Avaddon Ransonomics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2013 Legal Apps for Android, Ipad/Mac & Windows 8 Users
2013 LEGAL APPS FOR ANDROID, IPAD/MAC & WINDOWS 8 USERS Information for lawyers on where to find apps, How To’s and more. Presented by: Atty Nerino J. Petro, Jr. Practice Management Advisor Practice411™ Law Office Management Assistance Program State Bar of Wisconsin Tablet Comparison Chart, Cont’d Contents Smartphone and Tablet Resource Links ......................................................................................... 4 For Android ..................................................................................................................................... 4 Android Online Resources .......................................................................................................... 4 Apple Mac Resources .................................................................................................................... 6 Mac Online Resources ............................................................................................................... 6 Apple iPhone and iPad ................................................................................................................... 7 iPhone and iPad Online resources: ........................................................................................... 7 BlackBerry ...................................................................................................................................... 8 Kindle Fire & Nook Tablet.............................................................................................................. 8 Windows 8 Resources -
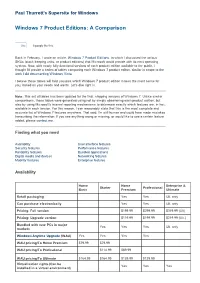
Windows 7 Product Editions: a Comparison
Paul Thurrott's Supersite for Windows Windows 7 Product Editions: A Comparison Like 8 people like this. Back in February, I wrote an article, Windows 7 Product Editions , in which I discussed the various SKUs (stock keeping units, or product editions) that Microsoft would provide with its next operating system. Now, with nearly fully-functional versions of each product edition available to the public, I thought I'd provide a series of tables comparing each Windows 7 product editon, similar in scope to the work I did documenting Windows Vista . I believe these tables will help you pick which Windows 7 product edition makes the most sense for you, based on your needs and wants. Let's dive right in. Note: This set of tables has been updated for the final, shipping versions of Windows 7. Unlike similar comparisons, these tables were generated using not by simply observering each product edition, but also by using Microsoft's internal reporting mechanisms to determine exactly which features are, in fact, available in each version. For this reason, I can reasonably state that this is the most complete and accurate list of Windows 7 features anywhere. That said, I'm still human and could have made mistakes transcribing the information. If you see anything wrong or missing, or would like to see a certain feature added, please contact me . Finding what you need Availability User interface features Security features Performance features Reliability features Bundled applications Digital media and devices Networking features Mobility features Enterprise features Availability Home Home Enterprise & Starter Professional Basic Premium Ultimate Retail packaging Yes Yes Ult. -

Wednesday, October 26, 2016 Tuesday, October 25, 2016
& SEE PAGES 12 – 15 FOR Tuesday, October 25, 2016 DEV & Anglebrackets KEYNOTES GRAND BALLROOM 6:00pm - 8:00pm The Microsoft Open Source Journey Tomorrow Today: Build Cool Sh*t Scott Hanselman, Principal Community Architect Giorgio Sardo and Pete Brown, for Web Platform and Tools, Microsoft Windows & Devices Group, Microsoft Wednesday, October 26, 2016 7:30am - 8:30am Continental Breakfast KEYNOTE GRAND BALLROOM 8:30am - 9:45am Mobile-first, Cloud-first Development Scott Guthrie, Executive Vice President, Cloud and Enterprise Group, Microsoft 9:45am - 10:30am Coffee Break - Marquee Ballroom, Expo Hall opens SESSIONS GB 123 GB 120 GB 124 GB 116 GB 121 GB 119 GB 104 & 105 10:30am - 11:45am Understanding the Software Project Implementing Web .NET (Core and More) Strategies for TypeScript and Build an App for Windows Desktop Design Security in Your Overview Modernizing ES6 in 60-ish Xbox One – New App Development Juval Lowy ASP.NET Scott Hunter ASP.NET 4.6 Minutes Capabilities in Landscape Application Solutions with Dan Wahlin & UWP Brian Noyes Javier Lozano ASP.NET Core John Papa Jerry Nixon Jay Schmelzer 11:45am - 12:00pm Break 12:00pm - 1:00pm Breaking C# 7 How to Be a More than Unit Tests: Introduction to Angular 2 in How to Scale Dependencies to Kathleen Good Community Automate All-the- Twitter Bootstrap 60-ish Minutes .NET Apps with Allow Unit Testing Dollard Member by Things Joe Guadagno Dan Wahlin & Distributed Steve Smith Contributing to Jordan Matthiesen John Papa Caching OSS & Iqbal Khan Brian Clark James Montemagno 1:00pm - 2:15pm -

