Amazon Web Services: Overview of Security Processes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Federal Communications Commission DA 10-1348
Federal Communications Commission DA 10-1348 Availability of Additional Share of Retail Monthly Monthly Charge in Broadband Service Broadband Service Installation Charges Broadband Bundled Length of Broadband Service Competition Fixed Type of Broadband Speed Foreign Charge (in USD, PPP Modem Rental Promot-ional Country Offerings Name / Offerings (Connection) including Line part of Double Play/ Service Usage limit Broadband Provider's URL Provider Status Broadband Technology (download/ upload) Currency Foreign (Purchasing Power Charge Price Description (Community or Charge Rental/ Triple Play ? Contract Access Market* Currency) Parity) National Level) Leasing Charge Bigpond Cable Standard Double play/ full service Australia Telstra Bigpond Incumbent 48% Cable 8Mbps/128kbps Aus Dollar $29.95 $20.40 Self installation $15.75 12 months No 200 MB 200 MB phone http://www.bigpond.com/home Bigpond Cable Standard Double play/ full service Telstra Bigpond Incumbent Cable 8Mbps/128kbps Aus Dollar $39.95 $27.21 Self installation $15.75 12 months No 400 MB 400 MB phone Double play/ full service Telstra Bigpond Incumbent Bigpond Liberty 12 GB Cable 8Mbps/128kbps Aus Dollar $59.95 $40.84 Self installation $15.75 12 months No 12 GB phone Double play/ full service Telstra Bigpond Incumbent Bigpond Liberty 25 GB Cable 8Mbps/128kbps Aus Dollar $79.95 $54.46 Self installation $15.75 12 months No 25 GB phone Up to 30 Mbps in Bigpond Cable Extreme Sydney and Melbourne Double play/ full service Telstra Bigpond Incumbent Cable Aus Dollar $39.95 $27.21 Self installation -

Security on the Mainframe Stay Connected to IBM Redbooks
Front cover Security on the IBM Mainframe Operating system and application security IBM Security Blueprint and Framework IBM mainframe security concepts Karan Singh Lennie Dymoke-Bradshaw Thomas Castiglion Pekka Hanninen Vincente Ranieri Junior Patrick Kappeler ibm.com/redbooks International Technical Support Organization Security on the IBM Mainframe April 2010 SG24-7803-00 Note: Before using this information and the product it supports, read the information in “Notices” on page ix. First Edition (April 2010) This edition applies to the IBM System z10 Enterprise Class server, the IBM System z10 Business Class server, and Version 1, Release 11, Modification 0 of z/OS (product number 5694-A01). © Copyright International Business Machines Corporation 2010. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . ix Trademarks . .x Preface . xi The team who wrote this book . xi Now you can become a published author, too! . xii Comments welcome. xii Stay connected to IBM Redbooks . xiii Part 1. Introduction . 1 Chapter 1. Introduction. 3 1.1 IBM Security Framework. 4 1.1.1 People and identity . 5 1.1.2 Data and information. 5 1.1.3 Application and process . 5 1.1.4 Network, server, and endpoint . 5 1.1.5 Physical Infrastructure . 6 1.2 Framework and Blueprint . 7 1.3 IBM Security Blueprint. 7 Chapter 2. Security of the IBM Mainframe: yesterday and today . 13 2.1 Operating systems . 14 2.1.1 z/OS operating system family . 14 2.1.2 z/VM Hypervisor family . -

An Advance Visual Model for Animating Behavior of Cryptographic Protocols
An Advance Visual Model for Animating Behavior of Cryptographic Protocols Mabroka Ali Mayouf Maeref1*, Fatma Alghali2, Khadija Abied2 1 Sebha University, Faculty of Science, Department of Computer Science, P. O. Box 18758 Sebha, Libya, Libyan. 2 Sebha University of Libya, Sebha, Libya. * Corresponding author. Tel.: 00218-925132935; email: [email protected] Manuscript submitted February 13, 2015; accepted July 5, 2015. doi: 10.17706/jcp.10.5.336-346 Abstract: Visual form description benefits from the ability of visualization to provide precise and clear description of object behavior especially if the visual form is extracted from the real world. It provides clear definition of object and the behavior of that object. Although the current descriptions of cryptographic protocol components and operations use a different visual representation, the cryptographic protocols behaviors are not actually reflected. This characteristic is required and included within our proposed visual model. The model uses visual form and scenario-based approach for describing cryptographic protocol behavior and thus increasing the ability to describe more complicated protocol in a simple and easy way. Key words: Animation, cryptographic protocols, interactive tool, visualization. 1. Introduction Cryptographic protocols (CPs) mostly combine both theory and practice [1], [2]. These cause protocol complexity describing and understanding. Therefore, separating the mathematical part from the protocol behavior should provide feeling of how the protocol works, thus increasing the ability to describe and to gain confidence in reflecting more complicated information about CPs, as well as to generate interest to know about other more complex protocol concepts. Several researchers realized the use of visual model and animation techniques to reflect the explanation of the learning objectives and their benefits [3]-[11]. -

