is a freely available, patent free high-quality data compressor. It Bzip2 1.0.6 bzip2-1.0.6-gcc-7.2.0-57yzgp6 typically compresses files to within 10% to 15% of the best available techniques (the PPM family of statistical compressors), whilst being around twice as fast at compression and six times faster at decompression. Cairo 1.14.12 cairo-1.14.12-gcc-7.2.0-nf3rapy Cairo is a 2D graphics library with support for multiple output devices. -

Conan Documentation Release 1.7.4
conan Documentation Release 1.7.4 conan Sep 24, 2021 CONTENTS 1 Introduction 3 1.1 Open Source...............................................3 1.2 Decentralized package manager.....................................3 1.3 Binary management...........................................4 1.4 Cross platform, build system agnostic..................................4 1.5 Stable...................................................5 2 Install 7 2.1 Install with pip (recommended).....................................7 2.2 Install from brew (OSX).........................................8 2.3 Install from AUR (Arch Linux).....................................8 2.4 Install the binaries............................................8 2.5 Initial configuration...........................................8 2.6 Install from source............................................9 2.7 Python 2 Deprecation Notice.......................................9 3 Getting Started 11 3.1 A Timer Using POCO Libraries..................................... 11 3.2 Installing Dependencies......................................... 12 3.3 Building the Timer Example....................................... 14 3.4 Inspecting Dependencies......................................... 14 3.5 Searching Packages........................................... 15 3.6 Building with Other Configurations................................... 15 4 Using packages 17 4.1 Installing dependencies......................................... 17 4.2 Using profiles............................................... 21 4.3 Workflows............................................... -

Open Source Software Disclosure Document
GM Performance Data Recorder OPEN SOURCE SOFTWARE DISCLOSURE DOCUMENT Cosworth Ltd 18th August 2016 1. Contents 1. Contents .......................................................................................................................................... 2 2. Introduction .................................................................................................................................... 4 3. Open Source Software Licenses used in this Product ..................................................................... 5 4. Licenses Used by Individual Packages ............................................................................................. 6 ais326dq .............................................................................................................................................. 6 alsa-lib ................................................................................................................................................. 6 alsa-utils .............................................................................................................................................. 6 bulk...................................................................................................................................................... 6 busybox ............................................................................................................................................... 6 camera-module .................................................................................................................................. -

El Mensajero De Pekin
EL MENSAJERO DE PEKIN Pere Fonolleda Ferran Font Setembre 2009 Creació del Videojoc: “El Mensajero De Pekín” Pere Fonolleda i Ferran Font Índex de continguts 1.Introducció................................................................................................................13 1.1.Motivació...........................................................................................................13 1.2.Objectius del Projecte.......................................................................................14 1.3.Temporització del Projecte................................................................................16 1.4.Organització del document...............................................................................17 1.5.Separació de tasques.......................................................................................18 1.5.1.Pere Fonolleda...........................................................................................19 1.5.1.1.Implementació de l'animació per óssos.............................................19 1.5.1.2.Implementació de la interfície gràfica.................................................19 1.5.1.3.Implementació del multijugador..........................................................20 1.5.2.Ferran Font................................................................................................20 1.5.2.1.Implementació de la física..................................................................20 1.5.2.2.Implementació de la música...............................................................20 -

Open Source Software License
Open Source Software License Contents Open Source Software License.................................................................................................................. 5 Copyright Attribution ................................................................................................................................ 68 3 Open Source Software License GNU GPL This projector product includes the open source software programs which apply the GNU General Public License Version 2 (June 1991) ("GPL Programs"). We provide the source code of the GPL Programs until five (5) years after the discontinuation of same model of this projector product. If you desire to receive the source code of the GPL Programs, contact Epson. These GPL Programs are WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. The list of GPL Programs is as follows and the names of author are described in the source code of the GPL Programs The list of GPL Programs • busybox-1.21.0 • iptables-1.4.20 • linux-3.4.49 • patches • udhcp 0.9.8 • wireless_tools 29 • dbus-1.6.18 • EPSON original drivers • StonesStreet One Drivers • mtd-utils-1.5.0 The GNU General Public License Version 2 is as follows. You also can see the GNU General Public License Version 2 at http://www.gnu.org/licenses/. GNU GENERAL PUBLIC LICENSE Version 2, June 1991 5 Copyright (C) 1989, 1991 Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. Preamble The licenses for most software are designed to take away your freedom to share and change it. -

Third Party Copyright Notices and Licenses
Third Party Copyright Notices and Licenses The following table list the licensing requirements for Third Party Code used in the Intel® True Scale Fabric Products: Third Party Copyright Notices and Licenses True Scale Fabric True Scale Fabric True Scale Fabric Switch Firmware OFED+ Software Suite Software Apache License Version 2.0 X Autoconf Configure Script Exception X Broadcom Common Firmware Environment (Cfe) Readme X X CHASHTABLE Readme X X Embox - The BSD 3-Clause License X EXPAT LICENSE X X Ext2 Filesystems Utilities X FreeBSD X X FREEBSD LICENSE GCC RUNTIME LIBRARY EXCEPTION X X GNU GENERAL PUBLIC LICENSE V1 X GNU GENERAL PUBLIC LICENSE V2 X GNU GENERAL PUBLIC LICENSE V3 X GNU LESSER GENERAL PUBLIC LICENSE V2.1 X libsmi - A Library to Access SMI MIB Information X MVAPICH2 X ncurses_examples X X Net SNMP X NETSNMP License X OFED BSD License X X Open MPI X OPENBSD LICENSE X X OPENSSL LICENSE X X Python 3.1.1 license X RSA Data Security X X Tcl/Tk License Terms X The BSD 3-Clause License X X The Intel BSD License X The zlib/libpng License X X valgrind.h X ZLIB License X X X Apache License Version 2.0 Version 2.0, January 2004 http://www.apache.org/licenses/ TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION 1. Definitions. "License" shall mean the terms and conditions for use, reproduction, and distribution as defined by Sections 1 through 9 of this document. "Licensor" shall mean the copyright owner or entity authorized by the copyright owner that is granting the License.