Vista DRM Wrap-Up & Announcing "Securable"
Transcript of Episode #75 Vista DRM Wrap-Up and Announcing "SecurAble" Description: Following last week’s guest appearance by Peter Gutmann, Steve and Leo wrap up the topic of Vista’s new, deep, and pervasive Digital Rights Management (DRM) system. Steve also announces the completion and availability of his latest freeware: “SecurAble." High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-075.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-075-lq.mp3 INTRO: Netcasts you love, from people you trust. This is TWiT. Leo Laporte: Bandwidth for Security Now! is provided by AOL Radio at AOL.com/podcasting. This is Security Now! with Steve Gibson, Episode 75 for January 18, 2007: Vista DRM. Security Now! is brought to you by Astaro, makers of the Astaro Security Gateway, on the web at www.astaro.com. Steve Gibson, laboring away at his lab of security at GRC.com, has come up with... Steve Gibson: My fortress of solitude. Leo: Your fortress of solitude has come up with yet another great application, SecurAble. We’re going to talk about that because it’s time, it’s time. But before we get to that, Steve, I don’t know, I hope a lot of people heard last week’s episode. And if you didn’t, I almost want to say pause the iPod and go back to 73 because... Steve: Oh, Leo, don’t almost say. Absolutely say it. Because I do want to continue on the topic a little bit more. -
Amazon Sidewalk
Security Now! Transcript of Episode #796 Page 1 of 27 Transcript of Episode #796 Amazon Sidewalk Description: At the beginning of this podcast, you're going to receive some details about another update to Chrome, and news of a few new high-profile ransomware victims. You'll learn about a breathtaking, remotely exploitable zero-click complete iPhone security compromise, as well as another significant big step forward for DNS privacy beyond DoH. We'll explain the nature of another serious and probably lingering problem within many Android apps. I have a few interesting bits of miscellany and SpinRite news to share. And before this is over, you will have obtained a full working sense for exactly what it is that Amazon has created and why, with their Amazon Sidewalk neighborhood IoT network concept, coming soon to all of your Amazon devices. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-796.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-796-lq.mp3 SHOW TEASE: It's time for Security Now!. Steve Gibson is here. Lots to talk about, including one of the most breathtaking iPhone hacks ever. Thank goodness it's been patched. We'll also take a look at a replacement for DoH known as ODoH. ODoH. And Steve's going to analyze the security and privacy model of Amazon's Sidewalk technology. Should you leave it on? Steve answers that question next on Security Now!. Leo Laporte: This is Security Now! with Steve Gibson, Episode 796, recorded Tuesday, December 8th, 2020: Amazon Sidewalk. -

Conversational-Windows-10.Pdf
! "#$%&'()*+#$),!-+$.#/(!01!! 23!4,)$!56!-'+78*!9!:);,!<8;''#**! "#=3'+78*>!?10@! ! Conversational Windows 10 Published by Conversational Geek Inc. www.conversationalgeek.com All rights reserved. No part of this book shall be reproduced, stored in a retrieval system, or transmitted by any means, electronic, mechanical, photocopying, recording, or otherwise, without written permission from the publisher. No patent liability is assumed with respect to the use of the information contained herein. Although every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions. Nor is any liability assumed for damages resulting from the use of the information contained herein. Trademarks Conversational Geek, the Conversational Geek logo and J. the Geek are trademarks of Conversational Geek. All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. We cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. Warning and Disclaimer Every effort has been made to make this book as complete and as accurate as possible, but no warranty or fitness is implied. The information provided is on an “as is” basis. The author and the publisher shall have neither liability nor responsibility to any person or entity with respect to any loss or damages arising from the information contained in this book or programs accompanying it. Additional Information For general information on our other products and services, or how to create a custom Conversational Geek book for your business or organization, please visit our website at ConversationalGeek.com Publisher Acknowledgments All of the folks responsible for the creation of this guide: Author: Alan L. -