IBM Security Access Manager Version 9.0.7 June 2019: Advanced Access Control Configuration Topics Contents
IBM Security Access Manager Version 9.0.7 June 2019 Advanced Access Control Configuration topics IBM IBM Security Access Manager Version 9.0.7 June 2019 Advanced Access Control Configuration topics IBM ii IBM Security Access Manager Version 9.0.7 June 2019: Advanced Access Control Configuration topics Contents Figures .............. vii Configuring authentication ........ 39 Configuring an HOTP one-time password Tables ............... ix mechanism .............. 40 Configuring a TOTP one-time password mechanism 42 Configuring a MAC one-time password mechanism 45 Chapter 1. Upgrading configuration ... 1 Configuring an RSA one-time password mechanism 46 Upgrading external databases with the dbupdate tool Configuring one-time password delivery methods 50 (for appliance at version 9.0.0.0 and later) .... 2 Configuring username and password authentication 54 Upgrading a SolidDB external database (for Configuring an HTTP redirect authentication appliance versions earlier than 9.0.0.0) ...... 3 mechanism .............. 56 Upgrading a DB2 external runtime database (for Configuring consent to device registration .... 57 appliance versions earlier than 9.0.0.0) ...... 4 Configuring an End-User License Agreement Upgrading an Oracle external runtime database (for authentication mechanism ......... 59 appliance versions earlier than 9.0.0.0) ...... 5 Configuring an Email Message mechanism .... 60 Setting backward compatibility mode for one-time HTML format for OTP email messages .... 62 password ............... 6 Configuring the reCAPTCHA Verification Updating template files ........... 6 authentication mechanism ......... 62 Updating PreTokenGeneration to limit OAuth tokens 7 Configuring an Info Map authentication mechanism 64 Reviewing existing Web Reverse Proxy instance point Embedding reCAPTCHA verification in an Info of contact settings ............ 8 Map mechanism ............ 66 Upgrading the signing algorithms of existing policy Available parameters in Info Map ..... -

Data Centers and Cloud Computing Data Centers
Data Centers and Cloud Computing Data Centers • Large server and storage farms – 1000s of servers • Intro. to Data centers – Many TBs or PBs of data • Virtualization Basics • Used by – Enterprises for server applications – Internet companies • Intro. to Cloud Computing • Some of the biggest DCs are owned by Google, Facebook, etc • Used for – Data processing – Web sites – Business apps Computer Science Lecture 22, page 2 Computer Science Lecture 22, page 3 Inside a Data Center MGHPCC Data Center • Giant warehouse filled with: • Racks of servers • Storage arrays • Cooling infrastructure • Power converters • Backup generators • Data center in Holyoke Computer Science Lecture 22, page 4 Computer Science Lecture 22, page 5 Modular Data Center Virtualization • ...or use shipping containers • Each container filled with thousands of servers • Can easily add new containers • Virtualization: extend or replace an existing interface to – “Plug and play” mimic the behavior of another system. – Just add electricity – Introduced in 1970s: run legacy software on newer mainframe hardware • Allows data center to be easily • Handle platform diversity by running apps in VMs expanded – Portability and flexibility • Pre-assembled, cheaper Computer Science Lecture 22, page 6 Computer Science Lecture 22, page 7 Types of Interfaces Types of OS-level Virtualization • Different types of interfaces – Assembly instructions – System calls • Type 1: hypervisor runs on “bare metal” – APIs • Type 2: hypervisor runs on a host OS • Depending on what is replaced /mimiced, -

Making Virtual Assistants Accessible 3
Making Virtual Assistants Accessible 3. Using Ring Doorbell deafscotland is the user led, membership organisation for the deaf sector in Scotland. For more information, visit the deafscotland website by clicking here: https://deafscotland.org/. The current UK-wide COVID-19 pandemic has brought the impact and understanding of social isolation into the mainstream and raised awareness of the devastating effects isolation can have. We have seen a recent increase in the use of virtual communication technology which allows people to stay connected. Virtual Assistant devices are being used more regularly to bridge this communication gap. 1. How to use Ring doorbell: Ring video doorbell alerts you when someone rings your doorbell or if movement is detected at your property. Announcements are sent to your phone, tablet or PC with you being able to see, hear and speak to visitors when this happens no matter where you are. Ring is available in a range of products and can be linked to Amazon Alexa-enabled devices. See Factsheet VA.2 ‘How to use the Amazon Echo’. Any Ring doorbell or security camera can be set up for two way communication. This two way audio/video communication can be supported on Amazon Echo Dot, Echo Spot and Echo Show. When linked, announcements will be heard through the Echo when anyone presses the doorbell or something triggers the motion sensors. 2. How to connect Ring to Alexa supported devices: Connecting Ring devices to an Echo is a simple process. To do this, download the Alexa app and add Ring as a skill in your Alexa app. -

Deploy, Operate, and Evolve Your Data Center: HP Datacenter Care
Brochure Deploy, operate, and evolve your data center HP Datacenter Care The data center is evolving—shouldn’t Improve agility, scalability—react at the your support keep pace? speed of business Historically, business-critical IT has been delivered on dedicated, HP Datacenter Care service is designed to support this homogenous, and proprietary infrastructures. In this siloed results-oriented approach by providing an environment-wide IT model, performance, uptime, and security outweighed support solution tailored to your needs. HP Datacenter Care considerations of speed, agility, and cost. Now, however, the trends is a flexible, comprehensive, relationship-based approach to of mobility, big data, and cloud computing are fundamentally personalized support and management of heterogeneous data changing how you deliver information, and how technology is centers. Datacenter Care is a structured framework of repeatable, implemented, moving closer to unconstrained access to IT. tested, and globally available services “building blocks.” You have an account support manager (ASM) who knows your business and your IT is delivered as services anywhere, across hybrid deployments of IT environment, and who can help you select the services you need private, managed, and public cloud, as well as traditional IT. It’s what from an extensive portfolio of support and consulting services. The HP is developing as the Converged Cloud, and it can finally allow ASM leverages our experience in supporting complex environments, enterprises to achieve business agility, with choice and improved global support partnerships, and technical expertise. ROI. Today, HP is a leader in the industry for support services, for customers worldwide who need to keep their systems running, So you get exactly the services you need—when and where you reduce costs, and avoid issues. -

Pdf/Idm Tech Wp 11G R1.Pdf
Oracle® Fusion Middleware Integration Overview for Oracle Identity Management Suite 11g Release 1 (11.1.1) E15477-03 August 2012 Oracle Fusion Middleware Integration Overview for Oracle Identity Management Suite, 11g Release 1 (11.1.1) E15477-03 Copyright © 2010, 2012, Oracle and/or its affiliates. All rights reserved. Primary Author: Vinaye Misra Contributors: Sidhartha Das, Ellen Desmond, Subbu Devulapalli, Sandy Lii, Kavya Muthanna, Sanjay Rallapalli, Vinay Shukla, Olaf Stullich, Lyju Vadassery, Mark Wilcox This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -

The Wizard Stands Behind the Curtain, Amazon's Invisible Wall and The
Find our latest analyses and trade ideas on bsic.it The wizard stands behind the curtain, Amazon’s invisible wall and the acquisition of Ring for $1 billion Amazon.com (NASDAQ: AMZN) – market cap as of 02/03/2018: $726.28bn Introduction Every time Amazon announces an acquisition, it is hard not to feel the excitement. All the more so considering that the online giant has had an uncertain relationship with M&A and has only in the recent years garnered the confidence to pull the trigger on large transactions. As a matter of fact, Amazon was an avid acquirer before the 2000s, when the dot.com bubble wiped out the value of Amazon’s external acquisitions and almost brought the company on the verge of bankruptcy. In fact, after the 2000s, Jeff Bezos has been more than reluctant on performing large deals, with only small to medium sized transactions being performed in the next decade, and of which Zappos and Audible are perhaps the only moderate standouts. However, last year the tune changed with the acquisition of Whole Foods, and Amazon looks like it is reverting to its old and original nature. In this very context we place the acquisition of Ring for $1 billion, setting the record for Amazon’s second largest acquisition to date. About Amazon.com Headquartered in Seattle (US), Amazon.com is the world’s largest online shopping retailer, operating in 189 countries and employing ca. 341,400 people across 5 continents. The company was incorporated in the state of Washington in 1994 by Jeff Bezos, who currently is CEO and President, and then reincorporated in the state of Delaware in 1996. -