Mac Security
Table of Contents Masthead ___________________________________________________________________ 4 About that Apple Optical Output Port – It’s a TOS up________________________________ 5 Apple’s Software License Agreement vs. Microsoft’s Vista License Agreement __________ 10 Rants, Raves and Revelations __________________________________________________ 19 According to Hoyle... _________________________________________________________ 22 Cross-Platform Software Development from a Macintosh Perspective: C++ Application Programming with REALbasic _____________________________________________________ 22 The European Perspective_____________________________________________________ 27 Geek Speak: Random Mac Stuff You Need to Know ________________________________ 31 Using the Growl Notification System _________________________________________________ 31 Ivory Tower - November 2006 __________________________________________________ 34 MacFevre __________________________________________________________________ 37 How to Make an AudioBook, Part 3 _________________________________________________ 37 The Northern Spy____________________________________________________________ 39 Think Upon a Thunk ______________________________________________________________ 39 doc_Babad's Software Review Overview - An Introduction___________________________ 42 Mac Security 101 ____________________________________________________________ 44 Why Do I Need Anti-virus Software? What You Should Know ___________________________ 44 Doc_Babad's Macintosh Tips - A Macintosh -

IS DESKTOP COMPUTING DEAD? by Pranav Dixit
This article was written for the Magazine Writing program at New York University’s Arthur L. Carter Journalism Institute. IS DESKTOP COMPUTING DEAD? By Pranav Dixit “PCs are like trucks. Only a few people need them. Eventually, they will be supplanted by devices, smart devices like tablets and phones, which are like cars. Not everybody needs a truck, but everybody needs a car.” - Steve Jobs at an All Things Digital conference, 2010. When I walk into the Best Buy store in Union Square the day before Thanksgiving, the crowds are already jostling for space even though most discounts don’t kick in till the evening of the following day. A quick look at the first 10 people in the checkout line reveals the following: the first four people are buying iPads; two people are buying the iPhone 5S; three are buying assorted Android smartphones; and the last person is trying haul an oversized LED TV all by herself. No one is buying a computer. “When I started working here 3 years back, I’d say we had about 1 in 3 people coming in to get a laptop,” says Holly Stern, a Best Buy customer service rep who looks particularly frazzled that day. “Now, it’s like 1 in 10. They want tablets, mostly. And phones. We had a four-week waiting list for the iPhone 5S last month.” To use a Silicon Valley buzzword, desktop computing has been completely and thoroughly disrupted. It is, after all, the age of here and now, and no one wants to be chained to a desk or lug around a laptop anymore to check their email or play a game when they can easily accomplish a majority of these casual activities on smaller, smarter, devices. -

Connotations Volume 16 Issue 06
Volume 18, Issue 6 December / January 2008 / 2009 ConNotations FREE The Bi-Monthly Science Fiction, Fantasy & Convention Newszine of the Central Arizona Speculative Fiction Society An Interview with Featured Inside Melanie Rawn Regular Features Special Features by Catherine Book SF Tube Talk An Interview with Melanie Rawn I met Melanie Rawn at a All the latest news about by Catherine Book small restaurant in Sedona, a Scienc Fiction TV shows halfway point between her home by Lee Whiteside in Flagstaff and mine in Phoe- Inkheart Screening Passes Contest nix. Her smile was like a ray of 24 Frames sunshine. Now, you might say All the latest Movie News that was too much a cliché; but, Leo Laporte and his by Lee Whiteside you know, clichés had to come Empire of the Net from somewhere and that is By Shane Shellenbarger exactly the right way to describe Gamers Corner her. Melanie is such a nice, New and Reviews from An Amercan in New Zealand friendly person; her interview the gaming world by Jeffrey Lu was so fun for me. I started by asking her how Videophile Plus long she’d been writing. Reviews of genre releases Scribbling – her term – since on DVD CASFS Business Report she was five years old, she remembered Melanie is one where A) she’s not that she started actually writing when she rewriting their stuff in her head, and B) Screening Room FYI was 20. She thinks a writer should not set her inner proofreader turns off. She Reviews of current theatrical releases News and tidbits of interest to fans pen to paper until they are certain they often receives galleys for her review and know the language they intend to use. -

Security Now! #832 - 08-17-21 Microsoft’S Culpable Negligence
Security Now! #832 - 08-17-21 Microsoft’s Culpable Negligence This week on Security Now! This week we look at another very significant improvement in Firefox's privacy guarantees and the first steps for Facebook into native end-to-end encryption. We look at several well-predicted instances of abuse of Microsoft's PrintNightmare vulnerabilities, and at a clever cryptocurrency mining Botnet that optimizes the commandeered system for its own needs. We note ASUS' terrific move to help their motherboard users make the move to Windows 11, and at the merger of NortonLifeLock and Avast. Then, after touching upon a bit of errata and some closing-the-loop feedback from our terrific podcast followers, we conclude with a sober consideration of Microsoft's handling of vulnerability patching during the past year. And we ask what it means. Sadly, this one speaks for itself... I suppose the racks were full? (They appear to be full.) But why not at least set them on top? Browser News Firefox Update I think it was the week before last that Paul Thurrott mentioned during Windows Weekly that he had done some testing of the latest Firefox and he was bullish about it. But I don't recall the details. And Leo, I confess that I may have missed a more recent change, but I think that the most recent browser change you've made, as a consequence of what Paul learned, is back over to Firefox, right? Is Firefox again your default URL handler? In any event, it's time to catch up on the technological changes that Firefox has been making. -

Windows 10 Field Guide Includes Reference, Surface Pro 3, Surface Pro 4, and Surface Studio Posters
Windows 10 Field Guide Includes Reference, Surface Pro 3, Surface Pro 4, and Surface Studio posters Paul Thurrott, Rafael Rivera and Martin McClean This book is for sale at http://leanpub.com/windows10fieldguide This version was published on 2021-07-06 This is a Leanpub book. Leanpub empowers authors and publishers with the Lean Publishing process. Lean Publishing is the act of publishing an in-progress ebook using lightweight tools and many iterations to get reader feedback, pivot until you have the right book and build traction once you do. © 2015 - 2021 Paul Thurrott, Rafael Rivera and Martin McClean Tweet This Book! Please help Paul Thurrott, Rafael Rivera and Martin McClean by spreading the word about this book on Twitter! The suggested tweet for this book is: Just picked up #Windows10FieldGuide, thanks @thurrott @withinrafael and Martin! The suggested hashtag for this book is #Windows10FieldGuide. Find out what other people are saying about the book by clicking on this link to search for this hashtag on Twitter: #Windows10FieldGuide Contents About the Book ................................................ 1 Trademarks and disclaimers ...................................... 1 We want your feedback! ......................................... 1 Meet the authors ............................................. 1 Thanks! ................................................... 2 Introduction .................................................. 1 Welcome to the final version of the Windows 10 Field Guide .................. 1 Original introduction -

The Future of Windows
The Future of Windows Michael Shalkey Channel Islands PC Users Group Camarillo, California The bottom line question is “What do you need to do to get ready for the coming changes?” and the answer is nothing. The kernel of the idea of this presentation was discussion by veteran Microsoft journalists and authors Paul Thurrott and Mary Jo Foley during the podcast Windows Weekly about the announcement of the Edge browser giving up the Microsoft rendering engine for the Chromium engine and the ramifications of that to PC computing. With the opening of Microsoft’s browser to all Chrome extensions there will finally be a unification of extensions between the 3 major browsers: Chrome, Firefox, Microsoft’s Edge (successor to Internet Explorer). More on that later. A platform like Windows is only as good as programs that run on it and if no programs will run on it, it’s useless. How programs work today is different than how they worked 30 years ago. Few computers are coming with CD drives and none have floppy drives. Many companies are moving away from the idea of installing a program on your computer and instead want you to use their program “in the cloud” from their websites (and charge you by the month for the privilege). This gives them the advantage of regular recurring revenue which makes their stock holders and Wall Street happy How companies make their money is a good indication of what they may plan to do in the future. ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ To help in understanding my future predictions, let’s start with the past and the history of how we got to where we are today.