The Cloud-Enabled Data Center
A Revolutionary Technology Extending the Ultra-Broad Functionality of Ethernet White Paper May 2013 The Cloud-Enabled Data Center The Cloud-Enabled Data Center Introduction A growing number of organizations are adopting some form of cloud computing to meet the challenges of rapidly deploying their IT services and addressing their dynamic workload environments while maximizing their IT return on investments (ROIs). Cloud computing gives users the ability to access the IT resources faster than traditional and virtual servers. It also provides improved manageability and requires less maintenance. By deploying technology as a service, your users access only the resources they need for a specific task, which prevents you from incurring costs for computing resources not in use. In addition, developing a cloud-enabled data center can improve operational efficiencies while reducing operational expenses by 50%. Panduit, the leader in Unified Physical Infrastructure offerings, and IBM, a pioneer in delivering cloud computing solutions to clients, have joined forces to deliver optimized, custom and preconfigured solutions for the cloud- enabled data center. This white paper describes how network, storage, compute and operations are important factors to consider when deploying private and public cloud computing in the data center. Specifically, it examines integrated stack/pre- configured and custom cloud deployments. It also explains the importance of the physical infrastructure as the foundation in successful cloud deployment and maintenance. Finally, it showcases how IBM’s depth of experience in delivering systems and software for cloud solutions when combined with Panduit’s physical infrastructure expertise, provides a tremendous impact on room-level data center environmental and new-age topology. -
Ready for Upload GCD Wls Networks
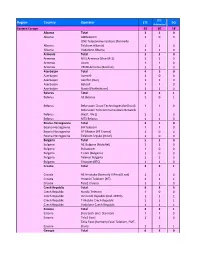
LTE‐ Region Country Operator LTE 5G Advanced Eastern Europe 93 60 18 Albania Total 320 Albania ALBtelecom 100 ONE Telecommunications (formerly Albania Telekom Albania) 110 Albania Vodafone Albania 110 Armenia Total 330 Armenia MTS Armenia (Viva‐MTS) 110 Armenia Ucom 110 Armenia VEON Armenia (Beeline) 110 Azerbaijan Total 430 Azerbaijan Azercell 100 Azerbaijan Azerfon (Nar) 110 Azerbaijan Bakcell 110 Azerbaijan Naxtel (Nakhchivan) 110 Belarus Total 431 Belarus A1 Belarus 101 Belarus Belarusian Cloud Technologies (beCloud) 110 Belarusian Telecommunications Network Belarus (BeST, life:)) 110 Belarus MTS Belarus 110 Bosnia‐Herzegovina Total 310 Bosnia‐Herzegovina BH Telecom 110 Bosnia‐Herzegovina HT Mostar (HT Eronet) 100 Bosnia‐Herzegovina Telekom Srpske (m:tel) 100 Bulgaria Total 530 Bulgaria A1 Bulgaria (Mobiltel) 110 Bulgaria Bulsatcom 100 Bulgaria T.com (Bulgaria) 100 Bulgaria Telenor Bulgaria 110 Bulgaria Vivacom (BTC) 110 Croatia Total 331 Croatia A1 Hrvatska (formerly VIPnet/B.net) 110 Croatia Hrvatski Telekom (HT) 111 Croatia Tele2 Croatia 110 Czech Republic Total 433 Czech Republic Nordic Telecom 100 Czech Republic O2 Czech Republic (incl. CETIN) 111 Czech Republic T‐Mobile Czech Republic 111 Czech Republic Vodafone Czech Republic 111 Estonia Total 331 Estonia Elisa Eesti (incl. Starman) 110 Estonia Tele2 Eesti 110 Telia Eesti (formerly Eesti Telekom, EMT, Estonia Elion) 111 Georgia Total 630 Georgia A‐Mobile (Abkhazia) 100 Georgia Aquafon GSM (Abkhazia) 110 Georgia MagtiCom 110 Georgia Ostelecom (MegaFon) (South Ossetia) 100 Georgia -

A Matter of Security, Privacy and Trust
A matter of security, privacy and trust: A study of the principles and values of encryption in New Zealand Michael Dizon Ryan Ko Wayne Rumbles Patricia Gonzalez Philip McHugh Anthony Meehan Acknowledgements This study was funded by grants from the New Zealand Law Foundation and the University of Waikato. We would like to express our gratitude to our project collaborators and members of the Advisory Board – Prof Bert-Jaap Koops (Tilburg University), Prof Lyria Bennett Moses (UNSW Sydney), Prof Alana Maurushat (Western Sydney University), and Associate Professor Alex Sims (University of Auckland) – for their support as well as feedback on specific parts of this report. We would also like to thank Patricia Gonzalez, Joseph Graddy, Philip McHugh, Anthony Meehan, Jean Murray and Peter Upson for their valuable research assistance and other contributions to this study. Michael Dizon, Ryan Ko and Wayne Rumbles Principal investigators December 2019 Executive summary Cybersecurity is crucial for ensuring the safety and well-being of the general public, businesses, government, and the country as a whole. New Zealand has a reasonably comprehensive and well-grounded legal regime and strategy for dealing with cybersecurity matters. However, there is one area that deserves further attention and discussion – encryption. Encryption is at the heart of and underpins many of the technologies and technical processes used for computer and network security, but current laws and policies do not expressly cover this significant technology. The principal objective of this study is to identify the principles and values of encryption in New Zealand with a view to informing future developments of encryption- related laws and policies.